Professional Documents
Culture Documents
IFW Security Infographic
Uploaded by
IDG_World0 ratings0% found this document useful (0 votes)
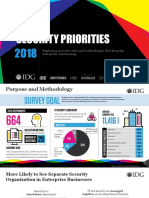
22 views1 pageCompanies have a process for assessing the cybersecurity practices of third-party partners. 51 % of IT decision-makers plan to invest / increase security investment in the next 12 months. 83 % of companies with high-performing security practices collaborate with others to deepen their knowledge of security and threat trends.
Original Description:
Copyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCompanies have a process for assessing the cybersecurity practices of third-party partners. 51 % of IT decision-makers plan to invest / increase security investment in the next 12 months. 83 % of companies with high-performing security practices collaborate with others to deepen their knowledge of security and threat trends.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
22 views1 pageIFW Security Infographic
Uploaded by
IDG_WorldCompanies have a process for assessing the cybersecurity practices of third-party partners. 51 % of IT decision-makers plan to invest / increase security investment in the next 12 months. 83 % of companies with high-performing security practices collaborate with others to deepen their knowledge of security and threat trends.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
You are on page 1of 1
Detecting/Combating
Protecting Company Data
Enforcing Security Policy
Advanced Persistent Threats
of companies have a
process for assessing
the cybersecurity
practices of
third-party partners.
1
TOP INVESTMENTS
#1 GOAL
DRIVING SECURITY INVESTMENTS
#3 GOAL
DRIVING SECURITY INVESTMENTS
#2 GOAL
DRIVING SECURITY INVESTMENTS
ENTERPRISE SMB
41
%
Only
of organizations
do not have a plan
for responding to
insider threats.
1
51
%
of IT decision-makers
plan to invest/increase
security investment
in the next 12 months
89
%
of IT decision-makers feel that security
is a critical/very important IT investment
84
%
of IT decision-makers
believe that security
will be impacted by
the Internet of Things
over the next
12 months.
73
%
of companies with
high-performing security
practices collaborate with
others to deepen their
knowledge of security
and threat trends.
1
82
%
53%
Anti-Malware
44%
Firewalls
TOP INVESTMENTS
ENTERPRISE SMB
42%
Firewalls
44%
Identity
Management
TOP INVESTMENTS
ENTERPRISE & SMB
38%
Intrusion Detection
and Protection
STILL CURIOUS
ABOUT SECURITY?
IT Decision-Makers are
Investing in an Average of
6 Security Solutions
How IT Decision-Makers Navigate through
Security Objectives and Obstacles
Sources: 2014 Navigating IT: Objectives and Obstacles / 2014 US State of Cybercrime Survey
1
To view the complete research results, download the executive summary
or contact your InfoWorld sales executive: infoworldmediakit.com
You might also like
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5794)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1090)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (838)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (890)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (587)
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (537)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (344)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (821)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (119)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (399)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2219)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (265)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (73)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- A Guide To Understanding How Organizations Are Evolving To A Digital-First Business ModelDocument1 pageA Guide To Understanding How Organizations Are Evolving To A Digital-First Business ModelIDG_WorldNo ratings yet
- 2017 IDG Customer Engagement ExcerptDocument8 pages2017 IDG Customer Engagement ExcerptIDG_WorldNo ratings yet
- IDG 2018 Cloud Computing ResearchDocument8 pagesIDG 2018 Cloud Computing ResearchIDG_World100% (4)
- 2018 U.S. State of Cybercrime SurveyDocument9 pages2018 U.S. State of Cybercrime SurveyIDG_WorldNo ratings yet
- 2018 Global State of Information Security SurveyDocument9 pages2018 Global State of Information Security SurveyIDG_WorldNo ratings yet
- 2018 IDG Security Priorities InfographicDocument1 page2018 IDG Security Priorities InfographicIDG_WorldNo ratings yet
- 2018 State of The Network InfographicDocument1 page2018 State of The Network InfographicIDG_WorldNo ratings yet
- 2017 U.S. State of Cybercrime SurveyDocument8 pages2017 U.S. State of Cybercrime SurveyIDG_WorldNo ratings yet
- 2018 CIO Tech Poll: Economic Outlook InfographicDocument1 page2018 CIO Tech Poll: Economic Outlook InfographicIDG_WorldNo ratings yet
- CIOs Are Driving Digital Transformation InfographicDocument1 pageCIOs Are Driving Digital Transformation InfographicIDG_WorldNo ratings yet
- 2018 IDG Cloud Computing InfographicDocument1 page2018 IDG Cloud Computing InfographicIDG_WorldNo ratings yet
- 2018 CIO Tech Poll: Economic OutlookDocument8 pages2018 CIO Tech Poll: Economic OutlookIDG_World100% (1)
- 2018 IDG Security Priorities SurveyDocument9 pages2018 IDG Security Priorities SurveyIDG_WorldNo ratings yet
- State of The Network 2018Document10 pagesState of The Network 2018IDG_WorldNo ratings yet
- 2018 IDG Digital Business SurveyDocument9 pages2018 IDG Digital Business SurveyIDG_World100% (3)
- CIO Tech Poll: Tech Priorities 2018Document7 pagesCIO Tech Poll: Tech Priorities 2018IDG_WorldNo ratings yet
- Digital Disruption & The NetworkDocument1 pageDigital Disruption & The NetworkIDG_WorldNo ratings yet
- State of The CIO 2018Document9 pagesState of The CIO 2018IDG_WorldNo ratings yet
- Demand GenerationDocument9 pagesDemand GenerationIDG_World100% (1)
- 2017 Customer Engagment Sample SlidesDocument8 pages2017 Customer Engagment Sample SlidesIDG_WorldNo ratings yet
- IDG 2017 Security Priorities StudyDocument8 pagesIDG 2017 Security Priorities StudyIDG_WorldNo ratings yet
- 2017 CIO Tech Poll: Economic OutlookDocument6 pages2017 CIO Tech Poll: Economic OutlookIDG_WorldNo ratings yet
- CSO 2016 SIEM Vendor Scorecard ResearchDocument7 pagesCSO 2016 SIEM Vendor Scorecard ResearchIDG_WorldNo ratings yet
- CW Forecast 2017 SampleDocument8 pagesCW Forecast 2017 SampleIDG_World100% (1)
- State of The Network 2017Document8 pagesState of The Network 2017IDG_WorldNo ratings yet
- State of The CIO 2017Document9 pagesState of The CIO 2017IDG_World100% (1)
- 2017 Global State of Information Security SurveyDocument7 pages2017 Global State of Information Security SurveyIDG_World100% (1)
- The Connection Between Security and Data & AnalyticsDocument1 pageThe Connection Between Security and Data & AnalyticsIDG_World100% (1)
- Tech Priorities 2017 SampleDocument7 pagesTech Priorities 2017 SampleIDG_WorldNo ratings yet
- Today's Cloud Focus & MotivatorsDocument1 pageToday's Cloud Focus & MotivatorsIDG_World100% (2)