Professional Documents
Culture Documents
Radware Mitigating The Dos/Ddos Threat Whitepaper: Smart Network. Smart Business
Uploaded by
Juan RiveraOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Radware Mitigating The Dos/Ddos Threat Whitepaper: Smart Network. Smart Business
Uploaded by
Juan RiveraCopyright:
Available Formats
Radware Mitigating the DoS/DDoS Threat Whitepaper
Table of Contents
Abstract......................................................................................................................................................3
DDoS is Growing and Evolving ......................................................................................................................3
DDoS Layers of Attack: the Protection Challenges..........................................................................................5
The Radware Approach to Fight the DDoS Threat............................................................................................7
Summary.....................................................................................................................................................9
Smart Network. Smart Business. 2
Radware Mitigating the DoS/DDoS Threat Whitepaper
Abstract
In the era of fast-growing cyber-hacktivism where DDoS attacks are the preferred weapon of mass disruption, a
closer look is required for emerging attack campaigns.
Attackers are getting sophisticated. There are frequent DDoS attack campaigns that disembark directly at the
victims’ IT infrastructure, bypassing managed DDoS protection services.
This paper highlights recent DDoS attacks trends and why they are successful; it then shows why relying on
managed DDoS protection services provides a partial solution against the DDoS threat. This paper also introduces
Radware DDoS protection solution and establishes the need for an on-premises security solution in addition to the
managed DDoS service.
DDoS is Growing and Evolving
Introduction
Cyber-hacktivism has become so prevalent that every online business, financial service, government agency, or
critical infrastructure is likely a target. Financially motivated attackers are still a threat, however their activity is not
on the news since just recently, they have received much less publicity.
Other
Ransom 4%
4%
Angry Users
12%
Competition
7%
Motivation is unknown
50%
Political/Hacktivism
22%
Figure 1: Radware Security Survey 2011: While the “unknown motivation” is still prominent
the most prominent motivation is by far political hacktivism
Smart Network. Smart Business. 3
Radware Mitigating the DoS/DDoS Threat Whitepaper
Cyber attacks have become the weapon of choice for hacktivists seeking to leverage the impact of conflicts and
social protests. Recent examples are the Anonymous group joining the Occupy Wall Street protesters to launch
cyber attacks on major financial institutions in New York, attacking Sony®,, and other companies affiliated with the
copyright industry for revenge as part of Operation Mega-upload. In addition, the Nightmare group works with the
hacker “0xOmar” to escalate their cyber war against Israel,
Attackers are getting sophisticated
An analysis of cyber attacks throughout 2011-2012 by Radware’s Emergency Response Team (ERT), notes that
companies that relied only on a ‘one-size-fits-all’ in-the-cloud managed security, or on-premise security solutions
alone, could not withstand the coordinated attack campaigns. The Radware ERT review of the attack traffic from
multiple reported cases shows that:
• Attackers are deploying multi-vulnerability attack campaigns, targeting all layers of the victim’s IT
infrastructure. This includes the network, servers, and application layers.
• Attackers who previously used distributed denial of service (DDoS) attack tools that focused on networks
have now developed new DDoS tools focusing on applications.
• Attackers are using “low & slow” attack techniques that misuse the application resource rather than
resources in the network stacks.
• Attackers are using evasion techniques to avoid detection and mitigation including SSL based attacks,
changing the page request in a HTTP page flood attacks and more.
VoIP
Application 2%
Network
54% 46%
SMTP
9%
TCP - SYN Flood
25%
HTTPS
13%
IPv6
2%
ICMP
6%
HTTP
21%
UDP
7%
TCP-
Other
DNS
6%
9%
Figure 2: Radware Security Survey 2011: Attack count by type and bandwidth
Smart Network. Smart Business. 4
Radware Mitigating the DoS/DDoS Threat Whitepaper
As a result, small to medium online businesses, financial services, data centers, and enterprises find themselves
with limited capabilities and knowledge to fight against emerging network security threats. While the common
practice of organizations is relying on DDoS protection from their service provider, the recent wave of attacks
in 2012 shows that attackers are getting sophisticated and manage to bypass the service provider and hit
businesses directly. This aises the need to build secured network architecture that combines in-the-cloud DDoS
protection and on-premise DDoS protection.
