Professional Documents
Culture Documents
Vimeo IDOR
Vimeo IDOR
Uploaded by
Arrch Silverberg0 ratings0% found this document useful (0 votes)
30 views4 pagesThis document describes an insecure direct object reference (IDOR) vulnerability discovered by Toufik Airane on the video sharing website Vimeo.com. It provides details on the timeline of discovery and disclosure to Vimeo, as well as an overview of how IDOR vulnerabilities work. It then demonstrates a proof of concept by retrieving a user ID from Vimeo's public API and showing how an attacker could potentially reset any user's password by manipulating the direct object reference in the password reset URL.
Original Description:
akoskdlaksldkasldkalsdklaksdlaksdl JUST UPLOADING FOR FREE ACCSESS
Original Title
Vimeo.IDOR
Copyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentThis document describes an insecure direct object reference (IDOR) vulnerability discovered by Toufik Airane on the video sharing website Vimeo.com. It provides details on the timeline of discovery and disclosure to Vimeo, as well as an overview of how IDOR vulnerabilities work. It then demonstrates a proof of concept by retrieving a user ID from Vimeo's public API and showing how an attacker could potentially reset any user's password by manipulating the direct object reference in the password reset URL.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
30 views4 pagesVimeo IDOR
Vimeo IDOR
Uploaded by
Arrch SilverbergThis document describes an insecure direct object reference (IDOR) vulnerability discovered by Toufik Airane on the video sharing website Vimeo.com. It provides details on the timeline of discovery and disclosure to Vimeo, as well as an overview of how IDOR vulnerabilities work. It then demonstrates a proof of concept by retrieving a user ID from Vimeo's public API and showing how an attacker could potentially reset any user's password by manipulating the direct object reference in the password reset URL.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
You are on page 1of 4
Vimeo.
com
Insecure Direct Object References
Reset Password
Toufik Airane
@tfairane
toufik.airane@gmail.com
www.tfairane.com
LATEX
January 5, 2015
Contents
1 Introduction
1.1 Metadata . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
1.2 Timeline . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
1.3 Contact . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
2
2
2
2
2 Proof Of Concept : IDOR
3 IDOR Defense Cheat Sheet
4 Prepare the feat
4.1 retrieve UserID . . . . . . . . . . . . . . . . . . . . . . . . . . . .
3
3
5 Scenario / Exploit
Introduction
Hi, my name is Toufik Airane, student in IT security from University of Paris
Descartes.
1.1
Metadata
vulnerability : Insecure Direct Object References (IDOR)
affect : reset password of any account with userid
media : http://tfairane.com/archives/Vimeo.IDOR.mp4
tools : Burp Suite
1.2
Timeline
30/12/2014 : discovered date (Happy new year !)
05/01/2015 : responsible disclosure on hackerone.com
1.3
Contact
Gmail : toufik.airane@gmail.com
Twitter : @tfairane
website : www.tfairane.com
Thanks to Vimeo.com staff.
Proof Of Concept : IDOR
Foremost, what is IDOR attack ?
A direct object reference occurs when a developer exposes a reference to an internal implementation object, such as a file, directory,
database record, or key, as a URL or form parameter. An attacker
can manipulate direct object references to access other objects without authorization, unless an access control check is in place.
https://www.owasp.org/index.php/Top 10 2007Insecure Direct Object Reference
IDOR Defense Cheat Sheet
Avoid exposing your private object references to users whenever possible,
such as primary keys or filenames.
Validate any private object references extensively with an accept known
good approach
Verify authorization to all referenced objects
https://www.owasp.org/index.php/Top 10 2007Insecure Direct Object Reference
4
4.1
Prepare the feat
retrieve UserID
Sometimes, users can customize their url path as : http://vimeo.com/kerrytrainor
So, retrieve UserID is easy, just call Vimeo.com API.
http://vimeo.com/api/v2/kerrytrainor/info.xml
<u s e r s >
<u s e r >
<id >10272636</ id>
<d i s p l a y n a m e >Kerry Trainor </d i s p l a y n a m e >
<c r e a t e d o n >20120202 14:12:45 </ c r e a t e d o n >
< i s s t a f f >1</ i s s t a f f >
...
</u s e r >
</u s e r s >
Finally. vimeo.com/user10272636
Scenario / Exploit
First, an attacker signup for an account and request forgot password.
