Professional Documents
Culture Documents
PHP Magic Tricks: Type Juggling
Uploaded by
MAKAKIOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
PHP Magic Tricks: Type Juggling
Uploaded by
MAKAKICopyright:
Available Formats
PHP Magic Tricks: Type Juggling
PHP Magic Tricks: Type Juggling
Who Am I
Chris Smith (@chrismsnz)
Previously:
▪ Polyglot Developer - Python, PHP, Go + more
▪ Linux Sysadmin
Currently:
▪ Pentester, Consultant at Insomnia Security
▪ Little bit of research
OWASP Day 2015 PHP Magic Tricks: Type Juggling
Insomnia Security Group Limited
Founded in 2007 by Brett Moore.
New Zealand-based company.
Offices in Auckland and Wellington, as well as global partners.
Brings together a team of like-minded, highly technically skilled, results-driven, security professionals.
CREST Certified Testers.
Regularly perform work for customers in such differing industries as:
▪ Tele- and Mobile Communications;
▪ Banking, Finance, and Card Payment;
▪ E-Commerce and Online Retail;
▪ Software and Hardware Vendors;
▪ Broadcasting and Media; and
▪ Local and National Government.
OWASP Day 2015 PHP Magic Tricks: Type Juggling
Conventions
Types:
▪ "string" for strings
▪ int(0), float(0) for numbers
▪ TRUE, FALSE for booleans
Terms:
▪ "Zero-like" - an expression that PHP will loosely compare to
int(0)
OWASP Day 2015 PHP Magic Tricks: Type Juggling
What is Type Juggling?
Present in other languages, but in PHP, specifically:
▪ Has two main comparison modes, lets call them loose (==)
and strict (===).
▪ Loose comparisons have a set of operand conversion rules to
make it easier for developers.
▪ Some of these are a bit weird.
OWASP Day 2015 PHP Magic Tricks: Type Juggling
PHP Comparisons: Strict
OWASP Day 2015 PHP Magic Tricks: Type Juggling
PHP Comparisons: Loose
OWASP Day 2015 PHP Magic Tricks: Type Juggling
PHP Comparisons: Loose
When comparing a string to a number, PHP will attempt to
convert the string to a number then perform a numeric
comparison
▪ TRUE: "0000" == int(0)
▪ TRUE: "0e12" == int(0)
▪ TRUE: "1abc" == int(1)
▪ TRUE: "0abc" == int(0)
▪ TRUE: "abc" == int(0) // !!
OWASP Day 2015 PHP Magic Tricks: Type Juggling
PHP Comparisons: Loose
It gets weirder... If PHP decides that both operands look like
numbers, even if they are actually strings, it will convert them
both and perform a numeric comparison:
▪ TRUE: "0e12345" == "0e54321"
▪ TRUE: "0e12345" <= "1"
▪ TRUE: "0e12345" == "0"
▪ TRUE: "0xF" == "15"
Less impact, but still important.
OWASP Day 2015 PHP Magic Tricks: Type Juggling
PHP Type Juggling Bugs
Very common, as == is the default comparison in other
languages
Difficult to actually exploit, due to usually not being able to input
typed data via HTTP, only strings
Usually manifest as bugs in hardening or protections, allowing
you to exploit other bugs that would otherwise be mitigated
OWASP Day 2015 PHP Magic Tricks: Type Juggling
Bug #1 - Laravel CSRF Protection Bypass
I discovered this bug November 2014
Was looking around at different places Type Juggling bugs could
affect application security.
Bug was very easy to find - first place I looked
A bit harder to exploit
OWASP Day 2015 PHP Magic Tricks: Type Juggling
Bug #1: The Bug
if (Session::token() != Input::get('_token'))
{
throw new Illuminate\Session\TokenMismatchException;
}
Session::token() is the CSRF token retrieved from the session
Input::get('_token') is a facade that corresponds to HTTP
request input ... sometimes
OWASP Day 2015 PHP Magic Tricks: Type Juggling
Bug #1: The Trick
▪ CSRF token is a "RaNdOmStRiNg123"
▪ What type of juggling can take place here?
