Professional Documents
Culture Documents
Threat Actors Steal Data
Uploaded by
obiwan xeonOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Threat Actors Steal Data
Uploaded by
obiwan xeonCopyright:
Available Formats
TrendLabs
When attackers have
reached this stage, it
is not a big issue for Advanced persistent threats (APTs) refer to a category of high-risk
them to transfer threats that pertain to computer intrusions by threat actors that
data out. aggressively pursue and compromise chosen target institutions or
enterprises. Data exfiltration is the main goal of advanced persistent
– Spencer Hsieh
threats (APTs).
Trend Micro threat
researcher APTs strive to remain undetected in the network in order to gain
access to the company’s crown jewels or valuable data. These
valuable data include intellectual property, trade secrets, and
customer information. In addition, threat actors may also seek other
sensitive data such as top-secret documents from government or
military institutions.
APTs typically use social engineering techniques by crafting email
content that would be contextually relevant in order to deliver
exploits. These exploits are later on used to download more
malware.
Once threat actors penetrate the network and establish persistent
control, they can easily transfer the gathered company data. At this
stage, it becomes an arduous task for system administrators to detect
any malicious activity in the network.
In the asset/data discovery stage, threat actors have access to
“territories” that contain valuable information and noteworthy
assets. These data are then identified and transferred through tools
like remote access Trojans (RATs), and customized and legitimate
tools.
Threat actors identify their target information using various data
monitoring and collecting tools before the actual data exfiltration.
Once attackers acquire the stolen information, the impact to any
organization or institution may include sabotage, data theft, and
damage to brand image and reputation.
2 | TrendLabs Security in Context Paper
Attackers use a mix of legitimate and malicious tools and
techniques in order to extract specific data from the target’s
perimeter. Here are some tools and techniques we have seen
used in actual APT campaigns.
• Backdoors have built-in upload and download
functions and are commonly installed in target systems.
This is a capability also observed in RATs.
Backdoors can upload collected files and use ports like
80 and 443 (for HTTP or HTTPS) and port 53 (for
DNS) to hide their traffic. These attackers can bypass
the connection restriction whenever they use HTTP to
transmit data and to bypass detection. Based on our
investigation, there are instances when attackers
manually download the .ZIP file containing all
collected data.
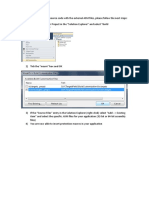
Figure 1. Screenshot of a backdoor traffic in data exfiltration
• File transfer protocol (FTP) is a standard network
protocol used to transfer files may also be used to
conduct data exfiltration.
• Web applications: Attackers open their own browsers
and can directly access information. IT administrators
won’t suspect any malicious activity since connecting
3 | TrendLabs Security in Context Paper
to web pages outside the network isn’t out of the
ordinary.
• Windows Management Instrumentation (WMI)
may be used to check the files opened by the targeted
employees or users. As such, cybercriminals can easily
determine and gather these files for transferring data.
• The forwarding rule in Microsoft® Outlook®
enables attackers to receive copies of the emails that
their target users receive.
• Attackers may use legitimate tools for gathering a list
of file types and documents files. They may also put a
timestamp to prevent duplicating the transferred data.
• Peripheral devices such as microphones and webcams
may be used to record audio and video in order to
monitor the targeted users’ activities.
Attackers need to leverage the abovementioned legitimate tools and
activities in order to hide their tracks and remain undetected in the
targeted network. They also make use of built-in or HTTP file
transfers. In addition, the Tor anonymity network masks one’s location
and traffic.
Figure 2. Stages of an APT
4 | TrendLabs Security in Context Paper
Attributing attacks is
often very difficult to
As threat actors move deeper into a target’s network, it is difficult
do. Accurately
for IT administrators to detect and mitigate APTs. Early detection
ascertaining who
attacked your device is then is crucial in order to prevent attackers from exfiltrating or
a daunting task and transmitting data.
will only provide you a
small subset of
Once the IT administrator suspects any malicious activity in the
possible motivations. network, he/she should assume compromise and trigger an
Determining investigation. This is why it is essential for enterprises to develop
motivations is also threat intelligence to help determine any indicators of activities that
very difficult to do, as may be related to APTs.
attackers would nearly
never reveal their real Since email is the most common form of office communication,
intentions. securing email remains a trusted solution against attackers who use it
as an entry point. However, enterprises should ensure that their
Kyle Wilhoit
– Trend Micro senior
email security solutions are complemented by a robust security
threat researcher technology with real-time local and global intelligence. This can
support the threat intelligence efforts of enterprises via its network-
wide security event collection and analysis enabling IT administrators
to carry remediation and containment plans.
It is also recommended that enterprises employ the Trend Micro™
Custom Defense Solution, an advanced threat protection platform
that performs network-wide monitoring to detect zero-day malware,
malicious communications, and attacker behavior that remains
unseen to traditional security solutions. This security platform has
sandbox simulation that enables enterprises to block spearphishing
emails and exploits used by attackers during the early stages of an
APT. As such, a Custom Defense strategy can prevent APTs from
entering the network, moving laterally to ‘territories’ that house
crucial company data, and subsequently, transferring these
information to threat actors.
