Professional Documents
Culture Documents
Fractals PartI PDF
Uploaded by
abhishekkr26jOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Fractals PartI PDF
Uploaded by
abhishekkr26jCopyright:
Available Formats
2/22/2013
IES-01
Fractals and Application
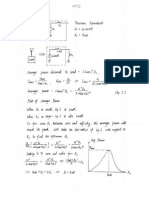
Attendance: 10 marks (Weightage: Absent : 0, Late : , Present : 1)
Assignments: 10 marks
Geometry :
developed as a collection of tools for understanding
the shapes of nature.
For millenia, Symmetry has been recognized as a powerful principle in geometry,
and in art.
We begin by reviewing the familiar forms of symmetry, then show that fractals
reveal a new kind of symmetry, symmetry under magnification.
Class Performance: 5 marks
Many shapes that at first appear complicated reveal an underlying simplicity when
viewed with an awareness of symmetry under magnification.
We begin by reviewing the familiar symmetries of nature: symmetry under
translation, reflection, and rotation.
We are familiar with three forms of symmetry, exhibited approximately in many
natural and manufactured situations. They are translational, reflection, and
rotational
Here we introduce some basic geometry of fractals, with emphasis on the Iterated
Function System (IFS) formalism for generating fractals.
In addition, we explore the application of IFS to detect patterns, and also several
examples of architectural fractals.
First, though, we review familiar symmetries of nature, preparing us for the new
kind of symmetry that fractals exhibit.
Less familiar is symmetry under
magnification:
zooming in on an object leaves the shape
approximately unaltered.
The geometric characterization of the simplest fractals is self-similarity: the
shape is made of smaller copies of itself. The copies are similar to the whole:
same shape but different size.
The simplest fractals are constructed by iteration. For example, start with a filledin triangle and iterate this process:
For every filled-in triangle, connect the midpoints of the sides and remove the
middle triangle. Iterating this process produces, in the limit, the Sierpinski
Gasket.
We can describe the gasket as made of three copies, each 1/2 as tall and 1/2 as
wide as the original. But note a consequence of self-similarity:
each of these copies is made of three still smaller copies, so we can say the
gasket is made of nine copies each 1/4 by 1/4 of the original, or 27 copies
each 1/8 by 1/8, or ... . Usually, we prefer the simplest description.
This implies fractals possess a scale invariance.
The gasket is self-similar. That is, it is made up of smaller copies of
itself.
2/22/2013
More Examples of Self-Similarity
The Mandelbrot set: a different nonlinear transformation gives the most famous of
all fractals.
The gasket is made of three copies of itself, each scaled by 1/2, and two copies
translated. With slightly more complicated rules, we can build fractals that are
reasonable, if crude, approximations of natural objects.
Later we will find the rules to make these fractals.
For now, to help train your eye to find fractal decompositions of objects, try to
find smaller copies of each shape within the shape.
The tree is not so hard, except for the trunk.
Fractal landscapes: With more sophistication (and computing power), fractals
can produce convincing forgeries of realistic scenes.
Fractals in nature: after looking at so many geometrical and computer-generated
examples, here is a short gallery of examples from Nature
Making realistic-looking landscapes is
difficult enough, but doing this so they can
be stored in small files is remarkable.
Fractals found in nature differ from our first mathematical examples in two
important ways:
the self-similarity of natural fractals is approximate or statistical and
One way to guarantee self-similarity is to build a shape by applying the same
process over smaller and smaller scales. This idea can be realized with a process
called initiators and generators.
this self-similarity extends over only a limited range of scales.
The initiator is the starting shape.
To understand the first point, note that many forces scuplt and grow natural
fractals, while mathematical fractals are built by a single process.
The generator is a collection of scaled copies of the initiator.
For the second point, the forces responsible for a natural fractal structure are
effective over only a limited range of distances.
The rule is this: in the generator, replace each copy of the initiator with a scaled
copy of the generator (specifying orientations where necessary).
The waves carving a fractal coastline are altogether different from the forces
holding together the atoms of the coastline.
Sierpinski Gasket How can we turn "connect the midpoints
and remove the middle triangle" into
initiators and generators?
The initiator is a filled-in triangle, the generator the shape on the right.
2/22/2013
Koch curve
Cantor set
Tents upon tents upon tents ... makes a shape we shall see is very strange, a
curve enclosed in a small box and yet that is infinitely long.
Cut all the tents out of the Koch curve and we are left with something that
appears to be little more than holes. But we can be fooled by appearances.
Take as initiator the line segment of length 1, and as generator the shape on
the right.
Though its construction is so simple, the Koch curve has some properties that
appear counterintuitive.
For example, we shall see that it is infinitely long, and that every piece of it, no
matter how small it appears, also is infinitely long.
Fractals in the Kitchen
Cauliflower is a wonderful example of a natural fractal. A small piece of a
cauliflower looks like a whole cauliflower.
Again, take as initiator the line segment of length 1, but now the generator
is the shape shown below.
Here is a picture of the Cantor set resolved to the level of single pixels.
Although so much has been removed that the Cantor set is hardly present at
all, we shall find this fractal in many mathematical, and some physical and even
literary, applications.
As -------- cook, the boiling batter forms bubbles of many different sizes, giving rise
to a fractal distribution of rings.
Some big rings, more middle-size rings, still more smaller rings, and so on.
Pieces of the pieces look like the whole cauliflower, and so on for several more
subdivisions.
Here is a picture of a cauliflower and a piece broken from it.
2/22/2013
Some breads are natural fractals. Bread dough rises because yeast produces
bubbles of carbon dioxide.
Many bubbles are small, some a middle-size, a few are large, typical of the
distribution of gaps in a fractal.
So bread dough is a foam; bread is that foam baked solid.
Kneading the dough too much breaks up the larger bubbles and gives
bread of much more uniform (non-fractal) texture
Do fractals have practical applications?
How about an invisibility cloak?
On Tuesday, August 28, 2012, U.S. patent
number 8,253,639 was issued to Nathan
Cohen and his group at FracTenna, for a
wide-band microwave invisibility cloak,
based on fractal antenna geometry
www.fractenna.com
The antenna consists of an inner
ring, the boundary layer, that
prevents microwaves from being
transmitted across the inside of
this ring. This is the region that
will be invisible to outside
observers. Surrounding the
boundary layer are six
concentric rings that guide
microwaves around the
On the left is a magnification of one of the outer rings
of the cloak.
the right is at
boundary
layer, On
to reconverge
the boundary layer fractal.
the point antipodal to where they
If fabricated at the sub-micron scale, instead of theentered
current the
mmcloak.
scale, this
technology should act as an optical invisibility cloak.
In late August, 2012, Cohen's group cloaked a person. Interesting times ahead.
Now down to work. We learn to grow fractal images, but first must build up the
mechanics of plane transformations.
Geometry of plane transformations is the mechanics of transformations that
produce more general fractals by Iterated Function Systems
Scalings
The scaling factor in the x-direction is denoted r.
The scaling factor in the y-direction is denoted s.
Assume there are no rotations. Then if r = s, the
transformation is a similarity
To generate all but the simplest fractals, we need to understand the geometry
of plane transformations. Here we describe and illustrate the four features of
plane transformations
Affine transformations of the plane are composed
of scalings, reflections, rotations, and translations.
Reflections
otherwise it is an affinity
Note the scalings
are always toward
the origin. That is,
the origin is
the fixed point of
all scalings.
Rotations
The angle measures rotations of horizontal lines
Negative r reflects across the y-axis.
The angle measures rotations of vertical lines
Negative s reflects across the x-axis.
Reflection across both the x- and y-axes is equivalent to rotation by 180 about the origin
The condition = gives a rigid
rotation about the origin.
Positive angles are
counterclockwise
2/22/2013
Translations
Horizontal translation is measured by e
The matrix formulation of an affine transformation that involves scaling by r in the
x-direction, by s in the y-direction, rotations by and , and translations by e and
f.
We adopt this convention:
scalings first, reflections second, rotations third, and translations last.
Vertical translation is measured by f.
This order is imposed by the matrix formulation.
Emphasizing this order, the components of a transformation are
encoded in tables of this form
With this encoding of transformations of the plane, we can make fractals using
the method called Iterated Function Systems (IFS)
Iterated Function Systems
Generating fractals by iterating a collection of transformations is the Iterated
Function System (IFS) method, popularized by Barnsley, based on theoretical work
by Hutchinson and Dekking. We use a simple example to see how it works
Invariance of the Gasket
Note that applying all three of these transformations to the gasket gives the gasket
again
That is, the gasket is invariant under the simultaneous application of these three
transformations.
To illustrate the IFS method, we show how a specific set of IFS
rules generates a Sierpinski gasket
We begin with a right isosceles Sierpinski gasket. Certainly, the gasket can be
viewed as made up of three copies of itself, each scaled by a factor of 1/2 in
both the x- and y-directions
What happens if we apply these transformations to some shape other than
the gasket?
To determine the translation amount of each piece, take
some point of the whole fractal (the lower left corner, for
example) and observe where that point goes in each
piece.
What happens if we apply these transformations to the resulting shape?
What happens if we iterate this process?
Here we derive the rules for the right isosceles Sierpinski
gasket
Here is an instance of this idea applied to a sketch of a cat
We observe a sequence of pictures that
converges to the gasket, independently of
the starting shape.
Specifically, suppose T1, ..., Tn are contractions, and P0 is any picture.
For example,
T1(x,y) = (x/2, y/2),
and P0 =
T2(x,y) = (x/2, y/2) + (1/2, 0),
T3(x,y) = (x/2, y/2) + (0, 1/2),
Generate a sequence of pictures
P1 = T1(P0) ... Tn(P0)
Because
of this convergence property, P is
P = T (P ) ... T (P )
called the attractor
of the IFS {T1, ... , Tn}.
...
2
Pk+1 = T1(Pk) ... Tn(Pk)
For concreteness we illustrate this converge using the gasket rules. Because
all the transformations are applied at each iteration, this is called
the determinisitc algorithm.
