Professional Documents
Culture Documents
55-Polynomial Time Primal
Uploaded by
ttunglOriginal Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
55-Polynomial Time Primal
Uploaded by
ttunglCopyright:
Available Formats
Mathematical Programming
78 (1997) 109-129
,USA
anston,
A polynomial time primal network simplex algorithm for minimum cost flows
James B. Orlin
Sloan School of Management, MIT, Cambridge, MA 02139, USA
Received I I July 1995; revised manuscript received 11 May 1996
Abstract Developing a polynomial time primal network simplex algorithm for the mininumn cost flow problem has been a long standing open problem. In this paper, we develop one such algorithm that 2 -l2 log n)) time, where n is the number of nodes in the network, nl runs in O(min(n2 ml. log nC,n is the number of arcs, and C denotes the maximum absolute arc costs if arc costs are integer and x otherwise. W'e first introduce a pseudopolynomial variant of the network simplex algorithni called the 'premultiplier algorithm". We then develop a cost-scaling version of the premultiplier algorithm that solves the minimum cost flow problem in O(min(nni log nC, nm 2 log n)) pivots. With certain simple data structures, the average time per pivot can be shown to be O(n). We also show that the diameter of the network polytope is 0(nn log n). 1997 The Mathematical Programming Society, Inc. Published by Elsevier Science B.V.
, Israel
Kcv'orsc.s: N'lininlLmun cost flows; Network simplex; Polynomial time; Simplex algorithin Premulitipterss
1. Introduction
A funcdamental problem within the area of network optimization is the mininlum cost led for publiiid basis
flow problem. The problem has applications to a remarkably wide range of fields, including chemistry and physics, computer networking, most branches of enaineerino,
only
.4ew Zealand, mail rates are te. For orders,
rdeliveryvia
manufacturing, public policy and social systems, schedulin
and routing, telecommuniifferent
cations, anc transportation (see, for example, [1]). There are a nuniber of
tegiFor orders )m
polynomial-time algorithms for the minimum cost flow problem. Curr-ently, the fastest
ee number for
algorithms for the minimum cost flow problem are due to Ahuja et al. [2], Goldberg and
Tarjan [31, and Orlin [4]. However, the algorithm of choice in practice is the network simplex aloritlnlhm due to its simplicity and speed. Although the network simplex algorithn seems to be excellent in practice, several natural pivot rules take an exponential nunber of pivots in the worst case, as proved by Zadeh [5]. To this
0025-5610/97/)S 7.00 c 1997 The Mathematical Programming Society, Inc. Published by Elsevier Science B.V. Pl S0025-5610(97)000 1 1 -7
Fax: (+31) 20,Fax: (+81) 3t34-3727, Fax: 'o International be used for the :nce should be .V. (Molenwerf 1North, Central )STMASTERS: .ont, NY 11003.
ate, there are no
________1_
110
J.B. Oriin/Mathematical Programming 78 (1997) 109-129
specializations of the primal network simplex algorithm that run in polynomial time for the minimum cost flow problem. For graphs with nodes and mn arcs, the current best bound on the number of pivots for the primal network simplex algorithm is I l/ +0(1)) due to Tarjan [6]. In this paper, we present the first polynomial time primal network simplex algorithm for the minimum cost flow problem. The number of pivots performed by this algorithm is O(nm log nC) or O(nn 2log n), whichever is smaller, where C is the largest integral cost coefficient. This resolves a long-standing open research question. We note that there are other closely related algorithms. There are polynomial time primal network simplex algorithms for (i) the assignment problem (see, for example, [7-10,11]); (ii) the shortest path problem (see, for example, [7,12-14,10,11]); and (iii) the maximum flow problem (see, for example, [15-171)). There are also polynomial time dual network simplex algorithms for the minimum cost flow problem (see, for t) example, [18-21]). Finally, [22] and [6] established that there are primal network simplex algorithms that have a polynomial number of pivots if one permits pivots that increase the objective function value. The number of pivots for Tarjan's rule is O(nmmin((log nC),m log n)), which is the same C) as the number of pivots of the rule given in this paper. These algorithms are not primal network simplex rules in the usual t)t) sense that the objective function value is monotonically non-increasing; however, they are useful from a theoretical perspective. We present a cost-scaling variant of a novel network simplex pivot rule, called te t) premultiplier algorithm. Normally for the network simplex algorithm, one maintains a t> vector of simplex multipliers so that the reduced cost is 0 for each arc (ij) of the spanning tree. Here we relax this condition and maintain a vector of "premultipliers" so tl~~~~~~~~~~~~~~~~~~~ ~~~~~~assu. that the reduced cost is non-positive for each arc that is directed towards the root in the spanning tree and the reduced cost is non-negative-for each arc directed away from the Z:> t) root. An unusual feature of this implementation is that the root of the spanning tree is permitted to change at each pivot; indeed, it is often required to change. This feature is t~~~~~~~~~ ~~~~~~~~~~~each Z:> also shared by one of Tarjan's algorithms [6]. The amortized running time per pivot of the algorithm presented here is 0(n). [23] develops a variant of dynamic trees that reduces the amortized running time per pivot to 0(log n) over a sequence of m pivots. This reduces the running time of the algorithm to C) b ((nmr log n)(min(log nC,m log n)). This running time is slower than running time of * bz:> the Goldberg-Tarjan [3] cost scaling algorithm by a factor of (log n)/(log n 2 /m). Thus, for sparse graphs, the two running times are comparable.
2
} low
use( f ~~~~~
i ~~~~~ resi ~~~~~ ev
.
C'.
~~~~~~ in bn ~~~~~~ bi au
,
caus
we(
assu we ~~~~~~ ir as i
netv any any ~~~~~~ kno -1t)pote: is
i 0-
~~~~~1~~~~.1. 1.1. Notations and definitions
Notations
and def
AJ I~~~~~~F Ir
Let G = (N, A) be a directed network with nodes and n arcs. Each arc (i,j) A has a cost cij, a capacity ,jy, and a lower bound , on the flow in the arc. If costs are integral, we let C denote max(lc ii: 1 (i,j) E A). If costs are not integral, then C = oc. We associate with each node i E N a number b(i) which indicates its supply or demand depending upon whether b(i) > 0 or b(i) < 0, respectively.
desci sho of tl algo
11-1
A ,
,k n
J.B. Orlin/ Mathematical Programming78 (1997) 109-129
111
The minimum cost flow problem can be stated as follows: Minimize subject to z(x) =
(i.
E
i)EA
cijxij
(a)
5
{j: (ij)A} iS
xj-
5
fj: (j,i)EA}
xj=b(i), forall ilN,
(lb)
(c)
ij < xij - uij ~ i
I
for all (i,j) E A.
.i I 7
II
-1 I
For convenience here, we modify the network flow problem by adding artificial arcs (1 ,j) and (j,l) for each node j 1. The capacity of each of these artificial arcs is cc, the lower bound on flow is 0, and the cost is + max(nlc j: (i,j)E A). These arcs may be used in the initial basic feasible solution, but no artificial arc will have a strictly positive flow in an optimal solution unless the original minimum cost flow problem is infeasible. For each feasible flow x, we associate residual capacities of the arcs as follows: If (i,j) E A, then the residual capacity of (i,j) is r = uij- xij, and the cost of (i,j) is coj. If (j,i) E A, then the residual capacity of (i,j) is rij = xj - Ij and the cost of (i,j) is c =-ci. The residual network, denoted by G(x), consists of all arcs whose residual capacity is strictly greater than 0. Thus, for any arc (i,j)E A, the residual network may contain arc (i,j) or (j,i) or both. We will use the notation "(i,j)" as though there is at most one arc directed from i to j in the residual network. The algorithm readily accommodates multiple arcs from i to j, but representing them as different arcs can be cumbersome. In general, this should cause no confusion in describing and analyzing the algorithm. (The reader may prefer to assume that there is at most one arc from i to j in the residual network.) In this paper, we define walks, directed walks, paths, directed paths, cycles, directed cycles, and cuts as in [1]. A vector of node potentials for the network G is a vector Tr with n components. For each vector r of node potentials, the reduced costs c are defined as follows: c,,i cij - -r, + ,rj. It is well known that minimizing the objective function cx for a network flow problem is equivalent to minimizing the objective function cx. Let W be any directed cycle, and let c(W) denote the sum of the costs of arcs of W. It is also well known that c(W)-= c(W). A flow x is said to be -optimzal with respect to the node Y tnt A fl nxx inf hn potentials ir ii 1 c: di arcs 41a7 k,J} 1l 1C ICtltQIUC1l IItWU kA).J\. LUW A LUIV is O-optimal is also optimal.
I4;1. A n t -T ri nr f1i cri rrr
1.2. Ouerview of the paper
1 |j
In Section 2, we describe the network simplex algorithm in a general form. We the pseudopolynomial version of the premnultiplier algorithm in Section 3 and mdescribe s this algorithm is a special case of the network simplex algorithm. In Section 4 that show of this paper, we give the details of the cost scaling variant of the premultiplier algorithm and show that the number of pivots per scaling phase is O(nml). We also show
--~~-~~-~---I -a
112
J.B. Orlin/ MathematicalProgramming 78 (1997) 109-129
that the number of scaling phases is O(min(log nC,mz log n)), and the amortized time per pivot is (n). In Section 5, we show that the diameter of the network polytope is
O(izrr log n).
