Professional Documents
Culture Documents
Intel Adaptive Modulation QPSK QAM - 303788
Intel Adaptive Modulation QPSK QAM - 303788
Uploaded by
Dejan NemecCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Intel Adaptive Modulation QPSK QAM - 303788
Intel Adaptive Modulation QPSK QAM - 303788
Uploaded by
Dejan NemecCopyright:
Available Formats
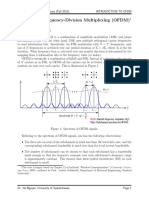
Adaptive Modulation (QPSK, QAM)
Introduced below are the concepts of digital modulation used in many communication systems today. Techniques described include quadrature phase shift keying (QPSK) and quadrature amplitude modulation (QAM) and how these techniques can be used to increase the capacity and speed of a wireless network. These modulation techniques are the basis of communications for systems like cable modems, DSL modems, CDMA, 3G, Wi-Fi* (IEEE 802.11) and WiMAX* (IEEE 802.16). well as bending (diffraction) around corners.
Modulation
Modulation is the process by which a carrier wave is able to carry the message or digital signal (series of ones and zeroes). There are three basic methods to this: amplitude, frequency and phase shift keying. Higher orders of modulation allow us to encode more bits per symbol or period (time). Amplitude shift keying (ASK) involves increasing the amplitude (power) of the wave in step with the digital signal (in other words, low = 0, high = 1) and is used in AM radio. Frequency shift keying (FSK) changes the frequency in step with the digital signal. Systems that use this modulation (broadcast FM radio) tend to be more resilient to noise since noise usually changes the amplitude of the signal. In Figure 1, different bits are represented by different frequencies which can then be detected by a receiver.
Carrier Waves
Radio waves are electromagnetic waves that move at the speed of light in a sine wave formation and can be used to carry a message over a distance. They can have different frequencies which describes how fast they are moving up and down which is measured in cycles per second or hertz. Carrier waves with different frequencies have different properties. For example, light waves are visible to the naked eye but cannot travel through walls. Radio waves (especially those of lower frequency) can penetrate walls and buildings as
Intel in Communications
Figure 1: Frequency Shift Keying Phase shift keying (PSK) changes the phase of the carrier in step with the digital message. For binary phase shift keying (BPSK), each symbol could indicate two different states or one bit per symbol (in other words, 0 = 0, 180 = 1). In Figure 2, the second wave is shifted by half a period or 180 degrees. The receiver can than recognize this shift indicating either a digital one or zero.
Adaptive Modulation (QPSK, QAM)
Application Note
1 Cycle Phase 0 degrees
1 Cycle Phase 180 degrees
Figure 2: Phase Shift Keying QPSK adds two more phases: 90 and 270 degrees. Now two symbols per bit can be transmitted. Each symbols phase is compared relative to the previous symbol; so, if there is no phase shift (0 degrees), the bits 00 are represented. If there is a phase shift of 180 degrees, the bits 11 are represented.
Phase Shift 90 degrees
Phase Shift 0 degrees
01
00
Figure 3: Quadrature Phase Shift Keying Table 1: Quadrature Phase Shift Keying Symbol 00 01 11 10 Phase Shift 0 degrees 90 degrees 180 degrees 270 degrees ASK and PSK can be combined to create QAM where both the phase and amplitude are changed. The receiver then receives this modulated signal, detects the shifts and demodulates the signal back into the original data stream. In Figure 4 showing 16-QAM, each symbol can now represent four bits instead of just the two bits per symbol with QPSK. Each point indicates a unique amplitude and phase of the wave (for example, point (1,1) indicates 90 degrees and amplitude of 1).