5 | TrendLabs Security in Context Paper
TREND MICRO LEGAL DISCLAIMER
The information provided herein is for general information and educational purposes only. It is not intended and should not be construed to constitute legal
advice. The information contained herein may not be applicable to all situations and may not reflect the most current situation. Nothing contained herein
should be relied on or acted upon without the benefit of legal advice based on the particular facts and circumstances presented and nothing herein should be
construed otherwise. Trend Micro reserves the right to modify the contents of this document at any time without prior notice.
Translations of any material into other languages are intended solely as a convenience. Translation accuracy is not guaranteed nor implied. If any questions
arise related to the accuracy of a translation, please refer to the original language official version of the document. Any discrepancies or differences created
in the translation are not binding and have no legal effect for compliance or enforcement purposes.
Although Trend Micro uses reasonable efforts to include accurate and up-to-date information herein, Trend Micro makes no warranties or representations of
any kind as to its accuracy, currency, or completeness. You agree that access to and use of and reliance on this document and the content thereof is at your
own risk. Trend Micro disclaims all warranties of any kind, express or implied. Neither Trend Micro nor any party involved in creating, producing, or delivering
this document shall be liable for any consequence, loss, or damage, including direct, indirect, special, consequential, loss of business profits, or special
damages, whatsoever arising out of access to, use of, or inability to use, or in connection with the use of this document, or any errors or omissions in the
content thereof. Use of this information constitutes acceptance for use in an “as is” condition.
Trend Micro Incorporated, a global leader in security software, strives to
make the world safe for exchanging digital information. Our innovative
security solutions for consumers, businesses and governments protect
information on mobile devices, endpoints, gateways, servers and the cloud.
For more information, visit www.trendmicro.com
©2013 by Trend Micro, Incorporated. All rights reserved. Trend Micro and
the Trend Micro t-ball logo are trademarks or registered trademarks of Trend
Micro, Incorporated. All other product or company names may be trademarks
or registered trademarks of their owners.
You might also like
- DDOS Attacks Tutorial Part 2: Brought To You byDocument23 pagesDDOS Attacks Tutorial Part 2: Brought To You byobiwan xeonNo ratings yet
- Smart BugDocument1 pageSmart Bugobiwan xeonNo ratings yet
- Sheet1: From Futurlec: Price Units SumDocument2 pagesSheet1: From Futurlec: Price Units Sumobiwan xeonNo ratings yet
- How To Add ASM Files in Your SolutionDocument1 pageHow To Add ASM Files in Your Solutionobiwan xeonNo ratings yet
- ATM Hacking (Old Trick) PDFDocument42 pagesATM Hacking (Old Trick) PDFobiwan xeon50% (2)
- College of Tourism and Hospitality ManangementDocument2 pagesCollege of Tourism and Hospitality Manangementobiwan xeonNo ratings yet
- Plot Flags MappingDocument10 pagesPlot Flags MappingDavid MendozaNo ratings yet
- Alphabet of LinesDocument19 pagesAlphabet of Linesobiwan xeonNo ratings yet
- JAVASCRIPTDocument25 pagesJAVASCRIPTobiwan xeonNo ratings yet
- List of All Government & Private Construction Contracts Completed Which Are Similar in NatureDocument4 pagesList of All Government & Private Construction Contracts Completed Which Are Similar in Natureobiwan xeonNo ratings yet
- Alphabet of Lines2Document26 pagesAlphabet of Lines2Micah Dianne DizonNo ratings yet
- Song ChordsDocument9 pagesSong Chordsobiwan xeonNo ratings yet
- AssignmentDocument5 pagesAssignmentobiwan xeonNo ratings yet
- Name: Alres C. Arena Prenciss Ann P. Juni 1) Website: Index - PHPDocument5 pagesName: Alres C. Arena Prenciss Ann P. Juni 1) Website: Index - PHPobiwan xeonNo ratings yet
- Blind Kiss All SummariesDocument39 pagesBlind Kiss All Summariesobiwan xeonNo ratings yet
- Reverse DataDocument1 pageReverse Dataobiwan xeonNo ratings yet
- ValuesDocument1 pageValuesobiwan xeonNo ratings yet
- DB 2Document53 pagesDB 2obiwan xeonNo ratings yet
- Song ChordsDocument9 pagesSong Chordsobiwan xeonNo ratings yet
- A QUEUE Is Logically A First in First Out (FIFO or First Come First Serve) Linear Data StructureDocument4 pagesA QUEUE Is Logically A First in First Out (FIFO or First Come First Serve) Linear Data Structureobiwan xeonNo ratings yet
