Professional Documents
Culture Documents
Configure IPSec Tunnel Between Windows Server 2003 and WS 2000
Uploaded by
Ramprasad VempatiOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Configure IPSec Tunnel Between Windows Server 2003 and WS 2000
Uploaded by
Ramprasad VempatiCopyright:
Available Formats
How To Configure IPSec Tunneling between Windows Server 2003 and WS 2000 Summery Goal MORE INFORMATION Create
ORMATION Create IPSec Policy Build a Filter List from NetA to NetB Build a Filter List from NetB to NetA Configure a Rule for a NetA-to-NetB Tunnel Configure a Rule for a NetB-to-NetA Tunnel Assign Your New IPSec Policy to Your Windows Server 2003 Gateway Configure Routing and Remote Access Filtering Configure Static Routes in Routing and Remote Access Test Your IPSec Tunnel Enable Auditing for Logon Events and Object Access IP Security Monitor Network Monitor Actual Test
REFERENCES SUMMARY You can use IP Security (IPSec) in tunnel mode to encapsulate Internet Protocol (IP) packets and optionally encrypt them. Windows Server 2003 supports IPSec tunneling for situations where both tunnel endpoints have static IP addresses. This article describes how to configure an IPSec tunnel between a Windows Server 2003 gateway and the WS 2000. Because the IPSec tunnel secures only traffic that is specified in the IPSec filters that you have to configure in the Windows 2003 Server, this article also describes how to configure filters in the Routing and Remote Access service to prevent traffic outside the tunnel from being received or forwarded.
Goal The goal is to configure the Windows Server 2003 gateway and the WS 2000 in this way that an IPSec tunnel will guide traffic from Int A to Int B or to guide traffic coming from Int B to Int A, over a secure session (See figure 1).
192.168.0.0/24
10.10.10.0/24
157.235.160.0/24
IP Int. A: 192.168.0.1
IP Ext. A: 10.10.10.1 IPSEC Tunnel
IP Ext. B: 10.10.10.2
IP Int. B: 157.235.160.143
192.168.0.100
WS 2000
157.235.160.1
Windows 2003 server
Figure 1 If you want to configure an IPSec policy in the Windows 2003 Server, you must build: one filter to match packets going from Int A to Int B (tunnel 1) one filter to match packets going from Int B to Int A (tunnel 2). a filter action to specify how the tunnel is secured (a tunnel is represented by a rule, so two rules are created).
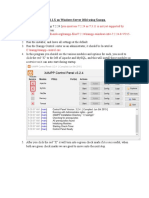
Create IPSec Policy (See figure 2) 1. Click Start -> Run, and then type secpol.msc to start the IP Security Policy Management snap-in. 2. Right-click IP Security Policies on Local Computer -> Create IP Security Policy. 3. Click Next, and then type a name for your policy (I used: IPSEC to WS2K). Click Next. 4. Click to clear the Activate the default response rule check box -> Next. 5. Click Finish (leave the Edit check box selected).
Figure 2 Build a Filter List from Int A to Int B 1. In the new policy properties, click to clear the Use Add Wizard check box, -> Add to create a new rule. 2. Click the IP Filter List tab, -> Add. 3. Type an appropriate name for the filter list ( I used: Net A B), click to clear the Use Add Wizard check box, -> Add. (See figure 3) 4. In the Source address box, select A specific IP Subnet, and then type the IP Address and Subnet mask to for Int A. (See figure 4) 5. In the Destination address box, select A specific IP Subnet, and then type the IP Address and Subnet mask for Int B. (See figure 4) 6. Click to clear the Mirrored check box.
7. Click the Protocol tab. Make sure that the protocol type is set to Any, because IPSec tunnels do not support protocol-specific or portspecific filters. (See figure 5) 8. Click OK.
Figure 3
Figure 4
Figure 5 Build a Filter List from Int B to Int A 1. Click the IP Filter List tab, -> Add. 2. Type an appropriate name for the filter list ( I used: Net B A), click to clear the Use Add Wizard check box, -> Add. (See figure 6) 3. In the Source address box, select A specific IP Subnet, and then type the IP Address and Subnet mask to for Int A. (See figure 7)
4. In the Destination address box, select A specific IP Subnet, and then type the IP Address and Subnet mask for Int B. (See figure 7) 5. Click to clear the Mirrored check box. 6. Click the Protocol tab. Make sure that the protocol type is set to Any, because IPSec tunnels do not support protocol-specific or portspecific filters. (See figure 8) 7. Click OK.