▪ What if: If the CSRF token starts with a letter, or the number 0
(~85% chance)?
▪ Comparing it with an integer means that PHP will juggle the
CSRF token to int(0)
OWASP Day 2015 PHP Magic Tricks: Type Juggling
Bug #1: The Exploit
Cool story, but how can we make Input::get('_token') return
int(0)?
HTTP Parameters are always strings, never other types
JSON?
Yep. Laravel feeds any request with '/json' in the Content-Type
header through a JSON parser and shoves the result into the
Input facade
OWASP Day 2015 PHP Magic Tricks: Type Juggling
Bug #1: The Exploit
$.ajax("http://<laravel app>/sensitiveaction", {
type: 'post',
contentType: 'application/x-www-form-urlencoded; charset=UTF-8; /json',
data: '{"sensitiveparam": "sensitive", "_token": 0}',
});
The content type doesn't trigger CORS restrictions (Firefox 34, Chrome
39) but does trigger Laravel JSON parsing
_token parameter passes the CSRF check, most of the time
OWASP Day 2015 PHP Magic Tricks: Type Juggling
Bug #1: The Aftermath
▪ Untested, but using TRUE as token value should pass 100%
▪ Reported to Laravel, promptly fixed
▪ However, the bug did not exist in the framework (which could
be patched by composer in a Laravel point release)
▪ Rather, it was in project template code used to bootstrap new
projects - everyone who used the default CSRF protection had
to manually apply the patch to their project!
▪ JSON bug/weakness still stands (Laravel 4)
OWASP Day 2015 PHP Magic Tricks: Type Juggling
Bug #2: Laravel Cryptographic MAC Bypass
Laravel again!
Discovered and published by MWR Information Security, June
2013
Bug was in cryptographic library used throughout the framework
The library powered Laravel's authentication system and exposed
for use by any Laravel applications
OWASP Day 2015 PHP Magic Tricks: Type Juggling
Bug #2: The Bug
A Laravel "encryption payload" looks like this:
{
"iv": "137f87545d8d2f994c65a6f336507747",
"value": "c30fbe54e025b2a509db7a1fc174783c35d023199f9a0e24ae23a934277aec66"
"mac": "68f6611d14aa021a80c3fc09c638de6de12910486c0c82703315b5d83b8229bb",
}
The MAC check code looked like this:
$payload = json_decode(base64_decode($payload), true);
if ($payload['mac'] != hash_hmac('sha256', $payload['value'], $this->key))
throw new DecryptException("MAC for payload is invalid.");
OWASP Day 2015 PHP Magic Tricks: Type Juggling
Bug #2: The Trick
The calculated MAC (i.e. the result of hash_hmac()) is a string
containing hexadecimal characters
The use of a loose comparison means that if an integer was
provided in the JSON payload, the HMAC string will be juggled to
a number
▪ "7a5c2...72c933" == int(7)
▪ "68f66...8229bb" == int(68)
▪ "092d1...c410a9" == int(92)
OWASP Day 2015 PHP Magic Tricks: Type Juggling
Bug #2: The Exploit
If the calculated MAC is "68f66...8229bb" then the following
payload will pass the MAC check:
{
"iv": "137f87545d8d2f994c65a6f336507747",
"value": "c30fbe54e025b2a509db7a1fc174783c35d023199f9a0e24ae23a934277aec66"
"mac": 68,
}
Now you can alter the ciphertext, "value", to whatever you
please, then repeat the request until a matching MAC input is
found
OWASP Day 2015 PHP Magic Tricks: Type Juggling
Bug #2: The Aftermath
The MAC bug allows an attacker to submit arbitrary ciphertexts and
IV's which are processed by the server in CBC mode
Arbitrary ciphertexts + CBC + poor error handling = Padding Oracle!
