Professional Documents
Culture Documents
Starter Pack - ASAL Computer Science
Uploaded by
Nicholas JonathanOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Starter Pack - ASAL Computer Science
Uploaded by
Nicholas JonathanCopyright:
Available Formats
Computer Science
for Cambridge International
AS & A Level
Starter Pack
Cambridge Elevate Teacher’s Resource
Dear Cambridge Teacher,
The Cambridge International AS & A Level Computer Science Teacher’s Resource will publish
later this summer.
We have produced this ‘Starter Pack’ to enable you to plan and teach the new course while
we finalise and print the new resource.
We are working closely with Cambridge Assessment International Education to provide
endorsed resources to support your students following the Cambridge Pathway to give you
confidence that they reflect the new syllabus.
This pack contains content from the teacher’s resource written to support the new syllabus
for examination from 2021.
It contains the following:
• Table of contents
• Introduction
• Chapter 1 and 2 from Part 1: Theory fundamentals and Chapter 12 and 13
from Part 2: Fundamental problem-solving and programming skills.
Please note that the material included in this Starter Pack is at an advanced draft stage but
may still change between now and publication. In addition, the content of the teacher’s
resource sample is a print version of a digital product and consequently may vary visually
from the actual resource.
Visit our website to view the full series or speak to your local sales representative. You can find
their contact details here:
cambridge.org/education/find-your-sales-consultant
Original material © Cambridge University Press 2019
Contents
Teaching Ideas
Part 1: Theory fundamentals
Chapter 1 Information representation
Chapter 2 Communication and networking technologies
Chapter 3 Hardware
Chapter 4 Logic Gates and logic circuits
Chapter 5 Processor fundamentals
Chapter 6 Assembly language programming
Chapter 7 Monitoring and control systems
Chapter 8 System software
Chapter 9 Security, privacy and data integrity
Chapter 10 Ethics and ownership
Chapter 11 Databases
Part 2: Fundamental problem-solving and programming skills
Chapter 12 Algorithm design and problem-solving
Chapter 13 Data types and structures
Chapter 14 Programming and data representation
Chapter 15 Software development
Part 3: Advanced theory iii
Chapter 16 Data representation
Chapter 17 Communication and internet technologies
Chapter 18 Hardware and virtual machines
Chapter 19 Logic circuits and Boolean algebra
Chapter 20 System software
Chapter 21 Security
Chapter 22 Artificial Intelligence (AI)
Part 4: Further problem-solving and programming skills
Chapter 23 Algorithms
Chapter 24 Recursion
Chapter 25 Programming paradigms
Chapter 26 File processing and exception handling
Chapter 27 Object-oriented programming (OOP)
Chapter 28 Low-level programming
Chapter 29 Declarative programming
Answers to coursebook questions and worksheets
PowerPoint presentations
Practice Papers
Practice Paper answers
Acknowledgements
Copyright
Original material © Cambridge University Press 2019
Teaching guidance
Part 1: Theory fundamentals
Chapter 1: Information representation
Main aims
To introduce learners to:
number systems
representation of quantities
internal coding of numeric, text, graphic image and sound data in a computer system
binary arithmetic
data compression.
Possible programme of study Resources
Topics Syllabus Suggested Resources in the Resources in this Past-paper
section number coursebook guide questions
of 40 min.
lessons
1 Numbers 1.1 3 Question 1.01 Worksheet 1.1
and Task 1.01 Questions
quantities Worked Examples 1.01 1, 3 & 4
& 1.02
Exam-style Questions
1&4
2 Internal 1.1 3 Tasks 1.02, 1.03 & 1.04 Worksheet 1.1 9608/11 Nov 2017
coding of Worked Example 1.03 Questions 2 & 5 Q1
numbers Exam-style Questions Worksheet 1.2
1&4 Question 1
Discussion point Example
Paper 1
Question 1
3 Text 1.1 1 Question 1.02 Worksheet 1.2 9608/12 Jun 2018
Question 2 Q4
4 Multimedia 1.2 5 Task 1.05 Worksheet 1.1 9608/11 Jun 2017
Worked Example 1.04 Question 6 Q3
Exam-style Questions Worksheet 1.2 9608/11 Jun 2018
2, 3 & 5 Question 3 Q2
5 Compression 1.3 2 Extension Question Worksheet 1.1
1.01 Question 7
Exam-style Questions 2 Worksheet 1.2
&5 Question 4
Original material © Cambridge University Press 2019
Preparing for this chapter
Formative assessment may use any or all of the Exam-style Questions in the coursebook.
The bullet-pointed items in the summary at the end of the coursebook chapter may be used to identify which
syllabus content is understood and which syllabus content needs further study.
Topic 1: Numbers and quantities
Covering coursebook section 1.01 Number systems and 1.02 Numbers and quantities
Introduction
The syllabus has defined the following learning objectives relating to this topic:
show understanding of the basis of different number systems
describe practical applications where Binary Coded Decimal (BCD) and Hexadecimal are used
show understanding of binary magnitudes and the difference between binary prefixes and decimal prefixes.
