Professional Documents
Culture Documents
Hidden Traffic Flow
Uploaded by
Raman Trivedi0 ratings0% found this document useful (0 votes)
7 views1 pageHidden traffic flow techniques schedule transmissions in advance through a transmitter scheduling generator and link decision generator to conceal actual network traffic patterns from eavesdroppers, even though the encrypted messages themselves may be intercepted. While this protects sensitive information, it reduces throughput by requiring transmissions to be scheduled ahead of time rather than sent immediately.
Original Description:
Basic understanding with HAVEQUICK
Copyright
© © All Rights Reserved
Available Formats
DOCX, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentHidden traffic flow techniques schedule transmissions in advance through a transmitter scheduling generator and link decision generator to conceal actual network traffic patterns from eavesdroppers, even though the encrypted messages themselves may be intercepted. While this protects sensitive information, it reduces throughput by requiring transmissions to be scheduled ahead of time rather than sent immediately.
Copyright:
© All Rights Reserved
Available Formats
Download as DOCX, PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
7 views1 pageHidden Traffic Flow
Uploaded by
Raman TrivediHidden traffic flow techniques schedule transmissions in advance through a transmitter scheduling generator and link decision generator to conceal actual network traffic patterns from eavesdroppers, even though the encrypted messages themselves may be intercepted. While this protects sensitive information, it reduces throughput by requiring transmissions to be scheduled ahead of time rather than sent immediately.
Copyright:
© All Rights Reserved
Available Formats
Download as DOCX, PDF, TXT or read online from Scribd
You are on page 1of 1
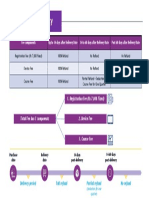
Hidden Traffic Flow: It is assumed that eavesdropper can detect the transmission, but can’t understand
the encrypted message being sent. Still eavesdropper can still deduce the information about the
network.
Ex: 1) Analyze traffic flow and detect the changes in traffic pattern.
2) Deduce the original sender of message.
3) Correlate traffic pattern with observable activities.
Thus hiding traffic flow technique has been used to protect the same. For that
Transmitter schedules Generator and link decision generator are used.
Input to TSG: 1) Network Topology
Input to LDG: 2) TSG, Network Topology and Traffic Demand.
For actual Traffic flow Link decision Generator are used, which is Hidden Traffic flow. And Eavesdropper
will only access TSG. By using this traffic flow is save.
Drawback: Reduced in the throughput, as its schedule in advance.
You might also like
- Hacking Network Protocols: Unlocking the Secrets of Network Protocol AnalysisFrom EverandHacking Network Protocols: Unlocking the Secrets of Network Protocol AnalysisNo ratings yet
- A New Cell-Counting-Based Attack Against TorDocument13 pagesA New Cell-Counting-Based Attack Against TorBala SudhakarNo ratings yet
- Iijcs 2014 03 13 028Document4 pagesIijcs 2014 03 13 028International Journal of Application or Innovation in Engineering & ManagementNo ratings yet
- Congestion Detection and Avoidance in Dynamic NetworksDocument4 pagesCongestion Detection and Avoidance in Dynamic NetworksEditor IJRITCCNo ratings yet
- HMMDocument5 pagesHMMyeahyeahyeahyeah69No ratings yet