Application Note
Adaptive Modulation (QPSK, QAM)
0010
0110
1110
1010
0011
0111
1 0
1111
1011
0000
Amplitude
-3
0001
-1 -1
0101
1
1101
3
1001
0000
0100
-3
1100
1000
Phase
Figure 4: Quadrature Amplitude Modulation 16-QAM
Adaptive Modulation
Different order modulations allow you to send more bits per symbol and thus achieve higher throughputs or better spectral efficiencies. However, it must also be noted that when using a modulation technique such as 64-QAM, better signal-to-noise ratios (SNRs) are needed to overcome any interference and maintain a certain bit error ratio (BER). The use of adaptive modulation allows a wireless system to choose the highest order modulation depending on the channel conditions. In Figure 5, you can see a general estimate of the channel conditions needed for different modulation techniques. As you increase your range, you step down to lower modulations (in other words, BPSK), but as you are closer you can utilize higher order modulations like QAM for increased throughput. In addition, adaptive modulation allows the system to overcome fading and other interference.
Adaptive Modulation (QPSK, QAM)
Application Note
Figure 5: Adaptive Modulation and Coding Both QAM and QPSK are modulation techniques used in IEEE 802.11 (Wi-Fi*), IEEE 802.16 (WiMAX*) and 3G (WCDMA/HSDPA) wireless technologies. The modulated signals are then demodulated at the receiver where the original digital message can be recovered. The use of adaptive modulation allows wireless technologies to optimize throughput, yielding higher throughputs while also covering long distances. Communications Group. Since joining Intel in 2000, he has worked on a variety of projects, including chipset design, chipset architecture, strategic marketing and several wireless technologies including: BLUETOOTH*, Wi-Fi* (IEEE 802.11), ultra wideband, WiMAX* (802.16) and 3G. He is currently researching future wireless technologies for mobility/portability including WiMAX*, 3G and beyond. He holds a B.S. in computer engineering from the University of Kansas.
Author Biography
Sam W. Ho is a technical marketing engineer in the Wireless Networking Group, part of the Intel
Intel Access
WiMAX* - Broadband Wireless Access Technology: Other Intel Support: www.intel.com/netcomms/technologies/wimax/index.htm Intel Literature Center developer.intel.com/design/litcentr/ (800) 548-4725 7 a.m. to 7 p.m. CST (U.S. and Canada)
International locations please contact your local sales office.
General Information Hotline:
(800) 628-8686 or (916) 356-3104 5 a.m. to 5 p.m. PST
For more information, visit the Intel Web site at: developer.intel.com
INFORMATION IN THIS DOCUMENT IS PROVIDED IN CONNECTION WITH INTEL PRODUCTS. NO LICENSE, EXPRESS OR IMPLIED, BY ESTOPPEL OR OTHERWISE, TO ANY INTELLECTUAL PROPERTY RIGHTS IS GRANTED BY THIS DOCUMENT. EXCEPT AS PROVIDED IN INTEL'S TERMS AND CONDITIONS OF SALE FOR SUCH PRODUCTS, INTEL ASSUMES NO LIABILITY WHATSOEVER, AND INTEL DISCLAIMS ANY EXPRESS OR IMPLIED WARRANTY, RELATING TO SALE AND/OR USE OF INTEL PRODUCTS INCLUDING LIABILITY OR WARRANTIES RELATING TO FITNESS FOR A PARTICULAR PURPOSE, MERCHANTABILITY, OR INFRINGEMENT OF ANY PATENT, COPYRIGHT OR OTHER INTELLECTUAL PROPERTY RIGHT. Intel products are not intended for use in medical, life saving, or life sustaining applications. Intel may make changes to specifications and product descriptions at any time, without notice. * Other names and brands may be claimed as the property of others. Copyright 2004, Intel Corporation. All rights reserved. Intel and the Intel logo are trademarks or registered trademarks of Intel Corporation or its subsidiaries in the United States and other countries. Printed in USA. Please Recycle Order Number 303788-001