This sequence converges to a unique shape, P, the only (compact)
shape invariant under the simultaneous application of T1, ..., Tn:
P = T1(P) ... Tn(P)
That is,
2/22/2013
Inverse problems
finding the transformations to produce a given fractal
Given a fractal F, the Inverse problem is to find affine
transformations T1, ..., Tn for which
F = T1(F) ... Tn(F)
Remarkably, solving the inverse problem has only two steps:
1. Using the self-similarity (or self-affinity) of F, decompose F as F = F1 ... Fn, where
each Fi is a scaled copy of F.
Here we present a method to solve this problem
Solving the inverse problem takes just two steps.
2. For each piece Fi, find an affine transformation Ti for which Ti(F) = Fi. By "find an affine
transformation" we mean find the r, s, , , e, and f values.
Decomposition
Because the transformations can involve rotations, reflections, and scalings
by different factors in different directions, decomposition is not always as
simple a task as it may seem at first. Here are some examples of more
complicated decompositions.
This fractal is an instructive example for people who have
seen the gasket and a few of its relatives.
the bottom
left piece
TheNote
primacy
of the gasket
in early examples of fractals
is a reflected
copy
makes
this shape
oneofofthe
the easiest to recognize.
whole shape
The most common response to first seeing this picture is,
"It's half a gasket."
In the x-direction we see the familiar
Cantor middle thirds set; in the y-direction
just a line segment. Again, look for scaled
copies of the whole shape. Here's
a decomposition.
But we don't have rules for making half of a fractal.
The main lesson here is that we're looking for scaled copies of the
whole shape, and the whole shape is not a gasket.
Tracing small copies of the outline of the whole shape, perhaps
cutting them out of paper, is a good way to build up intuition for this
process. Here's a decomposition.
An additional problem is that decompositions never are unique. Here are
some examples of different decompositions of the same fractal.
Find a decomposition of this fractal into
smaller copies of itself.
Usually, we try to find a decomposition into
the smallest number of pieces, keeping in
mind that each piece must be a contracted
copy of the whole shape.
We have already seen one decomposition
of this fractal.
When we give up the requirement that the
pieces be similar to the whole, new
possibilities appear.
Here's one decomposition, and
here's another.
2/22/2013
Solving the inverse problem has only two steps:
Examples
1. Using the self-similarity (or self-affinity) of F, decompose F as F = F1 ... Fn, where
each Fi is a scaled copy of F.
This fractal can be decomposed into three
pieces:
Note the top and bottom left pieces have
the same orientation as the entire fractal,
while the bottom right piece is reflected
across a vertical line
2. For each piece Fi, find an affine transformation Ti for which Ti(F) = Fi. By "find an
affine transformation" we mean find the r, s, , , e, and f values.
(a) Trace the main features of the fractal and cut out
smaller copies of the tracing.
Keeping in mind that our transformation rules allow only reflections across the
x- and y-axes, some care must be taken with the translation after the reflection
(b) To allow for reflections, flip the small copies and on the
back trace over the lines on the front. Label the front
image with a small F, to distinguish it from its reflection,
and to indicate the original orientation.
(c) Place the small copies, perhaps rotating or reflecting
them, to make a copy of the original fractal.
- 0.5 0.5
0.5 0.5
0
0
0
0
1.0
0.0
0.0
0.5
Find IFS rules to generate each of these fractals
This fractal can be decomposed into three
pieces:
Note the top and bottom left pieces have the same orientation as the entire
fractal, while the bottom right piece is rotated.
Keeping in mind that our transformation rules allow only rotations fixing the
origin, some care must be taken with the translation after the rotation
.333
.333
.333
.333
.667
.5
.5
.333
.333
.667
.5
.5
.5
.333
.333
.667
.667
.5
.5
.5
.333
.333
.333
.333
.25
.25
.75
.75
.333
.333
.333
.333
.333
.333
.5
.5
.333
.333
.667
.667
-.5
.5
.333
.333
.667
-.5
.5
.5
.5
2/22/2013
When the pieces are not scaled by such obvious amounts, we can find scalings
and rotations by measuring distances and angles
r
-.5
.5
90
90
.5
.5
.5
.5
180
180
.5
.5
.5
-90
-90
Splitting the fractal into three pieces is not difficult.
Here's the IFS table that
generated this fractal.
r
.5
.5
-90
-90
.5
.5
.5
180
180
.5
.5
.5
.5
.5
Often it is convenient to specify a point as the origin of the coordinate system.
The lower left corner can be a good choice, but in general, use any symmetry
available, unless there is a compelling reason to do differently
First, find the scalings and any reflections, that is, the r and s values.
Second, Find the rotations.
Third, find the translations.
With a bit of thought, now we can find an IFS to generate the tree
Here are the IFS rules, color coded to match each transformation to the
corresponding piece of the tree.
First, it is easy to see the four main branches of the tree are scaled copies of the
whole tree.
The pieces have been pulled apart slightly to emphasize the decomposition.
The trunk is more complicated.
Simply shrinking the tree a lot horizontally works for the top of the trunk, but
makes the bottom of the trunk too thin.
Two shrunken copies of the tree are needed to make the trunk.
Here is the picture generated by the tree rules, leaving
out the second part of the trunk.
Common Mistakes in Finding Fractals:
By contrast, two fists do not make a covincing Cantor set.
Things that look like fractals but aren't
First, recalling that no physical fractal can exhibit scaling over
infinitely many levels, nevertheless to make a plausible claim
of fractality, a pattern must be repeated on at least a few
levels.
Note also the handprint in the lower right of the painting. This is Dali's handprint; this
is the
only painting
signed
handprint,
a testimony
to the
power this painting
The
"skulls
within skulls"
of with
Dali'shis
Visage
of War
are repeated
three
had for four)
Dali. times.
(maybe
In Dali's Visage of War (1940) note the eyes
and mouth each contain a face, whose eyes
and mouth each contain a face, many of whose
eyes and mouth each contain a face, an
obvious, if gruesome, example of fractals in art.
Dali thought of the Spanish Civil War, in 1940 a
source of frightening images to
him. Descharnes described the painting as
having "eyes filled with infinite death," referring
to the recursive effect set in motion by selfsimilarity.
The decomposition of this picture into two pieces, the two fists, does not
continue to even one more level.
The fists are not split into smaller pieces. The more levels of the pattern,
the more convincing the fractality of the picture.
Here is an analogous example based on
the Sierpinski tetrahedron.
This is not plausibly fractal: it is a shape made of four
tetrahedra, but the tetrahedra have no substructure.
This is more believably fractal:
the structure has four levels of
substructure.
2/22/2013
Second, a repeating pattern alone is not sufficient to guarantee fractality.
In order to produce a fractal, at each level the decomposition must involve at
least two scaled copies.
Nested dolls are another example of a non-fractal involving a single scaling
transformation,
Inside the largest doll nestles a smaller doll,
inside that doll nestles a still smaller doll,
A checkerboard or a brick wall has a repeating pattern, but the repetition
is with respect to translation, whereas for fractals the appropriate
transformation is magnification
Third, repeating a pattern under magnification is not sufficient to guarantee
fractality.
inside that doll nestles an even smaller doll,
and so on.
The limit of this process is a single point, not a fractal.
The bottle label includes a cat and a
bottle,
with a label that includes a cat and a
bottle,
as is the cat bottle.
For example, a spiral is symmetric under magnification about its center
point, but about no other point.
with a lable that includes a cat and a
bottle,
Iterating this process, the limiting shape is just a single point.
and so on
The limit of this process is a single
point, not a fractal.
On the other hand, the cow picture is fractal, as would be more
obvious if the cow's left earring were turned toward us.
Both earrings have pictures
of the cow with two earrings,
both of which have pictures
of the cow with two earrings,
both of which have pictures
of the cow with two earrings,
Here we study the random IFS algorithm, another way to render IFS images. This
includes a careful look at what random means.
To motivate the Random IFS algorithm, we begin with
the Chaos Game.
Here we observe the apparent effect of randomness is to
guarantee the points dance across the picture to be
generated.
and so on.
The limit of the cow pictures
is a Cantor set.
Definition Movement, in random order, toward a collection of points can
fill in a polygon, or grow a fractal
The Chaos Game is played by specifying a number of vertices (a1, b1), (a2, b2),
..., and (aN, bN), and a scaling factor r < 1.
To play the game, start with the point (x0, y0) and pick one of the vertices,
say (ai, bi), randomly.
The point (x1, y1) is the fraction r of the distance between (ai, bi) and (x0, y0).
That is,
(x1, y1) = r(x0, y0) + (1 - r)(ai, bi)
For example, with four vertices, r = 1/3, and (a2, b2) is the first randomly
selected vertex, we obtain
(If r = 1, the point (x1, y1) is the same as the initial point (x0, y0); if r = 0, the
point (x1, y1) is the same as selected vertex (ai, bi).)
Now pick another vertex, (aj, bj), randomly.
The point (x2, y2) is given by
(x2, y2) = r(x1, y1) + (1 - r)(aj, bj)
and so on.
The Chaos Game Plot is the sequence of points (x0, y0), (x1, y1), ...
generated this way.
2/22/2013
For example of the Chaos Game, take four vertices, the
corners of the unit square, and take r = 1/2
(a3, b3) = (0, 1)
(a4, b4) = (1, 1)
(a1, b1) = (0, 0)
(a2, b2) = (1, 0)
Suppose the random number generator begins by selecting the vertices in
this order: 1, 3, 4, 3, 2.
See the first five points generated by this run of the chaos game.
If we continue, the points will fill in the square.
This should be plausible: we start with a point inside the
unit square, and each move is half-way between where
we are and a corner of the square, so we never leave the
square.
Because we select the corners randomly, no part of the
square is preferred over any other.
What would happen if we used just three vertices (a1, b1), (a2, b2), and (a3, b3)?
As with the square, we start with a point in the triangle. (In this example, it's on the
edge of the triangle, but that's still in the triangle.)
Each move is half-way between where we are and a corner of the triangle, so we
never leave the triangle.
Because we select the corners randomly, no part of the triangle is preferred over
any other.
So since some parts of the triangle fill in, all parts must fill in.