DDoS Layers of Attack: the Protection Challenges
DDoS Layers of Attack
From the point of view of a service provider, DDoS attacks can be partitioned into four dimensions as shown in
Figure 3:
• Volumetric bandwidth flood attack – Attackers flood the victim with a high volume of packets, consuming
networking equipment resources or bandwidth resources. These are network DDoS flood attacks such as
SYN flood attacks (high packet-per-second attacks), large UDP packet floods (bandwidth attacks), ICMP
floods, and more.
• Application DDoS flood attacks – These attacks generate complete sessions and target the application
resources. Examples are HTTP Get or Post flood attacks, or DNS flood attacks.
• SSL based attacks – Encrypted SSL DoS and DDoS attacks consume more CPU resources during the
encryption and decryption of the content than processing of a clear text. As a result, encrypted application
DoS & DDoS attacks amplify the impact, even at relatively low rates of requests per second.
• Low & slow DoS attacks – Low & slow application DDoS attacks exploit application implementation
weaknesses and design flaws. Examples are Slowloris, a tool that allows a single machine to take down
another machine’s web server with minimal bandwidth, and Circle cache-control (Circle-CC), which floods a
website by scanning the site across multiple pages systematically.
Volumetric Application SSL Based Low & Slow
Bandwidth Flood Attacks Flood Attacks Attacks DoS Attacks
Figure 3: DDoS layers of attacks, from high volume to low volume attacks
Where Current Mitigation Solutions Fail
As mentioned in the introduction, online businesses, financial services, data centers, and enterprises find
themselves with limited capabilities and knowledge to fight against emerging network security threats. The
common practice of organizations is to rely on DDoS protection from their service providers. However, the recent
wave of attacks in 2012 shows that the attackers are getting sophisticated and manage to bypass the service
provider and hit businesses directly, as shown in Figure 4.
Smart Network. Smart Business. 5
Radware Mitigating the DoS/DDoS Threat Whitepaper
Volumetric Application SSL Based Low & Slow
Bandwidth Flood Attacks Flood Attacks Attacks DoS Attacks
In-the-cloud
DDoS Protection
On-premises
DDoS Protection
Figure 4: Where current mitigation solutions fail to protect against DDoS attacks
In-the-cloud DDoS protection is effective against the volumetric bandwidth attacks, and some providers also offer
protection against application DDoS flood attacks, depending on the equipment they are using for detection and
accurate mitigation. However ,the service providers has no visibility into SSL encrypted traffic and cannot block
SSL based attacks; furthermore, the low & slow attacks typically will go undetected by the service providers as
they are low rate attacks that run under the detection thresholds.
To summarize, in-the-cloud DDoS protections are effective in cleansing a high volume of DDoS flood attacks.
Deploying an on-premises DDoS protection solution provides complete protection against the application DDoS
flood attacks, SSL based attacks, and the low & slow attacks. On-premises DDoS protection can detect and
mitigate volumetric attacks as well, however the physical location at the business perimeter network rather than
the carrier link, offers limited effectiveness: attackers that flood victims with a large volume of traffic achieve
Internet link saturation, which renders the on-premises solution useless. Figure 5 shows that 27% of customers
participating at the Radware survey reported that their service was denied due to overload of the Internet link.
30%
27%
24%
8%
5%
4%
Internet pipe Firewall IPS/IDS Load Balancer The server SQL server
(ADC) under attack
Figure 5: Which services or network elements are (have been the bottleneck) of DoS?
Smart Network. Smart Business. 6
Radware Mitigating the DoS/DDoS Threat Whitepaper
The Radware Approach to Fight the DDoS Threat
Introducing Radware Attack Mitigation System (AMS)
Protecting the application infrastructure requires deployment of multiple prevention tools. Radware’s Attack
Mitigation System (AMS), is a real-time network and application attack mitigation solution that protects the
application infrastructure against network and application downtime, application vulnerability exploitation, malware
spread, information theft, web service attacks, and web defacement.
