0% found this document useful (0 votes)
572 views6 pagesInternet Security T1
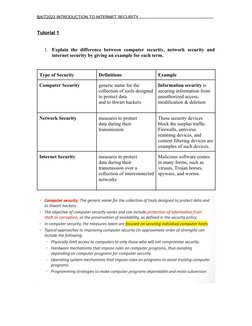
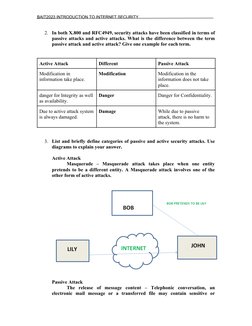
This document provides an introduction to internet security. It defines and distinguishes between computer security, network security, and internet security. It discusses the differences between passive and active security attacks, providing examples of each. Categories of passive and active attacks are defined along with diagrams. The differences between threats and attacks are outlined with examples. Finally, the document analyzes a 2009 denial-of-service attack on Twitter and Facebook and defines the security concept of availability.
Uploaded by
CHEE HAN LOCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as DOCX, PDF, TXT or read online on Scribd
0% found this document useful (0 votes)
572 views6 pagesInternet Security T1
This document provides an introduction to internet security. It defines and distinguishes between computer security, network security, and internet security. It discusses the differences between passive and active security attacks, providing examples of each. Categories of passive and active attacks are defined along with diagrams. The differences between threats and attacks are outlined with examples. Finally, the document analyzes a 2009 denial-of-service attack on Twitter and Facebook and defines the security concept of availability.
Uploaded by
CHEE HAN LOCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as DOCX, PDF, TXT or read online on Scribd