With a Padding Oracle, you can:
▪ Decrypt any encrypted ciphertexts
▪ Forge valid ciphertexts for arbitrary plaintexts
Without knowing the underlying encryption key
OWASP Day 2015 PHP Magic Tricks: Type Juggling
Bug #2: The Aftermath
Laravel's encryption library powered its "Remember Me"
authentication functionality
s:4:"1337"; + <padding>
This juggling bug allowed exploitation of the crypto flaws, leading to:
▪ Impersonation of any application user via. Remember Me cookie
▪ Remote Code Execution by leveraging PHP serialisation bugs:
▪ Magic Method execution of existing classes
▪ Other bugs (including recent DateTime Use After Free RCE)
OWASP Day 2015 PHP Magic Tricks: Type Juggling
Bug #3: Wordpress Authentication Bypass
Publicised by MWR Information Security (again) November 2014
Fun and interesting attack, but limited practicality
Probably easier ways to own Wordpress
Following is a simplified explanation of the bug
OWASP Day 2015 PHP Magic Tricks: Type Juggling
Bug #3: The Bug
$hash = hash_hmac('md5', $username . '|' . $expiration, $key);
if ($hmac != $hash) {
// bad cookie
}
$username, $expiration and $hmac are provided by the user
in the cookie value
$key for all intents and purposes is secret
OWASP Day 2015 PHP Magic Tricks: Type Juggling
Bug #3: The Trick
The calculated hash, the result of hash_hmac(), looks like:
"596440eae1a63306035942fe604ed854"
The provided hash, given by the user in their cookie, may be any string
If we can make the calculated hash string Zero-like, and provide "0" in the
cookie, the check will pass
"0e768261251903820937390661668547" == "0"
OWASP Day 2015 PHP Magic Tricks: Type Juggling
Bug #3: The Exploit
You have control over 3 elements in the cookie:
▪ $username - username you are targetting, probably "admin"
▪ $hmac - the provided hash, "0"
▪ $expiration - a UNIX timestamp, must be in the future
hash_hmac(admin|1424869663) -> "e716865d1953e310498068ee39922f49"
hash_hmac(admin|1424869664) -> "8c9a492d316efb5e358ceefe3829bde4"
hash_hmac(admin|1424869665) -> "9f7cdbe744fc2dae1202431c7c66334b"
hash_hmac(admin|1424869666) -> "105c0abe89825a14c471d4f0c1cc20ab"
OWASP Day 2015 PHP Magic Tricks: Type Juggling
Bug #3: The Exploit
Increment the expiration timestamp enough times and you will
eventually get a Zero-like calculated HMAC:
hash_hmac(admin|1835970773) -> "0e174892301580325162390102935332"
Which makes the comparison:
"0e174892301580325162390102935332" == "0"
Enough times = 300,000,000 requests avg, ~30 days @ 100
req/s
OWASP Day 2015 PHP Magic Tricks: Type Juggling
Bug #3: The Aftermath
Can (eventually) impersonate any user of the Wordpress
installation
Code has since been updated:
▪ SHA1/256 instead of MD5, much harder to get a Zero-like
hash
▪ Updated to use hash_equals() instead of ==, constant time,
type safe
▪ Also now includes another unique token
OWASP Day 2015 PHP Magic Tricks: Type Juggling
Recap
PHP's Type Juggling magic trick, a developer convenience, has
unexpected behaviour that might bite you
Difficult to exploit, as HTTP Request parameters are usually
always strings, but even then you can cause PHP to juggle
Security-sensitive developers need to know how PHP acts in
these situations, unpredictability can be catastrophic
