100% found this document useful (1 vote)
2K views61 pagesSAP BW/BI Security & Authorization Guide
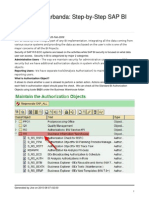
This document provides an overview of authorizations in SAP BW/BI. It discusses the importance of security and defines key concepts like OLTP, OLAP, and the differences between SAP R/3 and BI security. It also summarizes various SAP BW authorization objects like S_RS_COMP, S_RS_COMP1, S_RS_FOLD, S_RS_HIER, S_RS_ICUBE, and S_RS_ISRCM that control access to different components, folders, hierarchies, InfoCubes, and source systems in the BI platform.
Uploaded by
sreedevi k.v.Copyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PPT, PDF, TXT or read online on Scribd
100% found this document useful (1 vote)
2K views61 pagesSAP BW/BI Security & Authorization Guide
This document provides an overview of authorizations in SAP BW/BI. It discusses the importance of security and defines key concepts like OLTP, OLAP, and the differences between SAP R/3 and BI security. It also summarizes various SAP BW authorization objects like S_RS_COMP, S_RS_COMP1, S_RS_FOLD, S_RS_HIER, S_RS_ICUBE, and S_RS_ISRCM that control access to different components, folders, hierarchies, InfoCubes, and source systems in the BI platform.
Uploaded by
sreedevi k.v.Copyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PPT, PDF, TXT or read online on Scribd