You will receive a link :
https://vimeo.com/forgot\ password/[user id]/[token]
You might also like
- OSMR Exam ReportDocument5 pagesOSMR Exam ReportMinh Duc DangNo ratings yet
- Sample Report - Threat ModelDocument7 pagesSample Report - Threat ModelLRampaul0% (1)
- Unit 5 - Assignment 1 Frontsheet-đã Chuyển Đổi-đã Chuyển Đổi-đã Chuyển ĐổiDocument17 pagesUnit 5 - Assignment 1 Frontsheet-đã Chuyển Đổi-đã Chuyển Đổi-đã Chuyển ĐổiĐạt NguyễnNo ratings yet
- Insecure Direct Object References Reset Password: Toufik Airane @tfairane L TEX January 5, 2015Document4 pagesInsecure Direct Object References Reset Password: Toufik Airane @tfairane L TEX January 5, 2015Sohel AhmedNo ratings yet
- DFT20083 - 2.1 Describe Security PolicyDocument26 pagesDFT20083 - 2.1 Describe Security Policyamin124010No ratings yet
- Practical (1, 2 & 3) (1) .Docx TulsiDocument38 pagesPractical (1, 2 & 3) (1) .Docx TulsiTulsi guptaNo ratings yet
- Securing A Java EE 7 ApplicationDocument15 pagesSecuring A Java EE 7 ApplicationLuís MeloNo ratings yet
- PBT Sbit ReportDocument8 pagesPBT Sbit ReportLivinniaa ThanthapaniNo ratings yet
- Monitoring and Administrating System IS With SelftestDocument30 pagesMonitoring and Administrating System IS With Selftestferuza musemaNo ratings yet
- Red Team TrainingDocument16 pagesRed Team TrainingFernando da Costa CorreaNo ratings yet
- 20BCA1335 Ashish-Yadav AssinmentDocument4 pages20BCA1335 Ashish-Yadav AssinmentimyadashuNo ratings yet
- Windows Defender ATP: Step by Step For AnyoneDocument27 pagesWindows Defender ATP: Step by Step For Anyonepascalburume100% (1)
- 20 Hacker Tricks For Attacking Web AppsDocument30 pages20 Hacker Tricks For Attacking Web Appscrosuperman1970No ratings yet
- Windows Security Internals: A Deep Dive Into Windows Authentication, Authorization, and Auditing 1 / Converted Edition James ForshawDocument43 pagesWindows Security Internals: A Deep Dive Into Windows Authentication, Authorization, and Auditing 1 / Converted Edition James Forshawfelicia.white827100% (6)
- (Download PDF) Windows Security Internals 1 Converted Edition James Forshaw Online Ebook All Chapter PDFDocument42 pages(Download PDF) Windows Security Internals 1 Converted Edition James Forshaw Online Ebook All Chapter PDFfelicia.white827100% (5)
- Hacking and Securing iOS ApplicationsDocument46 pagesHacking and Securing iOS ApplicationssatishbNo ratings yet
- Java Training-Spring CoreDocument95 pagesJava Training-Spring CoreDuy Chuong HuynhNo ratings yet
- Penetration TestingDocument19 pagesPenetration TestingAkiNiHandiongNo ratings yet
- Ai Web Report 1 1Document25 pagesAi Web Report 1 1Suraj TheekshanaNo ratings yet
- Insecure Data StorageDocument8 pagesInsecure Data Storagemscss projectNo ratings yet
- OWASP Mobile Top 10: Insecure Data StorageDocument8 pagesOWASP Mobile Top 10: Insecure Data Storagemscss projectNo ratings yet
- Source Code Disclosure Over HTTPDocument10 pagesSource Code Disclosure Over HTTPCiorcian CiorciNo ratings yet
- Information Disclosure VulnerabilityDocument8 pagesInformation Disclosure Vulnerabilitysetyahangga3No ratings yet
- JKSDC External Firewall Build DocumentDocument44 pagesJKSDC External Firewall Build DocumentPawan BhattaraiNo ratings yet
- 4 - Secure Design PrinciplesDocument19 pages4 - Secure Design Principlessadam endrisNo ratings yet
- Security Vulnerability Report - OracleDocument103 pagesSecurity Vulnerability Report - OracleDinuNo ratings yet
- Application Security Code Review GuidelinesDocument3 pagesApplication Security Code Review GuidelinesBhemunathinu MadhukarNo ratings yet
- Windows Security Internals - A Deep Dive Into Windows Authentication, Authorization, and Auditing (For True Epub) 1st Edition James ForshawDocument43 pagesWindows Security Internals - A Deep Dive Into Windows Authentication, Authorization, and Auditing (For True Epub) 1st Edition James Forshawfelicia.white827100% (7)