OWASP Day 2015 PHP Magic Tricks: Type Juggling
Recommendations
Use === as your default comparison. Only reach for == if you
really need it
If you need to convert types, perform explicit type conversions
using a cast
(int)"0e23812" === (int)"0e48394832"
Be very mindful of these issues when writing security-sensitive code
OWASP Day 2015 PHP Magic Tricks: Type Juggling
www.insomniasec.com
Chris Smith - @chrismsnz
For sales enquiries: sales@insomniasec.com
All other enquiries: enquiries@insomniasec.com
Auckland office: +64 (0)9 972 3432
Wellington office: +64 (0)4 974 6654
OWASP Day 2015 PHP Magic Tricks: Type Juggling
References
CSRF Vulnerability in Laravel 4
http://blog.laravel.com/csrf-vulnerability-in-laravel-4/
Laravel Cookie Forgery, Decryption and RCE
https://labs.mwrinfosecurity.com/blog/2014/04/11/laravel-cookie-forgery-decryption-and-rce/
Wordpress Auth Cookie Forgery
https://labs.mwrinfosecurity.com/blog/2014/04/11/wordpress-auth-cookie-forgery/
Writing Exploits for Exotic Bug Classes: PHP Type Juggling
https://www.alertlogic.com/blog/writing-exploits-for-exotic-bug-classes-php-type-juggling/
PHP Documentation: Type Juggling
http://php.net/manual/en/language.types.type-juggling.php
OWASP Day 2015 PHP Magic Tricks: Type Juggling
BONUS BUG
Lets take strcmp():
int strcmp(string $str1, string $str2)
▪ Returns -1 if $str1 < $str2
▪ Returns 0 if $str1 === $str2
▪ Returns +1 if $str1 > $str2
OWASP Day 2015 PHP Magic Tricks: Type Juggling
BONUS BUG
How would you use this function?
if (strcmp($_POST['password'], 'thePassword') == 0) {
// do authenticated things
}
You control $_POST['password'], can you do anything to disrupt
this check?
OWASP Day 2015 PHP Magic Tricks: Type Juggling
BONUS BUG
Instead of POSTING a password string:
password=notThePassword
Submit an array:
password[]=
PHP translates POST variables like this to an empty array which
causes strcmp() to barf:
strcmp(array(), "thePassword") -> NULL
OWASP Day 2015 PHP Magic Tricks: Type Juggling
BONUS BUG
Lets take a look at the strcmp usage again:
if (strcmp($_POST['password'], 'thePassword') == 0) {
// do authenticated things
}
Lucky for us, thanks to type juggling, NULL == 0. Auth bypass!
OWASP Day 2015 PHP Magic Tricks: Type Juggling
You might also like
- PHP LockitDocument6 pagesPHP LockitKim MingNo ratings yet
- The Essential Skills To Becoming A Master HackerDocument8 pagesThe Essential Skills To Becoming A Master HackershibbirNo ratings yet
- 100% Evasion - Write A Crypter in Any Language To Bypass AV PDFDocument13 pages100% Evasion - Write A Crypter in Any Language To Bypass AV PDFVo TinhNo ratings yet
- Hacking GuideDocument13 pagesHacking GuideJohn WhiteNo ratings yet
- PHP Programming For Beginners: The Simple Guide to Learning PHP Fast!From EverandPHP Programming For Beginners: The Simple Guide to Learning PHP Fast!No ratings yet
- Exact Basics of Hacking Intro: DescriptionDocument6 pagesExact Basics of Hacking Intro: DescriptionStreet_Hacker_01No ratings yet
- Home-Grown Crypto (Aka Taking A Shiv To A Gun Fight) : The Owasp FoundationDocument87 pagesHome-Grown Crypto (Aka Taking A Shiv To A Gun Fight) : The Owasp Foundationapi-27294532No ratings yet
