Professional Documents
Culture Documents
SQL Injection: Cross-Site Script Attack
Uploaded by
Deepak Kumar DeoOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
SQL Injection: Cross-Site Script Attack
Uploaded by
Deepak Kumar DeoCopyright:
Available Formats
Cross-site script attack
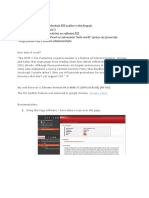
The attacker can compromise the session token by using malicious code or programs running at the client-side. The
example shows how the attacker could use an XSS attack to steal the session token. If an attacker sends a crafted link to
the victim with the malicious JavaScript, when the victim clicks on the link, the JavaScript will run and complete the
instructions made by the attacker. The example in figure 3 uses an XSS attack to show the cookie value of the current
session; using the same technique it's possible to create a specific JavaScript code that will send the cookie to the attacker.
<SCRIPT>alert(document.cookie);</SCRIPT>
SQL Injection
SQL injection is a security vulnerability that occurs in the database layer of an application.
It's better explained with an example. Suppose in a database-backed web site, user enters
username on a form, and server replies with address. Assume the following code is
embedded in the server application.
string username = dom.getForm("username");
string query = "SELECT address FROM usertable WHERE uname = '"+username+"';"
database.execute(query);
If the user types "eddie'; SELECT bankaccount FROM usertable WHERE uname = 'ahnuld'" as
username, the following SQL statement would be built by the code above:
SELECT address FROM usertable WHERE uname = 'eddie'; SELECT bankaccount FROM
usertable WHERE uname = 'ahnuld';
When sent to the database, this statement would be executed and Arnold's bankaccount
would be sent to the user. I am sure our governor wouldn't be happy about it.
You might also like
- Be LP3 Q2 41239 Ics MiniprojDocument10 pagesBe LP3 Q2 41239 Ics MiniprojWow BollywoodNo ratings yet
- Quiz Ch9 Answers PDFDocument4 pagesQuiz Ch9 Answers PDFCliefSengkeyNo ratings yet
- Complete Cross Site Scripting WalkthroughDocument23 pagesComplete Cross Site Scripting WalkthroughAndro SinagaNo ratings yet
- Cross Site Scripting XSSDocument31 pagesCross Site Scripting XSSKalpa De SilvaNo ratings yet
- Securing Web ApplicationDocument15 pagesSecuring Web ApplicationMary EnitekNo ratings yet
- Code InjectionDocument11 pagesCode InjectionJitendra RaiNo ratings yet
- LESSON 7-SQL InjectionDocument15 pagesLESSON 7-SQL InjectionMeriza MalinaoNo ratings yet
- Using XSS To Bypass CSRF ProtectionDocument12 pagesUsing XSS To Bypass CSRF ProtectionMuhammad AdhaNo ratings yet
- Cross Site Scripting (XSS) : by Amit TyagiDocument31 pagesCross Site Scripting (XSS) : by Amit TyagiGarland NealNo ratings yet
- IS Assignment CP - 02Document6 pagesIS Assignment CP - 02f180364 Rabab ZahraNo ratings yet
- Tracking Down App SecurityDocument69 pagesTracking Down App SecuritygeorgesharmokhNo ratings yet
- Detect SQL Injection Wordpress Plugin Using Regex: Submit By: Suncsr (Sun Cyber Security Research)Document4 pagesDetect SQL Injection Wordpress Plugin Using Regex: Submit By: Suncsr (Sun Cyber Security Research)haxiwig567No ratings yet
- XSS Attacks and Defenses: John MitchellDocument44 pagesXSS Attacks and Defenses: John MitchellHanef SamsudinNo ratings yet
- Web Application AttacksDocument5 pagesWeb Application AttacksHet Bhavin PatelNo ratings yet
- By Hari RuthalaDocument37 pagesBy Hari RuthalaRao Ali ShanNo ratings yet
- Web Application Disassembly With ODBC Error Messages: by David Litchfield Director of Security Architecture @stakeDocument5 pagesWeb Application Disassembly With ODBC Error Messages: by David Litchfield Director of Security Architecture @stakeFernando MuñozNo ratings yet
- Types of XSS AttacksDocument5 pagesTypes of XSS Attackstom1No ratings yet
- Web Security - Injection AttacksDocument3 pagesWeb Security - Injection AttackssandaruNo ratings yet
- Lab WDocument11 pagesLab WdawliNo ratings yet
- Tutorial On Cross Site Scripting (XSS) Prevention inDocument7 pagesTutorial On Cross Site Scripting (XSS) Prevention intjahsoloNo ratings yet
- 09 Web Site SecDocument17 pages09 Web Site SecThanh HươngNo ratings yet