Radware’s Attack Mitigation System contains three layers:
• Protections layer – A set of security modules including: Denial-of-service (DoS) protection, Network
Behavioral Analysis (NBA), Intrusion Prevention System (IPS), Reputation Engine and Web Application
Firewall (WAF). These modules fully safeguard networks, servers, and applications against known and
emerging network security threats
• Security risk management - Built-in Security Event Information Management (SEIM) collects and analyzes
events from all modules to provide enterprise-view situational awareness
• Emergency Response Team (ERT) - Consists of knowledgeable and specialized security experts who
provide 24x7 instantaneous services for customers facing a denial-of-service (DoS) attack in order to
restore network and service operational status
Fighting the DDoS threat is based on multiple AMS protection modules:
Volumetric Application SSL Based Low & Slow
Bandwidth Flood Attacks Flood Attacks Attacks DoS Attacks
Radware Security Features
Anti-DoS NBA SSL Attacks Protection IPS
Figure 6: Mapping Radware AMS protection modules according to the DDoS layers of defense
• Anti-DoS – This module protects against all types of network flood attacks including UDP floods, SYN
floods, TCP floods, ICMP floods, and out-of-state flood attacks.
• NBA – The NBA module detects application misuse attacks and protects against HTTP page and post flood
attacks, DNS flood attacks, SIP flood attacks, and more.
• SSL attacks protection – In conjunction with Radware SSL accelerator, AMS detects and prevents SSL
encrypted attacks, including application flood attacks and vulnerability based attacks.
• IPS – This module deploys deep packet inspection to detect and mitigate low & slow attack tools such as
Slowloris, Sockstress, and others.
Smart Network. Smart Business. 7
Radware Mitigating the DoS/DDoS Threat Whitepaper
End-to-end Mitigation Solution
At this stage, it is clear that an effective mitigation approach against the DDoS threat requires both in-the-cloud
protection and on-premises protection. Radware AMS is the best fit in the industry against the DDoS threat and
can be deployed in both locations:
On-premises Protection Against:
• Application DDoS Attacks
• SSL Based Attacks
• Low & Slow Attacks
Internet
SSL Attacks
Protection NBA
Anti-DoS
IPS
ISP Core Network
Anti-DoS
Attack Mitigation System
Customer Site
In-the-cloud protection against: Attack Mitigation System
• Volumetric Bandwidth Attacks
In-the-cloud Anti-DoS Service
Figure 6: Radware end-to-end mitigation solution fighting the DDoS threat
• In-the-cloud protection: AMS is used to remove the volumetric bandwidth attacks to avoid the risk of link
saturation. This is the first line of defense against DDoS attacks.
• On-premises protection: AMS is deployed at the business perimeter network to fend-off all type of DDoS
attacks: the low & slow attacks, SSL based attacks, application flood attacks, and leakage of network flood
attacks that managed to go undetected or unprotected in-the-cloud.
Only end-to-end mitigation deployment (in-the cloud AND on-premises protection), enables businesses to fully
protect their IT infrastructure against evolving DDoS attacks.
Smart Network. Smart Business. 8
Radware Mitigating the DoS/DDoS Threat Whitepaper
Summary
DDoS attacks are prevalent and no online business or organization can ignore them anymore. Attackers are
getting sophisticated and launch multi-vulnerability attack campaigns, which makes detection and mitigation
nearly impossible.
Organizations that used to rely on their service provider’s DDoS protection service (in-the-cloud), find that the
attacks hit their business, bypassing the provider’s protection layer.
In recent attack cases, we have seen that businesses that have deployed Radware AMS on premises in
conjunction with DDoS protection at the service provider were able to survive and maintain their business
operations in spite of large scale, large volume multi-vulnerability attack campaigns. When AMS is deployed on
both sides (on premises and at the service provider), they have achieved the best protection.
Radware AMS delivers the following solution benefits:
• Radware AMS is the only solution that can truly protect against all type of DDoS attacks including
volumetric DDoS flood attacks, application flood attacks, SSL based attacks, and the low & slow
DoS attacks.
• End-to-end deployment of Radware AMS is the best solution to fight the DDoS threat at all layers, mitigating
all attack vectors in seconds.
• When deployed on-premises, the online business has full control of its security solution and can be
assisted with Radware ERT when attack mitigation expertise is required.
• Make sure your service provider deploys Radware AMS or that the service provider can remove the
volumetric attacks with any other solution they deploy.
• AMS offers the lowest cost OpEx and CapEx solution to fight DDoS attacks.