You might also like
- Optimum Array Processing: Part IV of Detection, Estimation, and Modulation TheoryFrom EverandOptimum Array Processing: Part IV of Detection, Estimation, and Modulation TheoryNo ratings yet
- Questions and Answers On Basic Structures of ComputersDocument23 pagesQuestions and Answers On Basic Structures of Computerskibrom atsbha57% (7)
- Aviat WTM 6000 All IP Long Haul Trunking PlatformDocument16 pagesAviat WTM 6000 All IP Long Haul Trunking PlatformDerrick Senyo50% (2)
- Qam NotesDocument14 pagesQam NotesWaqasMirzaNo ratings yet
- On The Fundamental Aspects of DemodulationDocument11 pagesOn The Fundamental Aspects of DemodulationAI Coordinator - CSC JournalsNo ratings yet
- Cisar2020 PDFDocument8 pagesCisar2020 PDFManoj LNo ratings yet
- Ch04-Digital TransmissionDocument37 pagesCh04-Digital TransmissionSuraj ShahNo ratings yet
- QAM and M-Ary SignallingDocument21 pagesQAM and M-Ary SignallingKeitly VictoriaNo ratings yet
- Lect 09 - Adaptive Modulation and Coding PDFDocument5 pagesLect 09 - Adaptive Modulation and Coding PDFCu BomNo ratings yet
- Lecture1-3 18360 Ch2-StallingsDocument27 pagesLecture1-3 18360 Ch2-StallingsSuraj ShahNo ratings yet
- The Most Common Abbreviations in DVBDocument9 pagesThe Most Common Abbreviations in DVBStarLink1No ratings yet
- Channel Coding Techniques in TetraDocument12 pagesChannel Coding Techniques in TetraAdnan Shehzad100% (1)
- Exercise Ofdm Ieee 802 11a PDFDocument13 pagesExercise Ofdm Ieee 802 11a PDFmhaabNo ratings yet
- Understanding The Performance of TCP PacingDocument11 pagesUnderstanding The Performance of TCP Pacingdk_mishra1989No ratings yet
- 05 - High Speed Interface Various Applications - LG전자 - 홍국태 발표자료 - HS Interface - V10Document51 pages05 - High Speed Interface Various Applications - LG전자 - 홍국태 발표자료 - HS Interface - V10GiancarloRichardRivadeneyraMirandaNo ratings yet
- 10 - Debugging ToolsDocument67 pages10 - Debugging ToolsAlejo EtxebeNo ratings yet
- Tutorial1 Sol 180102Document9 pagesTutorial1 Sol 180102Punky HeroNo ratings yet
- Link Budget Analysis 1Document66 pagesLink Budget Analysis 1Ahmed MilianaNo ratings yet
- GR TutorialDocument79 pagesGR TutorialAamir HabibNo ratings yet
- NEC 5000S PresentationDocument58 pagesNEC 5000S PresentationLidiyaa WandeNo ratings yet
- Ieee 802.11 Wlan PDFDocument2 pagesIeee 802.11 Wlan PDFruletriplexNo ratings yet
- Homemade GPS ReceiverDocument24 pagesHomemade GPS ReceiverroyvalentikNo ratings yet
- IEEE 802.11s Wireless Mesh NetworksDocument7 pagesIEEE 802.11s Wireless Mesh NetworkskalpanasripathiNo ratings yet
- Final Year ProjectDocument53 pagesFinal Year ProjectAnonymous 7b87Ja5e1R100% (2)
- What Is The Function of SDCCHDocument12 pagesWhat Is The Function of SDCCHjabi_shaik_1No ratings yet
- 5G A Systems Approach PaperDocument67 pages5G A Systems Approach PaperArunNo ratings yet
- RL532A DatasheetDocument2 pagesRL532A DatasheetMOHSIN RAZANo ratings yet