Figure 6
Figure 7
Figure 8 When you have finished this with success you would see:
Figure 9 Configure a Rule for a Int A to Int B Tunnel 1. Click the IP Filter List tab, and then click to select the filter list that you created (Net A B). 2. Click the Tunnel Setting tab, click The tunnel endpoint is specified by this IP Address box, and then type IP Ext A (See figure 10). 3. Click the Connection Type tab, click Local area network (LAN) (See figure 11). 4. Click the Filter Action tab, click to clear the Use Add Wizard check box, -> Add to create a new filter action because the default actions allow incoming traffic in clear text. 5. Keep the Negotiate security option enabled, and then click to clear the Accept unsecured communication, but always respond using IPSec check box. You must do this for secure operation (See figure 12). 6. Click Add,-> Custom. Select Data Integrity and Encryption, -> select MD5 and select 3DES. Encapsulating Security Payload (ESP) is one of the two IPSec protocols (See figure 13). 7. Click OK. Click the General tab, type a name for the new filter action (I used IPSEC for WS2K), and then click OK. 8. Select the filter action that you just created. 9. Click the Authentication Methods tab, -> Add -> Use this string (preshared key), enter the same preshared key as you are going to use in the WS 2000 IKE configuration (See figure 14).
10. Click Close.
Figure 10
Figure 11
Figure 12
Figure 13
Figure 14
Configure a Rule for a Int B to Int A Tunnel 1. In IPSec policy properties, click Add to create a new rule. 2. Click the IP Filter List tab, click to select the filter list that you created (from Net B - A) (See figure 15). 3. Click the Tunnel Setting tab, click The tunnel endpoint is specified by this IP Address box, and then type IP Ext B (See figure 16). 4. Click the Connection Type tab, click Local area network (LAN) (See figure 17). 5. Click the Filter Action tab, -> select the filter action that you created above (See figure 18). 6. Click the Authentication Methods tab, and then configure the same method that you used in the first rule or used in the WS 2000 (the same method must be used in both rules) (See figure 19). 7. Click OK, make sure both rules that you created are enabled in your policy, and then click OK again.
Figure 15
Figure 16
Figure 17
Figure 18
Figure 19
Assign Your New IPSec Policy to Your Windows Server 2003 Gateway In the IP Security Policies on Local Computer MMC snap-in, right-click your new policy, and then click Assign (See figure 20).
Configure Static Routes in Routing and Remote Access The Windows Server 2003 gateway must have a route in its route table for Int B. To configure this route, add a static route in the Routing and Remote Access MMC. If the Windows Server 2003 gateway is multihomed with two or more network adapters on the same external network the potential exists for the following: Outbound tunnel traffic leaves on one interface, and the inbound tunnel traffic is received on a different interface. Even if you use IPSec offload network adapters, receiving on a different interface (than the outbound tunnel traffic is sent on) does not allow the receiving network adapter to process the encryption in hardware, because only the outbound interface can offload the Security Association (SA). Outbound tunnel traffic leaves on an interface that is different from the interface that has the tunnel endpoint IP address. The source IP of the tunneled packet is the source IP on the outbound interface. If this is not the source IP that is expected by the other end, the tunnel is not established (or packets are dropped by the remote endpoint if the tunnel has already been established). To avoid sending outbound tunnel traffic on the wrong interface, define a static route to bind traffic to NetB to the appropriate external interface: 1. In the Routing and Remote Access MMC, expand your server tree, expand the IP Routing subtree, right-click Static Routes, and then click New Static Route.
2. In the Interface box, click WIN2003extIP (if this is the interface that you want to always use for outbound tunnel traffic). 3. Type the Destination network and Network mask for NetB. 4. In the Gateway box, type 3rdextip. 5. Keep the Metric value set to its default (1), and then click OK. Note To address the issue of receiving inbound tunnel traffic on the wrong interface, do not advertise the interface's IP address by using a routing protocol. Also, configure a filter in the Routing and Remote Access service to drop packets to NetA or WIN2003extIP as indicated in the "Configure Routing and Remote Access Filtering" section of this article. back to the top Test Your IPSec Tunnel You can initiate the tunnel by pinging from a computer on Int A to a computer on Int B (or from Int B to Int A). If you created the filters correctly and assigned the correct policy, the two gateways establish an IPSec tunnel so they can send the ICMP traffic from the ping command in encrypted format. Even if the ping command works, verify that the ICMP traffic was sent in encrypted format from gateway to gateway. You can use the following tools to do this. Enable Auditing for Logon Events and Object Access This logs events in the security log. This tells you if IKE security association negotiation was tried and if it was successful or not. 1. Using the Group Policy MMC snap-in, expand Local Computer Policy, expand Computer Configuration, expand Windows Settings, expand Security Settings, expand Local Policies, and then click Audit Policy. 2. Enable Success and Failure auditing for Audit logon events and Audit object access. IP Security Monitor The IP Security Monitor console shows IPSec statistics. After you try to establish the tunnel by using the ping command, you can see if an SA was created (if the tunnel creation is successful, an SA is displayed). If the ping command is successful but there is no SA, the ICMP traffic was not protected by IPSec. If you see a "soft association" that did not previously exist, then IPSec agreed to allow this traffic to go "on the clear" (without encryption). Note In Microsoft Windows XP and the Windows Server 2003 family, IP Security Monitor is implemented as a Microsoft Management Console (MMC) console. To add the IP Security Monitor snap-in, follow these steps: 1. Click Start, click Run, type MMC, and then click OK.