The primary focus of this paper is on the worst-case analysis and on developing polynomial time primal network simplex pivot rules. Although we conjecture that the premultiplier algorithms introduced here can be implemented in a manner that is efficient in practice, we will not investigate practical implementations in this paper.
th( of by
D
w
Cc 2. The network simplex algorithm The network simplex algorithm maintains a basic feasible solution at each stage. A basic solution of the minimum cost flow problem is denoted by a triple (T,L,U); T, L, and U partition the arc set A. The set T denotes the set of basic arcs, that is, arcs of the spanning tree. L and U respectively denote the sets of non-basic arcs at their lower and upper bounds. We refer to the triple (TL,U) as a basis structure. The flow x associated with the basis structure is the flow obtained as follows: for each arc (i,j) E U, set Xij= ulij; for each arc (i,j) E L, set xij =I; obtain xij for each arc (i,j) E T so that constraints in (b) are satisfied. We say that the basis structure (T,L,U) is feasible if lij<xij<li for each arc
(i,j)E T.
the of re(
(k.
wi de(
coi set rec arc
COi oul
Non-degeneracy assumption. We will assume that every basic feasible solution is non-degenerate; that is, no tree arc is either at its lower bound or at its upper bound. The non-degeneracy assumption may sound like a severe restriction, but it is easily satisfied without loss of generality using a perturbation technique (see, for example, [10] and [241). One can increase b(1) by for some strictly positive but small value of , and decrease b(i) for every other node i by /(z - 1). Under the assumption that is sufficiently small, it can be shown that any optimal basic feasible solution for the perturbed problem is also optimal for the original problenm, and that every basic feasible flow is non-degenerate. Under the assumption that all supplies, demands and capacities
are integral, one can choose
= (n-
is obj
usc
)/n. In the case that the data are non-integral,
one can choose Cunningham's [28] combinatorial rule to carry out the pivots. This rule maintains a class of basic feasible solutions, called strongly basic feasible solutions. Cunningham developed this combinatorial rule and showed that it is equivalent to the perturbation technique described above. The non-degeneracy assumption implies that if x is the solution associated with the basis structure (TL,U), then G(x) contains all arcs of T as well as reversals of all arcs of T; that is, if (i,j) E T, then both (ij) and (j,i) will be in G(x). Our algorithms use two additional concepts.
Fig. node
.I---
------------s--L
C- ------
-- Y---i ---
- - ll-ii-. ---- qPa*- - ---
--
-w-------
--------
I--__ r -IPJ-rC ---
-I
Ok
J.B. Orlin/ Mathematical Programming 78 (1997) 109-129
113
)er Her
iDefinition
is ng :he is
1. We denote by G* (x) the subgraph of G(x) in which all arcs of T and their reversals have been deleted. (By the non-degeneracy assumption, G (x) consists
of those arcs (ij) E G( x) such that (j,i) G(x). Therefore, G
(x)
is fully determined
by the flow x.)
Definition 2. For any tree T and a root node v, we denote by T(v) a subgraph of G(x) which is a directed spanning in-tree T and in which all arcs are directed towards node v. Costs and capacities of arcs in T(u) are defined as in G(x).
A
5,,
We illustrate T(u) in Fig. . Fig. (a) is a tree rooted at node
whereas Fig. I(b) is
the same tree rerooted at node 4. Ihe arcs ot Ti) have the same orientation as the arcs
the and Lted
of T(4) except for the arcs on the path from 4 to in T(1). The arcs on this path are reoriented in T(4). Suppose that x is a basic feasible flow, and let T be the associated spanning tree. If
(k,l) E G (x), then the basic cycle W created by adding (k,l) to T is (k,l) together with the directed path from node to node k in T(k). To send flow around W is to decrease the residual capacity of each arc of W by = min(r;j: (i,j) E W), and
arc
is
1.
isily
[101
f c,
is
correspondingly increase the residual capacity of all the reverse arcs of W by . By sending units of flow around W, one of the arcs of W has its residual capacity reduced to 0. By the non-degeneracy assumption, > 0 and prior to sending flow around W there is a unique arc of W with residual capacity of . A simplex pivot consists of adding arc (k,1) to the tree, sending units of flow around W, and pivoting out the arc whose residual capacity is reduced to 0. In the case that the cost of the cycle is negative and > 0, the solution obtained by the simplex pivot has a strictly lower objective function than the solution prior to the pivot. The network simplex algorithm uses the following well-known fact:
the
;Ible
I1 .-
0--2-~0
I I I
i i i i
ities gral, rule ,ons. ) the
1 I
i I
Ii i I i
Ii i I i II i I
the l
LI
i
i I
I
(a) (b)
arcs
; use
Fig. . (a) An i-tree rooted at node 1. The arc values are costs. (b) The same in-tree as in (a) bt rooted at nod 4.
r I I C1CICI-.
- -- 111-1 bl I I
IILi
L------X--. -C-L--
C --IIIC--L---
114
J.B. Orlin / MathematicalProgramming 78 (1997) 109-129
Optimality conditions. A basis structure (T,L,U) is optimal if the cost of each basic
cycle is non-negative.
We now describe the network simplex algorithm in a very general form.
algorithm network-simplex;
i Ii e z I
II i
begin find a feasible basis structure (T,L,U); let x be the basic feasible flow; while x is not optimum do
begin find an arc (k,l) E G*(x) for which the corresponding basic cycle W has a
31
I i
Fig.
arc i,
negative cost; perform a simplex pivot by sending W; update x and (T,L,U); end
end;
= min(rij: (i,j) E W) units of flow around
T(v ers i F mull
(
Under the non-degeneracy assumption, the network simplex algorithm is finite since there are a finite number of basis structures, and the sequence of basis structures
(ij)
L
obtained by the algorithm have strictly decreasing objective function values.
A vector Xmof node potentials is called a vector of simplex multipliers for tree T if c(= O for all (ij) E T. In standard implementations of the network simplex algorithm, one maintains a vector of simplex multipliers for each basic feasible solution. Simplex
T( v
ofT
Proc
multipliers have the following computational advantage: if simplex multipliers are
maintained, then the cost of the basic cycle induced by the arc (k,l)E G (x) is c, therefore, one can test whether a basic cycle has negative cost by simply evaluating Cts = Ct,,- iTk + 71 and checking whether c < 0. This computational advantage comes
arc c ever,
)
redu redu<
at the cost of maintaining the simplex multipliers at each stage. The time to maintain the simplex multipliers is (n) steps per pivot in the worst case, although computational experience suggests that it is far less in practice.
redu( case,
In netw( Defir
3. The premultiplier algorithm In our implementation of the simplex algorithm, we will be maintaining a set of node
potentials that we refer to as "premultipliers". In this section, we define premultipliers and also describe a simple way of implementing the simplex algorithm using premultipliers, which we call the premultiplier algorithm. of node potentials is a set of premulltipliers witlh respect to the Definition 3. A vector rooted in-tree T(v) if c < for every arc (ij) E T(v). A vector if of node potentials f pe ipliers for tree T if it is a vecto of premultipliers with respect to is a ector
respe, premi eligib
is a vector Of'pretnurlltiplies for tree T if it is a vector of premultipliers wit7 respect to
Wne negati
."Mm..o , 1 , -1
J.B. Orlin/Mathematical Programming 78 (1997) 109-129
7' in
115
sic
i i
(D
A v
>--
0
2 I
0
5-5
I
34 0 f
I
0
(c)
2 5 I~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
(a)
(b)
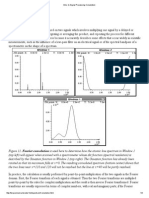
Fig. 2. (a) A spanning in-tree T(l) with arc costs. (b) The simplex multipliers. The reduced cost of each tree arc is 0. (c) Simplex premultipliers. Each arc of T(1) has a non-positive reduced cost. Ba
nd
T(u) for some node ut (Notice that simplex multipliers are a special case of premultipliers in which c= 0 for every arc (ij) in T(v).) Fig. 2(a) illustrates a spanning tree T(l), and Fig. 2(b) gives a set of simplex multipliers for the in-tree. Fig. 2(c) illustrates a set of premultipliers with respect to T(l). Each arc of the rooted in-tree has a non-positive reduced cost. If (ij) e T(l) and
(ij) qt A, then (j,i) E A, and its reduced cost is non-negative.
nce
Ires
r if
nm,
)lex are
Ckl, tin(
Lemma 1. Suppose that T is a tree, and mT is a set of premultipliers with respect to T(u). Then miT is also a set of premultipliers with respect to T(i) if and only if each arc of T on the path from node to node i has a reduced cost of O.
Proof. Note that T(i) may be obtained from T(v) by reversing the orientation of each
arc on the path P from i to v. Suppose first that each arc on the path P in T(u) has a reduced cost of 0. Then the reduced costs of the reversals of these arcs are also 0, and every other arc of T(i) has a non-positive reduced cost. Suppose now that somne arc (j,k) on the path P in T(v) from i to v has a reduced cost that is not 0. Then its reduced cost is negative, and in T(i) the reduced cost of (k,j) is positive. Thus in this case, r is not a vector of premultipliers with respect to T(i), leading to a contradiction.
roes
the anal
In the premultiplier algorithm, we define eligible arcs differently than in the standard network simplex algorithm. We also need the concept of eligible nodes. lode liers ultiDefinition 4. Let T denote a tree and let if denote a vector of premultipliers with respect to T(o) for some node v. We say that node i is eligible if r is a vector of premultipliers with respect to T(i). We call an arc (ij) e G (x) eligible if node i is eligible and c < 0.