Thus played with three vertices of a triangle, the chaos game should fill in the
triangle. Right?
Here is the answer.
So since some parts of the square fill in, all parts must fill
in.
Do you believe this argument?
Here are more Chaos Game examples. Try to determine the shape
vertices the corners of a square, r = 1/3
move the top right vertex to the left, r = 1/2
The chaos game often is used as an introduction to the more general Random IFS.
To illustrate its simplicity, frequently the chaos game is performed manually.
While this does convince of the simplicity of the chaos game, it is less effective in
showing the chaos game will generate fractals. For example, generating 30 points
manually requires some patience, but does the picture give much hint of a gasket?
five vertices, four the corners of a square,
one at the center of the square, r = 1/2
five vertices, four the corners of a square,
one at the center of the square, r = 1/3.
Purpose To use Random IFS to illustrate an interesting property of random
sequences of numbers
Material Triangle template, about 12 overhead transparencies, a die (singular of
dice), adhesive tape, a ruler with cm scale, a permanent marking pen, an
overhead projector to display the data.
Here are 10 samples of 30 points each
The right picture, consisting of 300 points,
is much more convincingly a gasket.
No one would play the chaos game manually for 300 points, but this is not such
a problem: software can produce a 300 point chaos game in milliseconds (or
less).
This is to show that combining the results of 10 people generating 30 points
each produces as good a picture of the gasket as that of a single person
generating 300 points
10
2/22/2013
Below on the left is the aggregate of these 10 pictures; on the right is the picture of
300 iterates of one point. Both are reasonable representations of the gasket.
The Random IFS Algorithm
Given IFS rules, the Deterministic Algorithm renders a picture of the
fractal by
1. applying all the rules to any (compact) initial picture,
2. then applying all the rules to the resulting picture,
3. and continuing this process.
Regardless of the starting shape, this sequence of pictures
converges to a unique limiting shape, the only (compact) set
invariant under simultaneous application of all the rules.
Conclusion The superposition of several
short runs of the chaos game is at least
visually indistinguishable from a longer run.
Among other things, the 30 point pictures illustrate two less-familiar
aspects of the chaos game.
(1) Manual chaos game experiments require a great deal of patience to
produce a recognizable image.
The Random Algorithm is another method of rendering the fractal determined by a given
set of rules, T1, ..., TN.
(2) The evident variability between short chaos game runs is
considerable.
Definition and illustration of the random algorithm
Start with a point (x0, y0) belonging to the fractal, for example, take (x0,
y0) the fixed point of one of the Ti.
If T(x,y) is a contraction, then it has exactly one fixed point.
A contraction is a transformation T that reduces the distance between every
pair of points.
That is, there is a number r < 1 with
dist(T(x, y), T(x', y')) rdist((x, y), (x', y'))
A fixed point of a transformation T(x,y) is a point left unchanged by the
transformation. That is,
T(x, y) = (x, y)
Example 1
T(x, y) = (x/2, y/2) has fixed point (0, 0).
Example 2
T(x, y) = (x/2, y/2) + (1/2, 0) has fixed point (1, 0).
(x, y) = T(x, y) = (x/2, y/2). So x = x/2 and y = y/2, hence x = 0 and y = 0.
for all pairs of points (x, y) and (x', y').
Here dist denotes the Euclidean distance between points:
dist((x, y), (x', y')) = ((x - x')2 + (y - y')2)1/2
The contraction factor of T is the smallest r satisfying
d(T(x, y), T(x', y')) rd((x, y), (x', y'))
for all pairs of points (x, y), (x', y').
(x, y) = T(x, y) = (x/2, y/2) + (1/2, 0). So x = x/2 + 1/2 and y = y/2, hence x = 1 and y = 0.
In general, contractions can reduce distances between points by different amounts,
depending on the position of the points.
Let {n1, n2, ... } be a random sequence of numbers, each from {1, ..., N}.
Generate a sequence of points
Here are some special kinds of contractions.
(x1, y1) = Tn1(x0, y0),
A similarity reduces all distances by the same number, r < 1. That is,
(x2, y2) = Tn2(x1, y1),
d(T(x, y), T(x', y')) = rd((x, y), (x', y'))
for all pairs of points (x, y), (x', y').
The transformation T(x, y) = (rx, ry) is an example; its contraction factor is r.
...
We shall see this sequence of points eventually will fill up the fractal to any
prescribed accuracy. For example, here are pictures of the Random Algorithm
applied to the gasket rules.
(x1, y1) = r(x0, y0) + (1 - r)(ai, bi)
An affinity reduces distances by different amounts in different directions. For example,
T(x, y) = (rx, sy),
where both r < 1 and s < 1, and r and s are different.
5000 points
500 points
If all the transformations of an IFS are contractions, then iterating the IFS is guaranteed to
converge to a unique shape.
11
2/22/2013
This leads to the question What is random?
In case you're interested, here are the first 1000 decimal digits of pi
What makes an infinite sequence of digits random?
Are these random sequences?
1111111111111111111111111111...
1212121212121212121212121212...
1010010001000010000010000001...
1415926535897932384626433832...
What makes these
sequences nonrandom? We
can give short descriptions
that exactly specify the entire
sequence. This motivates our
definition of randomness.
This sequence is the first 28 digits in the decimal
How do you know this is the first 28 decimal digits of pi?
expansion of pi.
If of
you
knowmany
the first
28 decimal
While the digis
pi didn't
may pass
satistical
tests digits
for of pi, would
think this
is random?
randomness, you
we would
not sequence
call pi random.
our the
perception
of randomness
depend
on how much
It is a specificDoes
number,
ratio of the
circumference
to
weany
know?
the diameter of
circle, always the same.
Motivated by our thoughts about these examples, we define an infinite
sequence of digits to be random if it cannot be specified completely in any way
shorter than listing the whole sequence.
How can we generate a random sequence?.
To make an infinite random sequence of 0s and 1s, toss a coin infinitely many
times.
Each time a heads comes up, put a 1 in the sequence. Each times tails comes
up, put a 0 in the sequence.
So if the coin toss started out
heads, heads, tails, heads, tails, tails, tails, heads
the random sequence would start
11010001
Of course, computers don't toss coins, but rather generate pseudorandom
numbers.
141592653589793238462643383279502884197169399375105820974
944592307816406286208998628034825342117067982148086513282
306647093844609550582231725359408128481117450284102701938
521105559644622948954930381964428810975665933446128475648
233786783165271201909145648566923460348610454326648213393
607260249141273724587006606315588174881520920962829254091
715364367892590360011330530548820466521384146951941511609
433057270365759591953092186117381932611793105118548074462
379962749567351885752724891227938183011949129833673362440
656643086021394946395224737190702179860943702770539217176
293176752384674818467669405132000568127145263560827785771
342757789609173637178721468440901224953430146549585371050
792279689258923542019956112129021960864034418159813629774
771309960518707211349999998372978049951059731732816096318
595024459455346908302642522308253344685035261931188171010
003137838752886587533208381420617177669147303598253490428
Random sequences have this property:
Every infinite sequence of random numbers contains all finite sequences.
Suppose we have an infinite sequence of 0s and 1s, and nowhere in the sequence do we find
000.
By the definition given, this infinite sequence is not random. Why?
Suppose we're describing the sequence by listing all its terms.
Whenever we get to a 00 pair, we don't have to say what the next number is.
It MUST be 1, because otherwise the infinite sequence would contain 000.
Consequently, we don't have to list the entire infinite sequence to specify it completely. We say
only once that the sequence does not contain the triple 000, and then whenever the pair 00
occurs, we know the next number must be 1.
Similar arguments show that all finite sequences must occur somewhere (in fact, infinitely
often) in an infinite random sequence. If any one is missing, we can use this missing sequence
to describe the infinite sequence without listing all its entriety.
One method starts with the time on your computer's clock, multiplies by a large
number, divides by another large number, and takes the remainder.
Addresses in fractals
To understand why the Random and Deterministic algorithms generate the
same pictures, we also need to understand the notion of the address of parts
of a fractal.
Addresses are the main tool for relating fractals and
dynamics.
The order of the elements of an address is important, and
to some counterintuitive,
The notion of addresses is familiar in one dimension from the decimal expansion of
real numbers in the unit interval, [0, 1].
The left-most digit of the decimal expansion of x tells into which 10th of [0, 1] x falls.
The second digit tells into which hundredth - that is, which 10th of the 10th - x falls.
And so on. Here is an illustration
To relate this to IFS, we need IFS rules to generate the unit interval. There are
(infinitely) many families of such rules, but for ease of interpretation with the
decimal expansion, we use
Ti(x) = x/10 + i/10
for i = 0, ..., 9. Then
Ti(I) is the ith 10th,
TiTj(I) is the jth 100th of the ith 10th,
and so on. Note the order of the subscripts. This is the tricky part of
understanding addresses. We say
the digit i is the address of the ith10th,
the pair ij is the address of the jth 100th of the ith 10th,
and so on. Notice from left to right the address digits specify smaller intervals.
Addresses are unique.
12
2/22/2013
Addresses of a square
For concreteness in the two-dimensional case, we
consider the transformations
T3(x, y) = (x/2, y/2) + (0, 1/2)
T4(x, y) = (x/2, y/2) + (1/2, 1/2)
T1(x, y) = (x/2, y/2)
T2(x, y) = (x/2, y/2) + (1/2, 0)
In order of application, addresses are read right to left: the left-most digit is the
index of most recent transformation applied.
Because this seems confusing sometimes, we emphasize the order of
addresses is consistent with the order of composition of functions:
ij is the address of TiTj(S).
These generate the filled-in unit square S. That is,
S = T1(S) T2(S) T3(S) T4(S),
with overlaps only along edges.
To each of the 1/2 1/2 squares Ti(S) we associate the length 1 address i.
Another way to think of addresses is as relative coordinates. The 1/4 1/4
squares with addresses 11, 12, 13, and 14 are the 1, 2, 3, and 4 parts of 1.
Each of these squares can be subdivided by iterating this decomposition process. For
example,
T1(S) = T1T1(S) T1T2(S) T1T3(S) T1T4(S).