2. Click File, click Add/Remove Snap-in, and then click Add. 3. Click IP Security Monitor, and then click Add. 4. Click Close, and then click OK. Network Monitor You can use Network Monitor to capture traffic going through the IP Ext B interface while you try to ping the computer. If you can see ICMP packets in the capture file that have source and destination IP addresses that correspond to the IP addresses of the computer that you are pinging from and the computer you are trying to ping, then IPSec is not protecting the traffic. To install Network Monitor, follow these steps: 1. Click Start, click Control Panel, click Add or Remove Programs, and then click Add/Remove Windows Components. 2. In the Windows Components wizard, click Management and Monitoring Tools, and then click Details. 3. In Subcomponents of Management and Monitoring Tools, click to select the Network Monitor Tools check box, and then click OK. 4. If you are prompted for additional files, insert the installation CD for your operating system, or type a path of the location of the files on the network. Configure Routing and Remote Access Filtering If you want to prevent traffic that does not have a source or destination address that matches Int A or Int B, create an output filter for the external interface in the Routing and Remote Access MMC so that the filter drops all traffic except packets from Int A to Int B. Also create an input filter so the filter drops all traffic except packets from Int B to Int A. You also have to allow traffic to and from IP Ext B and IP Ext A to allow IKE negotiation when the tunnel is being created. Routing and Remote Access filtering is performed over IPSec. You do not have to specifically allow the IPSec protocol because it never reaches the IP packet filter layer. The following example is a very simple representation of the Windows Server 2003 TCP/IP architecture: Application layer Transport layer (TCP|UDP|ICMP|RAW) ---- Network layer start ---IP Packet Filter (where NAT/Routing and Remote Access filtering is done) IPSec (where IPSec filters are implemented) Fragmentation/Reassembly ---- Network layer end -----NDIS Interface Datalink layer
Physical layer To configure the filters in the Routing and Remote Access service, load the Routing and Remote Access MMC and follow these steps: 1. Expand your server tree under Routing and Remote Access, expand the IP Routing subtree, and then click General. 2. Right-click WIN2003extIP, and then click Properties. 3. Click Outbound Filters, and then click New. 4. Click to select the Source network and Destination network check boxes. 5. In the Source network box, type the IP address and Subnet mask for NetA. 6. In the Destination network box, type the IP address and Subnet mask for NetB. 7. Keep the protocol set to Any, and then click OK. 8. Click New, and then click to select the Source network and Destination network check boxes. 9. In the Source network box, type the IP address and Subnet mask for WIN2003extIP. 10. In the Destination network box, type the IP address and Subnet mask for 3rdExtIP (for IKE negotiation use a subnet mask of 255.255.255.255). 11. Keep the protocol set to Any, and then click OK. 12. Click to select the Drop all packets except those that meet the criteria below check box, and then click OK. 13. Click Input Filters, click Add, and then click to select the Source network and Destination network check boxes. 14. In the Source network box, type the IP address and Subnet mask for NetB. 15. In the Destination network box, type the IP address and Subnet mask for NetA. 16. Keep the protocol set to Any, and then click OK. 17. Click New, and then click to select the Source network and Destination network check boxes. 18. In the Source network box, type the IP address and Subnet mask for 3rdExtIP. 19. In the Destination network box, type the IP address and Subnet mask for WIN2003extIP (for IKE negotiation use a subnet mask of 255.255.255.255). 20. Keep the protocol set to Any, and then click OK. 21. Click to select the Drop all packets except those that meet the criteria below check box, and then click OK two times. back to the top REFERENCES
For more information about the Routing and Remote Access service, see Windows Server 2003 online Help. To view the Windows Server 2003 Resource Kit and other technical documentation, visit the following Microsoft Web site: http://www.microsoft.com/windowsserver2003/default.mspx For IETF standards information, visit the following sites: IPSec http://www.ietf.org/html.charters/ipsec-charter.html L2TP http://www.ietf.org/html.charters/pppext-charter.html ftp://ftp.isi.edu/in-notes/rfc2661.txt http://www.ietf.org/html.charters/l2tpext-charter.html Microsoft provides third-party contact information to help you find technical support. This contact information may change without notice. Microsoft does not guarantee the accuracy of this third-party contact information.
