Professional Documents
Culture Documents
Bobi 4.0 Single Sign On - Sso
Uploaded by
Bashir AwanOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Bobi 4.0 Single Sign On - Sso
Uploaded by
Bashir AwanCopyright:
Available Formats
Windows AD Single Sign On
Firstly, lets define our server names and IPs (you must obviously adjust these and the commands below to reflect your server names and IPs:
Domain Name: DOMAIN (FQDN: DOMAIN.SITE) Service Account: bobjbiuser (password: Password1) Domain Controller: <DC>.<DOMAIN.SITE> BusinessObjects Server: <BI Server>.<DOMAIN.SITE> BusinessObjects AD Group: DOMAIN\UserGroup
Step 1 Create an Active Directory service account, bobjbiuser (password: Password1). Ensure the user config has Password never expires option checked on. On the BusinessObjects server, add the DOMAIN/bobjbiuser user to the Local Administrators group. Also assign the bobjbiuser user the right Act as part of Operating System in the Local Security Policy snap-in. Step 2 Run the following command on the Active Directory server to create appropriate Service Principal Names (SPNs):
setspn -a BICMS/bobjbiuser. <DOMAIN.SITE> bobjbiuser setspn -a HTTP/<BI Server> bobjbiuser setspn -a HTTP/<BI Server>.<DOMAIN.SITE> bobjbiuser
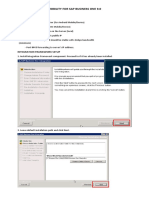
Verify the SPNs have been created by running setspn -l bobjbiuser. Step 3 Change the user config of bobjbiuser user in Active Directory configuration, and under the Delegation tab, turn on Trust this user for delegation to any service (Kerberos only). Step 4 Under the AD Authentication area in the Central Management Console, take the following actions:
Enable Windows Active Directory (AD) AD Administration Name = <DOMAIN>\bobjbiuser Default AD Domain: <DOMAIN.SITE> Add AD Group:< DOMAIN>\UserGroup Use Kerberos Authentication Service principal name = BICMS/bobjbiuser. <DOMAIN.SITE>
Enable Single Sign On for selected authentication mode
Click Save to save all your entries. Check under the Groups area to make sure your AD group has been added. Step 5 Modify the Server Intelligence Agent (SIA) process on the BusinessObjects server to run as the <DOMAIN>\bobjbiuser user. a. b. c. d. Stop SIA RMC on SIA and Properties Go to configuration Under Log on as enter your credential e. User: DOMAIN\bobjbiuser and password f. Click OK and start the service Step 6 Test this by logging into Web Intelligence Rich Client by using an AD user who is part of the group. SSO should occur once you select Windows AD authentication and click OK (no need to input your username or password). Step 7 Create a file called bscLogin.conf, save it into C:\Windows\ directory on the BusinessObjects server, and put the following content into it using Notepad: com.businessobjects.security.jgss.initiate { com.sun.security.auth.module.Krb5LoginModule required debug=true; }; Create a file called krb5.ini, save it into C:\Windows\ directory, and put the following content into it using Notepad: [libdefaults] default_realm = <DOMAIN.SITE> dns_lookup_kdc = true dns_lookup_realm = true default_tgs_enctypes = rc4-hmac default_tkt_enctypes = rc4-hmac udp_preference_limit = 1 [realms] DOMAIN.SITE ={ kdc = ADSERVER.DOMAIN.SITE default_domain = <DOMAIN.SITE>
