Professional Documents
Culture Documents
AFIC Android App
AFIC Android App
Uploaded by
Abdul Haseeb0 ratings0% found this document useful (0 votes)
12 views1 pageElastic Search, session management, and authorization controls are being implemented to prevent SQL injection, session hijacking, and cross-site request forgery, while secure cryptographic storage and validation of redirects and forwards are also being put in place. All security controls will be validated once the complete system is ready for security evaluation.
Original Description:
Original Title
AFIC Android app.docx
Copyright
© © All Rights Reserved
Available Formats
DOCX, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentElastic Search, session management, and authorization controls are being implemented to prevent SQL injection, session hijacking, and cross-site request forgery, while secure cryptographic storage and validation of redirects and forwards are also being put in place. All security controls will be validated once the complete system is ready for security evaluation.
Copyright:
© All Rights Reserved
Available Formats
Download as DOCX, PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
12 views1 pageAFIC Android App
AFIC Android App
Uploaded by
Abdul HaseebElastic Search, session management, and authorization controls are being implemented to prevent SQL injection, session hijacking, and cross-site request forgery, while secure cryptographic storage and validation of redirects and forwards are also being put in place. All security controls will be validated once the complete system is ready for security evaluation.
Copyright:
© All Rights Reserved
Available Formats
Download as DOCX, PDF, TXT or read online from Scribd
You are on page 1of 1
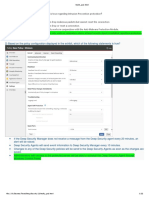
All security controls will be validated once complete system is ready for security
evaluation.
15. Elastic Search is being used to avoid SQL Injection.
17. Session mgmt. is required in order to avoid session hijacking/ Broken
authentication.
18 Objects are not allowed to be accessed without authorization.
19. Elastic Search is being used to avoid cross site request forgery.
20. Secure Cryptographic storage is implemented
22. Redirects are forwarding’s are validated properly
You might also like
- Deep Security 11 Certified Professional - Exam: Questions: 45 - Attempts: 3Document20 pagesDeep Security 11 Certified Professional - Exam: Questions: 45 - Attempts: 3machadotulio100% (2)
- Authorization, Authentication, and SecurityDocument25 pagesAuthorization, Authentication, and SecurityDaniel LaoNo ratings yet
- ISA Web Application SecurityDocument8 pagesISA Web Application Securitycazanova20No ratings yet
- Immigo Security: We Are ISO 27001 CertifiedDocument4 pagesImmigo Security: We Are ISO 27001 CertifiedperegrineimNo ratings yet
- Spring Security-DemoDocument7 pagesSpring Security-Demotbarua1No ratings yet
- Lecture 1Document28 pagesLecture 1Muhammad RehanNo ratings yet
- Unit 1 Introduction To Computer SecurityDocument54 pagesUnit 1 Introduction To Computer Securitybishal lamsalNo ratings yet
- In The The Bangladesh Bank Heist'' Explain How To Avoid Accident in Compromise Data.Document2 pagesIn The The Bangladesh Bank Heist'' Explain How To Avoid Accident in Compromise Data.Crystal Marie Jordan Aguhob100% (1)
- OpenMic ISAM API Protection 16aug2017Document24 pagesOpenMic ISAM API Protection 16aug2017gheodan100% (1)
- Privacy Security National ID by Drexx LaguiDocument20 pagesPrivacy Security National ID by Drexx LaguiLei CabilloNo ratings yet
- Blockchain and Cryptocurrency TechniquesDocument14 pagesBlockchain and Cryptocurrency TechniquesJuma SohnNo ratings yet
- SQL Injection On Adminlogin Page: Impact: IDocument3 pagesSQL Injection On Adminlogin Page: Impact: IbixowujyNo ratings yet
- Owasp Top 10Document9 pagesOwasp Top 10David OwnerNo ratings yet
- Chapter 14 Security Evasion TechniquesDocument20 pagesChapter 14 Security Evasion TechniquesAkshata ChawhanNo ratings yet
- Nist 800-171Document34 pagesNist 800-171listis116No ratings yet
- Certified Mitre Att - CK Training PDFDocument9 pagesCertified Mitre Att - CK Training PDFYnaiara AparecidaNo ratings yet
- Best Practices and Techniques For Building Secure ASPNET AppsDocument38 pagesBest Practices and Techniques For Building Secure ASPNET AppsRahul N ShripatiNo ratings yet
- Chapter 1 Computer SecurityDocument22 pagesChapter 1 Computer SecurityAjay GuptaNo ratings yet