- PHP Interview Questions and AnswersDocument4 pagesPHP Interview Questions and AnswershirenloveuNo ratings yet
- Rhino Mocks Tutorial Part 1Document5 pagesRhino Mocks Tutorial Part 1Dawah786No ratings yet
- Final Exam: Do Not Start Until The Correct TimeDocument8 pagesFinal Exam: Do Not Start Until The Correct TimeSaba HussienNo ratings yet
- Effectiveness of Antivirus in Detecting Web Application BackdoorsDocument8 pagesEffectiveness of Antivirus in Detecting Web Application BackdoorsMauricio de OzNo ratings yet
- Web Backdoors Evasion DetectionDocument9 pagesWeb Backdoors Evasion Detectionh1025090No ratings yet
- Lab HashDocument3 pagesLab HashWilliam MoralesNo ratings yet
- BlackHat Practical Padding Oracle AttacksDocument17 pagesBlackHat Practical Padding Oracle AttacksMal ObNo ratings yet
- Virus Inside MS WordDocument11 pagesVirus Inside MS WordpauloNo ratings yet
- JavaScript Leverage Its Strengths To Eliminate Its WeaknessesDocument35 pagesJavaScript Leverage Its Strengths To Eliminate Its WeaknessesPhil LaNasaNo ratings yet
- Offline Password Brute-ForcerDocument2 pagesOffline Password Brute-ForcerPeninah RukunguNo ratings yet
- Python Web Penetration Testing Cookbook - Sample ChapterDocument36 pagesPython Web Penetration Testing Cookbook - Sample ChapterPackt PublishingNo ratings yet
- Aula 6Document26 pagesAula 6littlehandsNo ratings yet
- API2 2019 Broken User AuthenticationDocument5 pagesAPI2 2019 Broken User AuthenticationShamsher KhanNo ratings yet
- JavaScript Interview Questions and Answers PDF - CodeProjectDocument8 pagesJavaScript Interview Questions and Answers PDF - CodeProjectJagdish TripathiNo ratings yet
- Topic 2Document32 pagesTopic 2Punam ChaudharyNo ratings yet
- Zero Day Garden Windows Exploit Development Part 4Document16 pagesZero Day Garden Windows Exploit Development Part 4Lincoln DiasNo ratings yet
- SQL Injection 4Document73 pagesSQL Injection 4Headster80% (5)
- Erepublik - Security Explained, Catching Bots and ScriptersDocument6 pagesErepublik - Security Explained, Catching Bots and Scriptersskydesign04No ratings yet
- Similar PHP Interview QuestionsDocument36 pagesSimilar PHP Interview QuestionsgijorajNo ratings yet
- Cryptopp FaqsDocument15 pagesCryptopp FaqstalalzxxNo ratings yet
- DEF CON 23 - Lance-Buttars-Nemus-Hacking-SQL-Injection-for-Remote-Code-Execution-on-a-LAMP-UPDATEDDocument96 pagesDEF CON 23 - Lance-Buttars-Nemus-Hacking-SQL-Injection-for-Remote-Code-Execution-on-a-LAMP-UPDATEDkashif majeed janjuaNo ratings yet
- Face Recognition With Python, in Under 25 Lines of CodeDocument8 pagesFace Recognition With Python, in Under 25 Lines of CodejlbmdmNo ratings yet
- VB5 Cracking With SmartCheck 5.0Document5 pagesVB5 Cracking With SmartCheck 5.0Sanjay PatilNo ratings yet
- Glynrob: Hashing and Public Key EncryptionDocument10 pagesGlynrob: Hashing and Public Key EncryptionIoio92No ratings yet
- Building My Own Siri - JarvisDocument26 pagesBuilding My Own Siri - Jarvisbugeac89No ratings yet
- Sozdanie Finansovyh Prilozheniy S Ispolzovaniem Laravel - 1Document91 pagesSozdanie Finansovyh Prilozheniy S Ispolzovaniem Laravel - 1agris.markusNo ratings yet
- Presentation 5587 1540244493Document41 pagesPresentation 5587 1540244493Bayo HarahapNo ratings yet