} Verify this file is completed correctly by navigating to <BI Folder>\SAP BusinessObjects\SAP BusinessObjects Enterprise XI 4.0\win64_x64\jdk\bin\ folder on the BusinessObjects server, and execute kinit bobjbiuser in a command prompt. If a new ticket is stored, the file is correct. Step 8 Stop Tomcat. Modify the BI Launch Pads .properties file to reveal the authentication dropdown. Navigate to <BI Folder>\SAP BusinessObjects\Tomcat6\webapps\BOE\WEB-INF\custom and create a file called BIlaunchpad.properties with the following text: authentication.visible=true authentication.default=secWinAD Open up the Tomcat Options, and add the following lines to the Tomcat Java Options: a. Start > Tomcat > Tomcat Configuration b. Go to Java Tab c. Enter the following code under Java Option at the end or previously entered commands (Dont delete previous commands d. Click Apply -Djava.security.auth.login.config=c:\windows\bscLogin.conf -Djava.security.krb5.conf=c:\windows\krb5.ini Start Tomcat, then try and do a manual logon to BusinessObjects, and check Tomcat trace logs for a commit succeeded. Step 9 Stop Tomcat. Modify <BI >\SAP BusinessObjects\Tomcat6\conf\server.xml, by adding maxHttpHeaderSize=65536 in Connector Port 8080 tag. Navigate to E:\Program Files (x86)\SAP BusinessObjects\Tomcat6\webapps\BOE\WEBINF\config\custom and create a file called global.properties with the following text: sso.enabled=true siteminder.enabled=false vintela.enabled=true idm.realm=DOMAIN.SITE idm.princ=bobjbiuser idm.allowUnsecured=true idm.allowNTLM=false idm.logger.name=simple idm.logger.props=error-log.properties
Open up Tomcat Options Add the following lines to Tomcat Java Options: -Dcom.wedgetail.idm.sso.password=Password1 -Djcsi.kerberos.debug=true Delete logs in E:\Program Files (x86)\SAP BusinessObjects\Tomcat6\logs\ and C:\SBOPWebapp_BIlaunchpad_IP_PORT\. Start Tomcat, go to E:\Program Files (x86)\SAP BusinessObjects\Tomcat6\logs\, check stdout.log has credentials obtained shown. Test silent single sign on is now working in a browser (not on the BusinessObjects server). Step 10 Copy BIlaunchpad.properties and global.properties from E:\Program Files (x86)\SAP BusinessObjects\Tomcat6\webapps\BOE\WEB-INF\config\custom to E:\Program Files (x86)\SAP BusinessObjects\SAP BusinessObjects Enterprise XI 4.0\warfiles\webapps\BOE\WEBINF\config\custom so that patches dont overwrite them and SSO stops working. Step 11 Create a keytab on the AD server by running the following command: ktpass -out bosso.keytab -princ bobjbiuser@DOMAIN.SITE -pass Password1 -kvno 255 -ptype KRB5_NT_PRINCIPAL -crypto RC4-HMAC-NT Copy this file to c:\windows of BOBJ server. Stop Tomcat. Add the following line to E:\Program Files (x86)\SAP BusinessObjects\Tomcat6\webapps\BOE\WEB-INF\config\custom\global.properties idm.keytab=C:/WINDOWS/bosso.keytab Open up the Tomcat Configuration, remove the Wedgetail line in Java Options, restart tomcat and make sure credentials obtained still showing up in stdout.log. Now check silent single sign on still operating correctly. Step 12 Remove debug=true from the C:\windows\bscLogin.conf file, and also remove the debugging line Djcsi.kerberos.debug=true Java Options in Tomcat Configuration.
a. b. c. d.
Stop Tomcat RMC on Tomcat and click Properties Go to Java tab Remove debug = true from there
Other information Detailed troubleshooting and best practices can be found in KBA 1476374 How to enable trace logging for BI40 Web applications found in KBA 1613472 For manual logon use http://server:PORT/BOE/BI/logonNoSso.jsp
You might also like
- How To Configure AD SSO For AAO With BI 4.0Document1 pageHow To Configure AD SSO For AAO With BI 4.0mannadas206No ratings yet
- Configuring SAP SSODocument13 pagesConfiguring SAP SSODaniel WoodNo ratings yet
- Ovr Installation 1Document28 pagesOvr Installation 1ShuBham SinGhNo ratings yet
- DD InstallationDocument7 pagesDD InstallationT VandanaNo ratings yet
- Install and Configure SAP BPC 7.5Document8 pagesInstall and Configure SAP BPC 7.5Rama Krishna MullapudiNo ratings yet
