0% found this document useful (0 votes)
414 views14 pagesUnderstanding Network Security Essentials
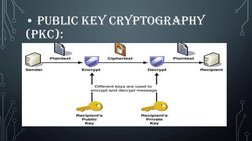
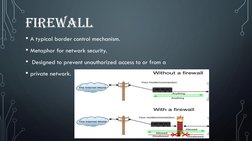
Network security involves protecting a network and its resources against threats. It is handled by a network administrator and involves multiple layers of security through hardware and software components like firewalls, antivirus software, and encryption. Some key aspects of network security include access control, authentication, confidentiality, integrity, and non-repudiation. Common security tools and technologies used include cryptography, public key cryptography, firewalls, secure socket layer, security protocols, and network security services.
Uploaded by
madeti gouthamCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PPTX, PDF, TXT or read online on Scribd
0% found this document useful (0 votes)
414 views14 pagesUnderstanding Network Security Essentials
Network security involves protecting a network and its resources against threats. It is handled by a network administrator and involves multiple layers of security through hardware and software components like firewalls, antivirus software, and encryption. Some key aspects of network security include access control, authentication, confidentiality, integrity, and non-repudiation. Common security tools and technologies used include cryptography, public key cryptography, firewalls, secure socket layer, security protocols, and network security services.
Uploaded by
madeti gouthamCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PPTX, PDF, TXT or read online on Scribd