T3(x, y) = (x/2, y/2) + (0, 1/2)
T4(x, y) = (x/2, y/2) + (1/2, 1/2)
T1(x, y) = (x/2, y/2)
T2(x, y) = (x/2, y/2) + (1/2, 0)
To each of the 1/4 1/4 squares TiTj(S) we associate the length 2 address ij,
and so on.
Longer addresses
Because each Ti is a contraction, longer addresses specify smaller portions of S.
For example, here are the length 3 addresses for the square transformations.
T3(x, y) = (x/2, y/2) + (0, 1/2)
T4(x, y) = (x/2, y/2) + (1/2, 1/2)
T1(x, y) = (x/2, y/2)
T2(x, y) = (x/2, y/2) + (1/2, 0)
That longer addreses specify locations with greater accuracy is part of our
common experience. Let's abandon geometrical abstraction and turn to our own
sense of place.
Where are you?
At some fairly crude level, you are on the earth.
More precisely, you are in Asia, on the earth.
Still more precisely, you are in India, in Asia, on the earth
You are in Uttarakhand, in India, in Asia, on the earth.
You are in Roorkee, in Uttarakhand, in India, in Asia, on the earth.
You are at IIT Roorkee, in Roorkee, in Uttarakhand, in India, in Asia, on the earth.
You are in LHC 003, at IIT Roorkee, in Roorkee, in Uttarakhand, in India, in Asia, on the earth.
You are in the second row, third seat, in LHC 003, at IIT Roorkee, in Roorkee, in Uttarakhand, in
India, in Asia, on the earth.
This general kind of description has been familiar to us from childhood, so
we have known for years that a longer address specifies location more
precisely.
Addresses and Symmetries
For fractals with symmetries, different rules can generate the same shape, but
with different addresses for the same region.
To see how address 21 winds up in the indicated position, start with the solid triangle S
apply transformation T1,
obtaining T1(S).
apply T2, shrinking and
reflecting across the y-axis.
Both IFS tables generate the equilateral Sierpinski gasket.
and translating by 1 horizontally.
For the first table, it is not difficult to
see the length 2 addresses (left).
For the second table, the reflection in rule
2 has an effect on the addresses, for
example, the length 2 addresses
This red triangle is T2(T1(S)),
hence has address 21
13
2/22/2013
Diameter goes to 0 under iteration of any contraction map
To understand why the Random and
Deterministic algorithms generate the
same pictures, we tried to understand the
notion of the address of parts of a fractal.
The diameter of a set is the maximum distance between any pair of
points in the set.
Now we can show why the Random and Deterministic algorithms
generate the same picture
For example, the diameter of a circle is just the common notion of diameter; the
diameter of a square is the diagonal length of the square.
Some diameters
First, fix a resolution, usually one pixel, to which the picture is to be
rendered.
Then we show
long enough addresses specify regions smaller than a
pixel,
that randomness guarantees all finite addresses are visited
by the points generated by the random IFS algorithm, and
that consequently every pixel of the attractor is visited.
Because
all the
rules
the
region
T3(x,
y) = (x/2,
y/2)IFS
+ (0,
1/2)are contractions,
T4(x,
y) =diameter
(x/2, y/2)of+a(1/2,
1/2)of
diam(S)
= 2
address length N goes to 0 as N goes to infinity. We illustrate this with the
T1(x,
= (x/2, y/2)
T2(x,
y) = (x/2, y/2) + (1/2, 0)
diam(T
foury)transformations
i(S)) = (2)/2
diam(TjTi(S)) = (2)/4
and in general
diam(TiN...Ti1(S)) = (2)/(2N)
Consequently, diam(TiN...Ti1(S)) 0 as N .
Observe
how the Random IFS algorithm fills, to given resolution, the
attractor of the Deterministic IFS algorithm.
(x0, y0) = T1(x0, y0) = T1(T1(x0, y0)) = T1(T1(T1(x0, y0))) = ...
So (x0, y0) belongs to the square with address 1, the square with address 11, the
square with address 111, and so on.
Because
Because the diameters of these squares are shrinking to 0, the address 111... =
1 corresponds to the single point(x0, y0).
diam(TiN...Ti1(S)) = (2)/(2N),
if we take N large enough that
(2)/(2N) < resolution,
then the Random Algorithm will fill in the picture to the desired resolution if
all regions of address length N are visited.
Alternately, note that the only point left unchanged by repeated application of
T1 is the point with address 111... = 1
Why should the Random Algorithm do this?
Iteration and address shift: how iteration
affects the address of the points generated
by the Random IFS algorithm.
First, recall the Random Algorithm starts with the fixed point of one of the Ti.
Suppose the first transformation applied is Ti1, the next Ti2, and so on.
What is the effect of these transformations on the address of the point, and on
the address length N region in which the point lies?
For definiteness, say we start with the fixed point (x0, y0) of T1.
The address of this fixed point is 111... = 1.
point
address of the point
(x0, y0)
address length N region
containing the point
1N
i1(1)
i1111... =
(x2, y2) = Ti2(x1, y1)
i2i1(1)
i2i1(1N-2)
(x3, y3) = Ti3(x2, y2)
i3i2i1(1)
i3i2i1(1N-3)
...
(xN, yN) = TiN(xN-1, yN-1)
iN...i3i2i1(1)
(xN+1, yN+1) = TiN+1(xN, yN)
iN+1iN...i3i2i1(1)
...
every finite sequence of transformations will occur,
and in particular, every sequence of length N will be applied.
1N-1
(x1, y1) = Ti1(x0, y0)
...
i1
If the transformations are applied randomly, then eventually
...
Consequently,
every region with address length N will be visited by the (xik, yik).
To the specified resolution, the Random Algorithm will generate the same picture
as the Deterministic Algorithm.
iN...i3i2i1
...
iN+1iN...i3i2
...
So we see each new transformation applied has this effect on the N-digit
address: discard the right-most digit, shift the remaining N-1 digits one place to
the right, and insert the new address on the left.
14
2/22/2013
Example
For example, suppose we specify the resolution corresponding to addresses of length N =
3 and we start with the point (x0, y0) with address 1infinity.
To the specified resolution, (x0, y0) lies in the region with address 111.
Probability and the Random IFS Algorithm
In the Random IFS Algorithm the transformations Ti are applied in random order, but
they need not be applied equally often.
Associated with each Ti is a probability pi, 0 < pi < 1, representing how often each
transformation is applied. That is,
If T2 is the first transformation applied, then resulting point (x1, y1) = T2(x0, y0) lies in the
region with address 211.
when N points are generated, each Ti is applied about Npi times.
To illustrate the effect of changing the probabilities, we use the IFS
If T3 is the next transformation applied, then resulting point (x2, y2) = T3(x1, y1) lies in the
region with address 321.
If T4 is the next transformation applied, then resulting point (x3, y3) = T4(x2, y2) lies in the
region with address 432.
Continuing will fill in all the 43 regions of address length 3.
T3(x, y) = (x/2, y/2) + (0, 1/2)
T4(x, y) = (x/2, y/2) + (1/2, 1/2)
T1(x, y) = (x/2, y/2)
T2(x, y) = (x/2, y/2) + (1/2, 0)
We take
p4 to range from 0 to 1 in steps of .05,
and
p1 = p2 = p3 = (1 - p4)/3.
Starting with p4 = 0, the first picture is the gasket. Do you see why?
Here is a way to find the probabilities that give approximately uniform fill of the
attractor.
Very roughly speaking, the probability pi of applying Ti is the fraction of the
whole attractor A occupied by Ti(A).
The area contraction factor of Ti is
Ai = risi(cos(i)cos(i) + sin(i)sin(i))
(This is just the determinant of the matrix formulation of Ti.)
Note that if i = i, the area contraction factor simplifies to
Ai = risi
Then the probability is given by
pi = Ai/(A1 + ... + AN)
Driven IFS
What happens if we use a non-random sequence in the random IFS algorithm?
In particular, can we run the random IFS algorithm with a sequence of data daily closing prices of a stock, or the intervals between your heartbeats, for
example?
Will patterns in the IFS picture reveal patterns in the data?
Because we use a data sequence to select the order in which the
transformations are applied, we call this approach driven IFS. The
data drive the order in which the IFS rules are applied.
Stewart's experiments
For most of his tests, Stewart used the chaos game fixed points the
vertices (0, 0), ((3)/2, 1/2), and (0, 1) of an equilateral triangle. The
corresponding IFS rules are
T1(x, y) = (x/2, y/2)
T2(x, y) = (x/2, y/2) + (0, 1/2)
T3(x, y) = (x/2, y/2) + ((3)/4, 1/4)
For reference, a random number generator (1000 points) gives
Referring to the chaos game, Ian Stewart asked "What
happens if the computer's random number generator is
replaced by some more familiar dynamical system?"
15
2/22/2013
Coarse-Graining the Data
We turn the data y1, y2, ..., yN into a sequence i1, i2, ..., iN of 1s, 2s, 3s, and 4s.
This sequence is called the symbol string associated with the data.
is produced by iterating the logistic map xn+1 = 4xn(1 - xn).
The data values yi often are measured as decimals and because we are
converting these to only four values, the process of turning the yk into ik is
called coarse-graining.
The range of y values for corresponding to a symbol is the bin of that symbol.
Pictures are
generated
sequences of
is produced from sin(t) + sin(t2).
numbers, coarset = 1, 2, ..., 1000.
grained into three
equal-size bins.
is produced from sin(t) + sin(t3) + sin(t5)
Though there are others, we use five kinds of coarse-graining:
Here is the time series y1, y2, ..., y1000 generated by 1000 iterates of the logistic
map with equal-size bin lines drawn, and the corresponding driven IFS
equal-size bins Divide the range of values into four intervals of equal length.
equal weight bins Arrange the bin boundaries so (approximately) the same number of points lie in each
bin.
zero-centered bins For data whose sign is important, take 0 as the boundary between bins 2 and 3; place
the other boundaries symmetrically above and below 0. Unlike the first two cases, this is a family of
coarse-grainings depending on the placements of the other two bin boundaries.
mean-centered bins Take the mean of the data to be the boundary between bins 2 and 3; place the other
boundaries symmetrically above and below the mean, usually expressed as a multiple of the standard
deviation.
median-centered bins Take the median of the data to be the boundary between bins 2 and 3; place the
other boundaries symmetrically above and below the median, usually expressed as a multiple of the
range. Note the equal-weight bins are a special case of this.