- Introduction To SAP Security: Ramesh Gurram 2014.02.14Document32 pagesIntroduction To SAP Security: Ramesh Gurram 2014.02.14Khalid MohammedNo ratings yet
- CH01Document30 pagesCH01LeonNo ratings yet
- CyberDocument13 pagesCyberRashed JisanNo ratings yet
- Chapter 2 Secure Desing and PrincipleDocument21 pagesChapter 2 Secure Desing and PrinciplehaileNo ratings yet
- Pert-15 Ch15 Security (2023-0210) - ENDDocument126 pagesPert-15 Ch15 Security (2023-0210) - ENDMuhammad RafiNo ratings yet
- Osi Security Architecture Delivery by Joel Anandraj.E Ap/ItDocument27 pagesOsi Security Architecture Delivery by Joel Anandraj.E Ap/ItjoelanandrajNo ratings yet
- Sec ElementDocument3 pagesSec ElementgashawNo ratings yet
- Security Policy En-1Document4 pagesSecurity Policy En-1dream.mahafuzNo ratings yet
- FirstoneDocument2 pagesFirstoneKarthik Bharadwaj H DNo ratings yet
- Authentication, Authorisation, Accountability-FARDocument20 pagesAuthentication, Authorisation, Accountability-FARAnnisa Fajri HayatiNo ratings yet
- Deep Security 11 Certified Professional - Exam: ErroDocument19 pagesDeep Security 11 Certified Professional - Exam: ErromachadotulioNo ratings yet
- Security Mechanisms, Network Security Model Class-L3Document12 pagesSecurity Mechanisms, Network Security Model Class-L3Sidhant GuptaNo ratings yet
- Security MechanismsDocument24 pagesSecurity MechanismsIka Devi PerwitasariNo ratings yet
- SE-00005-2011-Technical Requirements For Securities Exchange MemberDocument5 pagesSE-00005-2011-Technical Requirements For Securities Exchange MemberReagen Lodeweijke MokodompitNo ratings yet
- Entersoft Introduction FinalDocument27 pagesEntersoft Introduction FinalHardik JadavNo ratings yet
- Unit 5Document53 pagesUnit 5AasmiNo ratings yet
- Getting Started in CybersecurityDocument28 pagesGetting Started in Cybersecurityyusuffabiola172No ratings yet
- FINT-002 BLCK AnnotatedDocument33 pagesFINT-002 BLCK AnnotatedSantosh SahooNo ratings yet
- Security TalkDocument41 pagesSecurity TalknkNo ratings yet
- Topic 9Document19 pagesTopic 9Sam BradshawNo ratings yet
- Unvalidated Redirects and Forwards:: Safe URL RedirectDocument5 pagesUnvalidated Redirects and Forwards:: Safe URL RedirectHusain Ali ArifNo ratings yet
- Soal Uts Semester Gasal Ta. 2020-2021 Tingkat 3 Rks Mata Kuliah: Keamanan Sistem OperasiDocument4 pagesSoal Uts Semester Gasal Ta. 2020-2021 Tingkat 3 Rks Mata Kuliah: Keamanan Sistem OperasiFadhil RadityaNo ratings yet
- Chapter 2 Secure Desing and PrincipleDocument24 pagesChapter 2 Secure Desing and PrinciplehaileNo ratings yet
- Computer SecurityDocument18 pagesComputer SecurityARYAN RATHORENo ratings yet
- OWASP Mobile Checklist Final 2016Document6 pagesOWASP Mobile Checklist Final 2016atul_raj4No ratings yet
- 1.intro To Ethical HackingDocument5 pages1.intro To Ethical HackingSachin SharmaNo ratings yet
- Puru - Secure Coding Best PracticesDocument66 pagesPuru - Secure Coding Best Practicesvindya.patankarNo ratings yet
- 11.200 Electronic Signature Components and ControlsDocument93 pages11.200 Electronic Signature Components and ControlsSLAOUTINo ratings yet
- It 352: Lecture 2-: Najwa Alghamdi, MSC - 2012 /1433Document18 pagesIt 352: Lecture 2-: Najwa Alghamdi, MSC - 2012 /1433Aziza Al-qahtaniNo ratings yet
- Module 1 Introduction To Cyber SecurityDocument11 pagesModule 1 Introduction To Cyber Securityyas999nNo ratings yet
- 1 Cybersecurity in The BlockchainDocument32 pages1 Cybersecurity in The Blockchaincom01156499073No ratings yet
- IntroDocument26 pagesIntroVarun Gupta0% (1)
- DBMS Unit-8Document28 pagesDBMS Unit-8Krish PatelNo ratings yet
- Security Mechanisms, Network Security Model Class-L3Document12 pagesSecurity Mechanisms, Network Security Model Class-L3Rahul Singh ChauhanNo ratings yet
- Examen Deep Security 2020 Utlima PDFDocument37 pagesExamen Deep Security 2020 Utlima PDFSaul ValenzuelaNo ratings yet
- Finalterm Assignment3 JarantillaDocument2 pagesFinalterm Assignment3 JarantillaLeague of RònNo ratings yet
- Cybersecurity Essentials 3.0-Module13Document56 pagesCybersecurity Essentials 3.0-Module13Kudzwai nyamuchengweNo ratings yet
- Important WebDocument39 pagesImportant Web002Aadika BhatiaIT1No ratings yet
- Client Side Session Handling For AngularDocument8 pagesClient Side Session Handling For AngularHelen ANo ratings yet
- Lecture23 Software Design and Architecture - SE 494Document10 pagesLecture23 Software Design and Architecture - SE 494Bsef19m012-IQRA SARWARNo ratings yet
- GROUP 5 EcommerceDocument15 pagesGROUP 5 Ecommerceokware brianNo ratings yet