0% found this document useful (0 votes)
994 views8 pagesRail Fence Cipher
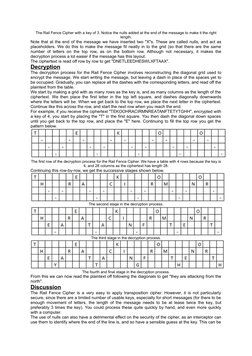
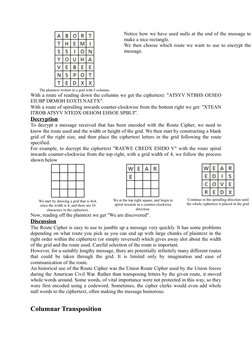
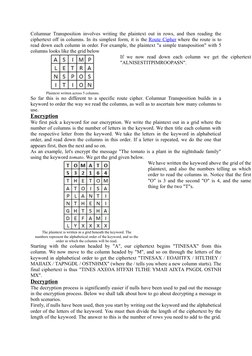
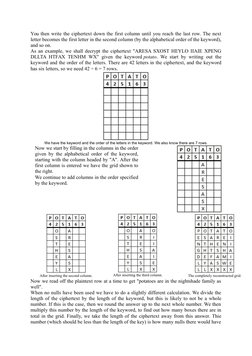
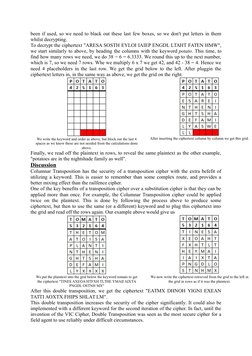
The document discusses several transposition ciphers including the Rail Fence cipher, Route cipher, and Columnar transposition cipher. The Rail Fence cipher encrypts messages by writing them in zig-zag lines and reading off each line in turn. The Route cipher encrypts messages by writing them in a grid and reading off following a specified route. Columnar transposition involves writing messages in a grid based on the number of letters in a keyword and reading off the columns in alphabetical order of the keyword letters.
Uploaded by
dianwiryoCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as DOCX, PDF, TXT or read online on Scribd
0% found this document useful (0 votes)
994 views8 pagesRail Fence Cipher
The document discusses several transposition ciphers including the Rail Fence cipher, Route cipher, and Columnar transposition cipher. The Rail Fence cipher encrypts messages by writing them in zig-zag lines and reading off each line in turn. The Route cipher encrypts messages by writing them in a grid and reading off following a specified route. Columnar transposition involves writing messages in a grid based on the number of letters in a keyword and reading off the columns in alphabetical order of the keyword letters.
Uploaded by
dianwiryoCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as DOCX, PDF, TXT or read online on Scribd