The notes and guidance given in the syllabus provide details of the topic content relating to these learning
objectives. However, the order is not intended as a basis for teaching. The breakdown into topics here matches
the coursebook content and is suitable for a teaching programme.
Note that the use of binary prefixes for defining quantities is an entirely new topic for this syllabus so there are no
exam paper questions for the 9608 syllabus that relate to this. The binary prefixes are only defined for large
values so it is only necessary to consider the decimal prefixes for the comparable large values.
Teaching guidance
Introducing the topic
It would be useful to start a class discussion to get learners to think of all the different types of numbers with
which they are familiar. Finally, you could ask them to identify which types of number they are going to meet in
the syllabus, and where.
You could follow this by a PowerPoint slide presentation outlining the individual aspects to be covered in the
following lessons.
You can postpone an introduction to binary prefixes until the last lesson for this topic.
Engaging with the topic
With regard to number conversions, the requirement is for learners to gain confidence through the completion of
paper-based exercises. You could set this up initially as an active learning session. Give learners values to convert,
without any introduction to the formal approaches suggested in the coursebook. Peer assessment with learners
working in pairs is a possibility. At the end, you could ask learners to assess the usefulness of the methods they all
have discovered or been introduced to.
Original material © Cambridge University Press 2019
You could ask learners unfamiliar with the use of decimal prefixes to research how engineers refer to energy
when they describe the output from a power station.
Opportunities for assessment
Check learners’ understand the following before moving on to the next topic:
The norm for unsigned integers is to count from 0 upwards
The values for powers of two from 20 up to 28 are 1, 2, 4, 8, 16, 32, 64, 128, 256.
It is best to leave further assessment until the next topic has been studied.
Differentiation
Supporting learners
It is important to insist that learners who are struggling with conversions involving binary numbers always write
the binary digits in boxes. Each box should have a header that has the appropriate power expressed as 20, 21, for
example, or the corresponding denary value or possibly both. The aim is to ensure the correct number of digits
are used and also to reinforce learners’ familiarity with the denary equivalents of the powers of two.
You could ask learners to look at Worked Examples 1.01 and 1.02 in the coursebook and to answer Questions 1, 3
and 4 in Worksheet 1.1.
Language awareness
Learners sometimes confuse binary and denary. It is important to stress that denary and decimal are synonyms.
However, there are certain contexts where a particular one is chosen.
Further reading
http://courses.cs.vt.edu/~csonline/NumberSystems/Lessons/index.html
http://csunplugged.org/binary-numbers
https://physics.nist.gov/cuu/Units/binary.html
Original material © Cambridge University Press 2019
Topic 2: Internal coding of numbers
Covering coursebook section 1.03 Internal coding of numbers
Introduction
The syllabus has defined the following learning objectives related to this topic:
show understanding of the basis of different number systems
perform binary addition and subtraction
describe practical applications where Binary Coded Decimal (BCD) and Hexadecimal are used.
As with the previous topic, the details of the syllabus content are not presented in an order that is meant to be
the order for teaching. Note that the syllabus refers only to positive or negative integers. There are a number of
points to note here:
You might wish to extend the teaching here to include fixed point binary real numbers, in order to cover the
fact that the mantissa for a floating-point representation of a number is a fixed point real value.
Sign and magnitude representation of a signed integer is not included in the syllabus. However, you will need
to refer to this in the context of converting a denary representation of a negative integer value into a two’s
complement binary representation.
Currency values are fixed point real numbers but cannot be stored and manipulated as real values because of
the inevitable approximation when a denary fraction is converted to a binary fraction. This problem
associated with real numbers is not explored in detail here. However, when explaining the use of BCD for
handling currency values you will need to give some explanation as to why this is done.
Binary addition and subtraction are an entirely new topic for this syllabus so there are no exam paper
questions for the 9608 syllabus that relate to this.
Teaching guidance
Introducing the topic
A PowerPoint presentation can be used that begins by emphasising two vital points:
There is a constraint on the storage of a value in a computer system caused by the limited number of bits
allowed
There is a need for a computer system to be able to carry out binary arithmetic effectively.
You could follow the PowerPoint for a definition of two’s complement and illustration of conversion from denary.
You could postpone introducing BCD and its applications until the last lesson for this topic.
Engaging with the topic
As previously, the requirement is: Learners can gain confidence in number conversions by completing paper-
based exercises.
Original material © Cambridge University Press 2019
You could set up consideration of binary arithmetic initially as an active learning session with learners given
values to add or subtract. This will allow them to discover the potential problems. You could begin this with
examples of unsigned integer arithmetic then follow on with using signed integers.
Opportunities for assessment
Check learners understand the following before moving on to the next topic:
A byte has eight bits so there are 28 = 256 different combinations allowing 256 different codes, but for
unsigned integers the highest value is 256 – 1 because one of the codes represents 0
In two’s complement representation of signed integers the topmost bit is 0 for positive and 1 for negative
values
In two’s complement representation the smallest magnitude negative number has all 1s. This can be
explained by the fact that the corresponding denary value can be calculated by assigning a negative value to
the most significant bit but positive values to all remaining bits
Just adding a leading zero to a binary value converts it to two’s complement
Two’s complement values are self-complementary; applying the two’s complement conversion takes positive
to negative or negative to positive
You can add any number of leading zeros to a representation of a positive value without changing the value
You can add any number of leading ones to a representation of a negative value without changing the value
BCD coding does not fully utilise the four bits in a nibble.
