Professional Documents
Culture Documents
Deep Packet Inspection
Uploaded by
arieu00Original Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Deep Packet Inspection
Uploaded by
arieu00Copyright:
Available Formats
Knowledge Articles & Software
Page 1 of 4
How do I inspect HTTPS traffic? [Fireware XTM v11.4.x]
Question
How do I inspect HTTPS traffic? [Fireware XTM v11.4.x] Many web sites use both the HTTP and HTTPS protocols to send information to users. While HTTP traffic can be examined easily, HTTPS traffic is encrypted. To examine HTTPS traffic requested by a user on your network, you must configure your XTM device to decrypt the information and then encrypt it with a certificate the user trusts. By default, the XTM device re-signs the content it has inspected with a self-signed certificate. Users without a copy of this certificate see a certificate warning when they connect to a secure web site with HTTPS. If the remote web site uses a certificate that is expired, or if the certificate is signed by a CA (Certificate Authority) the XTM device does not recognize, the XTM device re-signs the content as Fireware HTTPS Proxy: Unrecognized Certificate. If your organization already has a PKI (Public Key Infrastructure) set up with a trusted CA, then you can import a certificate on the XTM device that is signed by your organization. If your organization does not have a PKI, we recommend that you copy the default, self-signed certificate from the XTM device to each client device. This document includes information about how to export a certificate from the XTM device and import it on a Microsoft Windows or Mac OS X system. To import the certificate on other devices, operating systems, or applications, see the documentation from their manufacturers. For more information about how to use certificates with Policy Manager, see About Certificates. For more information about how to use certificates with the Fireware XTM Web UI, see About Certificates.
Answer
Before You Begin
We recommend that you provide the certificate(s) used to sign HTTPS traffic to all of the clients on your network before you enable this feature. You can attach the certificates to an email with instructions, or use network management software to install the certificates automatically. Also, we recommend that you test the HTTPS-proxy with a small number of users to ensure that it operates correctly before you apply the HTTPS-proxy to traffic on a large network.
Configure the HTTPS-proxy
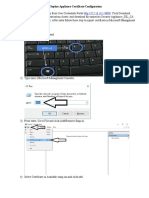
From Policy Manager 1. Select Edit > Add Policy.
The Add Policies dialog box appears.
2. Expand the Proxies category and select HTTPS-proxy. Click Add.
The New Policy Properties dialog box appears, with the Policy tab selected.
3. Adjacent to the Proxy Action drop-down list, click the View/Edit Proxy button.
The HTTPS Proxy Action configuration dialog box appears, with the Content Inspection category selected.
4. On the Content Inspection page, select the Enable deep inspection of HTTPS content check box. 5. From the Proxy Action drop-down list, select an HTTP-proxy action to use to inspect HTTPS content, or create a new HTTP-proxy action to use for this policy. 6. In the Certificate Validation section, select the options for OCSP certificate validation. 7. In the Bypass List text box, type the IP address a of web site for which you do not want to inspect traffic. Click Add.
The IP address appears in the Bypass List.
8. (Optional) Repeat Step 7 to add more IP addresses to the Bypass List.
http://customers.watchguard.com/articles/Article/3209/p?pubstatus=o
9/30/2011
Knowledge Articles & Software
Page 2 of 4
9. Click OK to close the HTTPS Proxy Action Configuration dialog box. 10. Click OK to close the New Policy Properties dialog box. 11. Click Closeto close the Add Policies dialog box. From Fireware XTM Web UI First, edit an HTTPS-proxy action to enable deep content inspection of HTTPS content. 1. Select Firewall > Proxy Actions.
The Proxy Actions page appears.
2. Select an HTTPS proxy action: HTTPS-Client or HTTPS-Server. Click Edit.
The Edit Proxy Action page appears for the proxy action you selected.