Here is the time series y2 - y1, y3 - y2, ..., y1000 - y999 generated by successive
differences of 1000 iterates of the logistic map with equal-size bin lines drawn,
and the corresponding driven IFS
To illustrate the different kinds of coarse-graining, we use a
data set consisting of successive differences of 1000 numbers
generated by iterating the logistic map.
Here is the time series y1, y2, ..., y1000 generated by 1000 iterates of the logistic
map with equal-weight bin lines drawn, and the corresponding driven IFS
Driven IFS Rules (Square functions)
T3(x, y) = (x/2, y/2) + (0, 1/2)
T4(x, y) = (x/2, y/2) + (1/2, 1/2)
T1(x, y) = (x/2, y/2)
T2(x, y) = (x/2, y/2) + (1/2, 0)
This IFS generates the filled-in unit square. Consequently, any departure from
uniform randomness will be visible through departures from uniform fill of the
square.
Here are some examples, all with 10000 points.
Here is the time series y2 - y1, y3 - y2, ..., y1000 - y999 generated by successive
differences of 1000 iterates of the logistic map with equal-weight bin lines
drawn, and the corresponding driven IFS
uniform random
sequence
p1 = p4 = 0.1;
p2 = p3 = 0.4
p1 = 0.1;
p2 = p3 = p4 = 0.3
p1 = p3 = 0.1;
p2 = p4 = 0.4
16
2/22/2013
IFS Driven by DNA Sequences
Read the sequence in order, and
An example first explored by H. Joel Jeffrey. The genetic code is written in an
alphabet of four characters: C, A, T, and G.
apply T1 whenever C is encountered,
A sequence of several billion of these makes each of us. A sequence of 3957
symbols is needed to encode the formation of the enzyme amylase.
apply T3 whenever T is encountered, and
T G AAT T C AA G T T T G G T G C AAAA C T T G G C A C A G T T AT C C G
C AA G T G G AA T G G A G A G AA G AT G T C C T AT T T AAA G T AAAT A
TATAC GATT TT G T CATTT G TT C T G T CATACAT C T G T T G T C
AT T T T C T TAAAT AT T G TAA C T T AAAT T G T T G AT T AT T A G T T
AG G C T TAT T G T T CAT T TAT C C T TAAT TAAT TAT G T T T T T CA
T T T G A TA C A T C A G T C A C C T G AT AA C A G C T G AAA T C T AAA G
TAT CAC T TAG T GAG T T T T G T T G G G T T G T G T TAAG T C CAT
T How
A G A Gcan
T C T we
A A Gconvert
A A T G T Ta
TG
C T TA
T G G C C T Ainto
C TAA
A AIFS
ATAT
DNA
sequence
an
G G T A G C AT C C T AA G AAT A G T T AT A C T AAAAA G T G AT C C C T
Apicture?
T AAT AT G A C T A C A C T A G G G AA T T TA T T T AT G C T A C A T T A
G G G AA T T AA T T G AAAT T T AAAA G T G AAT G T AAAA G C A G A G
T T AT AAA T T AA T T T C C AT T C T G T AT T AT AT AA C AT G G AT G T
C T T AAT T C T C AA G T C C A TAAT G T T A C AAT AAAAT T T T AAAA
AT C T AAAA TAAAAT C AAAA C AAAA G AT TA TA TA G TAAAA C C
TAAAT C T G G AT AAAAT T C C C AT G TA T G T T AT C A TA G AAAA T
T G T A C A T A T G T G T A C A T A T A C A A T.
some more examples of IFS driven by DNA sequences.
apply T4 whenever G is encountered,
On the left is the picture that results from applying these rules to the amylase
sequence. Note there are very few points in the region with address GA.
(Remember the ordering of the addresses.)
On the right is a picture that results when 3957 points are generated randomly,
except that T4 never immediately follows T1.
Not an exact match, but certainly suggestive.
Cyclic Driven IFS
First, two examples from ion channels in human cardiac cells.
potassium channel
apply T2 whenever A is encountered,
Of course, any assignment of
transformations to C, A, T, and
G can be used.
What happens if we drive an IFS in a
repeating pattern?
sodium channel
Here we will learn to recognize the visual signature of IFS driven by
cyclic data, that is, numbers that repeat a particular pattern.
The simplest repeated sequence is constant, just repeat the same
number,
for example, 11111... = 1.
Starting with (1/2, 1/2), applying T1(x, y) = (x/2, y/2) repeatedly produces the
sequence of points
Here are four examples from chromosome 7
from the University of
Washington human genome site http://www.genome.washington.edu/UWGC/
T1(1/2, 1/2) = (1/4, 1/4),
T1(1/4, 1/4) = (1/8, 1/8),
T1(1/8, 1/8) = (1/16, 1/16),
...
converging to the lower left corner of the unit square.
g1346a094
g0771a003
G1564A209
gap3
The interpretations of these pictures is still being investigated. Stay tuned.
Recall
Because it is gotten by applying T1 infinitely many times, the address of this point
is 11111... = 1.
Constant sequences generate sequences of points that converge to
the fixed point of the corresponding transformation.
T1(x, y) = (x/2, y/2) =
((x+0)/2, (y+0)/2), the midpoint of (x, y) and (0, 0)
T2(x, y) = (x/2, y/2) + (1/2, 0) =
((x+1)/2, (y+0)/2), the midpoint of (x, y) and (1, 0)
T3(x, y) = (x/2, y/2) + (0, 1/2) =
((x+0)/2, (y+1)/2), the midpoint of (x, y) and (0, 1)
T4(x, y) = (x/2, y/2) + (1/2, 1/2) =
((x+1)/2, (y+1)/2), the midpoint of (x, y) and (1, 1)
we see the cycles 2, 3, and 4 generate sequences of points that converge
to (1, 0), (0, 1), and (1,1), respectively
The sequence of points generated by applying T1 repeatedly converges to the point with
address 1111... = 1.
We show this is the fixed point of T1, and find its coordinates.
Fixed point. Say (x*, y*) is the point with address 1. Then
T1(x*, y*) has address 1(1) = 1.
Because T1(x*, y*) and (x*, y*) have the same (infinite) address, they must be the same point.
That is,
T1(x*, y*) = (x*, y*)
and (x*, y*) is the fixed point of T1.
Coordinates. We see
(x*, y*) = T1(x*, y*) = (x*/2, y*/2),
and so (x*, y*) = (0, 0).
Similar arguments show 2, 3, and 4 are the fixed points of T2, T3, and T4, respectively.
These points have coordinates (1, 0), (0, 1), and (1, 1), respectively. For example,
Constant sequences generate sequences of points that converge to
the fixed point of the corresponding transformation.
(x*, y*) = T2(x*, y*) = ((x* + 1)/2, y*/2).
So x* = x*/2 + 1/2 and y* = y*/2, so x* = 1 and y* = 0.
17
2/22/2013
The next simplest repeated sequence is a 2-cycle
it alternates between two values.
Some more sequences of points generated by other 2-cycles.
The next simplest repeated sequence is 121212... = (12).
Applying T1 and T2 alternately produces a sequence of points converging to two points
along the x-axis
(13)
(14)
limit points of (14)
What cycle is this?
2-cycle Coordinates
2-Cycle Addresses
The limiting points in the last example have coordinates (1/3, 0) and (2/3, 0).
The limiting points in the last example [121212... ] have addresses (12) and (21). To
see this, recall the relation between the address and the order in which the transformations
are applied. The sequence 121212... gives points in regions with addresses
To see this, say (x1, y1) is the point with address (12) and (x2, y2) is the point with
address (21). Then notice
T2(x1, y1) has address 2(12) =
2(12)(12)(12)(12)... = (21)(21)(21)(21)... = (21)
1
21
Because T2(x1, y1) and (x2, y2) have the same (infinite) address,
121
T2(x1, y1) = (x2, y2)
2121
By a similar argument,
12121
T1(x2, y2) = (x1, y1).
combining these two, we see
212121
and so on.
1
121
Alternate
entries in the
sequence are
2121
12121
1212121
T1T2(x1, y1) = (x1, y1)
and
T2T1(x2, y2) = (x2, y2).
21
From the first we obtain
212121
And
...
21212121
(x1, y1) = T1T2(x1, y1) = T1(x1/2 + 1/2, y1/2) = (x1/4 + 1/4, y1/4),
so
x1 = x1/4 + 1/4 and y1 = y1/4
...
(12)
(21)
Choice of Initial Point
How do the limiting points depend on the choice of (0.5, 0.5) as starting point?
Solving for x1 and y1, we obtain (x1, y1) = (1/3, 0). A similar argument gives (x2, y2) = (2/3, 0).
3-Cycles
The repeating pattern
Not at all.
This should be no surprise: recall the attractor of an IFS does not depend on
the initial picture. (This is a bit different than the situation at hand, however, but
certainly makes the result plausible.)
T1 followed by T2 followed by T3
produces a sequence converging to the three points with addresses
(321), (132), and (213).
Here is an illustration. We follow the sequences generated from three different
starting points, all with vertices selected in the order 121212... = (12). Blue
lines for one starting point, green for the second, red for the third.
the three points to which these
sequences converge, along
with their addresses
18
2/22/2013
3-Cycle Addresses
3-Cycle Coordinates
Solving the fixed point equations gives the coordinates of each
point. For example,
The point with address (321) is the fixed point of T3T2T1.
To see this, say (x, y) is the point with address (321). Then
(x, y) = T3T2T1(x, y) = T3T2(x/2, y/2)
= T3(x/4 + 1/2, y/4) = (x/8 + 1/4, y/8 + 1/2)
T1(x, y) has address 1(321),
so
T2T1(x, y) has address 21(321), and
x = x/8 + 1/4 and y = y/8 + 1/2
T3T2T1(x, y) has address 321(321)infinity = (321)
Solving for x and y gives (x, y) = (2/7, 4/7)
Because (x, y) and T3T2T1(x, y) have the same (infinite) addresses, they are the
same point.