Formative assessment covering this topic and the previous one would be appropriate. Tasks 1.01 to 1.04 from the
coursebook could be used along with Questions 1 to 5 from Worksheet 1.1.
Opportunities for reflection
You could ask learners to draw up a self-evaluation checklist of the individual concepts covered in these first two
topics. This would allow them to identify what they have been introduced to and which aspects need further
revision.
Differentiation
Supporting learners
You can ask learners to look at Worked Example 1.03 in the coursebook and to answer Questions 2 and 5 in
Worksheet 1.1.
Challenging learners
You can encourage high achievers to research computer arithmetic, including computer arithmetic associated
with the use of BCD.
You could use the Discussion Point from the coursebook and Question 5 from Worksheet 1.1 as a basis for
reflecting on the underlying reasons for the use of two’s complement.
Learners should answer Question from Worksheet 1.2.
Original material © Cambridge University Press 2019
Further reading
http://courses.cs.vt.edu/~csonline/NumberSystems/Lessons/index.html
http://csunplugged.org/binary-numbers
Topic 3: Text
Covering coursebook section 1.04 Internal coding of text
Introduction
The syllabus has defined the following learning objective related to this topic:
show understanding of, and be able to represent, character data in its internal binary form depending on the
character set used.
This topic requires learners to gain knowledge and understanding but you must reassure learners that no detailed
knowledge of the coding schemes is expected.
The ASCII concept is simple and straightforward and standardisation has occurred. However, learners need to be
made aware that the standard is not always followed. You might wish to schedule a lesson for introducing this
topic to immediately precede the introduction of programs using built-in functions for handling strings. These are
introduced in Section 13.06 of the coursebook.
Teaching guidance
Introducing the topic
A presentation discussing the origin of the character coding schemes is needed. This can include illustrations of
some of the ASCII codes. It can also describe how Unicode can simultaneously incorporate codes which have
different representations that might use one, two, three or four bytes.
Engaging with the topic
You could encourage learners to carry out online searches to investigate the schemes in a little more detail.
However, linking the subject to some programming will be a sensible way to engage learners.
Opportunities for assessment
Check learners understand the following before moving on to the next topic:
Seven-bit ASCII is a long-established standard; eight-bit versions of ASCII exist but have not been standardised
ASCII codes are either control codes, which are not displayed, or graphic codes, which are
Conversion of an upper case letter to lower case just requires one bit in the code to be changed
The normal version of Unicode is UTF-8
Unicode refers to code points, documented as U+ followed by four hexadecimal digits; for example, the letter
a is code point U+0061 and the Greek letter σ is code point U+03C3.
Original material © Cambridge University Press 2019
Differentiation
Supporting learners
Question 1.02 in the coursebook might help learners to appreciate the basic requirements of a character coding
scheme.
Challenging learners
You could ask high achievers to carry out limited research into some of the Unicode schemes.
Question 2 in Worksheet 1.2 could be attempted.
Further reading
https://www.ascii-code.com/
https://www.webopedia.com/TERM/A/ASCII.html
http://unicode.org/
Topic 4: Multimedia
Covering coursebook sections 1.05 Images and 1.06 Sound
Introduction
The syllabus has defined the following learning objective related to this topic:
show understanding of how data for a bitmapped image are encoded
perform calculations to estimate the file size for a bitmap image
show understanding of the effects of changing elements of a bitmap image on the image quality and file size
show understanding of how data for a vector graphic are encoded
justify the use of a bitmap image or vector graphic for a given task
show understanding of how sound is represented and encoded
show understanding of the impact of changing the sampling rate and resolution.
Some points to note:
Only graphic and sound remain in the syllabus; video has been removed
The focus is on graphic files but with no reference to the creation of a graphics file
For sound the focus is on the process of capturing sound and storing a binary representation of the sound
There is no explicit reference at this stage to how encoded sound is to be used, or to the use of proprietary
formats for storing multi-media content.
Original material © Cambridge University Press 2019
This content is essentially theoretical, with little reference to any technology required for implementation. It also
is a framework for learners to demonstrate understanding by performing calculations.
Teaching guidance
Introducing the topic
There will be a need for presentations where learners are introduced to the concepts and the terminology
associated with these specialised areas. However, it might not be the best approach to use these as the first
introduction to the topic.
The following figure from the coursebook can be used in a presentation to explain sampling of sound.
Engaging with the topic
It is probable that at least some learners will have had experience of using multi-media content. If this is the case
you could ask them to relate their experiences in a discussion session. This could be an aid in engaging learner
interest in a topic requiring the memorisation of a lot of facts and definitions. It will also allow you to point out
which parts of their experience are relevant to the syllabus content.
There is scope for practical activities to develop understanding and skills. You could provide learners with graph
paper. Working in pairs, each could draw two or three objects, create a drawing list then pass this on to the other
learner who has to recreate the drawing. An option would be to ask all learners to tackle Task 1.05 from the
coursebook.