© 2012 Radware, Ltd. All Rights Reserved. Radware and all other Radware product and service names are registered trademarks of Radware in
the U.S. and other countries. All other trademarks and names are the property of their respective owners.
Smart Network. Smart Business. 9
PRD-AMS-DoSDDoS-Threat-WP-01-2012/02-US
You might also like
- 2600: The Hacker Quarterly (Volume 1, Number 8, August 1984)Document6 pages2600: The Hacker Quarterly (Volume 1, Number 8, August 1984)Ranko Kohime100% (1)
- The Guildsman 01Document95 pagesThe Guildsman 01JP Sanders100% (1)
- Response Declaration of Ross Day in Response To Motion To Quash Jan 12Document61 pagesResponse Declaration of Ross Day in Response To Motion To Quash Jan 12spiritswanderNo ratings yet
- Crypto Affirmative - DDI 2015 STDocument208 pagesCrypto Affirmative - DDI 2015 STMichael TangNo ratings yet
- Security & Safety ManagementDocument51 pagesSecurity & Safety ManagementMichaela Ramos Beato100% (1)
- The 62443 Series OverviewDocument4 pagesThe 62443 Series OverviewJuan RiveraNo ratings yet
- Ransomware Threat Report 2022Document43 pagesRansomware Threat Report 2022Alexandre Olivio de AndradeNo ratings yet
- Cisco Umbrella: The First Line of Defense: DNS-layer SecurityDocument39 pagesCisco Umbrella: The First Line of Defense: DNS-layer SecurityalliisibaNo ratings yet
- CN17-PWC-Mayur Mehata-IsA 99 Cyber Security StandardDocument22 pagesCN17-PWC-Mayur Mehata-IsA 99 Cyber Security StandardJuan RiveraNo ratings yet
- Web App Vulnerability Report 2019: XSS & Libraries Pose Major Risks/TITLEDocument27 pagesWeb App Vulnerability Report 2019: XSS & Libraries Pose Major Risks/TITLEshakawathNo ratings yet
- SQL Query Tuning For SQL Server PDFDocument7 pagesSQL Query Tuning For SQL Server PDFMarcio SilvaNo ratings yet
- Web Application Security is a Stack: How to CYA (Cover Your Apps) CompletelyFrom EverandWeb Application Security is a Stack: How to CYA (Cover Your Apps) CompletelyNo ratings yet
- Automation Is Your Greatest Weapon Against Ddos AttacksDocument26 pagesAutomation Is Your Greatest Weapon Against Ddos Attacksming liNo ratings yet
- DDoS Protection PDFDocument56 pagesDDoS Protection PDFming liNo ratings yet
- How To Use SPSSDocument134 pagesHow To Use SPSSdhimba100% (6)
- Create A Digital Signature in ABAPDocument9 pagesCreate A Digital Signature in ABAPAdaikalam Alexander RayappaNo ratings yet
- The F5 DDoS PlaybookDocument23 pagesThe F5 DDoS PlaybookpvmNo ratings yet
- Netscout Arbor Managed Services For Internet Service ProvidersDocument4 pagesNetscout Arbor Managed Services For Internet Service ProvidersEstebanChiangNo ratings yet
- Ipv6 TrainingDocument259 pagesIpv6 TrainingChakravarthi ChittajalluNo ratings yet
- IEC 62433 Industrial Network and System SecurityDocument18 pagesIEC 62433 Industrial Network and System Securityatoti100% (4)
- NTT Security On OT SecurityDocument4 pagesNTT Security On OT SecurityDK56128No ratings yet
- Nozomi Networks OT IoT Security Report 2021 2HDocument38 pagesNozomi Networks OT IoT Security Report 2021 2HLucas Tura De SantiNo ratings yet
- Cameron W 340 Selinux For Mere MortalsDocument210 pagesCameron W 340 Selinux For Mere MortalsIjazKhanNo ratings yet
- Mitigating The Dos/Ddos ThreatDocument9 pagesMitigating The Dos/Ddos ThreatJuan RiveraNo ratings yet
- Radware DDoS SmokescreenDocument3 pagesRadware DDoS SmokescreenRRRNo ratings yet