- Application Vulnerabilities and DefencesDocument12 pagesApplication Vulnerabilities and DefencesSanmati JainNo ratings yet
- SQL InjectionDocument28 pagesSQL InjectionManish100% (1)
- Lab File (4) (It Security)Document26 pagesLab File (4) (It Security)pandeyjiiiiii995No ratings yet
- Reference 1 - 2017Document13 pagesReference 1 - 2017abenezer ketemaNo ratings yet
- Saleh Abd Alrahman Bit Ze3Document6 pagesSaleh Abd Alrahman Bit Ze3abd alrahman salehNo ratings yet
- Cross Site Scripting Ethical Hacking Lab ExerciseDocument10 pagesCross Site Scripting Ethical Hacking Lab ExercisePaul CraneNo ratings yet
- CakePHP Aggressive SecurityDocument10 pagesCakePHP Aggressive SecurityPankaj Kumar JhaNo ratings yet
- SQL InjectionDocument28 pagesSQL InjectionManish100% (3)
- BH US 11 Sullivan Server Side WP PDFDocument7 pagesBH US 11 Sullivan Server Side WP PDFsAdInNo ratings yet
- BH US 11 Sullivan Server Side WP PDFDocument7 pagesBH US 11 Sullivan Server Side WP PDFUnknown020No ratings yet
- Cross Site ScriptingDocument6 pagesCross Site Scriptingnaushad73No ratings yet
- SQL InjectionDocument22 pagesSQL Injectionapi-3750475100% (3)
- Cross Site Scripting 004Document15 pagesCross Site Scripting 004samNo ratings yet
- SQL Server Injection AttackDocument8 pagesSQL Server Injection AttackPablo ZambranoNo ratings yet
- A Taxonomy of SQL Injection AttacksDocument5 pagesA Taxonomy of SQL Injection AttacksJay ShrotriyaNo ratings yet
- Cross-Site Scripting PDFDocument18 pagesCross-Site Scripting PDFmandalikaNo ratings yet
- Damn Vulnerable Web ApplicationsDocument24 pagesDamn Vulnerable Web ApplicationsrutvikmehtaNo ratings yet
- How To Prevent Cross-Site Scripting (XSS) in JavaScriptDocument9 pagesHow To Prevent Cross-Site Scripting (XSS) in JavaScriptYouNo ratings yet
- Using XSS To Bypass CSRF ProtectionDocument13 pagesUsing XSS To Bypass CSRF Protectionali_sevNo ratings yet
- Cross Site ScriptingDocument20 pagesCross Site ScriptingmamathaNo ratings yet
- Buffer Overflow Attacks, SQL Injection AttacksDocument42 pagesBuffer Overflow Attacks, SQL Injection AttacksRaymondNo ratings yet
- The Blackhat's Toolbox: SQL Injections: Trust No-One Error-Based SQL InjectionDocument3 pagesThe Blackhat's Toolbox: SQL Injections: Trust No-One Error-Based SQL InjectionGerman ArleyNo ratings yet
- PMBDocument39 pagesPMBkartit0% (1)
- L28 - Security 1Document20 pagesL28 - Security 1C-dawgNo ratings yet
- Detection of SQL Injection and Cross-Site Scripting AttacksDocument6 pagesDetection of SQL Injection and Cross-Site Scripting AttacksVũ TuấnNo ratings yet
- Damn Vulnerable Web ApplicationsDocument16 pagesDamn Vulnerable Web ApplicationsAli KindyNo ratings yet
- SQL Injection HShahDocument7 pagesSQL Injection HShahÉderNo ratings yet
- Bike Write-UpDocument20 pagesBike Write-UpUserNo ratings yet
- Trend ReportDocument21 pagesTrend ReportRajasekhjar MatamNo ratings yet
- cs253 Final 2019 SolutionsDocument4 pagescs253 Final 2019 SolutionsfoosaaNo ratings yet
- SQL InjectionDocument10 pagesSQL InjectionTechnocrawl100% (1)
- Secure MVC Application - Saineshwar - Compressed PDFDocument135 pagesSecure MVC Application - Saineshwar - Compressed PDFALP69No ratings yet
- Cross Site ScriptingDocument12 pagesCross Site Scriptingsanik100% (1)
- JavaScript Programming: 3 In 1 Security Design, Expressions And Web DevelopmentFrom EverandJavaScript Programming: 3 In 1 Security Design, Expressions And Web DevelopmentNo ratings yet
- ETHICAL HACKING GUIDE-Part 3: Comprehensive Guide to Ethical Hacking worldFrom EverandETHICAL HACKING GUIDE-Part 3: Comprehensive Guide to Ethical Hacking worldNo ratings yet
- Securing .NET Web Services with SSL: How to Protect “Data in Transit” between Client and Remote ServerFrom EverandSecuring .NET Web Services with SSL: How to Protect “Data in Transit” between Client and Remote ServerNo ratings yet
- Add Hoc NetworkDocument67 pagesAdd Hoc NetworkhappinesspromishNo ratings yet
- CEH Module 15: Session HijackingDocument19 pagesCEH Module 15: Session HijackingAhmad MahmoudNo ratings yet
- Wipro Campus Placement, Aptitude Paper, Feb 2010, Delhi: AFW Team Leave Your CommentDocument24 pagesWipro Campus Placement, Aptitude Paper, Feb 2010, Delhi: AFW Team Leave Your CommentDeepak Kumar DeoNo ratings yet
- Final ProjectDocument60 pagesFinal ProjectDeepak Kumar DeoNo ratings yet