- Website HackingDocument23 pagesWebsite Hackingsuraj.hitech76No ratings yet
- ICTCYS613 Ebook v1.0Document111 pagesICTCYS613 Ebook v1.0contactNo ratings yet
- Application Security For The Android PlatformDocument112 pagesApplication Security For The Android PlatformwisterioNo ratings yet
- 1.1.4 Section QuizDocument6 pages1.1.4 Section QuizAshley AllenNo ratings yet
- China-Linked TA413 GroupDocument9 pagesChina-Linked TA413 GroupViren ChoudhariNo ratings yet
- Chapter 11. Basic Issues in Web Security: ObjectivesDocument4 pagesChapter 11. Basic Issues in Web Security: ObjectivesgebremariamNo ratings yet
- Keypass Password Protection ManagerDocument51 pagesKeypass Password Protection Managerhemant1122100% (2)
- Practical: 3: Aim: Determine and Analyze The Functional Non-Functional Requirements For A Given ProjectDocument12 pagesPractical: 3: Aim: Determine and Analyze The Functional Non-Functional Requirements For A Given ProjectKeval PatelNo ratings yet
- Two AuthenticationDocument41 pagesTwo AuthenticationABDULRAMAN ALWRIFINo ratings yet
- Software Requirement SpecificationDocument15 pagesSoftware Requirement SpecificationAnonymous 8axe1csezNo ratings yet
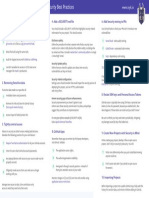
- Cheat Sheet: 10 Github Security Best Practices: WWW - Snyk.IoDocument1 pageCheat Sheet: 10 Github Security Best Practices: WWW - Snyk.Iolhewlett100% (1)
- Measures To Secure Existing College NetworkDocument8 pagesMeasures To Secure Existing College NetworkkunjanpbharadeNo ratings yet
- 2010KS Miriyala-Understanding in Depth Documentum SecurityDocument25 pages2010KS Miriyala-Understanding in Depth Documentum SecurityveerannjaneyuluNo ratings yet
- Aditya Gupta (@adi1391)Document20 pagesAditya Gupta (@adi1391)Ваня БаранNo ratings yet
- How To Detect Ransomware With FileAudit - Enterprise Network Security Blog From ISDecisionsDocument4 pagesHow To Detect Ransomware With FileAudit - Enterprise Network Security Blog From ISDecisionsAjay DhamijaNo ratings yet
- EDR Lab Tutorial Supplement - V4Document23 pagesEDR Lab Tutorial Supplement - V4Ali AbdelmalekNo ratings yet
- Hacking and Securing Ios ApplicationsDocument46 pagesHacking and Securing Ios Applicationsbiko alphonseNo ratings yet
- Cognos 10Document35 pagesCognos 10annareddypraveen100% (5)
- Securing Content: Solution Builder and Administrator Ibm Filenet Content ManagerDocument63 pagesSecuring Content: Solution Builder and Administrator Ibm Filenet Content ManagerDemianGodNo ratings yet
- ThesisDocument21 pagesThesisAkshay KrishnaNo ratings yet
- IDOR and HTTP Security HeadersDocument8 pagesIDOR and HTTP Security Headersshankar r100% (1)
- Cert-In: Web Server Security GuidelinesDocument22 pagesCert-In: Web Server Security GuidelinesRavikar ShyamNo ratings yet
- Review of Authentication MethodsDocument5 pagesReview of Authentication MethodsFXNo ratings yet
- Secure PL SQL CodingDocument33 pagesSecure PL SQL CodingHung DaoNo ratings yet
- Ios Platform SecDocument17 pagesIos Platform SecAlireza HemmatiNo ratings yet
- Protecting Windows Privileged AccountsDocument82 pagesProtecting Windows Privileged AccountsloclubuNo ratings yet
- Module 011 Log AnalysisDocument19 pagesModule 011 Log AnalysisRakesh PandeyNo ratings yet
- CCNA SecurityDocument14 pagesCCNA SecurityEric NapholzNo ratings yet
- GSPBC-1032 - Resource Development - Compromise AccountsDocument1 pageGSPBC-1032 - Resource Development - Compromise AccountsFaty DiopNo ratings yet
- Security Patterns: Integrating Security and Systems EngineeringFrom EverandSecurity Patterns: Integrating Security and Systems EngineeringNo ratings yet