- A Secure Detection Framework For ARP, DHCP, and DoS Attacks On Kali LinuxDocument12 pagesA Secure Detection Framework For ARP, DHCP, and DoS Attacks On Kali LinuxIJRASETPublicationsNo ratings yet
- ETL2020 - DDoS A4Document18 pagesETL2020 - DDoS A4hdave32No ratings yet
- ETL2020-DDoS - Ebook - EN-ENISA AMENZA #6Document18 pagesETL2020-DDoS - Ebook - EN-ENISA AMENZA #6jaimeNo ratings yet
- Distributed Denial of Service (Ddos) :: Finally Getting The Attention It DeservesDocument12 pagesDistributed Denial of Service (Ddos) :: Finally Getting The Attention It DeservesthebookerdudeNo ratings yet
- TNSM-2023-06849 Proof HiDocument14 pagesTNSM-2023-06849 Proof Hibasha429108167No ratings yet
- SR RealWorldWISR Insert EN2013Document2 pagesSR RealWorldWISR Insert EN2013Luis RodriguesNo ratings yet
- White Paper c11 741610Document16 pagesWhite Paper c11 741610Thibaut Serge Vianey AkproNo ratings yet
- Love and Marriage: Why Security and SD-WAN Need To Go TogetherDocument3 pagesLove and Marriage: Why Security and SD-WAN Need To Go TogetherElias DendirNo ratings yet
- Infoblox Whitepaper 2023 Global State of Cybersecurity Study PDFDocument15 pagesInfoblox Whitepaper 2023 Global State of Cybersecurity Study PDFThang ManhNo ratings yet
- Radware State of WEB APPDocument28 pagesRadware State of WEB APPIba AngelNo ratings yet
- Hadec: Hadoop-Based Live Ddos Detection Framework: Research Open AccessDocument20 pagesHadec: Hadoop-Based Live Ddos Detection Framework: Research Open Accessamine boulakhrabiNo ratings yet
- Brkpar 2777Document34 pagesBrkpar 2777mejamesonNo ratings yet
- The Quarantine ReportDocument20 pagesThe Quarantine ReportAlex SmirnoffNo ratings yet
- Day2 CcetDocument24 pagesDay2 CcetDhamini GowdaNo ratings yet
- Secureworks E1 LearningfromIncidentResponseJan-Mar22Document12 pagesSecureworks E1 LearningfromIncidentResponseJan-Mar22TTSNo ratings yet
- IBM Security X-Force The 2021 X-Force Threat Intelligence IndexDocument15 pagesIBM Security X-Force The 2021 X-Force Threat Intelligence IndexLohith VelagapudiNo ratings yet
- AA21-131A Darkside Ransomware Best Practices For Preventing Business Dis..Document6 pagesAA21-131A Darkside Ransomware Best Practices For Preventing Business Dis..Eni TestNo ratings yet
- TechTarget Whitepaper - Organizations Increasing Their Adoption of NFV PDFDocument5 pagesTechTarget Whitepaper - Organizations Increasing Their Adoption of NFV PDFJordan DukesNo ratings yet
- Estadisticas de Vulnerabilidad 2021Document31 pagesEstadisticas de Vulnerabilidad 2021J Carlos S AlcocerNo ratings yet
- DDos 2017 ReportDocument56 pagesDDos 2017 ReportBattulga PurevdorjNo ratings yet
- Telecoms Operators in The Eye of The Cyberstorm Final - OriginalDocument20 pagesTelecoms Operators in The Eye of The Cyberstorm Final - OriginalUdeeptha SenevirathnaNo ratings yet
- Toward Secure Software-Defined Networks Against Distributed Denial of Service AttackDocument46 pagesToward Secure Software-Defined Networks Against Distributed Denial of Service Attackdanilo.chagasNo ratings yet
- Lacework - WP - Ransomware - Rising - 040422 - V4Document8 pagesLacework - WP - Ransomware - Rising - 040422 - V4Vladislav AlekseevNo ratings yet
- 2020 Vulnerability Statistics ReportDocument20 pages2020 Vulnerability Statistics ReportMarcioAlessandroDoValNo ratings yet
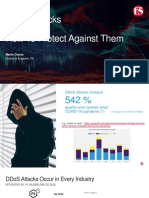
- Ddos Attacks and How To Protect Against Them: Martin OravecDocument34 pagesDdos Attacks and How To Protect Against Them: Martin OravecGelu ConstantinNo ratings yet