3. Expand the Content Inspection section. 4. Select the Enable deep inspection of HTTPS content check box. 5. From the Proxy Action drop-down list, select the HTTP-proxy action to use to inspect HTTPS content. For example, HTTP-Client. 6. Clear the Use OCSP to confirm the validity of certificates check box. 7. In the Bypass List text box, type the IP address of a web site for which you do not want to inspect traffic. Click Add. 8. (Optional) Repeat Step 7 to add more IP addresses to the Bypass List. 9. Click Save.
If you edited a predefined proxy action, you must clone your changes to a new proxy action before you can save them and apply them to a proxy policy. The Clone Proxy Action dialog box appears.
10. In the Name text box, type a new name for the proxy action. For example, type HTTPS-Client DCI. 11. Click OK.
The new proxy action appears in the Proxies list.
Next, add an HTTPS-proxy that uses the proxy action you added. 1. Select Firewall > Firewall Policies.
The Firewall Policies page appears.
2. Click the green plus icon.
The Select a Policy Type page appears.
3. Expand the Proxies category and select HTTPS-proxy. 4. Click Add policy.
The Policy Configuration page appears for the HTTPS-proxy.
5. From the Proxy Action drop-down list, select the proxy action you added. For example, select HTTPS-Client DCI. 6. Click Save.
Export the Certificate
This procedure exports a certificate from your XTM device in PEM format. You cannot use Fireware XTM Web UI to export a certificate. You must use Firebox System Manager (FSM). 1. 2. 3. 4. 5. Start Firebox System Manager for your XTM device. Select View > Certificates. Select the HTTPS Proxy Authority CA certificate from the list and click Export. Type a name and select a location to save the certificate locally. Copy the saved certificate to the client machine.
If you have previously imported the certificate on a client, you can export that certificate directly from operating system or browser certificate store. In most cases, this exports the certificate in the x.509 format. Windows and Mac OS X users can double-click an x.509 format certificate to import it.
Import a PEM Format Certificate with Windows XP
This process allows Internet Explorer, Windows Update, and other programs or services that use the Windows certificate store on Microsoft Windows XP to get access to the certificate. 1. From the Windows Start Menu, select Run. Type mmc and click OK.
A Windows Management Console appears.
http://customers.watchguard.com/articles/Article/3209/p?pubstatus=o
9/30/2011
Knowledge Articles & Software
Page 3 of 4
Select File > Add/Remove Snap-In. Click Add. Select Certificatesand click Add. Select Computer account and click Next. Click Finish, Close, and OK to add the certificates module. In the Console Root window, click the plus icon [+] to expand the Certificates tree. Expand the Trusted Root Certification Authorities object. 8. Under the Trusted Root Certification Authorities object, right-click Certificates and select All Tasks > Import. 9. Click Next. Click Browse to find and select the HTTPS Proxy Authority CA certificate you previously exported. Click OK. 10. Click Next, then clickFinish to complete the wizard.
2. 3. 4. 5. 6. 7.
Import a PEM Format Certificate with Windows Vista
This process allows Internet Explorer, Windows Update, and other programs or services that use the Windows certificate store on Microsoft Windows Vista to get access to the certificate. 1. On the Windows Start Menu, type certmgr.msc in the Search text box and press Enter.
If you are prompted to authenticate as an administrator, type your password or confirm your access.
2. Select the Trusted Root Certification Authorities object. 3. From the Action menu, select All Tasks > Import. 4. Click Next. Click Browse to find and select the HTTPS Proxy Authority CA certificate you previously exported. Click OK. 5. Click Next, then click Finish to complete the wizard.
Import a PEM Format Certificate with Mozilla Firefox 3.x
Mozilla Firefox uses a private certificate store instead of the operating system's certificate store. If clients on your network use the Firefox browser, you must import the certificate into the Firefox certificate store even if you have already imported the certificate on the host operating system. When you have more than one XTM device that uses a self-signed certificate for HTTPS content inspection, clients on your network must import a copy of each XTM device certificate. However, the default self-signed XTM device certificates use the same name, and Mozilla Firefox only recognizes the first certificate you import when more than one certificate has the same name. We recommend that you replace the default self-signed certificates with a certificate signed by a different CA, and then distribute those CA certificates to each client. 1. From the Firefox menu bar, select Tools > Options.