Another option is for bitmap images to be created on graph paper with different resolutions or on a spreadsheet
page using the cells as pixels.
To emphasise the need for some header (meta) data in a bitmap file, you could demonstrate this using 24
cardboard squares laid out in one of the possible rectangular shapes. An image is then drawn on the rectangle.
The squares are collected in order starting from the top left. The pile of squares represents the contents of a
bitmap file with each square representing a pixel. A learner is then asked to choose a resolution for the bitmap
image knowing that it must be one of the options 3 × 8, 4 × 6, 2 × 12 or one of these with the values reversed. The
learner then positions the squares one-by-one to match the resolution. The class is invited to inspect each
incorrect attempt to guess the correct resolution, which will be the one that reveals an image.
Original material © Cambridge University Press 2019
You could use a practical exercise to reinforce the understanding of encoding sound, with learners working in
pairs. One learner could draw a waveform on graph paper then create a set of sample values of the amplitude
then pass it to the other learner to recreate the waveform. Then they can compare the two waveforms.
Opportunities for assessment
Check learners understand the following before moving on to the next topic:
There are two defining quantities for a bitmap image: the colour depth defining the number of bits per pixel
and the resolution defining the dimensions of the image matrix measured in pixels
A pixel is the smallest individual element in an image, which can be thought of as a dot, small circle or square
A pixel is defined by a binary code representing its colour
The position of the pixel code in the bitmap file allows its position in the image to be calculated using the
header data defining the image resolution
The drawing list for an object in a vector graphic file should begin with the name of the shape
Dimensions in a drawing list must be relative to the overall dimensions of the image
The sampling rate defines precisely when measurements of amplitude are made
The sampling rate should be in accordance with Nyquist’s theorem
There is an approximation when the ADC converts the analogue signal to a binary value
The approximation is closer if more bits are used for the code, that is, if the sampling resolution is improved
File size increases with increasing sampling resolution and with increasing sampling rate but this will
improve quality.
This is a suitable opportunity for formative assessment. Exam-style Questions 2 and 3 from the coursebook could
be used along with Question 6 from Worksheet 1.1 and Question 3 from Worksheet 1.2.
Because this topic has so much specialised terminology it is a good opportunity to have an assessment using flash
cards. The key terms in the coursebook could be made into flash cards for you to hold up and ask learners to
write down the definition or call out the definition.
Opportunities for reflection
You could ask learners to draw up a self-evaluation checklist of the individual concepts covered in this topic.
This would allow them to identify what they have been introduced to and which aspects need further revision.
The Reflection Question from the coursebook could be used as a focus for some reflection on all of the topics
covered at this stage.
Differentiation
Supporting learners
You could ask learners to look at Worked Example 1.04 in the coursebook and to answer Question 6 in
Worksheet 1.1.
Challenging learners
Question 3 in Worksheet 1.2 should be answered.
Original material © Cambridge University Press 2019
Further reading
https://www.nationalarchives.gov.uk/documents/graphic-file-formats.pdf
https://www.bbc.com/bitesize/guides/zpfdwmn/revision/2
https://www.hardwaresecrets.com/how-analog-to-digital-converter-adc-works/2/
Topic 5: Compression
Covering coursebook section 1.07 Compression techniques
Introduction
The syllabus has defined the following learning objective related to this topic:
show understanding of the need for, and examples of, the use of compression
show understanding of lossy and lossless compression and justify the use of a method in a given situation
show understanding of how a text file, bitmap image, vector graphic and sound file can be compressed.
There is no explicit reference to the compression automatically applied if a file is saved in a proprietary format or
to the compression used when files are zipped. The only technique identified is RLE. You will have to apply
judgement as to how many other techniques might interest your learners.
Teaching guidance
Introducing the topic
Learners need to gain knowledge and understanding of the principles of compression. It might be beneficial to
begin with a discussion about the need to use compression or the advantages of using compression. Encourage
your learners to relate any direct experience they have had in using compression. You could remind them that
saving a file to a specific file type can lead to compression being used without telling the user. This should lead up
to the crucial consideration of when it is beneficial or necessary to recover the original file from its compressed
form. This can then introduce the concepts of lossy and lossless compression. You could conclude by summarising
the main points.
Engaging with the topic
Practical exercises could involve using appropriate software to compress files. You could compare the files sizes
before and after compression. Learners could check the quality of the files before and after compression.
You could ask learners to scrutinise a short paragraph of text. They should use the find operation to get a count of
common letters. They could then use the suggested codes, shown in coursebook Table 1.10 for Huffman coding,
to calculate the number of bits saved in comparison with the number needed for ASCII coding for each letter.
They could then compare this to the number of bits saved when using ASCII codes for the letters.
You could ask learners to search online to consolidate their understanding of this topic. You could use Extension
Question 1.01 in the coursebook as a starting point.
Original material © Cambridge University Press 2019
Opportunities for assessment
Check that learners understand the following before moving on to the next chapter:
It is vital that a file containing text is compressed using a lossless technique otherwise the text could become
incomprehensible
Lossy techniques normally rely on the imperfection of human senses such as limited ability to hear certain
frequency ranges or limited ability to distinguish between colours.