- 1294-Manuscript (Without Author Details) - 5326-1-10-20201227Document11 pages1294-Manuscript (Without Author Details) - 5326-1-10-20201227fx_ww2001No ratings yet
- Leveraging The Cloud WPDocument15 pagesLeveraging The Cloud WPdropboxNo ratings yet
- Making Sense of The Dark Web: What's Happening?Document3 pagesMaking Sense of The Dark Web: What's Happening?ÉderNo ratings yet
- Radically Simplifying WP 1Document8 pagesRadically Simplifying WP 1KLNo ratings yet
- A DDoS Attack Detection Method Based On Information Entropy and Deep Learning in SDNDocument5 pagesA DDoS Attack Detection Method Based On Information Entropy and Deep Learning in SDNPallavi PoteNo ratings yet
- A Network Fit For Business InfographicDocument1 pageA Network Fit For Business Infographicfitri ayuNo ratings yet
- The Logicnow Cyber Threat Guide: Nine Types of Internet Threats and How To Stop ThemDocument44 pagesThe Logicnow Cyber Threat Guide: Nine Types of Internet Threats and How To Stop ThemsunbratNo ratings yet
- Navigating Cyber: The Case For A Global Fincyber UtilityDocument10 pagesNavigating Cyber: The Case For A Global Fincyber Utilityyeison montanNo ratings yet
- International Journal of Information Management Data InsightsDocument13 pagesInternational Journal of Information Management Data InsightsNiraliNo ratings yet
- 01-2021 CNN MLDocument12 pages01-2021 CNN MLSayeed HabeebNo ratings yet
- AA21-131A DarkSide RansomwareDocument6 pagesAA21-131A DarkSide RansomwareNelson AbreuNo ratings yet
- Entropy Based Ddos Detection and Mitigation in Openflow Enabled SDNDocument5 pagesEntropy Based Ddos Detection and Mitigation in Openflow Enabled SDNFebyolanoerainiNo ratings yet
- Network Security For The Cloud Generation-: A Comprehensive Defense-in-Depth ApproachDocument16 pagesNetwork Security For The Cloud Generation-: A Comprehensive Defense-in-Depth ApproachSpad ParnianNo ratings yet
- Netskope Security Clouds Hands On: 2020 © Netskope Confidential. All Rights ReservedDocument53 pagesNetskope Security Clouds Hands On: 2020 © Netskope Confidential. All Rights Reservedpritish keneNo ratings yet
- State of The WAN Report 2017: Do Not Reproduce Without Prior PermissionDocument37 pagesState of The WAN Report 2017: Do Not Reproduce Without Prior PermissionHarry RazeNo ratings yet
- Radware Online Business Protection Ebook PDFDocument11 pagesRadware Online Business Protection Ebook PDFEdgardo McFlyNo ratings yet
- Research Paper On DdosDocument8 pagesResearch Paper On Ddosgahezopizez2100% (1)
- Application - Security - Research - Update - Report 2018 PDFDocument46 pagesApplication - Security - Research - Update - Report 2018 PDFGhilmer VHNo ratings yet
- AI Powered Ransomware PoudyalDocument9 pagesAI Powered Ransomware PoudyalUmesh PaliwalNo ratings yet
- How To Avoid Party Chaos 1698257750912Document8 pagesHow To Avoid Party Chaos 1698257750912Paul R. MessinaNo ratings yet
- 2022 Global Digital Trust Insights: The C-Suite Guide To Simplifying For Cyber Readiness, Today and TomorrowDocument31 pages2022 Global Digital Trust Insights: The C-Suite Guide To Simplifying For Cyber Readiness, Today and TomorrowCom DigfulNo ratings yet
- Sanctions Masterclass - Exploring the Intersection of Ransomware, Crypto, and Sanctions RisksDocument38 pagesSanctions Masterclass - Exploring the Intersection of Ransomware, Crypto, and Sanctions RisksabhishevrmaNo ratings yet