)the tials
ct to
We will show in Lemma 2 that the basic cycles induced by eligible arcs have a negative cost. And in the premultiplier method that follows, each arc that is pivoted into
^-` I----UI"~I"J"pCBIR4aa4CrCbCI-C-l
.. ______lq4C13CI_
- - -I
--
llkg113C
_CLCCIB*IPILIIC--- -T----__ --l_--I___Lrr___l--_---_-b--lb
I---------------------
116
J.B. Orlin/ Mathematical Programming 78 (1997) 109-29
a spanning tree will be an eligible arc. In general, it is not the case that a negative reduced cost arc in G (x) induces a negative cost basic cycle. For instance, consider the
example in Fig. 2(c) and suppose that c 2
=-1.
pr be
Then the cost of the basic cycle
5-2-1-5 containing (5,2) is 2. fol
Lemma 2. Let T be a tree, and suppose that r is a set of prenmultipliers with respect to the rooted i-tree T(v). Then the basic cycle induced by each eligible arc has a negative
cost.
en
Tt
as to
Proof. Let W be a basic cycle in T(O) induced by the arc (k,l) and let wvbe the apex of cycle W. Then, W {(k,l)} U P U P' where P is a directed path from node I to node w
in TO), and P' is a path from node w to node k in T). Hence, c(W) = C6(W) = c7 6+Z +Z~~~~~~~j])E c ~~~~~~~~~~~~~~~~kIperfo, ecj7 + E(j) ,cfs. Since (i) c < 0 (by definition); (ii) c < 0 for each arc + Z(~j) P (because 'T is a set of premultipliers for T(v)); and (iii) c = 0 for each arc (ij) (i,j) P' (by Lemma ); it follows that c(W) < 0. w
W probl each
non-c
new 1 probi finite Lemi Lemi
step.
In the premultiplier algorithm described below, the entering arc is always an eligible arc. arc.
algorithm premultiplier; begin
Proo
T
choose an initial basic feasible solution x and a vector respect to T(v);struct while x is not optimal do if there is an eligible arc then
begin
of premultipliers with
perfo struct pliers Piers vector only c LeI
modif
select an eligible arc (k,l);nly
simplex-pivor( k,I );
end else mnodify-premultipliers; end;
this el
fy ~~~~~~~~~~~~~~~~~~both end; ~not end;,~~~~~~~~~~~~~~~~~~~~~
'T(v)
c cc
Increa
procedure simplex-pivot(k,l); bein
{W is (,) let W denote the basic cycle containing (k,i); in T(k)}; k let 8 = in(r: (ij) W); units of flow around W; send let (p,q) denote the arc of W that is pivoted out; reset the root of the tree to be p;
en;
\.1.
plus the path from I to
by A non-p( We is the, is a se basic from
J.B. Orlin/ Mathlematical Programming78 (1997) 109-129
117
tive the ycle
procedure modify-preimultipliers;
begin let S denote the set of eligible nodes; Q: = {(i,j) E T(v): i S, j E S};
a: = min(-cE: (i, j) Q); {observe that > 0 whenever S # N)
for each node j E S, increase rr by A;
:t to tive end;
The subroutine simplex-pivot pivots in the arc (k,l) and pivots out the arc (p,q) so as to maintain primal feasibility. It also adjusts the root node of the tree.
We will now prove that the premultiplier algorithm solves the minimum cost flow
x of le w
arc arc
problem correctly in a finite number of iterations. Our proof consists of showing that at each iteration the algorithm either increases the number of eligible nodes or performs a non-degenerate pivot. As there can be at most n eligible nodes, the algorithm will
perform a non-degenerate pivot within n iterations. Each non-degenerate pivot obtains a
new basis structure with lesser objective function value. Since the minimum cost flow problem has a finite number of basis structures, the premultiplier algorithm terminates
finitely.
;ible
Lemma 3. The premultiplier algorithn naintains step.
vector of premultipliers at every
with
Proof. We will prove the lemma by performing induction on the number of steps performed by the algorithm. By assumption, the result is true for the initial basis
structure. Let us first study the effect of an execution of the pliers. Let 7T be the premultipliers with respect to the rooted vector of premultipliers subsequently. We need to show that T(v). (Recall that the procedure modify-premultipliers does
only changes the premultipliers.)
procedure modify-premultitree T(v), and let rr' be the c < for each arc (ij) in not change the tree T(v), it
fLet S denote the set of eligible nodes with respect to the vector '-. The procedure
modify-premultipliers increases the premultiplier of each node in S by A units. Clearly, this change does not affect the reduced costs of those arcs in T(v) which have either both of their endpoints in S or neither of their endpoints in S. By definition, T(v) does not contain any arc () with i E S and j S. So we have only to consider those arcs in T(v) for which i S and E S. Notice that the algorithm denotes this set of arcs by Q. Increasing the potentials of nodes in S by A increases the reduced cost of every arc in Q by A units, but it is easy to see that each one of these reduced costs remains non-positive and the reduced cost of at least one of these arcs becomes zero. We now consider the execution of the procedure simzplex-pivot. Recall that arc (k,!) is the entering arc. Since (k,l) is an eligible arc, node k is an eligible node. Therefore, mr is a set of premltipliers with respect to T(k), and c < O for each arc in T(k). The basic cycle W induced by arc (k,l) consists of arc (k,l) and the tree path P in T(k) from node I to node k (see Fig. 3). Te subsequent flow augmentation reCILduces the
I to.
____II
118
J.B. Orlin / Mathematical Programming78 (1997) 109-129
We
anc
prc tre( not DeJ
rchn Fig. 3. llustrating the proof of Lemma 3.
beg
N"
capacity of exactly one arc (p,q) in W to zero. Let T' = T-( p,q) + (k,l). Then the orientation of each arc in T'( p) - {(k,l)} is the same as the orientation of the arc in T(k), and so ci'<0 for every arc in T'(p) - (k,l)}. Further, notice that c <
Del The
completing the proof.
D Def Noc Def
k is
In the preceding proof, we observed that in an execution of the procedure modifypremultipliers the reduced cost of some tree arc, say ( ,j3) satisfying a S and 3 E S, becomes zero. Consequently, node a becomes an eligible node after the procedure has been executed, establishing the following lemma.
Lemma 4. Each call of modify-premulltipliers strictly increases the ntumber of eligible nodes.
We are now ready to prove the main result of this section.
Theorem 1. The premurltiplier algoritnhm issa special case of the nzetvvork simplex algorithm. As such, it solves the mnitinium cost flow problem in a finite number iterations.
Tarj larj algo
pha
Proof. The premultiplier algorithm maintains a vector of premultipliers at every step and, therefore, the basic cycle induced by an eligible arc always has a negative cost. Therefore, the premultiplier method is a special case of the network simplex algorithm. The finiteness follows directly from the non-degeneracy assumption, which guarantees that basis structures are not repeated. l
a ve if a it int phas as f al be
4. The scaling premultiplier algorithm In this section, we apply the Goldberg-Tarjan [3] cost scaling algorithm to the premultiplier algorithm of Section 3. The resulting specialization of the primal network simplex algorithm runs in O(min(log nC,m log n)) scaling phases, each of which 2 log )). performs O(nnm) pivots. So the total number of pivots is O(min(nm log nC,nmO
en
PSPttBBiP*s-oCCM--5-rr_*F-. _I____^_ 'rlOll$*DIP-rs11428-I-rP---- _g__Ulllr---
----(ICIJlllll/I*1
I;
.:
J.B. Orlin / MathematicalProgramming 78 (1997) 109-129
.
119
We also show how to implement the algorithm so that the average time per pivot is O(n) and the total running time is O(min(n 2 m log nC,n2 m 2 log n)). Recently [23] has improved the amortized running time to O(log n) per pivot using a variant of dynamic trees. The cost scaling version of the premultiplier algorithm uses four additional notations which we define next. Definition 5. The set N* denotes a subset of nodes whose multipliers have yet to denotes the multipliers at the change during the e-scaling phase. For example, if orr beginning of the current scaling phase, and if r denotes the current multipliers, then
N* ={i: 7T= r.
the
t in
-Definition
<0
lThen,
r is a vector of -premultipliers if c > -
6. Let r be a vector of premultipliers with respect to a basic feasible flow x. for all arcs (i,j) in G(x).
(E SS,
Definition 7. We call a node awake if i E N* or if -r is an integral multiple of /4. Nodes that are not awake are called asleep. Definition 8. An arc (k,l) in CG (x) is called admissible for the -scaling phase if node k is an eligible and awake node, and c -c/4.
Thas
gible
i0 ~
Siplex
er of
'
er .it of
step
cost.
The cost scaling version of the premultiplier algorithm is similar to Goldberg and Tarjan's [3] cost scaling algorithm and performs a number of scaling phases. The algorithm maintains a set of -premultipliers. A scaling phase, called an -scaling phase, consists of an execution of the procedure improve-approximation which takes in a vector or of c-premultipliers with respect to a basic feasible solution x and transforms into a vector r' of c/2-premultipliers with respect to a basic feasible solution x'. The phase terminates when N' = 0. The formal description of the cost scaling algorithm is as follows.
algorithm scaling-premultiplier;
ithm. Lntees
begin choose an initial basic feasible solution x and a vector r of premultipliers with respect to T(v); e:= max(lcTi: c < 0, (i,j) E G(x)); while x is not optimal do begin
inprove-approximation( x, e,r);
o the twork which
,g n)).