- Tetra Security ClassDocument21 pagesTetra Security ClassShoaib Arif BukhariNo ratings yet
- 0184.Z-Stack User's Guide For CC2530 ZigBee-PRO Network Processor - Sample Applications PDFDocument74 pages0184.Z-Stack User's Guide For CC2530 ZigBee-PRO Network Processor - Sample Applications PDFEugen NeagaNo ratings yet
- Gnuradio ProgrammingDocument28 pagesGnuradio ProgrammingJavier MelendrezNo ratings yet
- EC8491 - Communication TheoryDocument468 pagesEC8491 - Communication TheoryGurunathanNo ratings yet
- Ab Ansys Hfss For Antenna Simulation PDFDocument9 pagesAb Ansys Hfss For Antenna Simulation PDFغريب في بلاد الفرنجهNo ratings yet
- PDH & SDHDocument5 pagesPDH & SDHBahaa Alaboud100% (1)
- Power Measurement BasicsDocument27 pagesPower Measurement BasicsSatadal GuptaNo ratings yet
- iQBC Syllabus 20110823Document5 pagesiQBC Syllabus 20110823NinoNo ratings yet
- Lecture 3 P4 NetFPGADocument83 pagesLecture 3 P4 NetFPGAnguyentienduy1512No ratings yet
- Part 3. Multiplexing PDH SDHDocument59 pagesPart 3. Multiplexing PDH SDHMahesh SinghNo ratings yet
- UMTS AircomDocument20 pagesUMTS AircomDũng PhạmNo ratings yet
- OFDM LectureDocument128 pagesOFDM Lectureashugolu02No ratings yet
- PCM PDH and SDHDocument58 pagesPCM PDH and SDHAkram Ba-odhanNo ratings yet
- Monitoring Using A Windows BoxDocument37 pagesMonitoring Using A Windows BoxrajeshgadhviNo ratings yet
- SDH BasicsDocument31 pagesSDH BasicsAnkita Tiwari100% (1)
- NETFPGADocument23 pagesNETFPGABDeebak100% (1)
- Types of Beamforming: Adaptive AntennasDocument33 pagesTypes of Beamforming: Adaptive AntennasHarryNo ratings yet
- Ibuilder User Guide PDFDocument300 pagesIbuilder User Guide PDFgermancho81No ratings yet
- IDirect BroadbandDocument6 pagesIDirect BroadbandHakan SyblNo ratings yet
- Apollo Family BR Digital NewDocument4 pagesApollo Family BR Digital NewMuku vermaNo ratings yet
- Native Packet Transport NPT Family BrochureDocument8 pagesNative Packet Transport NPT Family BrochureNguyen Anh Duc100% (1)
- Convolutional Codes PuncturingDocument13 pagesConvolutional Codes PuncturinghunterdlrNo ratings yet
- T1 and E1 PCM SystemsDocument10 pagesT1 and E1 PCM SystemsPrafull BNo ratings yet
- PNMSJ Java CatalogDocument4 pagesPNMSJ Java CatalogAHMEDKAMAL2011100% (1)
- Unit V Ststem Examples & Design IssuesDocument104 pagesUnit V Ststem Examples & Design IssuesK Sasi RekhaNo ratings yet
- 2G, 3G, 4G Mobile CommunicationDocument50 pages2G, 3G, 4G Mobile CommunicationSujoy ShivdeNo ratings yet
- Lecture6 PLMNDocument34 pagesLecture6 PLMNNatnael MesheshaNo ratings yet
- Mobile Communications Chapter 7: Wireless Lans: Slides by Jochen Schiller With Modifications by Emmanuel AguDocument65 pagesMobile Communications Chapter 7: Wireless Lans: Slides by Jochen Schiller With Modifications by Emmanuel AguajayNo ratings yet
- SIP Extensions For The IP Multimedia Subsystem A Complete Guide - 2020 EditionFrom EverandSIP Extensions For The IP Multimedia Subsystem A Complete Guide - 2020 EditionNo ratings yet
- Lecture - 04Document31 pagesLecture - 04Jesmin MostafaNo ratings yet
- Wk3 Modulation BasicDocument57 pagesWk3 Modulation Basicapi-3714247No ratings yet
- CDMA2000 GSM ComparisonDocument14 pagesCDMA2000 GSM Comparisonapi-3699476No ratings yet
- CSVPN 01 S 03 ADocument22 pagesCSVPN 01 S 03 Aapi-3714247No ratings yet