The Options window appears.
2. Click Advanced. 3. Select the Encryption tab and click View Certificates.
The Certificate Manager window appears.
4. Select the Authorities tab, then click Import. 5. Browse to and select the certificate file and click Open. 6. On the Downloading Certificate dialog box, select the Trust this CA to identify web sites check box and click OK. 7. Click OK twice to close the Certificate Manager and Options dialog boxes. 8. Restart Mozilla Firefox.
Import a PEM Format Certificate with Mac OS X 10.5
This process allows Safari and other programs or services that use the Mac OS X certificate store to get access to the certificate. 1. 2. 3. 4. Open the Keychain Access application. Select the Certificates category from the list on the left side of the window. Click the plus icon on the lower toolbar, then find and select the certificate. Select the System keychain, then click Open. Or, you can select the System keychain and drag and drop the certificate file into the list.
http://customers.watchguard.com/articles/Article/3209/p?pubstatus=o
9/30/2011
Knowledge Articles & Software
Page 4 of 4
5. Right-click the certificate and select Get Info.
A certificate information window appears.
6. Expand the Trust category. From the When using this certificate drop-down list, select Always Trust. 7. Close the certificate information window. 8. Type your administrator password to confirm your changes. For more information about how to use certificates with FSM, see Manage XTM Device Certificates. For more information about how to use certificates with the Web UI, see Manage XTM Device Certificates.
Attachments
http://customers.watchguard.com/articles/Article/3209/p?pubstatus=o
9/30/2011
You might also like
- Customer Tips: Ipsec Client/Server Configuration Using Pre-Shared Keys in Windows EnvironmentsDocument18 pagesCustomer Tips: Ipsec Client/Server Configuration Using Pre-Shared Keys in Windows EnvironmentsSnowdrop HsuNo ratings yet
- SSL, VSTO, and CA Certificate Setup for PeopleSoft nVision DrillDownDocument2 pagesSSL, VSTO, and CA Certificate Setup for PeopleSoft nVision DrillDownsendram1No ratings yet
- Deploying Scom Gateway ServerDocument10 pagesDeploying Scom Gateway Servernaveednezam2686No ratings yet
- Reference Materials: Help With Prosystem ScanDocument8 pagesReference Materials: Help With Prosystem ScanJeremy McFerrinNo ratings yet
- CP E80.50 EPSVPNWindows UserGuideDocument16 pagesCP E80.50 EPSVPNWindows UserGuideSeto JoselesNo ratings yet
- Using A Certificate For The HTTPS ProtocolDocument17 pagesUsing A Certificate For The HTTPS ProtocolAryanNo ratings yet
- SSL Decryption Certificates TN RevCDocument7 pagesSSL Decryption Certificates TN RevCChau NguyenNo ratings yet
- Checkpoint NGX Secure Mote Secure ClientDocument43 pagesCheckpoint NGX Secure Mote Secure ClientHebert MolinaNo ratings yet
- PitDocument3 pagesPitdibiyaNo ratings yet
- ProxySG UBL Issue ReportDocument6 pagesProxySG UBL Issue ReportatherNo ratings yet
- Install SSL Certificate IIS 7 in Under 2 MinutesDocument6 pagesInstall SSL Certificate IIS 7 in Under 2 MinutesEzzyOrwobaNo ratings yet
- System Requirements & Settings ManualDocument14 pagesSystem Requirements & Settings ManualfaisalNo ratings yet