- Oriented Multicast Routing Algorithm Applied To Network-Level Agent SearchDocument18 pagesOriented Multicast Routing Algorithm Applied To Network-Level Agent SearchAlex HillNo ratings yet
- Lecture 11Document17 pagesLecture 11تُحف العقولNo ratings yet
- Chapter 4 ACNDocument20 pagesChapter 4 ACNcdhvvgybfNo ratings yet
- Networking Asignment Outcome 3Document10 pagesNetworking Asignment Outcome 3Chamoadh DissanayakeNo ratings yet
- Unit 4 Lec4Document19 pagesUnit 4 Lec4SangetaNo ratings yet
- Distributed Denial of Service Attack ToolsDocument8 pagesDistributed Denial of Service Attack Toolschand123123No ratings yet
- SniffingDocument120 pagesSniffingWoyNo ratings yet
- 201980090184+computer Network Final AssignmentDocument10 pages201980090184+computer Network Final AssignmentMd. Ziaul Haque ShiponNo ratings yet
- Mini Project - 18CSC302J - COMPUTER NETWORKS: Team MembersDocument6 pagesMini Project - 18CSC302J - COMPUTER NETWORKS: Team MembersVijay RamrajNo ratings yet
- NETWORKINGDocument13 pagesNETWORKINGraghuvarunbtech777No ratings yet
- Networking Basics 1Document32 pagesNetworking Basics 1raghuvarunbtech777No ratings yet
- Study of TCP Throughput On Network Simulator Opnet++ by Using Different ParametersDocument6 pagesStudy of TCP Throughput On Network Simulator Opnet++ by Using Different Parametersgovind_misraaNo ratings yet
- TCP - Congestion Control Algorithm For Enhancing High-Speed NetworksDocument5 pagesTCP - Congestion Control Algorithm For Enhancing High-Speed NetworksJournal of Computer ApplicationsNo ratings yet
- An AnalysisAn Analysis of The Performance of An MIH Based Switch Strategy For Heterogeneous Network MobilityDocument8 pagesAn AnalysisAn Analysis of The Performance of An MIH Based Switch Strategy For Heterogeneous Network MobilityManasa RaiNo ratings yet
- Complete DocumentDocument41 pagesComplete DocumentRamesh KumarNo ratings yet
- Name: Hilal Rauf Subject: Advance Computer Networks Subject Code: BSIT - 62 Part: TBDocument7 pagesName: Hilal Rauf Subject: Advance Computer Networks Subject Code: BSIT - 62 Part: TBMukesh AgarwalNo ratings yet
- حل اسئلة شبكات الحاسوب الدور الاول 2023 en0Document10 pagesحل اسئلة شبكات الحاسوب الدور الاول 2023 en0jasmhmyd205No ratings yet
- Notes On Computer Networks Unit 3Document13 pagesNotes On Computer Networks Unit 3Rohit Chaudhary83% (6)
- An Approach To Detect Packets Using Packet Sniffing: Rupam, Atul Verma, Ankita SinghDocument13 pagesAn Approach To Detect Packets Using Packet Sniffing: Rupam, Atul Verma, Ankita SinghijcsesNo ratings yet
- Last Minute Notes - Computer Networks: OSI Layers, Data Units and Functions: Layers Data Units FunctionsDocument9 pagesLast Minute Notes - Computer Networks: OSI Layers, Data Units and Functions: Layers Data Units FunctionsYusuf HumayunNo ratings yet
- Design of A Wired Network Using Different TopologiesDocument12 pagesDesign of A Wired Network Using Different TopologiesSiva ShankarNo ratings yet
- L7 CN Network Layer FinalDocument8 pagesL7 CN Network Layer FinalJeff jayNo ratings yet
- Network Performance and Transmission ImpairmentsDocument3 pagesNetwork Performance and Transmission ImpairmentsLife SayingsNo ratings yet
- Main Paper PDFDocument5 pagesMain Paper PDFSiva Prasad GottumukkalaNo ratings yet
- Part 5: Transport Protocols For Wireless Mobile Networks: Sequence NumbersDocument6 pagesPart 5: Transport Protocols For Wireless Mobile Networks: Sequence NumbersKani MozhiNo ratings yet
- EHDFchapter 4Document14 pagesEHDFchapter 4Ahmad Raza AnsariNo ratings yet
- Ipt NotesDocument4 pagesIpt NotesDavid PhanNo ratings yet
- Brisco MP 06Document53 pagesBrisco MP 06Amir AbasNo ratings yet