- Chapter 2: Overview of VPN and Ipsec TechnologiesDocument50 pagesChapter 2: Overview of VPN and Ipsec Technologiesapi-3714247No ratings yet
- WiMAX The Business Case Rev3Document24 pagesWiMAX The Business Case Rev3Madaleno Pedro Vicente DalúNo ratings yet
- WiMAX WP PDFDocument10 pagesWiMAX WP PDFDorival Junior Ferreira de MelloNo ratings yet
- Tutorial - Arduino and The TI ADS1110 16-Bit ADCDocument5 pagesTutorial - Arduino and The TI ADS1110 16-Bit ADCantoninoxxxNo ratings yet
- B.Tech - CSE-7th SemDocument2 pagesB.Tech - CSE-7th SemrohanNo ratings yet
- FM ADocument163 pagesFM ASahit Babu PamarthiNo ratings yet
- Wisenet - SPE110 Video Network EncoderDocument3 pagesWisenet - SPE110 Video Network Encoderforat 64079No ratings yet
- ACAPI Interface PaperDocument9 pagesACAPI Interface PapermrocachNo ratings yet
- Hot Standby Router Protocol (HSRP) Is A Cisco Proprietary Redundancy Protocol For Establishing A Fault-Tolerant DefaultDocument4 pagesHot Standby Router Protocol (HSRP) Is A Cisco Proprietary Redundancy Protocol For Establishing A Fault-Tolerant DefaultVidyun LambaNo ratings yet
- Freescale Semiconductor, Inc.: Application NoteDocument28 pagesFreescale Semiconductor, Inc.: Application NoteLaurentiu IacobNo ratings yet
- Nero Burning RomDocument134 pagesNero Burning RomJenny AbramsNo ratings yet
- RMP PresentationDocument109 pagesRMP Presentationprakashsapkal352No ratings yet
- PostgreSQLInstallation RunBookDocument33 pagesPostgreSQLInstallation RunBookRaj100% (1)
- Call Setup FlowchartDocument2 pagesCall Setup FlowchartMostafa MekawyNo ratings yet
- Laboratory ManualDocument62 pagesLaboratory Manualتبارك موسى كريم علوانNo ratings yet
- Zoiper Product Comparison ChartDocument7 pagesZoiper Product Comparison ChartRandy GordeyNo ratings yet
- OnCommand Unified Manager DFM-OprationDocument61 pagesOnCommand Unified Manager DFM-OprationPurushothama Gn100% (1)
- Product Selector EsDocument529 pagesProduct Selector EsJoséNo ratings yet
- DsPIC Elmer 166 en USDocument78 pagesDsPIC Elmer 166 en USnawzat100% (2)
- Red Hat Enterprise Linux 6: Virtualization Host Configuration and Guest Installation GuideDocument151 pagesRed Hat Enterprise Linux 6: Virtualization Host Configuration and Guest Installation GuideFauro2011No ratings yet
- Master Course PDFDocument1 pageMaster Course PDFmuhammad nasserNo ratings yet
- FChapter 2 - Intro To MC68000Document26 pagesFChapter 2 - Intro To MC68000Zyzerull SaadNo ratings yet
- Reference Books For ECEDocument1 pageReference Books For ECEPrapul ReddyNo ratings yet
- TRS Plus: Traffic Recording SystemsDocument2 pagesTRS Plus: Traffic Recording Systemss pradhanNo ratings yet
- Rajkumar J: 94428 57178 Linkedin: /In/RajkumarjambunathanDocument3 pagesRajkumar J: 94428 57178 Linkedin: /In/RajkumarjambunathanRajkumar JambunathanNo ratings yet
- Indoor Positioning SystemDocument11 pagesIndoor Positioning SystemPradeep CheekatlaNo ratings yet
- CXMLUsersGuide For PODocument206 pagesCXMLUsersGuide For POmeel_silvaNo ratings yet
- Digital Communication VTU Unit 1Document56 pagesDigital Communication VTU Unit 1raghudathesh50% (2)
- LLI-FifoSync64x24 V PDFDocument3 pagesLLI-FifoSync64x24 V PDFkumarsanjeev.net9511No ratings yet
- GenICam SFNC 2 0 0 PDFDocument366 pagesGenICam SFNC 2 0 0 PDFmike mikeNo ratings yet
- Explosives Rules, 2010 PDFDocument203 pagesExplosives Rules, 2010 PDFAhmed MujtabaNo ratings yet