Professional Documents
Culture Documents
Display Filters
Uploaded by
euOriginal Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Display Filters
Uploaded by
euCopyright:
Available Formats
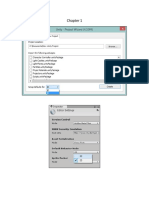
Filtering packets while viewing ------------------------------After capturing packets or loading some network traffic from a file, Wireshark w ill
display the packet data immediately on the screen. Using display filters, you can choose which packets should (not) be shown on the screen. This is useful to reduce the "noise" usually on the network, showing on ly the packets you want to. So you can concentrate on the things you are really interested in. The display filter will not affect the data captured, it will only select which packets of the captured data are displayed on the screen. Everytime you change the filter string, all packets will be reread from the capt ure file (or from memory), and processed by the display filter "machine". Packet by packet, this "machine" is asked, if this particular packet should be shown o r not. Wireshark offers a d for a wide range IP address", or on ts where a special very powerful display filter language for this. It can be use of purposes, from simply: "show only packets from a specific the other hand, to very complex filters like: "find all packe application specific flag is set".
Note: This display filter language is different from the one used for the Wiresh ark capture filters! ------------------------------------------------Some common examples -------------------Example Ethernet: display all traffic to and from the Ethernet address 08.00.08. 15.ca.fe eth.addr==08.00.08.15.ca.fe Example IP: display all traffic to and from the IP address 192.168.0.10 ip.addr==192.168.0.10 Example TCP: display all traffic to and from the TCP port 80 (http) of all machi nes tcp.port==80 Examples combined: display all traffic to and from 192.168.0.10 except http ip.addr==192.168.0.10 && tcp.port!=80 Beware: The filter string builds a logical expression, which must be true to sho w the packet. The && is a "logical and", "A && B" means: A must be true AND B mu st be true to show the packet (it doesn't mean: A will be shown AND B will be sh own). ------------------------------------------------Hint ---Filtering can lead to side effects, which are sometimes not obvious at first sig ht. Example: If you capture TCP/IP traffic with the primitive "ip", you will not see the ARP traffic belonging to it, as this is a lower protocol layer than IP!
You might also like
- 7347OT GraphicsDocument116 pages7347OT GraphicseuNo ratings yet
- GamesDocument1 pageGameseuNo ratings yet
- Userguide EN D5322 1 Android4.3Document116 pagesUserguide EN D5322 1 Android4.3euNo ratings yet
- 520 Manual English PDFDocument37 pages520 Manual English PDFeuNo ratings yet
- Output File - Adolix Split PDFDocument50 pagesOutput File - Adolix Split PDFeuNo ratings yet
- Third Person Games ListDocument1 pageThird Person Games ListeuNo ratings yet
- Exercicios InglesDocument5 pagesExercicios InglesAlecx Wanubio MendesNo ratings yet
- About Command SyntaxDocument3 pagesAbout Command SyntaxdeepukalkuniNo ratings yet
- About CommonParameters - HelpDocument6 pagesAbout CommonParameters - HelpHarshad S PatilNo ratings yet
- Playready EulaDocument2 pagesPlayready EulaeuNo ratings yet
- Table Text Service YiDocument30 pagesTable Text Service YidjjazrielNo ratings yet
- Aboutفا Arithmetic Operators.helpDocument9 pagesAboutفا Arithmetic Operators.helpUrdu SahafatNo ratings yet
- Playready EulaDocument2 pagesPlayready EulaeuNo ratings yet
- About Aliases - HelpDocument4 pagesAbout Aliases - HelpHarshad S PatilNo ratings yet
- Super ResolutionDocument2 pagesSuper ResolutioneuNo ratings yet
- WireadmeDocument1 pageWireadmeeuNo ratings yet
- Sharpen 5x5Document2 pagesSharpen 5x5euNo ratings yet
- InvertDocument1 pageInverteuNo ratings yet
- Spacials OftenDocument2 pagesSpacials OfteneuNo ratings yet
- Night VisionDocument1 pageNight VisioneuNo ratings yet
- Sharpen Complex 2Document2 pagesSharpen Complex 2euNo ratings yet
- Gray ScaleDocument1 pageGray ScaleeuNo ratings yet
- Expose BandingDocument1 pageExpose BandingeuNo ratings yet
- Night VisionDocument1 pageNight VisioneuNo ratings yet
- WireadmeDocument1 pageWireadmeeuNo ratings yet
- Film Projector Lamp VignetteDocument1 pageFilm Projector Lamp VignetteeuNo ratings yet
- Display Less Than 16Document1 pageDisplay Less Than 16euNo ratings yet
- EmbossDocument1 pageEmbosseuNo ratings yet
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (895)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5794)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (537)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (399)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (73)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (838)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (588)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (266)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (344)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1090)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2259)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (120)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (821)