: = max(I j <0O and (i,j) E (x)); {In general, e is decreased by at least a factor of 2 at each stage.} end;
end;
-- P--L-~~~~~----l-~~~----I-^ N -
r-.,-
-- -s-
C-I-
L-----C------CII-lll
--- --. L
--
120
J.B. Orlin / Mathematical Programming 78 (1997) 109-129
procedure improve-approximation(x, e,7r );
begin N * :=N; while N* # 0 do begin if there is an admissible arc do begin select an admissible arc (k,l); recall that c < - e/4} simplex-pivot(k, l); end else modify-c-premultipliers; end; end; procedure modify- -premultipliers; begin let S be the set of eligible nodes;
Or all
no
t
cu rez to reS in sta eli arc cuI coI the the inc bec
we
N :=N * -S;
if N * = 0 then terminate improve-approximation(x,,7r); ,:1 = min(- c7: (i,j) E T(v), i S, j E S);
,A2 = min(e/4 - n i (mod c/4): i E S);
increase %: by A = min(Al, 2 ) for each i E S; {observe that > 0 end; Observe that ri (mod e/4) E [0,/4), and so A2 > 0. In the procedure modify--premultipliers, we define A2 to be the least positive real number such that for some eligible node i, 7i + 2 is an integral multiple of /4. The subroutine simplex-pivot is the same subroutine as in the premultiplier algorithm described earlier. It pivots in the arc (k,l) and pivots out arc (p,q) so as to maintain primal feasibility. If arc (p,q) is pivoted out, then node p is set to be the root of the new spanning tree. By the non-deeneracy assumption, there is a unique choice for the leaving arc. There is a simpler version of this algorithm which uarantees the same number of pivots, but for which the running time is 0(m) per pivot. The changes needed are as follows: First, relax the definition of an admissible arc (i,j) so that node i is eligible, but not necessarily awake. In addition, we still require that (i,j) have residual capacity, and that the reduced cost of (i,j) is at most - c/4. Second, eliminate A2 in the modification of the premultipliers, and let = min(dA,,/4). These alterations in the algorithm do not affect the bound on the number of pivots nor do they affect the bound on the number of modifications of the premultipliers. With these modifications, the amortized time per pivot increases to O(in). In order to uarantee an amortized average time of O(n) per pivot, we need to be careful in how we identify admissible arcs. For this purpose, we maintain a widely used data structure, called the currenzt ar-c cdata structure (see, for example, [1]). Each node i has a current arc, which is an arc in G(x) and is the next candidate for admissibility testing. Initially, the current arc of node is the first arc emanating from node i. We
up tim ph2 adr
wh
aw; can for I
2. 1 3. 4.
alc Len pha
'g~aa~n8Crt~lrrsaaaara3~sll~ --
O .---
---- L
i-
---
---
i 'il
; I
J.B. Orlin/ Mathematical Pro graminig 78 (1997) 109-129
121
Ei
i: ~
j 4g~ g
reble the
ted
acy
i
of
as
~~as 4
ble, ity,
the
und the be
ised
the ,
assume that arcs emanating from each node are ordered in some fashion and this ordering once defined remains unchanged throughout the algorithm. Whenever the algorithm attempts to find an admissible arc emanating from node i, it tests whether the node's current arc is admissible. If not, it designates the next arc in the arc list as the current arc. The algorithm repeats this process until it either finds an admissible ar or reaches the end of the arc list. When the arc list is exhausted, the current arc of i is set to be 0, representing the fact that there are no arcs to scan. The current arc of node i is reset to FirstArc(i) when i is reawakened, that is, when the premultiplier of node i has increased to the next integral multiple of e/4. In a search for an admissible arc, the algorithm will first perform a depth first search starting at the root node to identify nodes that are eligible. For each node that is both eligible and awake, the algorithm will scan the node's arc list starting with its current arcs. The time to identify nodes that are both eligible and awake and for which the current arc is not null is O(n) following a pivot or update of premultipliers. We conclude that the number of times that arc (i,j) is scanned per scaling phase is at most the number of times in which node i is awakened. In principle, one could once again scan arcs emanating from node i as soon as increases; however, if one were to do so, then scanning for admissible arcs would become the bottleneck operation of the algorithm. In order to eliminate this bottleneck, we say that node i goes to sleep subsequent to scanning its arc list, and does not wake up until ri has increased by a total of /4 units. Since each node is awakened O(n) times per scaling phase (see Lemma 9), each arc is scanned O(n) times per scaling phase, for a total running time of O(nm) per scaling phase for scanning arc lists for admissible arcs. Moreover, suppose that the premultipliers are r' and the flow is x' when node i goes to sleep and the multipliers are 'r and the flow is x when node i awakens. Then for each arc (ij) E G(x'), c,, > - /4. Also ri r+ /4, and one can show that for each arc (i,j) e G( x), c > - ,/2. So /2-optimality is maintained for all arcs emanating from a node not in N (see Lemma 6). pWe now outline some important features of the cost scaling premultiplier algorithm. 1. As in the premultiplier algorithm of Section 3, during the -scaling phase, each multiplier will be monotonically non-cecreasing from iteration to iteration. Moreover, there will be at least one multiplier that does not change during the entire scaling phase, and each other multiplier will increase by at most 3ne/2. 2. Each arc (k) that is pivoted in is an admissible arc with reduced cost c < - /4, and so the cost of the basic cycle is less than or equal to - e/4. 3. Each arc (kl) will be pivoted in at most 6i times during a scaling phase, and the total number of pivots per scaling phase is 0(n7m7). 4. The number of scaling phases is O(min( n log n, log nC)).
de i ility
We
iu~sed iWe
will now establish a polynomial bound on the number of pivots performed by the algorithm. We will prove this result after establishing a series of lemmas. Lemma 5. Suppose that no is a vector of E-prentlltipliersobtained during the e-scaling
phase, and let i be any node tnot in N . Let 7r' be the vector f premulltipliers
i I.
122
J.B. Orlin / Mathematical Programming 78 (1997) 109-129
immediately prior to the most recent executionz of modify-s-premultipliers at which time i was both eligible and awake. Then 0 < i - rj < s/4.
that resp
Proof. Let nTo denote the premultipliers at the beginning of the scaling phase. We first note that node i is both eligible and awake at the first time that the potential of node i is increased in the -scaling phase, and so 7r' is well-defined. Consider first the case that i -T o < /4. In this case the lemma is easily seen to be true. We next consider the case that ir- m > s/4. In this case, let a be the largest integral multiple of /4 that is strictly less than 7rT.It follows that r - < /4, and r/ < a< rrTi. We will show that .r = a, and this will complete the proof. Consider the first iteration at which the premultiplier of node i is increased to a value that is at least a. By construction of 2 in the subroutine modify--premultipliers, the premultiplier of node i is increased to exactly a. Now consider the first iteration at which the premultiplier of node i is increased to a value that is strictly larger than a. At this iteration, node i was both eligible and awake. We conclude that node i will not again become awake until its node potential becomes a + s/4 > 7ri , and so rrT = a, completing the proof.
Lemma 6. Suppose that x is a basic feasible flow and that 7T is a vector of s-prenmultipliers obtained during the -scalingphase. For-all (ij) E G(x), if i _N , then c > - /2. In particular, if N = 0, then r is a vector of E/2-premultipliers with respect to x.
cons ther ther
resp
pha! E-sc
Lerr The? that Pro
Proc num indu, (,i) respE
Proof. Consider arc (i,j) G(x). Let r' be the vector of premultipliers immediately prior to the most recent iteration of modify--premultipliers at which time node i was both awake and eligible. At this point, arc (ij) was a tree arc or was an inadmissable non-tree arc, and so c > -/4 or else (i,j) had no residual capacity. Let us first consider the case that ct > -/4. In this case, c = c - (,') + (j - T). By Lemma 5, (rn - if) < E/4, and jf i>fj. It follows that ci >_ - c/4- c/4 + 0 =
-s/2.
It fo x'-. G(x a nui detai Let) of P
No
We now consider the case that (i,j) had no residual capacity at the iteration in which the premultipliers were i'. Suppose at some later iteration, when the pre-multipliers are
T', (i,j) receives some residual capacity. Arc (i,j) can receive residual capacity only when arc (j,i) enters the basis, and so c < -/4 implying c =-cf > s/4.
node, from
there
Moreover,
C=c C, - ( -i.-iT{) +( - i)) C C -(7F-i7T' + j( Tj.)
h to conc direct comp Lemr
> /4 - E/4 + O= O completing the proof. Cl
Lemma 7. Either somle node becomes awake subsequent to the eection of modify-spremultipliers or the number of eligible nodes strictly increases.
Proof. Let denote the vector of premultipliers prior to the execution of modtfy-s-premulltipliers, and let ' denote the premultipliers subsequlently. Let S denote the nodes
Proof the sdurint
*~sJi~sssrsanra
--
---
~-~b
L--m-"^---i-~lI '~-
---
----
-P-
J.B. Orli /Mathemnatical Programming78 (1997) 109-129
123
ne
rst
is
iat
that are eligible with respect to ir. Note that all of the nodes in S respect to F'. In the case that A = A,2 at least one node becomes consider the case that A = A.t This is the same case as in the proof of there is at least one node that is eligible with respect to r' that is respect to r. HI :~~~he ~We s~~at ,phase.
are eligible with awake. We now Lemma 4, and so not eligible with
:he
nat
>w
now proceed to bound the total increase in the multipliers during the scaling We will show in Lemmas 8 and 9 that each -rri increases by O(ne) during the -scaling phase. The counterpart of Lemmas 8 and 9 for pseudoflow algorithms for the minimum cost flow problem was proved in [3].