- How To Reset The Administrator Password in Business Intelligence Platform 4Document3 pagesHow To Reset The Administrator Password in Business Intelligence Platform 4Iheanyi AcharekeNo ratings yet
- Mobility For Sap Business One 9.0: Integration Framework SetupDocument13 pagesMobility For Sap Business One 9.0: Integration Framework SetupRobeth John BacalanNo ratings yet
- Configuring Domino With IISDocument7 pagesConfiguring Domino With IISdeepuwasNo ratings yet
- Integration of BW in SAP EPDocument20 pagesIntegration of BW in SAP EPJuan Carlos FloresNo ratings yet
- Technote Wna Sso Ad v4.0Document36 pagesTechnote Wna Sso Ad v4.0shivanagendra koyaNo ratings yet
- AST-0054634 AdobeColdFusion9ServerLockdownGuideDocument35 pagesAST-0054634 AdobeColdFusion9ServerLockdownGuidedruvame8398No ratings yet
- Obi SsoDocument31 pagesObi Ssokevinchristee21No ratings yet
- IIS Setups - Dynamics AX Workflow WanderingsDocument13 pagesIIS Setups - Dynamics AX Workflow WanderingsTilak RajuNo ratings yet
- Netbackup Basic TroubleshootingDocument10 pagesNetbackup Basic TroubleshootingWaqas Asghar SipraNo ratings yet
- Cognos Installation and Configuration SimplifiedDocument45 pagesCognos Installation and Configuration SimplifiedSuman JhaNo ratings yet
- SSO Between Ep To Bo & Sap Bo To BWDocument16 pagesSSO Between Ep To Bo & Sap Bo To BWrajendraNo ratings yet
- Lab: 5. Creating A Boot - Properties Properties For Managed ServerDocument1 pageLab: 5. Creating A Boot - Properties Properties For Managed ServervssprpvemuriNo ratings yet
- Step by Step Installation of Microsoft Dynamics 365 Finance and Operations On Premise by Umesh Pandit PDFDocument75 pagesStep by Step Installation of Microsoft Dynamics 365 Finance and Operations On Premise by Umesh Pandit PDFTilak Raju100% (1)
- Installing Community Surveys in Connections 5.5Document18 pagesInstalling Community Surveys in Connections 5.5Charina De la CruzNo ratings yet
- Server Tracing Using The BO - Trace - Ini File in XI3.1Document4 pagesServer Tracing Using The BO - Trace - Ini File in XI3.1srivardanNo ratings yet
- Active Directory Integration: SAGE Computing ServicesDocument45 pagesActive Directory Integration: SAGE Computing ServicesUday KiranNo ratings yet
- Examen Password SafeDocument17 pagesExamen Password SafeheisembergNo ratings yet
- AMIT3023 Web Application Programming Practical Exercise 7Document12 pagesAMIT3023 Web Application Programming Practical Exercise 7dydre hooiNo ratings yet
- Configuring BIApps 11.1.1.10.1 ExternalLDAP AuthenticationDocument3 pagesConfiguring BIApps 11.1.1.10.1 ExternalLDAP AuthenticationAsad HussainNo ratings yet
- (TUTORIAL) How To Enhance Your IIS Server Security With Client Certificates - TDocument11 pages(TUTORIAL) How To Enhance Your IIS Server Security With Client Certificates - TAlexandarNo ratings yet
- Answer: B: Exam Name: Exam Type: Exam Code: Total QuestionsDocument9 pagesAnswer: B: Exam Name: Exam Type: Exam Code: Total QuestionsprepcramNo ratings yet
- Configure Windows AD Authentication For Business Object Enterprise XI 3.1Document10 pagesConfigure Windows AD Authentication For Business Object Enterprise XI 3.1kphwnNo ratings yet
- ExchangeDocument4 pagesExchangeMarcos SachiNo ratings yet
- Setting Up Workflow Adaper - FileDocument4 pagesSetting Up Workflow Adaper - Filenilesh.patidar87No ratings yet
- Cloud Natural LanguageDocument1 pageCloud Natural LanguageDenys StolbovNo ratings yet
- Configure AD FS and DRS for SSODocument7 pagesConfigure AD FS and DRS for SSOAlgirdas SakalauskasNo ratings yet
- TIBCO BusinessWorksTM: Understanding Web Services Security configurationDocument2 pagesTIBCO BusinessWorksTM: Understanding Web Services Security configurationsenthur123No ratings yet