You might also like
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5794)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (399)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (894)
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (537)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (838)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (587)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (265)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (73)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (344)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2219)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (119)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (821)
- Facebook Page Management For BeginnersDocument24 pagesFacebook Page Management For BeginnersEmelyn Mendoza VentanillaNo ratings yet
- Interactive PowerPoint Quiz Game with PointsDocument5 pagesInteractive PowerPoint Quiz Game with PointsMarJenNo ratings yet
- Motto, Vision, Mission & Philosophy - Official Portal of UKMDocument3 pagesMotto, Vision, Mission & Philosophy - Official Portal of UKMasNo ratings yet
- Opus Audio FormatDocument29 pagesOpus Audio Formatpeteco carabajalNo ratings yet
- Introduction To SIS-LMSDocument9 pagesIntroduction To SIS-LMSMayom MabuongNo ratings yet
- WWW Tutorialspoint Com Java Java - Exceptions HTM PDFDocument11 pagesWWW Tutorialspoint Com Java Java - Exceptions HTM PDFKaranNo ratings yet
- XBMC User GuideDocument17 pagesXBMC User Guideapi-320473608No ratings yet
- Cadstar Schematic DiyDocument36 pagesCadstar Schematic DiyAvk SanjeevanNo ratings yet
- ChatGPT For CodersDocument31 pagesChatGPT For Coderskrishnarajs.krs1No ratings yet
- The7 - Multi-Purpose Website Building Toolkit For WordpressDocument2 pagesThe7 - Multi-Purpose Website Building Toolkit For WordpressmohmedinhoNo ratings yet
- Lab 7: 802.1X: Wireless NetworksDocument13 pagesLab 7: 802.1X: Wireless NetworksJosel ArevaloNo ratings yet
- Itunes U User'S Guide: Apple EducationDocument20 pagesItunes U User'S Guide: Apple EducationRoberto Báez MoralesNo ratings yet
- Idirect Evolution X1 Installation Guide PDFDocument9 pagesIdirect Evolution X1 Installation Guide PDFNandar ChokieNo ratings yet
- System Administrators GuideDocument630 pagesSystem Administrators GuidePankaj MishraNo ratings yet
- Full Xibo InstallationDocument27 pagesFull Xibo InstallationPero Perić100% (2)
- 1MA170 0eDocument23 pages1MA170 0enirmalk_87No ratings yet
- QA Analyst Resume TitleDocument7 pagesQA Analyst Resume TitleMadhav GarikapatiNo ratings yet
- Assessment Answer Key: Total Training For Adobe Acrobat X Pro - EssentialsDocument6 pagesAssessment Answer Key: Total Training For Adobe Acrobat X Pro - EssentialsdmcamplexNo ratings yet
- Lab Sheet 01Document35 pagesLab Sheet 01tariqshah457No ratings yet
- History of Computer ReviewerDocument10 pagesHistory of Computer ReviewerNeil Andrew Aliazas78% (9)
- DigitDocument104 pagesDigitEdwin GeraldNo ratings yet
- DummiesGuideDocument51 pagesDummiesGuideMilorad SpasicNo ratings yet
- Safety Critical Systems Assignment 4 PDFDocument9 pagesSafety Critical Systems Assignment 4 PDFShanu DuaNo ratings yet
- Install and Configure Windows Server 2003 DNS ServerDocument4 pagesInstall and Configure Windows Server 2003 DNS Servermkaran2009No ratings yet
- 1 Simple Budget Template With Dashboard TipsographicDocument7 pages1 Simple Budget Template With Dashboard TipsographicReza AfarandNo ratings yet
- WR28 User GuideDocument95 pagesWR28 User GuidegarycharlesNo ratings yet
- ADF 2 - sg2Document409 pagesADF 2 - sg2charchit123No ratings yet
- INFO2180 - Lab 3 (20 Marks) : Tic-Tac-ToeDocument8 pagesINFO2180 - Lab 3 (20 Marks) : Tic-Tac-ToeJavian CampbellNo ratings yet
- Productivity+ Software For CNC Machine Tools: PowerfulDocument6 pagesProductivity+ Software For CNC Machine Tools: PowerfulJeffrey CastoNo ratings yet
- OrangeApps - UserLogonIO KRC2 KRC4.User - en V1.0Document28 pagesOrangeApps - UserLogonIO KRC2 KRC4.User - en V1.0Berkay DoganNo ratings yet