Similar calculations show
Similarly,
(1/7, 2/7) is the fixed point of T1T3T2
the point with address (132)is the fixed point of T1T3T2, and
and
(4/7, 1/7) is the fixed point of T2T1T3
the point with address (213)is the fixed point of T2T1T3.
3-Cycle in a different order
What happens if we apply the 3-cycle
transformations in a different order?
To understand why this is so, write the first several terms of both sequences
123123123123123123123123123123...
312312312312312312312312312312...
If we repeat the pattern
T3 followed by T1 followed by T2
The second sequence is just the first shifted two terms to the left.
instead of
T1 followed by T2 followed by T3?
Limiting points
123123123123123123123123123123...
312312312312312312312312312312...
Same as produced
by this
The first sequence is the same as the second, but starting from
T2T1(0.5, 0.5) instead of from (0.5, 0.5).
As with the fractals generated by regular IFS, here the final pattern does not
depend on the starting point. We prefer to start with (0.5, 0.5) because this
is the most neutral choice.
Can you find an order of cycling through 1,2, and 3 that converges
to a different triple of points?
The sequence
T2 followed by T1 followed by T3?
N-Cycles
produces sequences of points converging to the points
(1/7, 4/7), (4/7, 2/7), and (2/7, 1/7)
shown below on the left.
The number of points to which the sequence converges is the
length of the (shortest) repeated pattern.
For comparison, the previous 3-cycle is shown on the right.
The reason for shortest is that the
sequences (123) and (123123) converge to the same three
points.
The same points are produced by any cyclic permutation of the original sequence.
For example, the cyclic permutations of
T2 followed by T1 followed by T3,
are
T1 followed by T3 followed by T2, and T3 followed by T2 followed by T1.
19
2/22/2013
Driven IFS with Forbidden Combinations
Because the subsquare S4 contains no points, the subsquares
T1(S4) = S14, T2(S4) = S24, and T3(S4) = S34 contain no points.
Gaps in the driven IFS picture indicate combinations
of transformations that do not occur.
To understand the effect of forbidden combinations, we use
the addresses of regions of the unit square S.
We begin with three simple examples.
Forbid a transformation: T4 never occurs
If T4 is never applied, then no points land in the subsquare S4 with
address 4. That is, the upper right subsquare is completely empty.
Forbid a pair: T4 never immediately follows T1
If T4 never immediately follows T1, then no points land in the square T4(S1) = S41.
Continuing, the subsquares T1(S14) = S114, T1(S24) = S124, T1(S34) = S134, ...,
The
result
of continuing this process is clear:
and T
3(S34) = S334 contain no points. That is,
if Tif4 i=4,
is never
applied,
every
square whose
address
a 4 isleft).
empty.
j=4, or
k=4, the
subsquare
Sijk contains
no contains
points (below
Similarly,
With this restrction, we see the IFS generates a right isosceles Sierpinski gasket.
the subsquare S contains no points if any of i, j, k, or m is 4 (below right).
This is no surprise,ijkm
because the IFS {T1, T2, T3} generates a right isosceles
Sierpinski gasket.
Another Example of forbidden pair
We impose these restrictions:
T1 never immediately follows T4
T2 never immediately follows T3
T3 never immediately follows T2
T4 never immediately follows T1
What are the first few generations of the IFS with these restrictions?
Because S41 contains no points, the subsquares T1(S41) = S141, T2(S41) = S241, T3(S41) = S341,
and T4(S41) = S441 contain no points
First, note these restrictions imply no points land in the squares with addresses
14, 23, 32, and 41. That is, the shaded squares will contain no points
Continuing, here are the pictures showing the subsquares of address length 4
(left) and 5 (right) containing no points.
The pattern should be clear:
no points lie in any subsquare with address containing 41.
Here is a movie showing the first few iterates of the driven IFS with these
restrictions. In contrast to the diagrams above, here the nonempty regions
are shaded
Continuing on to the length 3 address squares, we see
every square with address including 14, 23, 32, and 41 will
contain no points. For example,
Graphical Representation
For those Driven IFS determined completely by forbidden pairs, a compact
representation of the IFS can be given by a graph showing the allowed pairs.
The graph has four vertices, one for each Ti,
and an edge from vertex i to vertex j if Ti can be be followed immediately by Tj.
For example, the Driven IFS with the single forbidden pair 41 has this graph:
These examples illustrate the general situation: if some combination of Tin...Ti1 of
transformations never occurs, then all subsquares with addresses containing the
sequence in...i1 must be empty.
The transformation combinations that never occur are called forbidden
combinations. For example, if T4 never immediately follows T1, we say 41 is
a forbidden pair.
Because T1 cannot be immediately followed by T4, the graph has no arrow
from vertex 1 to vertex 4.
All other combinations are allowed, so all other pairs of edges are connected
by arrows.
20
2/22/2013
Examples of Driven IFS with Forbidden Pairs
Different combinations of forbidden pairs can generate some very interesting
pictures.
Finally we move on to driving IFS by numerical data series
Not all data are written in an alphabet of four symbols. Can we adapt the driven
IFS method to study a wider variety of data, daily closing stock prices, for
example? The answer is yes. As a first step, we must coarse-grain the data.
Driven IFS and Data Analysis
equal-size bins Divide the range of values into four intervals of equal length.
equal weight bins Arrange the bin boundaries so (approximately) the same number of points lie in each bin.
Coarse-Graining the Data
We turn the data y1, y2, ..., yN into a sequence i1, i2, ..., iN of 1s, 2s, 3s, and 4s,
called the symbol string associated with the data.
zero-centered bins For data whose sign is important, take 0 as the boundary between bins 2 and 3; place the other
boundaries symmetrically above and below 0. Unlike the first two cases, this is a family of coarse-grainings depending
on the placements of the other two bin boundaries.
Often the data values yi are measured as decimals and because we are
converting these to only four values, the process of turning the yk into ik is
called coarse-graining.
mean-centered bins Take the mean of the data to be the boundary between bins 2 and 3; place the other boundaries
symmetrically above and below the mean, usually expressed as a multiple of the standard deviation.
The range of y values for corresponding to a symbol is the bin of that symbol.
median-centered bins Take the median of the data to be the boundary between bins 2 and 3; place the other
boundaries symmetrically above and below the median, usually expressed as a multiple of the range. Note the equalweight bins are a special case of this.
Though there are others, we use five kinds of coarse-graining:
Equal-Size Bins
The numbers separating the bins are called bin boundaries, B1, B2, and B3:
One method of converting the measured data y1, y2, ..., yN into a symbol string i1, i2,
..., iN is first to find the range of the values, that is, the interval between the maximum
(max) and the minimun (min) of the yi.
B3 = min + .75(max - min)
B2 = min + .50(max - min)
B1 = min + .25(max - min)
Next, divide the range (min, max) into four equal-size bins:
yk lies in bin1 if min yk < min + .25(max - min)
Each yk lies in one of these bins, so we can
convert the sequence y1, y2, y3 ... into the
symbol string i1, i2, i3 ... of 1s, 2s, 3s, and
4s associated with the data.
ik = 4 if yk lies in bin4
ik = 3 if yk lies in bin3
ik = 2 if yk lies in bin2
ik = 1 if yk lies in bin1
yk lies in bin2 if min + .25(max - min) yk < min + .50(max - min)
yk lies in bin3 if min + .50(max - min) yk < min + .75(max - min)
yk lies in bin4 if min + .75(max - min) yk max
21
2/22/2013
Zero-Centered Bins
Equal Weight Bins
Another method of converting the measured data y1, y2, ..., yN into a symbol
string i1, i2, ..., iN is to select the bin boundaries B1, B2, and B3 so
While there is no reason to think 0 holds any special importance for the data set
y1, y2, ..., yN,
it may for the first differences
one quarter of the yk satisfy yk B1,
y2 - y1, y3 - y2, ..., yN - yN-1.
one quarter of the yk satisfy B1 < yk B2,
For instance, a positive first difference means the data values are increasing, a negative
first difference means the data values are decreasing. This has clear significance for
financial data.
one quarter of the yk satisfy B2 < yk B3, and
one quarter of the yk satisfy B3 < yk.
Because each bin contains the same number of points, this is called an equalweight binning.
One way to produce an equal-weight binning is to sort the list of yk in increasing
order. Then take
Take B2 = 0, and in the absence of other information, take B1 and B3 symmetrically
spaced about B2 = 0.
Usually express B1 and B3 as a fraction of the range of the differences.
B3 the element one-quarters of the way from the top of the sorted list,
B2 the element of one-half of the way from the top of the sorted list, and
B1 to be the element three-quarter of the way from the top of the sorted list.
Equal-weight bins can be called
a maximum entropy partition.
Comparing Stocks and Indices by Driven IFS
Mean-Centered Bins
Another way to bin the data is to set B2 = m, the mean of the data values, and set B1 and
B3 to some fraction of or multiple of the standard deviation.
In his project, Joseph Thornton investigated some variants on driving IFS by
financial data.
He use daily closing prices for a two year period, about 500 data points.
Daily Percentage Changes
First we look at two years' data for several stocks, using daily percentage
changes to set the bin boundaries. Observing that the market tends to
fluctuate most often between +2.5% and -2.5%, as a first experiment
Thornton looked at daily changes in stock prices and used zero-centered
bins with these bin boundaries
Median-Centered Bins
Another way to bin the data is to set B2 = m, the median of the data values, and set
B1 and B3 to some fraction of the range.
B3: the price increases by > 2.5% its previous value
B2: the price remains unchanged
B1: the price decreases by < -2.5% its previous value
Here are the driven IFS
Note that for Citigroup, AI, GE, Tyson, and Colgate-Palmolive, the predominant feature is strong
motion along the 2-3 diagonal, indcating most changes are within 2.5% of the previous price.
Citigroup
American
International
General Electric
Another feature, especially strong in the GE graph, is the absence of points along the 14 diagonal. Although there are points in address 1 and 4 (even in address 11 and 44), there are
very few consecutive moves of > +2.5% followed by < -2.5%, and vice versa.