- Claims Walkthrough: Creating Forms-Based Authentication For Claims-Based Sharepoint 2010 Web Applications Role ProvidersDocument24 pagesClaims Walkthrough: Creating Forms-Based Authentication For Claims-Based Sharepoint 2010 Web Applications Role Providerseleazar_lostNo ratings yet
- SUM408-Configuring and Troubleshooting XenDesktop SitesDocument69 pagesSUM408-Configuring and Troubleshooting XenDesktop Siteskinan_kazuki104No ratings yet
- Endpoint Troubleshooting Steps-1Document7 pagesEndpoint Troubleshooting Steps-1FLybYbYNo ratings yet
- Administer Microsoft 70-411 ExamDocument28 pagesAdminister Microsoft 70-411 Examsmile2meguysNo ratings yet
- 70-410 10022014Document433 pages70-410 10022014Pabalelo Gaofenngwe Sefako100% (1)
- Killtest: Examen ExamenDocument11 pagesKilltest: Examen ExamenRoberto Moncada LopezNo ratings yet
- lIIS Server Configuration For Record Retrieval - Version 6.0 Instructions Made On Windows Server 2003Document6 pageslIIS Server Configuration For Record Retrieval - Version 6.0 Instructions Made On Windows Server 2003Harish Chary VutaplaNo ratings yet
- SCCM Home LabDocument11 pagesSCCM Home Labpeddareddy100% (1)
- How To Setup and Configure Commerce Data Exchange Real-Time ServiceDocument12 pagesHow To Setup and Configure Commerce Data Exchange Real-Time ServiceIslam SultanNo ratings yet
- Business Intelligence Publisher New Features GuideDocument26 pagesBusiness Intelligence Publisher New Features GuideMadasamy MurugaboobathiNo ratings yet
- Deploying the BSSV package to BSSV serverDocument10 pagesDeploying the BSSV package to BSSV serverAnonymous rOv67RNo ratings yet
- Setting Up BI in Netweaver 7.0 ABAP Trial VersionDocument4 pagesSetting Up BI in Netweaver 7.0 ABAP Trial Versionhunter.correaNo ratings yet
- Cognos Controller - Active Directory and Single Sign OnDocument8 pagesCognos Controller - Active Directory and Single Sign OntdsrogersNo ratings yet
- Configuring Security For Mobile Devices: This Lab Contains The Following Exercises and ActivitiesDocument10 pagesConfiguring Security For Mobile Devices: This Lab Contains The Following Exercises and ActivitiesMD4733566No ratings yet
- 1053 ConfiguringWebServicesTransformationinInformaticaCloudtoReadDatafromSAPBWBExQuery H2L PDFDocument10 pages1053 ConfiguringWebServicesTransformationinInformaticaCloudtoReadDatafromSAPBWBExQuery H2L PDFLion RoarNo ratings yet
- Win Server ChecklistDocument10 pagesWin Server ChecklistEduardo MorenoNo ratings yet
- Integrating OAM 11.1.2.3 with Microsoft Outlook Web Access (OWA) 2013Document4 pagesIntegrating OAM 11.1.2.3 with Microsoft Outlook Web Access (OWA) 2013Ashutosh NichatNo ratings yet
- How To Setup SAP N/W SSO With X/509 CertificatesDocument34 pagesHow To Setup SAP N/W SSO With X/509 CertificatesvenukantiNo ratings yet
- IIS 7: The Administrator's Guide: Alexis Eller Program Manager Microsoft CorporationDocument44 pagesIIS 7: The Administrator's Guide: Alexis Eller Program Manager Microsoft Corporationnishasaiyed2304No ratings yet
- RBS FILESTREAM Installation For Sharepoint 2013Document6 pagesRBS FILESTREAM Installation For Sharepoint 2013Hikari0601No ratings yet
- Importing BIAR File Using BICONFIG UtilityDocument3 pagesImporting BIAR File Using BICONFIG UtilityjacNo ratings yet
- 70-533 Paper 2Document184 pages70-533 Paper 2kiraak41No ratings yet
- Windows SSLDocument6 pagesWindows SSLSiddhant DhanveNo ratings yet
- 70-411 Exam QuestionsDocument82 pages70-411 Exam QuestionsBogdanDirzan100% (1)
- Installation and Configuration of IBM FileNet Information Management Software: A step-by-step guide to installing and configuring IBM FileNet ECM and Case Manager on RHEL 8.0 (English Edition)From EverandInstallation and Configuration of IBM FileNet Information Management Software: A step-by-step guide to installing and configuring IBM FileNet ECM and Case Manager on RHEL 8.0 (English Edition)No ratings yet