- CA Server Using Certificates and SSL in Windows: Student Name: Aishpreet Sran UID:18BCS2835 Section/Group: CSE-17/BDocument6 pagesCA Server Using Certificates and SSL in Windows: Student Name: Aishpreet Sran UID:18BCS2835 Section/Group: CSE-17/BAFAQ CUNo ratings yet
- Global ProtectDocument15 pagesGlobal ProtectArun SomashekarNo ratings yet
- SI50 UserGuide InventoryServer APPENDIXDocument8 pagesSI50 UserGuide InventoryServer APPENDIXmat wueNo ratings yet
- Install and Configure FortiGate Default CertificateDocument3 pagesInstall and Configure FortiGate Default CertificatePravin100% (1)
- Symantec CryptoExec For WHMCS - Installation and Management GuideDocument14 pagesSymantec CryptoExec For WHMCS - Installation and Management GuideKalpesh PatelNo ratings yet
- How To Connect To EPRS - (Updated)Document33 pagesHow To Connect To EPRS - (Updated)Mondeh Albero100% (1)
- Create Windows CA Certificate Templates For CUCMDocument32 pagesCreate Windows CA Certificate Templates For CUCMDavid Van HerckNo ratings yet
- Establishing two-factor authentication with Juniper SSL VPN and Celestix HOTPinDocument6 pagesEstablishing two-factor authentication with Juniper SSL VPN and Celestix HOTPinputakoNo ratings yet
- Content Filtering SolutionDocument16 pagesContent Filtering SolutionAnonymous NWFB3TNo ratings yet
- Configure Multi-FactorDocument27 pagesConfigure Multi-FactorTran ThangNo ratings yet
- 21.4.7 Lab - Certificate Authority StoresDocument7 pages21.4.7 Lab - Certificate Authority StoresLISS MADELEN TRAVEZ ANGUETANo ratings yet
- 17.2.7 Lab - Certificate Authority StoresDocument7 pages17.2.7 Lab - Certificate Authority StoresntutaNo ratings yet
- Connecting IoT Gateway MQTT To AWS KSEDocument5 pagesConnecting IoT Gateway MQTT To AWS KSEsyifa hananiaNo ratings yet
- 9.2.2.7 Lab - Certificate Authority Stores PDFDocument9 pages9.2.2.7 Lab - Certificate Authority Stores PDFInteresting facts ChannelNo ratings yet
- Deploying Web Server Certificate For Site SystemsDocument18 pagesDeploying Web Server Certificate For Site SystemsLaeeqSiddiquiNo ratings yet
- EOffice DSC Signer ServicesDocument2 pagesEOffice DSC Signer ServicesstjhsstNo ratings yet
- Configure Windows RADIUS ServerDocument7 pagesConfigure Windows RADIUS Serveraami145No ratings yet
- Práctica de Laboratorio 21.4.7Document9 pagesPráctica de Laboratorio 21.4.7rojas.saldana.armando.sptmNo ratings yet
- How To Connect To EPRS - Guidelines For New and Existing Users (Updated)Document33 pagesHow To Connect To EPRS - Guidelines For New and Existing Users (Updated)Kim Andales62% (29)
- Palo Alto - How To Configure Captive PortalDocument17 pagesPalo Alto - How To Configure Captive PortalDanny MannoNo ratings yet
- Module 4 Implementing VPN PDFDocument7 pagesModule 4 Implementing VPN PDFAfendey ArthurNo ratings yet
- SBAG8704 B - SecureLink v3.2.4 - 2020 03 28 - 2 PDFDocument17 pagesSBAG8704 B - SecureLink v3.2.4 - 2020 03 28 - 2 PDFNguyễn Đức LâmNo ratings yet
- Pedestrian Dynamics Installation GuideDocument12 pagesPedestrian Dynamics Installation GuideMohamed El AmeliNo ratings yet
- Certificate MGMT Guide PDFDocument12 pagesCertificate MGMT Guide PDFLeeanne BillingsNo ratings yet
- WWW - tcs-CA - Tcs.co - in Index - JSP LeftHtml HTML Faqsleft - HTDocument9 pagesWWW - tcs-CA - Tcs.co - in Index - JSP LeftHtml HTML Faqsleft - HTsumitsemwalNo ratings yet
