0% found this document useful (0 votes)
87 views6 pagesKPDCL Sop Hardning
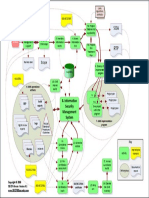
This document outlines Kashmir Power Distribution Corporation Limited's (KPDCL) Standard Operating Procedure for system hardening. It describes an 8-step process for identifying assets, assessing risks, selecting hardening guidelines, implementing configurations, documentation, testing, review, and continuous improvement. The goal is to secure systems and infrastructure according to ISO/IEC 27001 by disabling unneeded services, applying patches, enforcing access controls, and monitoring for security incidents. Responsibilities are assigned and records must be kept to demonstrate compliance.
Uploaded by
deeptanwar1997Copyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as DOCX, PDF, TXT or read online on Scribd
0% found this document useful (0 votes)
87 views6 pagesKPDCL Sop Hardning
This document outlines Kashmir Power Distribution Corporation Limited's (KPDCL) Standard Operating Procedure for system hardening. It describes an 8-step process for identifying assets, assessing risks, selecting hardening guidelines, implementing configurations, documentation, testing, review, and continuous improvement. The goal is to secure systems and infrastructure according to ISO/IEC 27001 by disabling unneeded services, applying patches, enforcing access controls, and monitoring for security incidents. Responsibilities are assigned and records must be kept to demonstrate compliance.
Uploaded by
deeptanwar1997Copyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as DOCX, PDF, TXT or read online on Scribd