Professional Documents
Culture Documents
The Path To Secure Iot & Iiot Devices: Device Tampering Detection
Uploaded by
mauriziolapucaOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
The Path To Secure Iot & Iiot Devices: Device Tampering Detection
Uploaded by
mauriziolapucaCopyright:
Available Formats
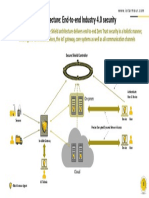
The Path to Secure IoT & IIoT Devices
SO
Intrusion Detection
Device & Security
Tampering Monitoring
Detection
Embedded
Security
Management
Secure IoT
Secure Boot & Regulatory
Secure Firmware Strong Compliance
Problems
Updates Authentication
Protection
against cyber
Gain Complete Secure attacks
Device Visibility Data Security Communication
Cyber Startup Observatory© - Insight
You might also like
- It Security: Nur Ain Atirah BT Hamidon B031810150 3bitsDocument1 pageIt Security: Nur Ain Atirah BT Hamidon B031810150 3bitsNur Ain AtirahNo ratings yet
- It Security: Nur Ain Atirah BT Hamidon B031810150 3bitsDocument1 pageIt Security: Nur Ain Atirah BT Hamidon B031810150 3bitsNur Ain AtirahNo ratings yet
- Anviz Product and Solution BrochureDocument16 pagesAnviz Product and Solution Brochureallanpaul.mrcircuitsNo ratings yet
- FortiGuard Security Services Simplified & SecureDocument9 pagesFortiGuard Security Services Simplified & SecureEdgar Rodriguez ContrerasNo ratings yet
- FortiOS 5.4.1 - How ToDocument39 pagesFortiOS 5.4.1 - How ToAnonymous YLI2wFNo ratings yet
- Cybersecurity Snapshot February 2022Document1 pageCybersecurity Snapshot February 2022Kiran KherNo ratings yet
- Cyber ScapeDocument1 pageCyber Scapemirza sharifNo ratings yet
- Cyber ScapeDocument1 pageCyber ScapefernandoNo ratings yet
- ISMS Release Mailer Ver 15.0docxDocument2 pagesISMS Release Mailer Ver 15.0docxAditi PandeyNo ratings yet
- IBM Security - Immune System Strategy - 2018!05!15Document34 pagesIBM Security - Immune System Strategy - 2018!05!15Erick GonzalesNo ratings yet
- Software Security EngineeringDocument17 pagesSoftware Security EngineeringMuthu RamachandranNo ratings yet
- VIP Partner Summit22 - FortiGuard SecurityDocument23 pagesVIP Partner Summit22 - FortiGuard Securityfsdfd sdfsdfNo ratings yet
- Exprivia Apulia IoT Security Cisco DR StangalinoDocument51 pagesExprivia Apulia IoT Security Cisco DR StangalinoFernando ArmendarizNo ratings yet
- How To Protect An Ot Network With A Next Generation Firewall and Industrial Cybersecurity ServiceDocument2 pagesHow To Protect An Ot Network With A Next Generation Firewall and Industrial Cybersecurity ServicePablo BinNo ratings yet
- Mind MapDocument1 pageMind Mapmmm wNo ratings yet
- IoT Armour - Next-Gen Zero Trust Cybersecurity For Industry 4.0 ArchitectureDocument1 pageIoT Armour - Next-Gen Zero Trust Cybersecurity For Industry 4.0 ArchitectureBlock ArmourNo ratings yet
- Varutra - Corporate Profile PDFDocument14 pagesVarutra - Corporate Profile PDFNaveen SinghNo ratings yet
- IBM Security Strategy 2016Document34 pagesIBM Security Strategy 2016Erick GonzalesNo ratings yet
- Introduction To IOT Devices Security IssuesDocument8 pagesIntroduction To IOT Devices Security Issuessahilbhai01020304No ratings yet
- Cyber SecurityDocument5 pagesCyber Securityniladri mondalNo ratings yet
- IoT Auditing ISACA Version 1Document61 pagesIoT Auditing ISACA Version 1Sridharan Govindaraj100% (1)
- NSE Insider - Learn How FortiSIEM's New Security Analytics Can Extend Threat Visibility August 11, 2020Document35 pagesNSE Insider - Learn How FortiSIEM's New Security Analytics Can Extend Threat Visibility August 11, 2020fathanNo ratings yet
- Cyber SecurityDocument5 pagesCyber Securityrhyshryroch royerasNo ratings yet
- Microsoft Cybersecurity Solutions GroupDocument63 pagesMicrosoft Cybersecurity Solutions Grouprghr100% (1)
- Inspira OT Security: Change Drivers & Threat LandscapeDocument4 pagesInspira OT Security: Change Drivers & Threat LandscapemahimaNo ratings yet
- Presentation 1Document3 pagesPresentation 1abishekvsNo ratings yet
- WP Ot Ciso Solution SelectionDocument6 pagesWP Ot Ciso Solution SelectionPedrito OrangeNo ratings yet
- Security For Your Digital Transformation: Rennex Callaghan Microsoft Jamaica Cloud SpecialistDocument17 pagesSecurity For Your Digital Transformation: Rennex Callaghan Microsoft Jamaica Cloud SpecialistPravinNo ratings yet
- IAM Sales Pres6oDocument26 pagesIAM Sales Pres6oLohit YadavNo ratings yet
- Kit SuneDocument5 pagesKit SuneNaftali Fernando SitompulNo ratings yet