- Sign A CA Certificate On Windows Server 2008 and Import The Certificate For SSL InspectionDocument6 pagesSign A CA Certificate On Windows Server 2008 and Import The Certificate For SSL Inspectionm0nsysNo ratings yet
- Paloalto Networks Cybersecurity Academy Essentials IiDocument10 pagesPaloalto Networks Cybersecurity Academy Essentials IiLena GlazkovaNo ratings yet
- How To Setup Up VPN Connection PDFDocument8 pagesHow To Setup Up VPN Connection PDFsuhaib asimNo ratings yet
- Install SSL Certificate on Tomcat ServerDocument13 pagesInstall SSL Certificate on Tomcat Serverbhaip123No ratings yet
- SOPHOS CertificateDocument12 pagesSOPHOS CertificateHanna SNo ratings yet
- Technical Brief Enabling NTLM AuthenticationDocument4 pagesTechnical Brief Enabling NTLM AuthenticationsasNo ratings yet
- Mcafee Epo 4.0 DocumentationDocument36 pagesMcafee Epo 4.0 DocumentationVineeth BarathNo ratings yet
- Forticlient VPN SOP - EcospaceDocument15 pagesForticlient VPN SOP - EcospaceAkash RaiNo ratings yet
- Guide To Install The SSL Certificate in Admanager PlusDocument5 pagesGuide To Install The SSL Certificate in Admanager PlusJayavignesh ZohoNo ratings yet
- McAfee ApplicationsDocument6 pagesMcAfee ApplicationsDilbar DeewanaNo ratings yet
- How To Install Third Party SSL Certificates For IPSec VPNDocument15 pagesHow To Install Third Party SSL Certificates For IPSec VPNmartinhache2014No ratings yet
- Create and Import SSL Certs for Canon MFPsDocument5 pagesCreate and Import SSL Certs for Canon MFPsBükkös Alpár RobertNo ratings yet
- Configuring OpenID Connect AuthenticationDocument9 pagesConfiguring OpenID Connect AuthenticationkrishnamurthyyadavNo ratings yet
- Iot Gateway MQTT Client Microsoft AzureDocument6 pagesIot Gateway MQTT Client Microsoft Azuremrl1307No ratings yet
- 1 Downloading Installation and Backup of Digital Certificates With User Generated Password Using Mozilla Firefox v.2Document15 pages1 Downloading Installation and Backup of Digital Certificates With User Generated Password Using Mozilla Firefox v.2JAHYRAH BARTOLOMENo ratings yet
- Configure SMIME On WorxMail For IOSDocument27 pagesConfigure SMIME On WorxMail For IOSstrokenfilledNo ratings yet
- Securing Communication of Legacy Applications with IPSec: Step-by-Step Guide to Protecting “Data in Transit” without Changes in Your Existing SoftwareFrom EverandSecuring Communication of Legacy Applications with IPSec: Step-by-Step Guide to Protecting “Data in Transit” without Changes in Your Existing SoftwareNo ratings yet
- SSL VPN : Understanding, evaluating and planning secure, web-based remote accessFrom EverandSSL VPN : Understanding, evaluating and planning secure, web-based remote accessNo ratings yet
- Hiding Web Traffic with SSH: How to Protect Your Internet Privacy against Corporate Firewall or Insecure WirelessFrom EverandHiding Web Traffic with SSH: How to Protect Your Internet Privacy against Corporate Firewall or Insecure WirelessNo ratings yet
- Securing Application Deployment with Obfuscation and Code Signing: How to Create 3 Layers of Protection for .NET Release BuildFrom EverandSecuring Application Deployment with Obfuscation and Code Signing: How to Create 3 Layers of Protection for .NET Release BuildNo ratings yet
- ETHICAL HACKING GUIDE-Part 3: Comprehensive Guide to Ethical Hacking worldFrom EverandETHICAL HACKING GUIDE-Part 3: Comprehensive Guide to Ethical Hacking worldNo ratings yet