- Idc Ddos Security 0613 WPDocument12 pagesIdc Ddos Security 0613 WPSurajRaje DarandaleNo ratings yet
- Mi019 146Document66 pagesMi019 146Jhon CoelloNo ratings yet
- B0193AV P IA Series Integrated Control Configurator PDFDocument136 pagesB0193AV P IA Series Integrated Control Configurator PDFJuan Rivera50% (2)
- Uk Palm Otdr: Most Compact High-Performance OTDRDocument3 pagesUk Palm Otdr: Most Compact High-Performance OTDRJuan RiveraNo ratings yet
- Evaluating The Chemical Diffusion Coefficient of Sulfur in Slag by Metal Analysis: Model Concept and ExperimentsDocument11 pagesEvaluating The Chemical Diffusion Coefficient of Sulfur in Slag by Metal Analysis: Model Concept and ExperimentsJuan RiveraNo ratings yet
- Technical Specification: IEC TS 62351-6Document6 pagesTechnical Specification: IEC TS 62351-6Juan Rivera0% (1)
- ISO IEC 27017 BackgrounderDocument2 pagesISO IEC 27017 BackgrounderJuan RiveraNo ratings yet
- Iso31000 2009Document38 pagesIso31000 2009valentina sucerquiaNo ratings yet
- ICS ModulesDocument67 pagesICS ModulesJuan RiveraNo ratings yet
- C S I E .: A I ISA/IEC 62443: KenexisDocument15 pagesC S I E .: A I ISA/IEC 62443: KenexisJuan RiveraNo ratings yet
- IECEx Cyber Security Update 2016Document7 pagesIECEx Cyber Security Update 2016Juan RiveraNo ratings yet
- 09 Power MethodDocument72 pages09 Power Methodnayeem4444No ratings yet
- National Youth Service Corps: 1. Online RegistrationDocument7 pagesNational Youth Service Corps: 1. Online RegistrationEngr Armstrong Enyioma AlaomaNo ratings yet
- Foxit PhantomPDF For HP - Quick GuideDocument31 pagesFoxit PhantomPDF For HP - Quick GuideGuill HerNo ratings yet
- Unit 2 Information Progress Test: The Business Upper Intermediate Tests / Unit 2 1Document7 pagesUnit 2 Information Progress Test: The Business Upper Intermediate Tests / Unit 2 1Amap Zenon ZenonczykNo ratings yet
- Forensic ScienceDocument6 pagesForensic SciencefunnyrokstarNo ratings yet
- F06084145 PDFDocument5 pagesF06084145 PDFSharath rNo ratings yet
- US v. Timothy GrahamDocument9 pagesUS v. Timothy GrahamRussell BrandomNo ratings yet
- AKB0048 Stage 12Document34 pagesAKB0048 Stage 12snc260No ratings yet
- Conv74 4Document3 pagesConv74 4Jose Reiriz GarciaNo ratings yet
- Shik Mahamood Ali FormsDocument88 pagesShik Mahamood Ali Formssatya1401100% (1)
- Salary Review Police PDFDocument15 pagesSalary Review Police PDFBen MusimaneNo ratings yet
- People's Republic of China QR Form 101: Document Type I Nternational Release Form Your Name National ID NumberDocument3 pagesPeople's Republic of China QR Form 101: Document Type I Nternational Release Form Your Name National ID NumberChen ZhaiNo ratings yet
- Remote Diagnostics Using IoTDocument12 pagesRemote Diagnostics Using IoTMassSomeshNo ratings yet
- Project MineSweeper AlgorithmDocument5 pagesProject MineSweeper AlgorithmTrầnQuangHiếuNo ratings yet
- F 5 e 9Document59 pagesF 5 e 9Aadan CaddeNo ratings yet
- Implement CIA Triad using Anti Cyber Crime LawDocument10 pagesImplement CIA Triad using Anti Cyber Crime LawRomel BandoquilloNo ratings yet
- Ojt CompilationDocument44 pagesOjt CompilationAcoo Xii HernandezNo ratings yet
- Ethics and Information Security: Presented byDocument15 pagesEthics and Information Security: Presented bymahamNo ratings yet
- MysiteDocument123 pagesMysiteapi-3847330No ratings yet
- Report Solicitor Form 1Document4 pagesReport Solicitor Form 1Fuzzy_Wood_PersonNo ratings yet