Differentiation
Supporting learners
Question 7 in Worksheet 1.1 could be used.
Challenging learners
Question from Worksheet 1.2 should be answered.
Language awareness
Learners absolutely must use the terms ‘lossy’ or ‘lossless’. They should not use expressions such as ‘jpeg
compression’ or anything similar.
Further reading
http://computer.howstuffworks.com/file-compression2.htm
www.cs4fn.org/mathemagic/sonic.html
Original material © Cambridge University Press 2019
Worksheet 1.1: for testing basic understanding
1 Select the binary and hexadecimal representations of the denary number 62 from the following options:
A 11111001
B 00011111
C 00111110
D 1F
E 3E
F 3D
2 The 8-bit code 10010001 could represent a number of values depending on the coding scheme being used.
Select from the following the one value that it could not represent.
A 145
B 91
C 17
D -111
3 24 21
4s 2s
1 0 1 0 0 1 1 0
a The last row in the above table shows a binary code. Fill in the top two rows of the table, assuming that
the code represents a binary number.
b If this binary code represents an unsigned integer, is the denary equivalent an even or an odd number?
Explain your reason.
c If this binary code represents an unsigned integer, give the denary equivalent.
d If this binary code represents a two’s complement representation of a signed integer, does it represent a
negative or positive number? Explain your reason.
e Give the denary equivalent of this two’s complement representation.
4 If the denary number 373 is to be converted to a binary representation, how many bits will be needed?
Explain your reason.
5 A car has an odometer (measuring distance travelled in kilometres), which at the start of a journey shows
99940 and at the end shows 00230.
a Use common sense reasoning to find the distance travelled.
b Try calculating this by subtracting 99940 from 00230 using a calculator or spreadsheet.
What is the problem?
c Nine’s complement is defined as the number obtained by subtracting each digit from 9 and ten’s
complement is obtained by adding 1 to the nine’s complement. Show a calculation to get the correct
answer by converting the 99940 to its nine’s complement then to its ten’s complement and then adding
this to 00230.
Original material © Cambridge University Press 2019
6 A bitmap has an image stored that has resolution of 1024 × 768 and a colour depth of 8. Another file contains a
five-minute soundtrack stored using a sampling rate of 100 samples per second and a sampling resolution of 16.
Which file is the larger one?
7 Give an example where lossy compression will be useful and another where lossless compression is essential.
Original material © Cambridge University Press 2019
Worksheet 1.2: more challenging questions
1 Binary Coded Decimal (BCD) can be used to store currency values with each individual denary digit
represented by one BCD code, and an implied position for the decimal point between the two nibbles in
the byte. It is possible to carry out arithmetic using BCD but this requires a special technique as discussed in
the coursebook.
a Use the following diagram to show the BCD representations of the two numbers 9.75 and 7.68, assuming
packed BCD is used.
b If the two numbers are added what is the total expressed as a denary value?
c If the two binary representations are added, ignoring the fact that they are BCD codes, what is the
result obtained?
d Show a correct calculation using the BCD values but applying the correction factor 0110.
e Why does this correction factor work?
f 9.75 can be represented exactly as a fixed-point binary value but 7.68 cannot. Why is this so?
2 Choose whether each of the following statements is true or false:
A In the early days of computing a printer could only print upper-case letters.
B To convert the ASCII code for an upper-case letter to the corresponding lower-case letter you have to
add 20.
C To convert the ASCII code for a lower-case letter to the corresponding upper-case letter you have to
add 20.
3 Choose whether each of the following statements is true or false:
A A picture element is an object in a vector graphic image.
B Colour depth refers to the intensity of the colour used to define an object in a vector graphic image.
C A drawing list is a list of the objects in a vector graphic image.
D The resolution of an image is the size of a pixel in a bitmapped image
4 The following table is a rearranged version of Table 1.04 in the coursebook. It shows a possible set of Huffman
codes to be used for lossless compression of a text consisting only of the eight letters shown.
E T o h l p w z
10 01 111 110 0001 0000 0011 0010
The codes will have been chosen by using an algorithm that has as the input the frequencies of occurrence of
each of the letters in the particular text. The choice of codes can be represented as a Huffman tree. A partially
completed tree is shown below:
Original material © Cambridge University Press 2019
a Can you work out the rules that are being used to position the letters on the tree so that they have the
codes as shown in the table?
b Can you complete the tree by placing the remaining letters?
c Could this tree be extended to include more letters? If not why not?
d Can you suggest a modification of the tree to include two more letters?
Original material © Cambridge University Press 2019
Teaching guidance
Part 1: Theory fundamentals
Chapter 2: Communication and networking
technologies
Main aims
To introduce learners to:
the purpose and benefits of networking devices
network topologies
network technology and media
ethernet
the Internet infrastructure and applications
IP addressing
domain names.