Lemma 8. Let x and x' denote any two distinct non-degenerate basic feasible flows. Then for any pair of nodes i and j, there is a path P in G( x) from node i to node j sulch that the reversal of P is a path from node j to node i in G(x').
lue the
at At not
ers
,oS *I~ ginductively d(ji) ;eY
tely was ible First By
9=
~ !
ich are nly
/4.
Proof. Let T denote the tree corresponding to the basic flow x. Let d(i,j) denote the number of arcs in the unique path from node i to node j in tree T. We prove the result on d(i,j). Consider first the case that d(i,j) = , and thus either (i,j) E T or E T. Suppose that (ij) T. Let r denote the residual capacity of (ji) with respect to x'. If r > 0, then let P = (i,j) and the result is true. So suppose that r = 0. It follows from the non-degeneracy assumption that rj, > . By flow decomposition, x' - x can be decomposed into flows around cycles each of which is a directed cycle in G(x). Equivalently, x may be transformed into x' by sequentially sending flow around a number of directed cycles, each of which is in G(x) (see, for example, [1] for more details). Since rj = O 0 < rj,, it follows that one of these cycles, say W, contains arc (j,i). Let P denote the path in W from node i to node j. Then P is in G(x), and the reversal of P is in G(x'), completing the proof in the case that (i,j) E T. Now suppose that d(i,j)= K> , and assume that the lemma is true for all pairs of nodes u and w such that d(uL,w) K - . Let h be the node that precedes j on the path from i to j in T. Thus d(i,h)= K- , and d(h,j)= 1. By the inductive hypothesis, there are paths P and P in G(x) such that P is a path from i to h, P is a path from h to j, and the reversals of P and P2 are in G(x'). Let P3 be a path obtained by concatenating P and P into a directed walk from i to j and then removing any directed cycles contained in the walk. Then P3 is in G(x) and its reversal is in G(x'), completing the proof. 3
Lemnma9. During the -scaling phase, -ri is increased by at most 3/2 nc units.
-pre-
odes
Proof. Let x denote the basic flow and r denote the premultipliers at the beginning of the -scaling phase. Let x' denote basic flow and m' the premultipliers at some iteration during the -scaling phase. Select a node j E N *. (The -scaling phase ends immedi-
~~I~~ _ _
___~~~~~_~-I
- -- ---1---1111.-L---31---
I-
._-
124
J.B. Orlin / Mathematical Programming78 (1997) 109-129
ately when N * = 0, and so throughout the scaling phase N* # 0.) By the definition of
vati( that Ler scahe sca are i with factc a nu a nu
<'
Let P be a path from node j to node i in G(x) such that the reversal of P, denoted as pr, is in G(x'). Without loss of generality, Z:v. rr ~ ~ $ we assume ~ ..r that ir node - r j is the only node cC ~ of -.
N* in P. (Otherwise, we could replace j by the last node je of N in P, and replace
P by the subpath P* of P from j* to i.) Then, it follows from the -optimality of the flow that
c7( P) = c( P) - 7+ Ti r -(n - 1)c.
Moreover, since every arc of P' emanates from a node in N-N*, it follows from Lemma 6 that
c '(Pr) = C(Pr) - i + Trj 2 -( - 1)
/2.
each
optin
does
Adding the negative of the above two inequalities and noting that (i) 7Tj = wr, and (ii) ) = 0 yields the following c(P) + c(Pr inequality: irr'< 7 i + 3(n - 1)c/2. 0
Lemma 10. The scaling premultiplier algorithmn performs at most 6nm pivots per scaling phase.
prool W
O(m not ii
Proof. In the -scaling phase, suppose that r is the vector of premultipliers at some iteration at which (i,j) or (j,i) is pivoted in, and that r' is the vector of premultipliers at the next iteration at which (i,j) or (j,i) is pivoted in again. We claim that , , rj> /2. By Lemma 9, wi and rj may each increase by at most 7 -ir f+ irj1
perm
phas
perm may1 phase y a Inre
3 n/
3nc/2 during the scaling phase. If our claim is true, then the number of iterations at
which (i,j) or (,i)is pivoted in is at most 6n, and the lemma would follow. We now justify our claim that r; - r. + f rrj> /2. Suppose that r is the J J---/ -- ~--~rr-------vector of premultipliers when arc (ij) is pivoted in. (The proof in the case when arc (j,i) is pivoted in at that iteration is essentially the same.) Thus, = Ci j- i + fj < - /4. Consider first the case that (j,i) is pivoted in when ' are the multipliers. Tlhen, r" C < - /4, and so c" =- C > e/4. It follows that -i %; , c/2 < cj - C, -= = i) + ( j - f) j) < ( ( < j) and thus the claim is true in this case. We now consider the case that arc (ij) in G(x) is pivoted in when ' is the vector of premultipliers. It is easy to see that in between the two iterations when (i,j) is pivoted
in, arc (j,i) must be pivoted out of the rooted in-tree (because when arc (i,j) is pivoted
incre;
Su
basic
dei
premt = c(V i each is pre
pivot
in, positive flow is sent from node i to node j and it cannot pivot in again until flow is
sent back from node j to node i). Let " be the vector of premultipliers when (j,i) is
pivoted out of the rooted in-tree 7(v). Since 7" is a vector of premultipliers and (j,i) E T(v), it follows that c 0, or equivalently c > 0. Since premultipliers are
non-decreasing during the scaling phase, r < T" < r'. Now observe that c j-/, +CCrj 0 and c +-7 t j 7i < -,E/4, cij - 7S-I + w> 0, and c 'r i + -' < - e/4. It follows from these obser!
Fin Acta Actua' pivot pivot I
Is*aaa*ar*srr*o*ssans
81 L-"-"arrrre
r---------LI-----
"-lrrr-rrr.------
I-----
-r
--
._I
J.B. Orlin/ MatlematicalProgramming78 (1997) 109-129
125
I of )ted
e of
vations that -T that - v + -
7r>
and 7 - vi , -T 2 is true, completing the proof.
Tj
>
/4
> c 0/4,
and so our claim
lace the
Lemma 11. The scaling premultiplier algorithm terminates in O(min(m log n, log nC)) scaling phases with an optimal flow.
Proof. We first bound the number of scaling phases to log nC in the case when the data are integral. The initial value of is O(nC). (Recall that we have added artificial arcs with cost nC + to create the initial basis.) By Lemma 6, decreases by at least a factor of 2 at each scaling phase. Thus, within O(log nO) scaling phases, is reduced to a number that is strictly less than l/n. We now claim that x is an optimal flow if e < I /n. By Lemma 6, -r is a vector of -premultipliers, and so c > - > - /n for each arc (i,j) in G(x). Suppose W is any directed cycle in G(x). Then c(W)= cr(W) -1. Since c(W) is integral, it also follows that c(W) 0, and thus the flow is optimal. (Here we make use of a well-known result that if the residual network G(x) does not contain any negative cycle, then x is an optimal flow.) This completes the proof that there are O(log nC) scaling phases. We now show that the number of scaling phases at which a pivot takes place is O(m log n). We say that an arc is permanently non-basic at the c-scaling phase if it is not in any feasible basis in the -scalin phase or in any subsequent phase. (The idea of permanently non-basic arcs is based on the work of Tardos [25,26].) For every scaling phase with a pivot, we will show that some arc in the spanning tree becomes permanently non-basic within (4 + [2 log n) additional scaling phases. Since each arc may become permanently non-basic at most once, this will bound the number of scaling phases with a pivot at (4mn + m[2 log nl).
Since () the total increase in r in the -scaling phase is 3c6/2, and (ii) decreases
rom
I (ii)
per
;ome )liers that most ns at
;
the
n arc
7rj <
by a factor of at least 2 in two consecutive scaling phases, it follows that the total increase in r, in the -scaling phase and all ubsequent scaling phases is bounded by 3n/2 3n/4+3ne/8+ =3nc. So if cJ> 3n during the e-scaling phase,
(ij) is permanently non-basic because its reduced cost will never become negative.
rhen,
Suppose that arc (ij) is pivoted in during the -scaling phase, and let W denote the basic cycle containing (ij) Then c(W) - /4 because arc (ij) is /4-eligible. Let c' denote the scale factor (4 + [2 log n1) scaling phases later, and let a' be the vector of
JICHUlllMPIClll
rrilita
r~llVr vni
iL LIC U-IlIIIIS
ln
o I
Oi
bC culldll
o dLa
Thn
pfiac>S.
oI
I-),=, n
liCIi %
t/ LIUt
2I) -).
7 1InusI1
-'(1
C
YV
lector
voted voted
ow is
ector tc
j,i) is
s and
rs are
Since W has at most n arcs, there is an arc (i,j) of W for which - 3 j < -3n '. Since r' is a vector of e'-premultipliers (and thus satisfies cj - 6' for each arc (i,j) in G(x)), it follows that arc (i,j) is not present in G(x). But then arc (j,i) is present in G(x), and c, > 3n '. erefore (j,i) is penmanently non-basic, which is what we wanted to prove. We conclllude that the number of scaling phases in which a
-
c(W)
< -4n 2 E'.
pivot takes place is O(ml log 17).
bse ij
>bser-I
Finally, we bound the number of scaling phases at which no pivot takes place. Actually, we will show that there are never two consecutive scaling phases in which no pivot takes place. Suppose that no pivot takes place at te E-scaing phase. Since no arc
1_1________^_11_____^_IYI1--
126
J.B. Orlin / Mathematical Programming 78 (1997) 109-129
is pivoted in, the subroutine mnodify--premultipliers is called consecutively until each node is eligible. So, at the end of the scaling ti a)phase, the vector r of premultipliers is a
vector of simplex multipliers, and each arc of the tree has a reduced cost of 0. At the
and per per
next scaling phase, the scale factor = max(- c c < 0). Thus there will be some arc (k,l) with ck = - . Since all nodes including node k are both eligible and awake, it follows that (kl) is an admissible arc, and thus a pivot takes place during this scaling phase. Therefore, the number of scaling phases is at most twice the number of scaling phases at which a pivot takes place, and this is O(m log n).
Lemma 12. The subroutine modify--premltipliers is executed O(nnm) times per scaling phase.
5. E
Tha
Tha
via
cons O(n
Proof. By Lemma 7, each execution of modlify-s-prenmultipliers either awakens a new node or it leads to an eligible node being added. By Lemma 9, the former case can happen at most 6n times per node, and thus 0(n2) times in total. We now bound the number of times that a new node is made eligible. Whenever a new node is made eligible in the subroutine modify-c-premultipliers, there is an arc (i,j) E T such that the reduced cost of (ij) was non-zero before the change in premultipliers, and the reduced cost was zero subsequently. We refer to this as cancelling a tree arc. We now claim that the number of times that an arc (i,j) can be cancelled is at most the number of times that (ij) is pivoted in. To see that, notice that the reduced cost of (ij) is negative when (ij) is pivoted in, and it remains negative
until either (ij) is cancelled or else (ij) is pivoted out. Once (ij) is cancelled, then the reduced cost of (ij) stays at zero until (i,j) is pivoted out. Thus each arc (i,j) is cancelled at most once in between successive times that (ij) i pivoted in, proving that
The Pro We dege L Ther algoi (bec
A pertu decrn
N.
(i,j) is cancelled O(n) times per scaling phase. We are now ready to prove our main result:
E unim progi a bo
Theorem 2. The scalinzg premultiplier algorithm solves a ninimum cost flow problemn in a sequence of O(min(m log n, log nC)) scatling phases, each of which has O(nn) 2 pivots. Moreover, the running time per scaling phase is O(n1 m).
progi O(n2
Proof. By Lemma 11, the number of scaling phases is O(min(m log n, log nC)), and the algorithm ends with an optimal flow. By Lemma 10, each scaling phase has O(nm) pivots. The time to send flow around the cycle and update the spanning tree is O(n) per pivot. If there is an admissible arc, then the time to find it is O(n) per pivot plus the time to update current arcs. We have noted earlier in this section that updating of current arcs requires O(nnz) time per scaling phase. By Lenma 12, there are O(nm) updates of the
vector of premultipliers in the subroutine modilf-E-p-emzultipliers. Each call of modify
pivot; the cc
Ackn Th
from
c-prelultitiplierspotentially involves scanning all of the nodes in N, once to compute A1
comrr
~~ffP~~~~n a a64d r
nr~~~~b~~n a~~
s~~---r--~~~~-sl-","Opp-
-~-l--
-- ,
J.B. Orlin / MathematicalProgramming 78 (1997) 109-129
127
ach is a the arc >,it ling ting -
and once to compute A2 , and thus takes O(n) time. We conclude that the running time per scaling phase is O(n2 m). w
5. Diameter of the network polytope In this section, we show that the diameter of the network polytope is O(nm log n). That is, for any basic feasible solutions x' and x*, it is possible to obtain x* from x' via a sequence of O(nm log n) primal simplex pivots. Our proof uses the same construction as does [22], who showed that the diameter of the network polytope is O(n 2 m log n).
Theorem 3. The diameter of the network polytope is O( nm log n).
ling
per
new can the
iers,
the is as n be that -tive . the
j) is
Proof. Let x' be a basic feasible solution corresponding to the basis structure (T,L,U). We first consider the case in which every basis is non-degenerate. We consider the degenerate case subsequently. < i < u. if - I=1 if xI = O let c =-1 if x= Let 2 = u,, and let cO Then x is the unique optimum flow that minimizes c x. Using the premultiplier algorithm, one can obtain x* as a sequence of O(nm log nC)= O(nnm log n) pivots (because C = 0(1)). We now consider the case that bases may be degenerate. We observe that by perturbing the right-hand side to make the problem non-degenerate, the diameter can not decrease. So the diameter of the degenerate problem is bounded as well by O(nm log n).
; that Network flow problems are a special case of linear proarams defined on totally unimodular matrices. Dyer and Frieze [27] showed that the diameter of these linear programs is pplynomially bounded, but their ingenious proof technique did not result in a bound of low degree. Their bound on the diameter of totally unimodular linear programming polytopes s a polynomial or nhhn egree, one that exceeds the 2 O(n m log n) bound of Goldfarb and Hao as well as the result presented here. We note that the results of Section 4 show that there is a sequence of O(nm log nC) pivots moving from any basic feasible solution to another basic feasible solution so that the costs are monotonically non-decreasing (or non-increasing).
in LnI (amni)
.d the
( nm)
z) per
, f;n A rl rnnrlnrlrvnr-nn fe
t arcs )f the
odifyite A1
This paper was partially supported by ONR Grant N00014-94-1-0099 and a grant from the UPS foundation. I want to thank Charu Aggarwal and Izumi Sakuta for helpful comments on an earlier draft of this manuscript. want to thank both Don Goldfarb and
m-
-(Rlr~~QII~*ILP
I'll I 111-
---
r13nar~ls*ar~r
"ls~
-----
c--------
--
------------
28
J.B. Orli / Mathematical Programming 78 (1997) 109-129 [23]
Ravi Ahuja for encouraging my work on the problem of finding a polynomial-time primal network simplex algorithm. I also wish to thank Ravi Ahuja for extensive editorial suggestions that led to simplifications at several points, improvements in notation at several points, and that filled in a number of small gaps in arguments. His suggestions led to numerous improvements in the exposition.
[24] [251
[26] [271
References
[1] R.K. Ahuja, T.L. Magnanti and J.B. Orlin, Network Flows: Teory, Algorithms and Applications
[28]
(Prentice Hall, Englewood Cliffs, NJ, 1993).
[2 R.K. Ahuja, A.V. Goldberg, J.B. Orln and RE. Tarjan, Finding minimumn-cost flows by double scaling,
Mathematical Programming 53 (1992) 243-266.
[3] A.V. Goldber and R.E. Tarjan, Solving minimum cost flow problem by successive approximation,
Mathematics of Operations Research 15 (1990) 430-466. [4] J.B. Orlin, A faster strongly polynomial minimum cost flow algorithm, Operations Research 41 (1993) 338-350.
[5] N. Zadeh, A bad network problem for the simplex method and other minimum cost flow algorithms,
Mathematical Programming 5 (1973) 255-266.
[6] R.E. Tarjan, Efficiency of the primal network simplex algorithm for the minimumn-cost circulation
problem, Mathematics of OperationsResearch 16 (1991) 272-291. [7] R.K. Ahuja and J.B. Orlin, The scaling network simplex algorithm, OperationsResear-ch 40, Supplement I (1992) S5-S 13. [81 M. Akoul, A enuinely polynomial primal simplex algorithm for the assignment problem, Discrete Applied Mathematics 45 (1993) 93-115.
[9
M.S. Hung, A polynomial simplex method for the assignment problem, Operations Research 31 (1983)
595-600. [10] J.B. Orlin, On the simplex algorithm for networks and generalized networks, Mathematical Programming Study 24 (1985) 166-178.
[1I1] PT. Sokkalinoam, P. Sharma and R.K. Ahuja, A new primal simplex aorithm for network flow
problem, Unpublished manuscript, 1993; Presented at NETFLOW'93 at San Miniato, Italy.
[12] M. Aaul, Shortest path and simplex method, Research Report, Department of Computer Science and
Operations Research, North Carolina State University, Raleigh, NC, I 985. [13] R. Dial, F. Glover, D. Karney and D. Klingman, A computational analysis of alternative algorithms and labeling techniques for finding shortest path trees, Nevtworks. 9 (1 979) 215-248. [14] D. Goldfarb, J. Hao and S. Kai, Efficient shortest path simplex algorithis, Operations Research 38 (1990) 624-628. [151 A.V. Goldberg, M.D. Grigoriadis and R.E. Tarjan, Use of dynamic trees in a network simplex algorithm for the maximum flow problem, Mathematical Programming 50 (1991) 277-290. [16] D. Goldfarb and J. Hao, A primal simplex algorithm that solves the maximum flow problem in at most nm pivots and O(n 2 m) time, Mathematical Programming 47 (1990) 353-365. [17] D. Goldfarb and J. Hao, On strongly polynomial variants of the network simplex algorithm for the maximum flow problem, Operations Research Letters 10 (1991) 383-387.
[18] J.B. Orlin, Genuinely polynomial simplex and nonsinmplex algorithms for the minimum cost flow
problem, Technical Report No. 1615-84, Sloan School of Management, MIT, Cambridge, MA, 1984.
[19] S.A. Plotkin and E. Tardos, Improved dual network simplex, in: Poceedings o rhe 1.st ACM-SIAM
Sympositum on Discrete Algorithms (1990) 367-376.
[20] J.B. Orlin, S.A. Plotkin and E. Tardos, Polynomial dal network sinmplex algorithms, Mathematical
Programming 60 (1993) 255-276.
[21] R. Armstrong and Z. Jin, A strongly polynomial dual nletwork simplex algorithm, Mathematical
Programming 78 (1997) 131-148. [22] D. Goldfarb and J. Hao, Polynomial simplex algorithnms for the minimnm cost network flow problem, AIgorithmica 8 (1992) 145-160.
:"?saenawmaslrr*aoaraaraa4n*wlcplsl
I-----"k------b
lt
III
------
- ------rs-
-- r
J.B. Orlin/ Mathematical Programming 78 (1997) 109-129
129
ime
[23] R.E. Tarjan, Dynamic trees as search trees via Euler tours, applied to the network simplex algorithm, MMathematical Programming 78 (1997) 169-177.
;ive
in His
flows, in: G.L. Nemhauser, A.H.G. Rinnooy Kan and [24] R.K. Ahuja, T.L. Magnanti and J.B. Orlin, Network Research and Management Science. Vol. 1: Optimization
M.J. Todd, eds., Handbooks in Operations (North-Holland, Amsterdam, 1989) 211-369. [25] E. Tardos, A strongly polynomial minimum cost circulation algorithm, Combinatorica5 (1985) 247-255. [26] E. Tardos, A strongly polynomial algorithm to solve combinatorial linear programs, Operations Research 34 (1986) 250-256.
[27] M. Dyer and A. Frieze, Random walks, totally unimodular matrices and a randomised dual simplex
algorithm, Mathematical Programming 64 (1994) 1-16. [28] W.H. Cunningham, A network simplex method, Mathematical Programming 11 (1976) 105-116.
tions tling, ition,
t993)
thmns, lation ,ment 'crete 1983) iming flow :e and is and ch 38 orithm t most or the t flow )84. -SIAM natical natical oblem,
p
i i
r*glliiFisf
- -- C-l I I----- - -
-- - -------rar---L---------.r
--I ------------___---r----rre--------L----I - 3LICr_-------I-----.--s -------- -------.---------
You might also like
- Performance Analysis of Power Line Communication Using DS-CDMA Technique With Adaptive Laguerre FiltersDocument5 pagesPerformance Analysis of Power Line Communication Using DS-CDMA Technique With Adaptive Laguerre FiltersMasterArvinNo ratings yet
- Reduced-Complexity LLL Algorithm For Lattice-Reduction-Aided MIMO DetectionDocument5 pagesReduced-Complexity LLL Algorithm For Lattice-Reduction-Aided MIMO DetectionRasool FarajiNo ratings yet
- 26-Scope and Definition of Network Models, Minimum Spanning Tree Algorithm-04-02-2023Document12 pages26-Scope and Definition of Network Models, Minimum Spanning Tree Algorithm-04-02-2023pegan22525No ratings yet
- Theory Flow Graphs : Feedback - Further SignalDocument7 pagesTheory Flow Graphs : Feedback - Further SignalmeifiusNo ratings yet
- An Ant Algorithm For Solving Qos Multicast Routing Problem: A. YounesDocument12 pagesAn Ant Algorithm For Solving Qos Multicast Routing Problem: A. YounesPethaperumal PerumalNo ratings yet
- Phase Domain Modelling of Frequency Dependent Transmission Lines by Means of An Arma ModelDocument11 pagesPhase Domain Modelling of Frequency Dependent Transmission Lines by Means of An Arma ModelMadhusudhan SrinivasanNo ratings yet
- Optimal Circuits For Parallel Multipliers: Paul F. Stelling,,, Charles U. Martel, Vojin G. Oklobdzija,,, and R. RaviDocument13 pagesOptimal Circuits For Parallel Multipliers: Paul F. Stelling,,, Charles U. Martel, Vojin G. Oklobdzija,,, and R. RaviMathew GeorgeNo ratings yet
- Advance Computer ArchitectureDocument16 pagesAdvance Computer ArchitecturePunam SahuNo ratings yet
- 00001476Document8 pages00001476damaya1701No ratings yet
- Trabajo HerreolenDocument76 pagesTrabajo Herreolenrorrito33No ratings yet
- VitterDocument21 pagesVitterManfred SniffelNo ratings yet
- TR (Zak) : Xo+z,' Z + ZDocument5 pagesTR (Zak) : Xo+z,' Z + ZSara WigginsNo ratings yet
- Research Article: Efficient Congestion Mitigation Using Congestion-Aware Steiner Trees and Network Coding TopologiesDocument9 pagesResearch Article: Efficient Congestion Mitigation Using Congestion-Aware Steiner Trees and Network Coding TopologiesRagini SandhyaNo ratings yet
- Basic Op of CryptoDocument13 pagesBasic Op of CryptoSaifullah Khalid100% (1)
- Finding The Shortest Path in Dynamic Network UsingDocument5 pagesFinding The Shortest Path in Dynamic Network UsingyuvashreeNo ratings yet
- An Efficient Algorithm For The Evaluation of Convolution IntegralsDocument22 pagesAn Efficient Algorithm For The Evaluation of Convolution IntegralsCarlangasPardoNo ratings yet
- Statistical service guarantees in networks using effective service curvesDocument21 pagesStatistical service guarantees in networks using effective service curveseugeneNo ratings yet
- Minimum-Cost Spanning Tree Asa Path-Finding Problem: Laboratory For Computer Science MIT Cambridge MA 02139Document5 pagesMinimum-Cost Spanning Tree Asa Path-Finding Problem: Laboratory For Computer Science MIT Cambridge MA 02139Kevin SkoutNo ratings yet
- 1982 - Algorithm 583 LSQR Sparse LinearDocument15 pages1982 - Algorithm 583 LSQR Sparse LinearluongxuandanNo ratings yet
- IOSR JournalsDocument7 pagesIOSR JournalsInternational Organization of Scientific Research (IOSR)No ratings yet
- Oerder Meyer PDFDocument8 pagesOerder Meyer PDFKarthik GowdaNo ratings yet
- Optimised Timing Error Detection Algorithm for Digital ReceiversDocument2 pagesOptimised Timing Error Detection Algorithm for Digital ReceiverscvccrmNo ratings yet
- Agente Viajero 4Document24 pagesAgente Viajero 4Mauro Michel Ramirez GuerraNo ratings yet
- Effective Algorithms For Designing Power Distribution NetworksDocument8 pagesEffective Algorithms For Designing Power Distribution Networksdocs miNo ratings yet
- Ahuja1990 FasterDocument11 pagesAhuja1990 FasterdnyNo ratings yet
- Subex Linear ProgrammingDocument19 pagesSubex Linear ProgrammingkokoroNo ratings yet
- 6 Prim SimplexDocument17 pages6 Prim Simplexdco2012No ratings yet
- Rayleigh Fading Multi-Antenna Channels Alex Grant: This Work Was Supported by Nortel NetworksDocument4 pagesRayleigh Fading Multi-Antenna Channels Alex Grant: This Work Was Supported by Nortel NetworkslalithyadiviNo ratings yet
- Mpi I 97 1 010Document9 pagesMpi I 97 1 010Anant ChhajwaniNo ratings yet
- Davis Analysis of Active RC Networks by DecompositionDocument3 pagesDavis Analysis of Active RC Networks by Decompositionbenitogaldos19gmail.comNo ratings yet
- Practical Issues Implementing Analog-to-Information: ConvertersDocument6 pagesPractical Issues Implementing Analog-to-Information: ConvertersMimitech JohnNo ratings yet
- 0407 Is I VC Block Adaptive FiltersDocument4 pages0407 Is I VC Block Adaptive FiltersRaj Ranjan SinghNo ratings yet
- Research On Flux Observer Based On Wavelet Neural Network Adjusted by Antcolony OptimizationDocument5 pagesResearch On Flux Observer Based On Wavelet Neural Network Adjusted by Antcolony OptimizationKameleon TaliNo ratings yet
- Vlsi Final Notes Unit4Document21 pagesVlsi Final Notes Unit4RohitParjapatNo ratings yet
- Training Feed Forward Networks With The Marquardt AlgorithmDocument5 pagesTraining Feed Forward Networks With The Marquardt AlgorithmsamijabaNo ratings yet
- TPWL IeeeDocument6 pagesTPWL Ieeezhi.han1091No ratings yet
- DCC2006 SoundCardProgramming F6CTEDocument6 pagesDCC2006 SoundCardProgramming F6CTEProyec YectosNo ratings yet
- Itt - (J+L) TI.v (T-JT) J: (Half Short-Circuits) .) )Document8 pagesItt - (J+L) TI.v (T-JT) J: (Half Short-Circuits) .) )Luisa De CairesNo ratings yet
- LE PaperDocument16 pagesLE PaperYagami LightNo ratings yet
- ISORA2008F07Document6 pagesISORA2008F07carboneze9706No ratings yet
- Algebraic Survivor Memory Management Design For Viterbi DetectorsDocument6 pagesAlgebraic Survivor Memory Management Design For Viterbi Detectorsapi-19790923No ratings yet
- A Simple Parallel Algorithm For The Single-Source Shortest Path Problem On Planar DigraphsDocument22 pagesA Simple Parallel Algorithm For The Single-Source Shortest Path Problem On Planar DigraphsKimlong NguyenNo ratings yet
- Network ModelDocument9 pagesNetwork ModelnyapeteNo ratings yet
- Daa Module 1Document26 pagesDaa Module 1Abhishek DubeyNo ratings yet
- Modeling and Optimization of Drilling ProcessDocument9 pagesModeling and Optimization of Drilling Processdialneira7398No ratings yet
- Computer Solution: Digital Electromagnetic Transients Multiphase NetworksDocument12 pagesComputer Solution: Digital Electromagnetic Transients Multiphase NetworksObed GarcíaNo ratings yet
- Domme 1967Document12 pagesDomme 1967Carlos ChávezNo ratings yet
- Parallel Algorithms and Architectures 1Document22 pagesParallel Algorithms and Architectures 1Ismael Abdulkarim AliNo ratings yet
- Review of Linear Time-Invariant (Lti) Multi-Port System TheoryDocument48 pagesReview of Linear Time-Invariant (Lti) Multi-Port System TheoryUtah UtahNo ratings yet
- ISPDC03Document6 pagesISPDC03tibobernardNo ratings yet
- 9 Bus System DataDocument16 pages9 Bus System DataKiran Mula40% (5)
- Hybrid Control of Load Simulator For Unmanned Aerial Vehicle Based On Wavelet NetworksDocument5 pagesHybrid Control of Load Simulator For Unmanned Aerial Vehicle Based On Wavelet NetworksPhuc Pham XuanNo ratings yet
- Neural Networks for System IdentificationDocument5 pagesNeural Networks for System IdentificationLissete VergaraNo ratings yet
- Computers and Mathematics With ApplicationsDocument10 pagesComputers and Mathematics With Applicationsalireza khoshnoodNo ratings yet
- Bandwidth Minimization Algorithm For Finite Element MeshDocument13 pagesBandwidth Minimization Algorithm For Finite Element MeshSyed MustafaNo ratings yet
- Introduction to Signal Processing: Fourier ConvolutionDocument3 pagesIntroduction to Signal Processing: Fourier ConvolutionSiddharth KumarNo ratings yet
- Representation of Switching Circuits by Binary-Decision ProgramsDocument15 pagesRepresentation of Switching Circuits by Binary-Decision ProgramsTurmaAlimentos testeNo ratings yet
- BER and PAPR Reduction Using Companding Algorithms in OFDMDocument5 pagesBER and PAPR Reduction Using Companding Algorithms in OFDMInternational Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- Spline and Spline Wavelet Methods with Applications to Signal and Image Processing: Volume III: Selected TopicsFrom EverandSpline and Spline Wavelet Methods with Applications to Signal and Image Processing: Volume III: Selected TopicsNo ratings yet
- Network Flow AlgorithmsDocument33 pagesNetwork Flow AlgorithmsttunglNo ratings yet
- SolutionsDocument5 pagesSolutionsPhillipe El HageNo ratings yet
- Ok Network 5Document141 pagesOk Network 5ttunglNo ratings yet
- Resume OnepageDocument1 pageResume OnepagettunglNo ratings yet
- Ok LpmultiDocument16 pagesOk LpmultittunglNo ratings yet
- Msms 2Document19 pagesMsms 2ttunglNo ratings yet
- Nsdi10 Al FaresDocument15 pagesNsdi10 Al FaresttunglNo ratings yet
- Ok MCF 2011 - 3Document42 pagesOk MCF 2011 - 3ttunglNo ratings yet
- n10 MincostflowDocument10 pagesn10 MincostflowttunglNo ratings yet
- IPOV WS06 MultiCommodityFlowDocument17 pagesIPOV WS06 MultiCommodityFlowttunglNo ratings yet
- Min Cost NewDocument15 pagesMin Cost NewttunglNo ratings yet
- Mincostflow NotesDocument95 pagesMincostflow NotesttunglNo ratings yet
- MCMCF TRDocument19 pagesMCMCF TRttunglNo ratings yet
- Master Mincostflow NahabedianDocument41 pagesMaster Mincostflow NahabedianttunglNo ratings yet
- Lecture 21Document16 pagesLecture 21ttunglNo ratings yet
- Lecture 7Document34 pagesLecture 7ttunglNo ratings yet
- IPOV WS06 MultiCommodityFlowDocument17 pagesIPOV WS06 MultiCommodityFlowttunglNo ratings yet
- 2013 06459492Document13 pages2013 06459492ttunglNo ratings yet
- The Multi-Commodity Network Flow ProblemDocument2 pagesThe Multi-Commodity Network Flow ProblemStephen HartantoNo ratings yet
- An Mincostflow 2013Document22 pagesAn Mincostflow 2013ttunglNo ratings yet
- Improved Approximation Algorithms For The Multi-Commodity Flow Problem and Local Competitive Routing in Dynamic NetworksDocument10 pagesImproved Approximation Algorithms For The Multi-Commodity Flow Problem and Local Competitive Routing in Dynamic NetworksttunglNo ratings yet
- An Mincostflow 2013Document22 pagesAn Mincostflow 2013ttunglNo ratings yet
- Min Cost Flow and Succsesive Shortest Path AlgorithmDocument18 pagesMin Cost Flow and Succsesive Shortest Path AlgorithmRobel SharmaNo ratings yet
- Overall Cost Minimization For Data Aggregation in Energy-Constrained Wireless Sensor NetworksDocument5 pagesOverall Cost Minimization For Data Aggregation in Energy-Constrained Wireless Sensor NetworksttunglNo ratings yet
- MATHEMATICAL BIOSCIENCES AND ENGINEERINGDocument4 pagesMATHEMATICAL BIOSCIENCES AND ENGINEERINGttunglNo ratings yet
- Min Cost Flow ProblemsDocument22 pagesMin Cost Flow ProblemsttunglNo ratings yet
- (Stephen P Borgatti, Martin G. Everett, Jeffrey C. (B-Ok - CC) PDFDocument320 pages(Stephen P Borgatti, Martin G. Everett, Jeffrey C. (B-Ok - CC) PDFAritra HalderNo ratings yet
- Shivam Garg: ResumeDocument2 pagesShivam Garg: ResumeShivamNo ratings yet
- PMP Study Plan Waleed Elbasyouni 2018 PDFDocument1 pagePMP Study Plan Waleed Elbasyouni 2018 PDFTarek Khafaga100% (1)
- Ultimate 8043 Instructions Part 1Document15 pagesUltimate 8043 Instructions Part 1Catalin JipescuNo ratings yet
- Flipkart Customer Care Mail PDFDocument2 pagesFlipkart Customer Care Mail PDFAvik DasNo ratings yet
- 1.3 Predicates and Quantifiers: Uniqueness Quantifier Quantifiers With Restricted DomainsDocument7 pages1.3 Predicates and Quantifiers: Uniqueness Quantifier Quantifiers With Restricted DomainsKhairah A KarimNo ratings yet
- NumericalDocument663 pagesNumericalJingzhou Wang100% (4)
- SwotDocument2 pagesSwotapi-465380027No ratings yet
- SE05Document5 pagesSE05Nguyen Anh TuNo ratings yet
- Linux AdminDocument44 pagesLinux Adminchaits258No ratings yet
- E-Studio 450S 500S (SM, PC)Document525 pagesE-Studio 450S 500S (SM, PC)Donot Spamme100% (1)
- Difference Between Smoke and Sanity TestingDocument7 pagesDifference Between Smoke and Sanity TestingantoniealbertoNo ratings yet
- 3gpp XML File Format SpecificationDocument16 pages3gpp XML File Format SpecificationMansour FallNo ratings yet
- Comparison Between Labview DSC and Other SCADA Software - NI Discussion ForumsDocument1 pageComparison Between Labview DSC and Other SCADA Software - NI Discussion Forumsiosmaris2331No ratings yet
- Sap Businessobjects Rapid Marts Overview - 1: Applies ToDocument10 pagesSap Businessobjects Rapid Marts Overview - 1: Applies ToDanai PiyaNo ratings yet
- Pattern Matching and ReplacementDocument3 pagesPattern Matching and ReplacementSuperquantNo ratings yet
- SALA-Advanced Econometrics II 10 11-SyllabusDocument3 pagesSALA-Advanced Econometrics II 10 11-SyllabusalecarboNo ratings yet
- Radio Jockey CourseDocument3 pagesRadio Jockey CoursebhabanipinkyNo ratings yet
- Model-Based Testing For ERPDocument13 pagesModel-Based Testing For ERPBPMXchangeNo ratings yet
- CandidateHallTicket UPPCL PDFDocument2 pagesCandidateHallTicket UPPCL PDFmahesh dubeyNo ratings yet
- GATE Study Material: 10 QuestionsDocument96 pagesGATE Study Material: 10 QuestionsGulshan SinghNo ratings yet
- Digitization: An Overview of Issues: Prof. Harsha ParekhDocument10 pagesDigitization: An Overview of Issues: Prof. Harsha ParekhkhujistamahmoodNo ratings yet
- EQuIS Data Processor Reference ManualDocument26 pagesEQuIS Data Processor Reference ManualtimjiminNo ratings yet
- Binary OperationDocument17 pagesBinary OperationSheryl Grace Padilla Delo100% (1)
- IT Project Management Solutions ManualDocument7 pagesIT Project Management Solutions ManualMinato ArisatoNo ratings yet
- COMP 171 Data Structures and Algorithms Spring 2005Document12 pagesCOMP 171 Data Structures and Algorithms Spring 2005Gobara DhanNo ratings yet
- Embedded C - PeKDocument189 pagesEmbedded C - PeKRoland VladutescuNo ratings yet
- Stochastic ProcessDocument1 pageStochastic ProcessROHIT NARAYANINo ratings yet
- Graph TraversalDocument4 pagesGraph TraversalnemonizerNo ratings yet
- RAS Notification 2007Document12 pagesRAS Notification 2007jaipurite100% (5)