- Project Report: Object Tracking in Wireless Sensor NetworksDocument12 pagesProject Report: Object Tracking in Wireless Sensor Networkspratyush0501No ratings yet
- TCP-IP & Static RoutingDocument6 pagesTCP-IP & Static Routingabhineet sharmaNo ratings yet
- Practical Attacks Against The I2p NetworkDocument20 pagesPractical Attacks Against The I2p NetworknewjerseycoupleNo ratings yet
- Scanning and Analysis Tools - Packets SniffersDocument22 pagesScanning and Analysis Tools - Packets Sniffersaurox3d100% (1)
- Transport Layer ServicesDocument7 pagesTransport Layer ServicesashkingNo ratings yet
- Unit 3Document7 pagesUnit 3SY ECE51 SHEJUL YUVRAJNo ratings yet
- WSN Module 2.2Document34 pagesWSN Module 2.2Aditya RoyNo ratings yet
- Routing SimulatorDocument69 pagesRouting SimulatorQuestionPapersTube67% (3)
- Communication and Networking - TERMSDocument7 pagesCommunication and Networking - TERMSjnoasj didsniafdsNo ratings yet
- Finding A Connection Chain For Tracing IntrudersDocument15 pagesFinding A Connection Chain For Tracing IntrudersAndre CtNo ratings yet
- Throughput Analysis of TCP Newreno For Multiple BottlenecksDocument10 pagesThroughput Analysis of TCP Newreno For Multiple BottlenecksTJPRC PublicationsNo ratings yet
- Introduction Into Mobile Core Network: Webex Sunday Session 24 March 2013Document35 pagesIntroduction Into Mobile Core Network: Webex Sunday Session 24 March 2013Abdul RehmanNo ratings yet
- Signal Processing For Sensor NetworkDocument18 pagesSignal Processing For Sensor NetworkkumarNo ratings yet
- Messages Packets Packet Router Link-Layer SwitchesDocument2 pagesMessages Packets Packet Router Link-Layer SwitchesMony JosephNo ratings yet
- Last Minute Notes - Computer Networks - GeeksforGeeksDocument14 pagesLast Minute Notes - Computer Networks - GeeksforGeekstejas zambareNo ratings yet
- DCN Unit-3saqDocument6 pagesDCN Unit-3saqsravan kumarNo ratings yet
- Networking Chapter 10 LabsDocument6 pagesNetworking Chapter 10 LabsJeff BrownNo ratings yet
- TCP ACC Another Congestion Control Algorithm BIC Simulation and Analysis Using The NS3Document10 pagesTCP ACC Another Congestion Control Algorithm BIC Simulation and Analysis Using The NS3GirishPaliwalNo ratings yet
- Transport Layer STDDocument8 pagesTransport Layer STDMd Habibur RahmanNo ratings yet
- Fundamentals To NetworkDocument14 pagesFundamentals To NetworkDinesh MathewNo ratings yet
- DCN QuestionsDocument8 pagesDCN QuestionsAnuj GargNo ratings yet
- CN 1Document7 pagesCN 1T024KOUSTAV CHATTERJEENo ratings yet
- AnetDocument8 pagesAnetErkihun MuluNo ratings yet
- InternetDocument5 pagesInternethueychopper.briosoNo ratings yet
- Mobile Wireless Enhanced Routing Protocol in Adhoc Networks: A.SreelathaDocument4 pagesMobile Wireless Enhanced Routing Protocol in Adhoc Networks: A.SreelathaJacob GollamudiNo ratings yet
- Refund Policy One PagerDocument1 pageRefund Policy One PagerRaman TrivediNo ratings yet
- JEE2023012320Document1 pageJEE2023012320Raman TrivediNo ratings yet
- Reviseio CSystemeeDocument25 pagesReviseio CSystemeeRaman TrivediNo ratings yet
- Channel Impairments: Muhammad Uzair Rasheed 2009-CPE-03 Uce&T Bzu MultanDocument25 pagesChannel Impairments: Muhammad Uzair Rasheed 2009-CPE-03 Uce&T Bzu MultanRaman TrivediNo ratings yet
- Data and Signals: M. Mozammel Hoque Chowdhury, Dept. of CSE, JUDocument38 pagesData and Signals: M. Mozammel Hoque Chowdhury, Dept. of CSE, JURaman TrivediNo ratings yet
- MyLinkBudget SheetDocument2 pagesMyLinkBudget SheetRaman TrivediNo ratings yet