- PHP Interview Questions and AnswersDocument55 pagesPHP Interview Questions and AnswersVidyakumar LivingforoldpeopleNo ratings yet
- Search: PHP: Booleanos - ManualDocument15 pagesSearch: PHP: Booleanos - ManualperexwiNo ratings yet
- 1-4 What Went Wrong - Troubleshooting JavaScript - Learn Web Development - MDNDocument12 pages1-4 What Went Wrong - Troubleshooting JavaScript - Learn Web Development - MDNPedro Leite (Mindset Épico)No ratings yet
- Encryption - Client Server Encryption Plus Extras - C# ProgrammingDocument12 pagesEncryption - Client Server Encryption Plus Extras - C# ProgrammingDragosNo ratings yet
- La RavelDocument15 pagesLa RavelGarima WaliaNo ratings yet
- Asia 18 Tal Liberman Documenting The Undocumented The Rise and Fall of AMSIDocument71 pagesAsia 18 Tal Liberman Documenting The Undocumented The Rise and Fall of AMSItrupzup7No ratings yet
- 1-3 A First Splash Into JavaScript - Learn Web Development - MDNDocument16 pages1-3 A First Splash Into JavaScript - Learn Web Development - MDNPedro Leite (Mindset Épico)No ratings yet
- PHP Interview Questions and AnswersDocument39 pagesPHP Interview Questions and AnswersDolphin RajeshNo ratings yet
- (Unique Random String Generator PHP) : Download For FreeDocument2 pages(Unique Random String Generator PHP) : Download For FreeNikola NejedlýNo ratings yet
- Hakin9 OPEN 04 2013Document40 pagesHakin9 OPEN 04 2013Francisco OrtizNo ratings yet
- Bug Bytes #71 - 20K Facebook XSS, LevelUp 0x06 & Naffy's NotesDocument16 pagesBug Bytes #71 - 20K Facebook XSS, LevelUp 0x06 & Naffy's NotesSaedohNo ratings yet
- Week 03Document29 pagesWeek 03api-247491493No ratings yet
- Controlling Your Robot With Python: 1 Preparing The EnvironmentDocument6 pagesControlling Your Robot With Python: 1 Preparing The Environmentdarfyma putraNo ratings yet
- PHP Interview Questions and Answers: × CCCC CCCCCCCCCCCCCCCDocument5 pagesPHP Interview Questions and Answers: × CCCC CCCCCCCCCCCCCCCUmesh BagalurNo ratings yet
- Unit Iv Javascript - Web Technology (I Semester)Document24 pagesUnit Iv Javascript - Web Technology (I Semester)Vish PNo ratings yet
- From Sqli To Shell IIDocument37 pagesFrom Sqli To Shell IIdanielfiguero5293No ratings yet
- EPCCPDocument17 pagesEPCCPfroanaNo ratings yet
- JavaScript Interview Questions and Answers - 70 JavaScript Interview Questions - DEV CommunityDocument78 pagesJavaScript Interview Questions and Answers - 70 JavaScript Interview Questions - DEV CommunityRahul YadavNo ratings yet
- Pythonforhackers SampleDocument14 pagesPythonforhackers Sampletariq786No ratings yet
- 1st DayDocument47 pages1st DayZIHANGIRRRNo ratings yet
- 06 JavascriptDocument82 pages06 JavascriptGerry CalàNo ratings yet
- Short Answer Questions: 1. Write The Structure of PHP Script With An ExampleDocument26 pagesShort Answer Questions: 1. Write The Structure of PHP Script With An ExampleMeeraj MedipalliNo ratings yet
- Intro To JavaScript Web DesignnzDocument13 pagesIntro To JavaScript Web Designnzsoulexiled5No ratings yet
- Coding For Kids: JavaScript Adventures with 50 Hands-on ActivitiesFrom EverandCoding For Kids: JavaScript Adventures with 50 Hands-on ActivitiesNo ratings yet
- CF SyllabusDocument1 pageCF SyllabusSindhuja ManoharNo ratings yet