- No Cost Contract Automation: Create a digital contract lifecycle management system using Microsoft 365From EverandNo Cost Contract Automation: Create a digital contract lifecycle management system using Microsoft 365No ratings yet
- Wireless Network MikrotikDocument36 pagesWireless Network MikrotikMarco Nm Martinez AndradeNo ratings yet
- Gek 113511B PDFDocument192 pagesGek 113511B PDFprabhu_natarajan_nNo ratings yet
- Engg Drawing MCQDocument93 pagesEngg Drawing MCQPraveen Dwivedi100% (1)
- Gian Multiphysics VK MPDocument2 pagesGian Multiphysics VK MPmohanNo ratings yet
- 8259A Programmable Interrupt Controller (8259A/8259A-2) : (See Packaging Spec., Order 231369)Document35 pages8259A Programmable Interrupt Controller (8259A/8259A-2) : (See Packaging Spec., Order 231369)Renit AntoNo ratings yet
- HDHDocument45 pagesHDHsiva kumarNo ratings yet
- Parallel ProcessingDocument6 pagesParallel Processingrnsys2001No ratings yet
- Cloud Router Switch Series: Setup Guide and Warranty InformationDocument3 pagesCloud Router Switch Series: Setup Guide and Warranty InformationyankurokuNo ratings yet
- LibreOffice Impress 7.0 GuideDocument331 pagesLibreOffice Impress 7.0 GuideFlavioRodolfoSeveroNo ratings yet
- TANGAZO LA KAZI MTUWASA, Na TAPANA 26 JANUARI 21Document7 pagesTANGAZO LA KAZI MTUWASA, Na TAPANA 26 JANUARI 21Alex MaugoNo ratings yet
- AS400 Command DSPDocument158 pagesAS400 Command DSPAdi FangNo ratings yet
- Manual BPLA PDFDocument78 pagesManual BPLA PDFIsacc AlvesNo ratings yet
- Your Journey To SAP S - 4HANA A Practical Guide - SAP BlogsDocument11 pagesYour Journey To SAP S - 4HANA A Practical Guide - SAP Blogsbravinod100% (1)
- SSHDocument10 pagesSSHSanju NaikNo ratings yet
- Performance Task in Ict 9Document6 pagesPerformance Task in Ict 9Spongie BobNo ratings yet
- Chapter 13 - Introduction To Classes: Starting Out With C++, 3 EditionDocument80 pagesChapter 13 - Introduction To Classes: Starting Out With C++, 3 EditionGurdarshan Singh SinghNo ratings yet
- Chapter 8Document12 pagesChapter 8Fatima Tul ZahraNo ratings yet
- Index Match Basics Excel Free WorkBook XelplusDocument4 pagesIndex Match Basics Excel Free WorkBook Xelplusmatho_2013No ratings yet
- Excal 2023Document45 pagesExcal 2023sahil ChaudharyNo ratings yet
- Flare To TspecFlaretotDocument5 pagesFlare To TspecFlaretotlaminarsNo ratings yet
- Competitor Analysis For MinisDocument17 pagesCompetitor Analysis For Minismariam.ayman1810No ratings yet
- Enjoyyourstudy Com Gniit Sem D Mt1 Exam QuestionDocument36 pagesEnjoyyourstudy Com Gniit Sem D Mt1 Exam QuestionMohit BhansaliNo ratings yet
- Data Science - PythonDocument30 pagesData Science - PythonnikhithaNo ratings yet
- Exam Request or Nomination FormDocument4 pagesExam Request or Nomination FormMohammad NizamuddinNo ratings yet
- 3 Class: Microprocessors Lab Introduction To Debugger: The Intel Corporation's 8086 MicroprocessorDocument10 pages3 Class: Microprocessors Lab Introduction To Debugger: The Intel Corporation's 8086 MicroprocessorMamounNo ratings yet
- Gpucoder UgDocument560 pagesGpucoder UgciaobubuNo ratings yet
- Websphere Application Server Liberty Profile Guide For DevelopersDocument240 pagesWebsphere Application Server Liberty Profile Guide For DevelopersedyNo ratings yet
- Resume Yogeshwaran SDocument2 pagesResume Yogeshwaran Sbharathks641No ratings yet