Possible programme of study Resources
Topics Syllabus Suggested Resources in the Resources in this Past-paper
section number of coursebook guide questions
40 min. lessons
1 Networking 2.1 2 Two Discussion Points
2 Supporting 2.1 3 Question 2.01 Worksheet 2.1 9608/11 Jun
technology Task 2.01 Questions 1 to 5 2018 Q1
Exam-style Question 1 Worksheet 2.2
Question 1
3 Ethernet 2.1 1 Discussion Point Worksheet 2.1
Question 6
Example Paper 1
Question 2
4 Internet 2.1 3 Question 2.02 Worksheet 2.1
Task 2.02 Question 7
Exam-style Question 3
Discussion Point
5 Addressing 2.1 5 Extension Question 2.01 Worksheet 2.1 9608/11 Nov
Task 2.03 Questions 8, 9 & 10 2018 Q2
Exam-style Questions Worksheet 2.2 9608/12 Nov
2, 4, 5 & 6 Question 2 2018 Q2
Two Discussion Points
Original material © Cambridge University Press 2019
Preparing for this chapter
Formative assessment may use any or all of the Exam-style Questions in the coursebook.
The bullet-pointed items in the summary at the end of the coursebook chapter may be used to identify syllabus
content that is understood and syllabus content that needs further study.
Topic 1: Networking
Covering coursebook sections 2.01 The evolution of the purpose and benefits of networking and 2.02 Network
topologies.
Introduction
Before considering this specific topic, it is worth emphasising two general points:
1 The syllabus content covered by the whole of this chapter is presented as an unstructured list of items. This
fragmentation is inevitable with networking embracing such a wide range of different aspects, each of which
is quite complex, and many items will be better understood when the A Level content is covered.
2 Networking is a practical activity involving the installation and management of hardware and software.
However, you as a teacher and any of your learners are unlikely to have any practical experience of
networking. You are likely to have used systems that are networked. Almost all of the subject matter will
therefore be experienced by your learners theoretically and not practically.
The syllabus has defined the following learning objectives related to this topic:
show understanding of the purpose of, and benefits of, networking devices
show understanding of the characteristics of a LAN (local area network) and a WAN (wide area network)
explain the client-server and peer-to-peer models of networked computers
show understanding of thin-client and thick-client and the differences between them
show understanding of the bus, star, mesh and hybrid topologies.
There is a major change in syllabus content from the 9608 syllabus, in that scripting has been omitted. This leaves
the client-server content more generalised. Another change is that network topologies are now here and not in
the A Level content as was the case previously. Ring topology has been removed. Hybrid technology is a new
feature.
Teaching guidance
Introducing the topic
You could introduce this topic by starting a class discussion to get learners to think of their experience of using
networks and their understanding of the technologies used.
You could follow this by a presentation outlining the individual aspects to be covered in the following lessons.
Original material © Cambridge University Press 2019
Engaging with the topic
It will be helpful if you can discuss the networks in daily use (perhaps with class participation) with technical staff,
and examine the components.
There are two Discussion Points in the coursebook chapter that could be utilised.
Opportunities for assessment
Check learners understand the following before moving on to the next topic:
Although a server is usually presented as a hardware device attached to a network, it is really the software
running on the hardware.
Further reading
https://www.studytonight.com/computer-networks/
Topic 2: Supporting technology
Covering coursebook sections 2.03 Transmission media and 2.04 LAN hardware
Introduction
The syllabus has defined the following learning objectives related to this topic:
show understanding of the differences between and implications of the use of wireless and wired networks
describe the hardware that is used to support a LAN.
You might wish to briefly discuss Bluetooth because your learners are likely to be familiar with its use. However,
you should note that the syllabus only has explicit reference to WiFi. Hubs and gateways could be introduced
even though they are not explicitly mentioned in the syllabus.
Teaching guidance
Introducing the topic
A presentation would be appropriate to introduce transmission media. For learners lacking any prior knowledge
of electromagnetic waves, for example light, you could give some introductory coverage of how the spectrum is
divided into different types of electromagnetic wave, depending on frequency (or wavelength).
You could postpone a presentation regarding LAN hardware until the last lesson for this topic.
Engaging with the topic
It should be possible to examine items of cabling and hardware in use at your centre. It is also a topic for which
learners can be given individual search tasks. For example, you could ask learners to gather some details about
the different types of twisted pair then present their findings.
Original material © Cambridge University Press 2019
You could hold discussions about the relative benefits and drawbacks of using satellites or fibre-optic cabling for
long distance communication.
Opportunities for assessment
Check learners understand the following before moving on to the next topic:
Copper wire is the norm for twisted pair or coaxial cable
Attenuation is loss of signal quality due to distance transmitted
Interference is an unwanted interaction between the transmitted signal and other signals
The altitude of a satellite is chosen according to the purpose of the satellite.
Differentiation
Supporting learners
You could ask learners to answer Questions 1 to 4 in Worksheet 2.1.
Challenging learners
Question 1 in Worksheet 2.2 can be attempted.
Further reading
http://ecomputernotes.com/computernetworkingnotes/communication-networks/describe-the-different-transmission-
media
https://www.technologyuk.net/telecommunications/networks/transmission-media.shtml
https://www.linux.com/learn/intro-to-linux/2017/10/linux-networking-hardware-beginners-lan-hardware
Topic 3: Ethernet
Covering coursebook section 2.05 Ethernet
Introduction
The syllabus has defined the following learning objective related to this topic:
show understanding of Ethernet and how collisions are detected and avoided.
