0% found this document useful (0 votes)
80 views9 pagesLab 6-Filtering Network Traffic With Tcpdump
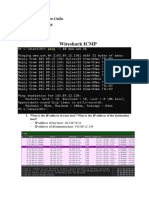
This document provides a practical guide for filtering network traffic using tcpdump, covering command line options, packet dissection, and writing BPF filters. It includes exercises for analyzing IP and TCP headers, identifying options, and detecting signs of intrusion. Additionally, it outlines a scenario for examining traffic from a specific source IP for potential malicious behavior.
Uploaded by
dsrathnayake4Copyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd
0% found this document useful (0 votes)
80 views9 pagesLab 6-Filtering Network Traffic With Tcpdump
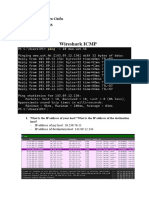
This document provides a practical guide for filtering network traffic using tcpdump, covering command line options, packet dissection, and writing BPF filters. It includes exercises for analyzing IP and TCP headers, identifying options, and detecting signs of intrusion. Additionally, it outlines a scenario for examining traffic from a specific source IP for potential malicious behavior.
Uploaded by
dsrathnayake4Copyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd