Professional Documents
Culture Documents
VPN Site-Site TAR 15
Uploaded by
Eduardo0 ratings0% found this document useful (0 votes)
59 views4 pagesVPN
Original Title
VPN Site-site TAR 15
Copyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentVPN
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
59 views4 pagesVPN Site-Site TAR 15
Uploaded by
EduardoVPN
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
You are on page 1of 4
U.C.S.M. Ing.
de Sistemas Tpicos Avanzados en Redes
Pgina: 1
UNIVERSIDAD CATLICA DE SANTA MARA
PROGRAMA PROFESIONAL DE INGENIERA DE SISTEMAS
SESIN 15:
Configuracin VPN
I
OBJETIVOS
Configuracin EIGRP en los routers
Crear un VPN site to site IPSEC
II
ACTIVIDADES
Configuracin VPNs Site-to-Site IPsec con CLI IOS
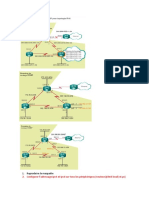
Topology Diagram
Ing. Karina Rosas Paredes
Ing. Jose Esquicha Tejada
Ing. Leticia Laura Ochoa
Prctica 15
1.- Configurar interfaces
2.- Configurar protocolo de enrutamiento EIGRP 100
3.-Configurar polticas ike
R1(config)# crypto isakmp enable
R1(config)# crypto isakmp policy 10
R1(config-isakmp)# authentication pre-share
R1(config-isakmp)# encryption aes 256
R1(config-isakmp)# hash sha
R1(config-isakmp)# group 5
R1(config-isakmp)# lifetime 3600
R3(config)# crypto isakmp enable
R3(config)# crypto isakmp policy 10
R3(config-isakmp)# authentication pre-share
R3(config-isakmp)# encryption aes 256
R3(config-isakmp)# hash sha
R3(config-isakmp)# group 5
R3(config-isakmp)# lifetime 3600
R1(config)# crypto isakmp key cisco address 192.168.23.3
R3(config)# crypto isakmp key cisco address 192.168.12.1
R1# show crypto isakmp policy
4.- Configurar polticas ipsec
R1(config)# crypto ipsec transform-set 50 esp-aes 256 esp-sha-hmac
R1(cfg-crypto-trans)# exit
R3(config)# crypto ipsec transform-set 50 esp-aes 256 esp-sha-hmac
R3(cfg-crypto-trans)# exit
R1(config)# crypto ipsec security-association lifetime seconds 1800
R3(config)# crypto ipsec security-association lifetime seconds 1800
5.-Definir trfico interesante
R1(config)# access-list 101 permit ip 172.16.1.0 0.0.0.255 172.16.3.0 0.0.0.255
R3(config)# access-list 101 permit ip 172.16.3.0 0.0.0.255 172.16.1.0 0.0.0.255
Ing. Karina Rosas Paredes
Ing. Jose Esquicha Tejada
Ing. Leticia Laura Ochoa
Prctica 15
6.- crear crypto map
R1(config)# crypto map MYMAP 10 ipsec-isakmp
R1(config-crypto-map)# match address 101
R1(config-crypto-map)# set peer 192.168.23.3
R1(config-crypto-map)# set pfs group5
R1(config-crypto-map)# set transform-set 50
R1(config-crypto-map)# set security-association lifetime seconds 900
R3(config)# crypto map MYMAP 10 ipsec-isakmp
R3(config-crypto-map)# match address 101
R3(config-crypto-map)# set peer 192.168.12.1
R3(config-crypto-map)# set pfs group5
R3(config-crypto-map)# set transform-set 50
R3(config-crypto-map)# set security-association lifetime seconds 900
R1(config)# interface fastethernet0/0
R1(config-if)# crypto map MYMAP
R3(config)# interface serial0/0/1
R3(config-if)# crypto map MYMAP
R1# show crypto ipsec transform-set
R1# show crypto map
R1# show crypto isakmp sa
R1# show crypto ipsec sa
Pruebe un Ping extendido desde el R1 con interfaz origen la loopback0, hacia el la loopback 0 del R3.
Ing. Karina Rosas Paredes
Ing. Jose Esquicha Tejada
Ing. Leticia Laura Ochoa
Prctica 15
7.- Utilice la herramienta WireShark para verificar la seguridad en la conexin
Qu sucede?
_________________________________________________________________________________
_________________________________________________________________________________
________________________________________________________________________________
Ing. Karina Rosas Paredes
Ing. Jose Esquicha Tejada
Ing. Leticia Laura Ochoa
Prctica 15
You might also like
- IPv6 0X06 Découverte de Voisinage Et Adresse AutomatiqueDocument22 pagesIPv6 0X06 Découverte de Voisinage Et Adresse AutomatiqueFrançois-Emmanuel GoffinetNo ratings yet
- Cours BY PART 9 PDFDocument52 pagesCours BY PART 9 PDFibouNo ratings yet
- Diagnostiquer IPv6Document221 pagesDiagnostiquer IPv6lalunerougeeNo ratings yet
- IPv6 13 14Document52 pagesIPv6 13 14amirdgNo ratings yet
- Exercices - 01 - Parefeu - ÉlèvesDocument2 pagesExercices - 01 - Parefeu - Élèvesabdellah magueri100% (1)
- MPLS 6peDocument12 pagesMPLS 6peHichamLechqarNo ratings yet
- 02-Multicast-Addressing EN v03Document14 pages02-Multicast-Addressing EN v03vladimir AKONo ratings yet
- DS1-datacom Part 2Document16 pagesDS1-datacom Part 2Aeroe OfficielNo ratings yet
- Corrigé TD2-ex4Document5 pagesCorrigé TD2-ex4mohamed agrebiNo ratings yet
- Configuration Des Interfaces IPv6 en Cisco IOSDocument7 pagesConfiguration Des Interfaces IPv6 en Cisco IOSBlin NkoukaNo ratings yet
- Adressage IPv 6Document82 pagesAdressage IPv 6Oumar DialloNo ratings yet
- ITN Module 13 094452Document26 pagesITN Module 13 094452Ibrahima Sory BahNo ratings yet
- IPv6 EIGRPDocument17 pagesIPv6 EIGRPSellé GueyeNo ratings yet
- Résumé IpDocument13 pagesRésumé IpMahdi HemritiNo ratings yet
- TDIPv 6Document2 pagesTDIPv 6Lionel Lawson-BodyNo ratings yet
- TD 3Document4 pagesTD 3Lc ZtNo ratings yet
- 12-ICMP FMDocument30 pages12-ICMP FMTarek BelkheiriNo ratings yet
- Ipv 6Document21 pagesIpv 6zidan2003No ratings yet
- Intro Ipv6Document64 pagesIntro Ipv6AwonoNo ratings yet
- Cours Ipv6-3x3Document20 pagesCours Ipv6-3x3douniaNo ratings yet
- 5 qosRouteurCISCODocument5 pages5 qosRouteurCISCOSara JEBRINo ratings yet
- Ipsec Et SSL - OdpDocument13 pagesIpsec Et SSL - OdpSaïda Mahamat SeidNo ratings yet
- Reproduire La MaquetteDocument4 pagesReproduire La MaquetteBadr El maazouziNo ratings yet
- Présentation Pour La SoutenanceDocument48 pagesPrésentation Pour La SoutenanceGhasston MradNo ratings yet
- Andres ChristopheDocument152 pagesAndres Christophedona100% (1)
- Ciscomadesimple - Be-Configuration Du NAT Sur Un Routeur CiscoDocument7 pagesCiscomadesimple - Be-Configuration Du NAT Sur Un Routeur CiscopapefayeNo ratings yet
- Devoir Nouhaila Charaf TcpipDocument5 pagesDevoir Nouhaila Charaf TcpipcharafNo ratings yet
- ICMPDocument22 pagesICMPDamien.Stéphane LekouamiNo ratings yet
- Serie N°3Document2 pagesSerie N°3사라SaraNo ratings yet
- TP1 NS3 ExempleDocument6 pagesTP1 NS3 ExempleYosra Mejri100% (3)