Only a very limited knowledge of Ethernet is required at this stage. Protocols are properly introduced at A Level
stage.
Original material © Cambridge University Press 2019
Teaching guidance
Introducing the topic
A presentation will suffice here. This should outline why collisions are a problem when end-systems share a
transmission medium and how these can be avoided.
Engaging with the topic
In accordance with the Discussion Point in the coursebook, learners could be asked to research the development
of Ethernet through ever faster versions.
Differentiation
Supporting learners
Question 6 in Worksheet 2.1 could be attempted.
Further reading
http://www.teach-ict.com/technology_explained/ethernet/ethernet.html
https://www.lifewire.com/what-is-ethernet-3426740
Topic 4: Internet
Covering coursebook sections 2.06 The Internet infrastructure and 2.07 Applications that make use of the
Internet
Introduction
The syllabus has defined the following learning objective related to this topic:
describe the hardware that is used to support the Internet
describe the role and function of a router in a network
show understanding of the differences between the World Wide Web (WWW) and the Internet
show understanding of cloud computing
show understanding of bit streaming.
The major concepts associated with the Internet are TCP/IP, layered protocol suites and packet switching. Since
all of these are only formally introduced in the A Level syllabus content, the learning experience here has to be
carefully planned. The coursebook chapter does use the term ‘protocol’ in a few places but usually with a
disclaimer that its exact meaning is not important at this stage. You might decide that a little clarification here
would be beneficial.
Cloud computing is an entirely new topic for this syllabus so there are no exam paper questions for the 9608
syllabus that relate to this.
Original material © Cambridge University Press 2019
Teaching guidance
Introducing the topic
It is very likely that many if not all of your learners think that they know all about the Internet. You could begin
with a class discussion to find out how good their prior knowledge is.
You should be able to introduce the Discussion Point and Question 2.02 from the coursebook into this discussion.
This can be followed by a presentation outlining the subject matter that needs to be understood at this stage.
Engaging with the topic
When introducing bit streaming it is likely that learners will have used this without giving it much thought. It is an
opportunity for learners to carry out some research to expand their knowledge. Video is often involved: this topic
has been removed from the multi-media section of the syllabus, but learners might wish to gain some background
knowledge and supplement their earlier learning. They could gain some knowledge of compression techniques.
The use of a buffer is a key element: this does not appear in the syllabus until the next section, but there is an
opportunity here to gain a little knowledge in advance.
Opportunities for assessment
Check learners understand the following before moving on to the next topic:
The Internet is an internetwork that can support applications
The World Wide Web is one of many applications supported by the Internet
On-demand streaming requires storage because viewing is taking place after the initial broadcast. However, it
does not require a download to the viewer’s computer.
Both on-demand and real-time bit streaming over the Internet require the use of a buffer on the viewer’s
computer.
The final topic in this chapter will introduce some detailed content relating to one small aspect of networking. For
this reason the current stage is a suitable opportunity for formative assessment of what has been studied so far.
You could use Exam-style Questions 1 and 3 from the coursebook and Question 7 from Worksheet 2.1.
Opportunities for reflection
You could ask learners to draw up a self-evaluation checklist of the individual concepts covered in this topic. This
would allow them to identify what they have been introduced to and which aspects need further revision.
You could use the Reflection Question from the coursebook as a focus for some reflection on all of the topics
covered so far.
Differentiation
Supporting learners
Learners could attempt Question 6 in Worksheet 2.1.
Original material © Cambridge University Press 2019
Challenging learners
Ask learners to complete Task 2.02 in the coursebook.
Language awareness
The terms ‘the Internet’ or ‘the web’ are often treated as synonyms. Learners need to develop a rigorous
approach to their use of language.
Further reading
http://web.stanford.edu/class/msande91si/www-spr04/readings/week1/Howstuffworks.htm
https://computer.howstuffworks.com/internet/basics/internet-infrastructure.htm
https://computer.howstuffworks.com/cloud-computing/cloud-computing.htm
Topic 5: Addressing
Covering coursebook section 2.08 IP addressing and 2.09 Domain names
Introduction
The syllabus has defined the following learning objective related to this topic:
explain the use of IP addresses in the transmission of data over the Internet
explain how a Uniform Resource Locator (URL) is used to locate a resource on the WWW, and the role of the
Domain Name Service (DNS).
The syllabus has retained the structure of the content from the 9608 syllabus with IP addressing introduced here
in the AS syllabus before IP has been fully introduced as part of the A Level content. This allows the learning
programme to be limited to just a few topics.
The content has two new items specifically identified: sub-netting and static and dynamic IP addressing. In
addition, IPv6 is now specifically identified alongside IPv4. The reference to IPv6 is in a guidance sentence about
the format of an address. The remainder of the learning can focus on the use of IPv4.