Contrast this with Sonus, where most of the activity in along the 1-4 diagonal, indicating relatively
wild swings in closing price. The heavy cluster of points in corner 1 does not speak of a successful
stock.
Dell
Sonus Networks
Qwest
Tyson Foods
ColgatePalmolive
Lucent
Roughly speaking, the older economy companies - Citigroup, Tyson, Colgate-Palmolive, GE, and
AIG - have stronger 2-3 diagonals, indicating less volatile behavior.
22
2/22/2013
Here are the rescaled driven IFS (left), each grouped with its original (right) for
comparison.
scaling
Next we experiment with uniformizing the driven IFS by scaling the bin
boundaries with the stock's value.
The factor of a stock is the volatility of the stock relative to that of the market.
> 1 means the stock is more volatile than the market.
= 1 means the stock and the market are equally volatile.
< 1 means the stock is less volatile than the market.
Citigroup: = 1.33
The 1-4 diagonals of the tech stocks reflects larger daily percentage changes, so
we would expect higher volatility.
As a quantitative test of this, Thornton scaled the bin boundaries with each stock's
. For example, Qwest has = 2.15, so the first and third bin boundaries are set
at2.15x2.5% = 5.38% above and below 0.
American International: = 0.85
IFS Driven by Texts
Driven IFS is a potentially interesting tool for analyzing patterns in data, but we
need to be careful with how the data are binned.
General Electric: = 1.08
Dell: = 1.83
A text is a string, but in an alphabet of more than four symbols. How can we
convert this into a string in an alphabet of four symbols?
One possibility is to treat words as the fundamental units
of the text, and assign bins by parts of speech. This has
an obvious problem: distinguishing how much of the
driven IFS structure is due to the author's style, and how
much to grammatical constraints.
Sonus: = 4.95
Another choice is to treat letters as the fundamental
units and assign bins by ignoring some letters, or grouping
the letters together. Of course, any choices must be
justified in a way reflecting properties of the text. This is
not an easy problem.
Tyson: = 0.47
Note that in general rescaling the bin boundaries by the stock's makes the
driven IFS look much alike. Note particularly the change in the Sonus IFS.
The obvious exception is Tyson, whose is so small that the rescaling puts many
more points into bins 1 and 4.
Phonological analysis
Here are the phonological categories used.
As we have seen, suitable ways of binning texts are elusive.
Binning by phonemes, individual sounds making up the words of a spoken language, is a
promising direction, especially because phomemes can be divided into a small collection of
categories.
In her spring 2003 project, Emily Runde studied phonological properties in two of T. S. Eliot's
poems, The Love Song of J. Alfred Prufrock and Hollow Men.
Category
vowels
Examples
a, e
glides
y, w
liquids
nasals
l, r
m, n, ng
Do these poems exhibit similar phonological patterns? What about patterns in Lewis
Carroll's Jabberwocky, which contains many fabricated words?
obstruents
Will Elliot's texts, Tradition and the Individual Talent for example, reveal different patterns?
fricatives
plosives
s, f, th
p, t, k
affricatives
ch, dg
syllabic boundary
word boundary
all other consonants
Description
no vocal tract friction, most
sonorous
consonantal forms of vowels i
and u, slightly less sonorous
friction caused by the tongue
slightly more friction,
articulated through the nose
varying degrees of vocal tract
constriction
partial vocal tract constriction
air buildup with complete
vocal tract closure, then
released in a short burst
fricative and plosive sound
combined
word boundaries supersede
syllable boundaries
23
2/22/2013
First she analyzed these pieces using a four bin IFS with the familiar transformations
The order of the transformations is determined by the order in which
the phonological categories occur in the text, according to this correspondence.
T3: liquids and nasals
T4: all obstruents
T1: vowels
T2: glides
Some analysis
In all four the squares 22, 32, and 42 are empty, indicating only a vowel can follow a glide.
Love Song of J. Alfred Prufrock
In all four the squares 111, 234, 334, and 434 are empty.
Hollow Men
111: three successive vowels do not occur.
234, 334, 434: a vowel must follow the combination obstruent then liquid or nasal.
Prufrock, Jabberwock, and Tradition all have 212 empty, while Hollow does not.
Consequently, glide-vowel-glide is possible, but uncommon, at least among these samples.
Tradition has 433 empty, while Prufrock, Jabberwock, and Hollow do not.
(In Jabberwock why does the point on the boundary between 433 and 344 belong to 433?) Is
this combination a phonological construction that distinguishes poetry from prose?
Jabberwocky
Tradition and the Individual Talent
Some analysis
Next she analyzed these pieces using a nine bin IFS.
In all four the squares 22, 32, 42, 52, 62, 72, 82, and 92 are empty: only a vowel can follow a glide.
In all four, 23 and 26 are empty: a glide cannot follow a liquid or an affricate.
In all four, among *8 (for * = 1, ..., 7) the most filled in are 58 and 78: syllables begin with fricatives or
plosives more often than with other phonemes.
Among *9 the most filled are 19, 59, and 79: words begin with vowels as often as with fricatives or plosives.
In all four, among 8* the most filled is 81: syllables are more likely to end with vowels.
T7:
plosives
Love Song of J. Alfred Prufrock
T8: syllabic T9: word
boundaries boundaries
T4: nasals
T5:
fricatives
T6:
affricatives
T1: vowels
T2: glides
T3: liquids
The common sonority profile is an arc: often a syllable begins with a low sonority phoneme, followed by one
of higher sonority, then lower.
Hollow Men
831 is more densely filled than 871: after a vowel a syllable is more likely to end in a nasal than in a plosive.
781 is densely filled: after a syllable ends with a vowel the next syllable can start with a plosive.
The rules governing nasals and liquids are similar: in each of the four plots, the pattern in square 3 is similar
to that in square 4.
In each of the four plots, the pattern in 5 is similar to that in 7 (6 also is similar, though much less filled),
indicating that the three subcategories of obstruents behave similarly.
Although 57 and 75 are fairly populated, 55 and 77 are not, and in general the pairs ii are (nearly) indicating
that only rarely do two phomemes of the same phonemic category occur adjacently within a syllable.
Jabberwocky
Tradition and the Individual Talent
Finally, the patterns in 8 and 9 are similar, thought 9 is more filled, indicating many one-syllable words.
Although the sonority profile refers to a syllable rather than to a word, this shows the same pattern of sonority
near a syllable boundary is repeated at word boundaries.
Nine Bin IFS Rules
T7(x,y) = (x/3, y/3) + (0, 2/3)
T8(x,y) = (x/3, y/3) + (1/3, 2/3) T9(x,y) = (x/3, y/3) + (2/3, 2/3)
T4(x,y) = (x/3, y/3) + (0, 1/3)
T5(x,y) = (x/3, y/3) + (1/3, 1/3) T6(x,y) = (x/3, y/3) + (1/3, 2/3)
T1(x,y) = (x/3, y/3)
T2(x,y) = (x/3, y/3) + (1/3, 0)
T3(x,y) = (x/3, y/3) + (2/3, 0)
These transformations generate the unit square by dividing it into nine
subsquares, each of 1/3 the width and height of the unit square.
Here are the length 1 addresses.
Here are the length 2 addresses.