- VmwareDocument199 pagesVmwareKishore_S_Nair_2393No ratings yet
- ESA Microprocessor Monitor CommandsDocument22 pagesESA Microprocessor Monitor CommandsMa LathiNo ratings yet
- Abhishek Nandepu ResumeDocument2 pagesAbhishek Nandepu Resumeapi-583820454No ratings yet
- MicroVAX II 630QB Technical ManualDocument160 pagesMicroVAX II 630QB Technical ManualBernhardNo ratings yet
- 800 GigaCenter Release Notes R12.2.7Document26 pages800 GigaCenter Release Notes R12.2.7Shawn HolderNo ratings yet
- 2019 Presentation DEM Rocky - cpu.GPUDocument6 pages2019 Presentation DEM Rocky - cpu.GPUJulio SalgadoNo ratings yet
- BINARY NUMBER SYSTEMSDocument63 pagesBINARY NUMBER SYSTEMSPrevenaManiamNo ratings yet
- COM118 Conformance Test Register 61850Document28 pagesCOM118 Conformance Test Register 61850dipenkhandhediyaNo ratings yet
- Aastra 6730i Data SheetDocument2 pagesAastra 6730i Data SheetCristhian HaroNo ratings yet
- Watchguard Cyberark Integration GuideDocument10 pagesWatchguard Cyberark Integration GuideVincenzo PetrucciNo ratings yet
- RHSA1 Day5Document37 pagesRHSA1 Day5Zeinab Abdelghaffar Radwan AbdelghaffarNo ratings yet
- CARAT Pro Updateanleitung ENG - 2019-09-16 - 3.0Document3 pagesCARAT Pro Updateanleitung ENG - 2019-09-16 - 3.0JhonatanNo ratings yet
- ADA Lab ManualDocument34 pagesADA Lab Manualnalluri_08No ratings yet
- RAVENNA ASIO & Core Audio Guide OptimizationDocument36 pagesRAVENNA ASIO & Core Audio Guide OptimizationDavid JacquesNo ratings yet
- VxRail Appliance - VxRail Installation Procedures-VxRail E560 - E560FDocument101 pagesVxRail Appliance - VxRail Installation Procedures-VxRail E560 - E560FLadislauNo ratings yet
- Stop and Wait Protocol Using NS2Document7 pagesStop and Wait Protocol Using NS2miraclesureshNo ratings yet
- EN100 Readme V4 - 26 PDFDocument14 pagesEN100 Readme V4 - 26 PDFiraqnewNo ratings yet
- Resource For TroubleshootingDocument7 pagesResource For Troubleshootingbcalderón_22No ratings yet
- Vmebus 16 Port Asynchronous Communications Multiplexer: 16 PortsDocument5 pagesVmebus 16 Port Asynchronous Communications Multiplexer: 16 PortsErasmo Franco SNo ratings yet
- LogDocument2 pagesLogHein Aung280KNo ratings yet
- Meraki Datasheet Ms125 Series enDocument7 pagesMeraki Datasheet Ms125 Series enblackmamba etti jeanNo ratings yet
- Sep2 Meterview: Energy Measurement and ManagementDocument2 pagesSep2 Meterview: Energy Measurement and ManagementAdil HameedNo ratings yet
- Geh 6700Document292 pagesGeh 6700Anis HamdaneNo ratings yet
- Sample Code For Interfaceing The TLV320AIC1106 Codec With The TMS320C5402 DSPDocument11 pagesSample Code For Interfaceing The TLV320AIC1106 Codec With The TMS320C5402 DSPJeevan ReddyNo ratings yet
- Oracle Database 12c Backup and Recovery Workshop Ed 2Document6 pagesOracle Database 12c Backup and Recovery Workshop Ed 2Manuel ElizaldeNo ratings yet
- Lab 08 Operating SystemsDocument3 pagesLab 08 Operating SystemsNicholas CapassoNo ratings yet
- Speedgoat RequirementsDocument2 pagesSpeedgoat RequirementsshreenandanraoNo ratings yet
- Acr Win InstallDocument46 pagesAcr Win InstallJoyce ShiNo ratings yet
- Dhi-Nvr4108/4116Hs-8P-4Ks2: 8/16 Channel Compact 1U 8poe 4K&H.265 Lite Network Video RecorderDocument3 pagesDhi-Nvr4108/4116Hs-8P-4Ks2: 8/16 Channel Compact 1U 8poe 4K&H.265 Lite Network Video RecorderJimmy Andres Arias TrujilloNo ratings yet
- Shell Automation An Introduction To Bash Shell Scripting: Anoop JohnDocument23 pagesShell Automation An Introduction To Bash Shell Scripting: Anoop JohnDodo winyNo ratings yet