- Tic Tac ToeDocument22 pagesTic Tac ToeLipikaNo ratings yet
- Unit 1Document40 pagesUnit 1Prabesh KarkiNo ratings yet
- HTTP Tutorial Math Lamar Edu Classes Alg PolynomialFunctions AspxDocument1 pageHTTP Tutorial Math Lamar Edu Classes Alg PolynomialFunctions AspxAkash TutiNo ratings yet
- BackupDocument9 pagesBackupJusdy JoeNo ratings yet
- r05310505 Principles of Programming LangaugesDocument5 pagesr05310505 Principles of Programming LangaugesSRINIVASA RAO GANTANo ratings yet
- What Is A Pipe in Linux?Document4 pagesWhat Is A Pipe in Linux?C.RadhiyaDeviNo ratings yet
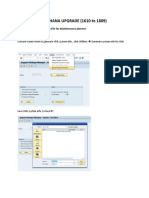
- S/4 HANA UogradeDocument26 pagesS/4 HANA UogradeRanga nani100% (1)
- Salesforce Certified Platform Developer 1: Lesson 11: Exception HandlingDocument43 pagesSalesforce Certified Platform Developer 1: Lesson 11: Exception HandlinganantvirNo ratings yet
- Recovery Scenarios in Data Guard Environment PDFDocument68 pagesRecovery Scenarios in Data Guard Environment PDFG.R.THIYAGU ; Oracle DBA100% (20)
- MITS4002 Activity 09 PDFDocument5 pagesMITS4002 Activity 09 PDFUdhdhav KheniNo ratings yet
- HTML (Hyper Text Markup Language)Document53 pagesHTML (Hyper Text Markup Language)Deepak Patel100% (1)
- 11g Duplicate Active Database - GavinsoormaDocument11 pages11g Duplicate Active Database - GavinsoormaKumar GummulaNo ratings yet
- ResumeDocument4 pagesResumeAnonymous pYK8tqNo ratings yet
- Two-Stage Generative Adversarial Networks For Docu PDFDocument30 pagesTwo-Stage Generative Adversarial Networks For Docu PDFbroNo ratings yet
- Welcome To The Help Pages of Winbuilder!Document8 pagesWelcome To The Help Pages of Winbuilder!freeware81No ratings yet
- How To Register and Subscribe A System To The Red Hat Customer Portal Using Red Hat Subscription-Manager - Red Hat Customer PortalDocument9 pagesHow To Register and Subscribe A System To The Red Hat Customer Portal Using Red Hat Subscription-Manager - Red Hat Customer PortalSunil CruseNo ratings yet
- Diferença Entre Switch Layer 2 e 3Document3 pagesDiferença Entre Switch Layer 2 e 3pablopaesNo ratings yet
- OOSE Week 07-UML Sequence DiagramDocument20 pagesOOSE Week 07-UML Sequence DiagramInnoxentDollNo ratings yet
- Surveying 2 Fieldwork 2Document5 pagesSurveying 2 Fieldwork 2api-200069730% (2)
- Value Engineering POMDocument16 pagesValue Engineering POMnabendu4u100% (1)
- An Introduction To Combinatorics and Graph Theory: David GuichardDocument155 pagesAn Introduction To Combinatorics and Graph Theory: David Guichardc1336787100% (1)
- Semester-1 /2: Chitkara School of Engineering and TechnologyDocument4 pagesSemester-1 /2: Chitkara School of Engineering and TechnologytsetanNo ratings yet
- Multiple Choice Questions: System Analysis &designDocument51 pagesMultiple Choice Questions: System Analysis &designtwinkle_shahNo ratings yet
- Decision MakingDocument9 pagesDecision MakingTalhaFarrukhNo ratings yet
- Epl2 PM en PDFDocument876 pagesEpl2 PM en PDFValmir VettoreNo ratings yet
- Programming Fundamentals Chapter 1 INTRODocument31 pagesProgramming Fundamentals Chapter 1 INTROMichael T. BelloNo ratings yet
- trpl1 PDFDocument411 pagestrpl1 PDFWalker TalkerNo ratings yet
- KRONOS Update and RestoreDocument4 pagesKRONOS Update and RestorePaul John100% (1)