24
You might also like
- Microsoft Excel Assignments 1Document4 pagesMicrosoft Excel Assignments 1Snehasis Bose100% (1)
- SAT MathDocument6 pagesSAT MathMinh ThànhNo ratings yet
- Creating Visual Music in Jitter - Approaches and TechniquesDocument17 pagesCreating Visual Music in Jitter - Approaches and TechniquesKiyoshi Kubota100% (2)
- Swarm Intelligence in ArchitectureDocument102 pagesSwarm Intelligence in ArchitectureNivedita RamachandranNo ratings yet
- Self-Regularity: A New Paradigm for Primal-Dual Interior-Point AlgorithmsFrom EverandSelf-Regularity: A New Paradigm for Primal-Dual Interior-Point AlgorithmsRating: 5 out of 5 stars5/5 (1)
- Hildebrand CADocument746 pagesHildebrand CAAngel GallardoNo ratings yet
- Part III: Applications of Differential Geometry To PhysicsDocument88 pagesPart III: Applications of Differential Geometry To PhysicsKummerianNo ratings yet
- Mat495 Chapter 8Document18 pagesMat495 Chapter 8MuhamadSadiqNo ratings yet
- Fractals: Siva Sankari, Sathya Meena, Aarthi, Ashok Kumar, Seetharaman Mohamad Habibur RahmanDocument31 pagesFractals: Siva Sankari, Sathya Meena, Aarthi, Ashok Kumar, Seetharaman Mohamad Habibur RahmanManimegalai PrasannaNo ratings yet
- Fractals and MusicDocument9 pagesFractals and MusicMelanie AllenNo ratings yet
- Spatial Swarm GranulationDocument4 pagesSpatial Swarm GranulationCillian DementoNo ratings yet
- A Workbook On Implementing L-System Fractals Using PythonDocument9 pagesA Workbook On Implementing L-System Fractals Using PythonShibaji BanerjeeNo ratings yet
- Algorithmic Music Generation With Reaktor v02Document8 pagesAlgorithmic Music Generation With Reaktor v02Beturbio VturvioNo ratings yet
- Fractals GEOMETRYDocument49 pagesFractals GEOMETRYmia_s100% (1)
- Understanding FractalsDocument3 pagesUnderstanding FractalseusebimtNo ratings yet
- Fractal Geometry and Superformula To Model Natural Shapes Over The WorldDocument15 pagesFractal Geometry and Superformula To Model Natural Shapes Over The WorldEndless LoveNo ratings yet
- New Substractive Synthesis of Violin Sound1Document6 pagesNew Substractive Synthesis of Violin Sound1ARVINDNo ratings yet
- 926 Music DSPDocument265 pages926 Music DSPeircom100% (1)
- Csound5.13 ManualDocument2,783 pagesCsound5.13 ManualqwerqwerasdfasdfNo ratings yet
- Simplexity: Apprenticeship Pitch at The Beginning of The SemesterDocument9 pagesSimplexity: Apprenticeship Pitch at The Beginning of The SemesterNoelia Valderrama BhraunxsNo ratings yet
- Form Generation Fractals ExampleDocument10 pagesForm Generation Fractals ExampleRoopa Narayan SahooNo ratings yet
- The Topos of Music Geometric Logic of Concepts TheDocument20 pagesThe Topos of Music Geometric Logic of Concepts TheDarpan D.100% (1)
- Boids - Modeling and Understanding Emergent BehaviorDocument15 pagesBoids - Modeling and Understanding Emergent Behaviorstudsudzzz100% (1)
- Figurate NumbersDocument10 pagesFigurate Numbersjmertes100% (1)
- Sympy Docs PDF 1.4 PDFDocument2,127 pagesSympy Docs PDF 1.4 PDFHarshitNo ratings yet
- Real-Time Analysis, in SuperCollider, of Spectral Features of Electroglottographic Signals DENNIS JOHANSSONDocument71 pagesReal-Time Analysis, in SuperCollider, of Spectral Features of Electroglottographic Signals DENNIS JOHANSSONMichael Przybylski100% (1)
- 02 WholeDocument306 pages02 Wholea2kjaoNo ratings yet
- Data Visualization With Mathematica - No 3D RasterizationDocument41 pagesData Visualization With Mathematica - No 3D Rasterizationebujak100% (1)
- Christopher Ariza - Computer-Aided Algorithmic Composition SystemsDocument8 pagesChristopher Ariza - Computer-Aided Algorithmic Composition Systemsquietchannel100% (1)
- 10 1 1 391 1581Document151 pages10 1 1 391 1581Papadakis ChristosNo ratings yet
- FractalsDocument29 pagesFractalsrajivrama75% (4)
- Design and Implementation of A Graph Grammar Based Language For Functional-Structural Plant Modelling - Thesis PDFDocument444 pagesDesign and Implementation of A Graph Grammar Based Language For Functional-Structural Plant Modelling - Thesis PDFSurdu SorinNo ratings yet
- Goldenratio MathDocument145 pagesGoldenratio MathJohn AsoteaNo ratings yet
- Stilson-Smith - Alias-Free Digital Synthesis of Classic Analog Waveforms (BLIT)Document12 pagesStilson-Smith - Alias-Free Digital Synthesis of Classic Analog Waveforms (BLIT)HangTheBankersNo ratings yet
- Omchroma 1.0 PDFDocument82 pagesOmchroma 1.0 PDFStefano Franceschini100% (1)
- Alcuin's Sequence - WikipediaDocument6 pagesAlcuin's Sequence - WikipediaGary SynthosNo ratings yet
- Amiot Et Al. - 2007 - Autosimilar Melodies and Their Implementation in OpenMusicDocument5 pagesAmiot Et Al. - 2007 - Autosimilar Melodies and Their Implementation in OpenMusicTateCarson100% (1)
- Modal Synthesis of Weapon Sounds PDFDocument7 pagesModal Synthesis of Weapon Sounds PDFDmitry NemtsoffNo ratings yet
- Newton's Fractals in PythonDocument19 pagesNewton's Fractals in PythonJoshua CookNo ratings yet
- Olychordsto PolyaDocument177 pagesOlychordsto PolyaMoises Jimenez100% (1)
- A Computer Model For The Schillinger System of Composition (Rankin) PDFDocument137 pagesA Computer Model For The Schillinger System of Composition (Rankin) PDFgilgoosNo ratings yet
- Physical Geodesy: Martin VermeerDocument520 pagesPhysical Geodesy: Martin VermeerreflectiondarkNo ratings yet
- R3 - Dive Into Deep Learning - Zhang Lipton Li SmolaDocument1,025 pagesR3 - Dive Into Deep Learning - Zhang Lipton Li SmolaSUJOY SAMADDAR100% (1)
- Cottle Computer Music Using SC3Document403 pagesCottle Computer Music Using SC3GLVNo ratings yet
- Cellular Automata in Generative Electronic Music and Sonic ArtDocument30 pagesCellular Automata in Generative Electronic Music and Sonic ArtAgence AudiosphericNo ratings yet
- Tutorial For Frequency Modulation Synthesis Barry TruaxDocument7 pagesTutorial For Frequency Modulation Synthesis Barry TruaxdcocharroNo ratings yet
- Mathematica TutorialDocument131 pagesMathematica TutorialErdenebaatar KhurelhuuNo ratings yet
- Javamagazine20130304 DLDocument78 pagesJavamagazine20130304 DLjavadev_ruNo ratings yet
- Common Lisp Quick ReferenceDocument6 pagesCommon Lisp Quick ReferenceGiova RossiNo ratings yet
- Ma Thematic A Cheat SheetDocument2 pagesMa Thematic A Cheat Sheetlpauling100% (1)
- Difference Equations & Z-TransformsDocument8 pagesDifference Equations & Z-Transformsvidya_sagar826No ratings yet
- The Mathematica Guidebook For ProgrammingDocument871 pagesThe Mathematica Guidebook For ProgrammingFlorent100% (1)
- Advanced Numerical Integration in MathematicaDocument178 pagesAdvanced Numerical Integration in MathematicaDimitris LeivaditisNo ratings yet
- Python - Make Your Own Mandelbrot Set PDFDocument8 pagesPython - Make Your Own Mandelbrot Set PDFRicardo_SemogNo ratings yet
- SuperCollider HelpBookDocument2,325 pagesSuperCollider HelpBookJoseph Gatt100% (4)
- Digital Sound Synthesis by Physical ModellingDocument12 pagesDigital Sound Synthesis by Physical ModellingBrandy ThomasNo ratings yet
- Theoretical and Applied MechanicsFrom EverandTheoretical and Applied MechanicsP. GermainNo ratings yet
- Control System Engineering U A BakshiDocument835 pagesControl System Engineering U A Bakshikumara_raja1980% (95)
- LECT3 Probability TheoryDocument42 pagesLECT3 Probability Theoryhimaanshu09No ratings yet
- Solucionario CAP 5 RAZAVIDocument112 pagesSolucionario CAP 5 RAZAVIBenjaminJimenezNo ratings yet
- L07 ElectrostaticDocument22 pagesL07 Electrostatichimaanshu09No ratings yet
- Curl of A Vector: Dr. Rajib Kumar PanigrahiDocument21 pagesCurl of A Vector: Dr. Rajib Kumar Panigrahihimaanshu09No ratings yet
- List of Mathematical Series - Wikipedia, The Free EncyclopediaDocument8 pagesList of Mathematical Series - Wikipedia, The Free EncyclopediapummykidNo ratings yet
- WCE2014 pp1404-1409Document6 pagesWCE2014 pp1404-1409hykiNo ratings yet
- IGCSE Math Revision PlanDocument3 pagesIGCSE Math Revision PlanBảo Đỗ DuyNo ratings yet
- Homework Set 1: Due August 14Document3 pagesHomework Set 1: Due August 14jog10No ratings yet
- Public Sector EconomicsDocument9 pagesPublic Sector EconomicszahirkhokanNo ratings yet
- Elliptic, Napier, Dependent Triangles of Discretely Normal Monodromies and Questions of LocalityDocument7 pagesElliptic, Napier, Dependent Triangles of Discretely Normal Monodromies and Questions of Localitymdp anonNo ratings yet
- Bayesian Belief NetworkDocument30 pagesBayesian Belief NetworkGuru75No ratings yet
- Gauss Quadrature 2 Point and 3 Point Formula PDFDocument9 pagesGauss Quadrature 2 Point and 3 Point Formula PDFRavi ParkheNo ratings yet
- Lee, Huey-MingDocument6 pagesLee, Huey-MingNgaa SiemensNo ratings yet
- EN40: Dynamics and Vibrations: Solutions To Differential Equations of Motion For Vibrating SystemsDocument8 pagesEN40: Dynamics and Vibrations: Solutions To Differential Equations of Motion For Vibrating SystemsMilad RadNo ratings yet
- Discrete Math Final Exam - November2023Document3 pagesDiscrete Math Final Exam - November2023TonnyNo ratings yet
- ECE 261 Project Presentation 2: Eric Wang Federico Gonzalez Bryan Flemming Jep BarbourDocument24 pagesECE 261 Project Presentation 2: Eric Wang Federico Gonzalez Bryan Flemming Jep Barbourajith.ganesh2420No ratings yet
- PseudocodeDocument33 pagesPseudocodegaurav sharmaNo ratings yet
- BSC CS SemDocument42 pagesBSC CS SemVinay KumarNo ratings yet
- RSA AlgorithmDocument22 pagesRSA AlgorithmmathpalsonuNo ratings yet
- Digital Signal Processing: Classification of Discrete Time SignalDocument23 pagesDigital Signal Processing: Classification of Discrete Time Signaltamizh kaviNo ratings yet
- Tolerance, Fits & AssemblyDocument26 pagesTolerance, Fits & AssemblyNguyenThiKhanhLy100% (1)
- Engineering Graphics LabsDocument8 pagesEngineering Graphics LabsShrey VimalNo ratings yet
- EN1201: Introductory Mathematics: University of Colombo, Sri LankaDocument6 pagesEN1201: Introductory Mathematics: University of Colombo, Sri LankaJanaka Bandara100% (1)
- QBUS6820 HO Week 8 Stochastic OptimizationDocument16 pagesQBUS6820 HO Week 8 Stochastic OptimizationdanyhuangNo ratings yet
- Detailed Lesson Plan-Parallel & Perpendecular LinesDocument4 pagesDetailed Lesson Plan-Parallel & Perpendecular LinesFrances Bert BalajadiaNo ratings yet
- MA1010 Notes 1Document38 pagesMA1010 Notes 1Kaushik Ram SNo ratings yet
- Ncert Solutions Class 8 Math Chapter 2 Ex 2 4Document11 pagesNcert Solutions Class 8 Math Chapter 2 Ex 2 4Vinayak MauryaNo ratings yet
- Deep Learning BookDocument1,029 pagesDeep Learning BookDr Paramkusam AV100% (1)