- Review ArticleDocument16 pagesReview ArticleMonzha labsNo ratings yet
- 07 Huawei Security Products Pre-Sales Specialist TrainingDocument48 pages07 Huawei Security Products Pre-Sales Specialist Trainingkoprael zukyNo ratings yet
- 7 HUAWEI CLOUD Services Security Services V2.2Document27 pages7 HUAWEI CLOUD Services Security Services V2.2Muhammad ImranNo ratings yet
- CCTv1 Exam BlueprintDocument5 pagesCCTv1 Exam BlueprintFirdamdam SasmitaNo ratings yet
- Cybersecurity Domains 3.1Document1 pageCybersecurity Domains 3.1Shun KamNo ratings yet
- Genetec Security Center PDFDocument8 pagesGenetec Security Center PDFMOEDNo ratings yet
- 4 SOC ConsultingDocument54 pages4 SOC Consultingriadelidrissi100% (3)
- ZeroTrustSecurity PDFDocument7 pagesZeroTrustSecurity PDFzdravkoNo ratings yet
- Microsoft Zero Trust Maturity Model - Oct 2019Document7 pagesMicrosoft Zero Trust Maturity Model - Oct 2019Javier MoralesNo ratings yet
- STM32 TrustDocument32 pagesSTM32 Trustnick choiNo ratings yet
- Cyber ScapeDocument1 pageCyber ScapeFernando MuñozNo ratings yet
- Intro Checkpoint Firewall PDFDocument79 pagesIntro Checkpoint Firewall PDFpham datNo ratings yet
- ACSI Event Presentation v1.0Document13 pagesACSI Event Presentation v1.0Dedy HariyadiNo ratings yet
- Network Management in Organisations: Ethical Issues Associated With Various TechnologiesDocument5 pagesNetwork Management in Organisations: Ethical Issues Associated With Various TechnologiesOxford AssignmentNo ratings yet
- International Journal of Information Security and Applications (IJISA)Document2 pagesInternational Journal of Information Security and Applications (IJISA)CS & ITNo ratings yet
- Information Security and Cyber ThreatsDocument14 pagesInformation Security and Cyber ThreatsAnjum NazirNo ratings yet
- Webinar Presentation Cybersecurity4ProtectionEngineersDocument81 pagesWebinar Presentation Cybersecurity4ProtectionEngineersthanh tranNo ratings yet
- A Guide To Starting A Career: in Cyber SecurityDocument16 pagesA Guide To Starting A Career: in Cyber SecurityjasNo ratings yet
- Aruba Central SESION 1Document17 pagesAruba Central SESION 1her.angelsk8100% (1)
- Ibm Bigfix: Patch ManagementDocument16 pagesIbm Bigfix: Patch ManagementDimas ANo ratings yet
- The Map of Cybersecurity Domains Henry Jiang - March 2021 - REV 3.0Document1 pageThe Map of Cybersecurity Domains Henry Jiang - March 2021 - REV 3.0profesor Andres Felipe Gonzalez Coronado100% (1)
- Cyber Security: Week 6: Web Security-E-mail Security-Mobile Device Security-Cloud SecurityDocument30 pagesCyber Security: Week 6: Web Security-E-mail Security-Mobile Device Security-Cloud SecurityUDxNo ratings yet
- A Guide To Starting A Career: in Cyber SecurityDocument16 pagesA Guide To Starting A Career: in Cyber SecurityOvidiu Costea100% (2)
- CB Insights - Cybersecurity Trends PDFDocument44 pagesCB Insights - Cybersecurity Trends PDFJoao Duarte100% (2)
- Cyber Security: Building Confidence in Your Digital FutureDocument2 pagesCyber Security: Building Confidence in Your Digital Futureresurse111No ratings yet
- Final Cyber Security Book (2014-15)Document188 pagesFinal Cyber Security Book (2014-15)Kartik GulatiNo ratings yet
- Mind Map Information Security (Chapter 1)Document4 pagesMind Map Information Security (Chapter 1)Shannyliez StewardNo ratings yet
- Security Monitoring With Automation and Response For Diskominfo DKIDocument10 pagesSecurity Monitoring With Automation and Response For Diskominfo DKIfathanNo ratings yet
- Grid Security Solution BriefDocument7 pagesGrid Security Solution BriefAthithya RNo ratings yet
- Cyber Risk Management Pillars Financial ServicesDocument1 pageCyber Risk Management Pillars Financial ServicesmauriziolapucaNo ratings yet
- NIST Cybersecurity Framework: Identify Protect Detect Respond RecoverDocument1 pageNIST Cybersecurity Framework: Identify Protect Detect Respond RecovermauriziolapucaNo ratings yet
- Bridging The Gap Between Operational Technology and Information TechnologyDocument8 pagesBridging The Gap Between Operational Technology and Information TechnologymauriziolapucaNo ratings yet
- How Artificial Intelligence Is Being WeaponizedDocument5 pagesHow Artificial Intelligence Is Being WeaponizedmauriziolapucaNo ratings yet
- Stuxnet Malware Analysis PaperDocument29 pagesStuxnet Malware Analysis PaperAlexandra MirzacNo ratings yet
- State of Cyber Security 2019 PDFDocument46 pagesState of Cyber Security 2019 PDFcamilorichNo ratings yet