- Humanities BudionganDocument93 pagesHumanities Budionganobiwan xeonNo ratings yet
- JavascriptDocument26 pagesJavascriptobiwan xeonNo ratings yet
- File Systems and DatabasesDocument54 pagesFile Systems and Databasesobiwan xeonNo ratings yet
- Xmas MessageDocument2 pagesXmas Messageobiwan xeonNo ratings yet
- Processess: Alres C. Arena Bsit Ii-IDocument1 pageProcessess: Alres C. Arena Bsit Ii-Iobiwan xeonNo ratings yet
- Synaptics - v17 - 0 - 19 ReleaseDocument1 pageSynaptics - v17 - 0 - 19 ReleaseAndre Bahtiar FauziNo ratings yet
- Hook TestDocument2 pagesHook Testobiwan xeonNo ratings yet
- Categories of Digital Graphic1Document6 pagesCategories of Digital Graphic1obiwan xeonNo ratings yet
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (895)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5794)
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (399)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (266)
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (537)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (838)
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (588)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2259)
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (73)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (344)
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1090)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (121)
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (821)
- ISO IEC 27032 2023 (En)Document36 pagesISO IEC 27032 2023 (En)Sonia zghal Kallel100% (2)
- Marketing PortfolioDocument19 pagesMarketing PortfolioAli RazaNo ratings yet
- Website Nwebsite Url Informatio Alexa Rank DR TLDDocument56 pagesWebsite Nwebsite Url Informatio Alexa Rank DR TLDkathlyn channelNo ratings yet
- Rizal Report TemplateDocument28 pagesRizal Report TemplateAngelo SumaoyNo ratings yet
- Developer Report: Acunetix Website Audit 23 December, 2021Document7 pagesDeveloper Report: Acunetix Website Audit 23 December, 2021BAGAS TRI RAMADANA -No ratings yet
- Iftekher AzizDocument2 pagesIftekher AzizIftekher AzizNo ratings yet
- Seo & Wordpress: Testing (Manual and Automation)Document15 pagesSeo & Wordpress: Testing (Manual and Automation)deepika adhikariNo ratings yet
- Upfile - 0 Tybsclab Semii cs349 5b75428743344Document35 pagesUpfile - 0 Tybsclab Semii cs349 5b75428743344akash pandeyNo ratings yet
- A Start in MarathiDocument95 pagesA Start in MarathiBharat AnandNo ratings yet
- Payroll Tutorial 2Document20 pagesPayroll Tutorial 2ryanrburton09No ratings yet
- 2022 - EN - Quick Start Guide For POE Cameras - V2.0Document24 pages2022 - EN - Quick Start Guide For POE Cameras - V2.0Jai Sri HariNo ratings yet
- User ManagementDocument7 pagesUser ManagementSuneth RanathungaNo ratings yet
- Developing and Deploying Siebel CRMDocument68 pagesDeveloping and Deploying Siebel CRMMake India growNo ratings yet
- Protect 8.31communicationsDocument24 pagesProtect 8.31communicationsibs434No ratings yet
- Technology Crossword PuzzleDocument1 pageTechnology Crossword PuzzleAryan AroraNo ratings yet
- Indian Telecom Security Assurance Requirements (ITSAR) : 5G Aggregated GNB NSA Option - 3, 7 & 4Document74 pagesIndian Telecom Security Assurance Requirements (ITSAR) : 5G Aggregated GNB NSA Option - 3, 7 & 4Vijju JatNo ratings yet
- Aditya Mahajan: Professional SummaryDocument2 pagesAditya Mahajan: Professional SummaryvishuchefNo ratings yet
- Soap ApiDocument441 pagesSoap ApiMohit GuptaNo ratings yet
- Quiz 1Document27 pagesQuiz 1Whipple AnchetaNo ratings yet
- PADL - Automated Paddle Sport RentalsDocument2 pagesPADL - Automated Paddle Sport RentalsPR.comNo ratings yet
- Assignment No 4Document18 pagesAssignment No 4Jusil T. GaiteNo ratings yet
- Wix Portfolio RubricDocument1 pageWix Portfolio Rubricapi-308067286No ratings yet
- VHD-V500N 3.0 User Manual3.1.8VDocument69 pagesVHD-V500N 3.0 User Manual3.1.8Vpinke01No ratings yet
- B8 Comp TsolDocument4 pagesB8 Comp TsolNana Yaw Poku JuniorNo ratings yet
- Krafton Pubg - LoliDocument8 pagesKrafton Pubg - Loliyoutube premNo ratings yet
- Actiance Datasheet SocialiteDocument2 pagesActiance Datasheet SocialiteAndri HerumurtiNo ratings yet
- Vaibhav KanadeDocument3 pagesVaibhav KanadeShweta ShirsatNo ratings yet
- Kris Radzanowski, Owner of EssentialZen, Attends Meta Event in Washington, D.C.Document3 pagesKris Radzanowski, Owner of EssentialZen, Attends Meta Event in Washington, D.C.PR.comNo ratings yet
- How To Spam Trustwallet Logs (Hackslord)Document5 pagesHow To Spam Trustwallet Logs (Hackslord)Kabano CoNo ratings yet
- Bridge InisghtDocument227 pagesBridge InisghtSchatten des TodesNo ratings yet