Teaching guidance
Introducing the topic
You have an option here. Because your learners will be familiar with using URLs and email addresses you might
choose to begin with a discussion of domain names and the domain name system. You could then consider the
underlying addressing system. The alternative is to start with the IP address system and then move on to the
user-friendly domain name system. Whichever approach is used, there is a need for learners to become familiar
with a considerable body of facts and concepts. In addition, they need to understand the reasons for the
decisions that have been made with respect to Internet usage. Learners could initially be asked to carry out their
own research. However, there will be a need for a presentation to ensure that all relevant aspects have been
considered and understood.
Original material © Cambridge University Press 2019
Engaging with the topic
You will need problem-solving exercises to consolidate the learners’ knowledge and understanding. You could
give learners questions individually or in small groups. The coursebook contains Discussion Points, Task 2.03 and
Extension Question 2.01 that could be part of this activity.
Opportunities for assessment
Check that learners understand the following before moving on to the next chapter:
IPv4 addressing is hierarchical; each address consists of a netID and a hostID
The IPv4 address has 32 bits so it occupies four bytes
The address can be written in a dotted decimal representation
A domain name is constructed in accordance with a hierarchy of domains
The Domain Name Service (DNS) uses a distributed hierarchical database installed on servers attached to the
Internet
An IPv6 address has 128 bits for a full address but abbreviated representations are allowed.
You could use questions 2, 4, 5 and 6 from the Exam-style Questions in the coursebook for formative assessment.
Differentiation
Supporting learners
Questions 7, 8 and 9 in Worksheet 2.1 could be answered.
The IP address topic is an opportunity to check that binary and hexadecimal representations are well understood.
Challenging learners
You should give learners question 2 from Worksheet 2.2.
Further reading
https://www.uswitch.com/broadband/guides/what_is_an_ip_address/
http://www.build-your-website.co.uk/understanding-domain-names/
Original material © Cambridge University Press 2019
Worksheet 2.1 for testing basic understanding
1 a Name the two types of cable that use copper to transmit an electrical signal.
b Which one of these is typically bundled?
c In the bundled cable, what is done to minimise interference?
d In the other type, why is interference less of a problem?
2 Sort the different cable types by numbering them 1, 2 and 3.
In part a, number them in order of increasing bandwidth.
In part b, number them in order of increasing attenuation at high frequency.
Part a
Coaxial
Fibre optic
Twisted pair
Part b
Coaxial
Fibre optic
Twisted pair
3 a Explain three factors that need to be considered when using wireless transmission.
b For each factor, state which type of radiation it interferes with the most.
4 Choose whether each statement about wireless transmission is true or false:
A The frequency for these forms of electromagnetic radiation increases from radio wave to microwave to
infrared.
B Attenuation due to rain is worst for radio waves.
C Infrared is the one that can best transmit through a wall.
D Infrared can be more effectively focussed into a directed beam.
5 Choose from the list below the correct word or phrase for each of the blank spaces in the following
two sentences.
The _______________________ is provided by _______________________ satellites where
_______________________ are needed for global coverage. The _______________________ is
supplemented by _______________________ satellites where _______________________ are needed for
global coverage.
A ten
B fifty
C medium earth orbit (MEO)
D global positioning system (GPS)
E low earth orbit (LEO)
F cellular phone network
Original material © Cambridge University Press 2019
6 The CSMA/CD (carrier sense multiple access with collision detection) technology is sometimes used with
Ethernet in a LAN.
a When is it essential to use this?
b Outline the steps in the procedure that is followed when an end-system wishes to send a transmission
c Does an end-system have to take any action to ensure that a transmission is received using Ethernet?
7 Choose whether each statement is true or false
a POTS and PSTN mean the same thing.
b A PSTN might function as an ISP.
c A leased line service is a type of dial-up service provided by a PSTN.
d The Internet is just a very large WAN.
e The web and the Internet mean the same thing.
8 Consider the following two dotted decimal representations:
192.0.255.15
128.235.455.15
Explain why only one is a possible IP address.
9 Consider the following IP addresses:
192.38.45.255
128.38.45.255
64.38.45.255
Without converting to binary form, state which class each IP address represents.
10 Consider the following URL:
http://www.mirc.co.uk/help/jarkko2.txt
Explain the meaning of each part of this. In particular, identify the domain name and its associated hierarchy.
Original material © Cambridge University Press 2019
Worksheet 2.2: more challenging questions
1 By creating a scale drawing, calculate some time delays for signals transmitted from a satellite to Earth.
Assume that a LEO satellite has altitude 1000 km. For a LEO and for a GEO satellite, calculate:
a The time to reach the nearest point on the surface.
b The difference in timing to reach the furthest point accessible.
Discuss the significance of your findings with respect to the speeds of operation of a computer system.
2 a An organisation has been allocated a class C IP address that it intends to use in a sub-netting scheme. If it
decides to create LANs with 30 workstations in each, how many LANs could be created? If instead they
decide to limit each LAN to only 14 workstations, how many LANs could be created?
b Construct a diagram to illustrate sub-netting with four LANs. The diagram should show the four LANs with
four workstations, with each workstation labelled with a binary representation suitable for its
identification. Explain your labelling of the workstations. Full IP addresses are not needed.
Original material © Cambridge University Press 2019
Teaching guidance
Part 2: Fundamental problem solving
and programming skills
Chapter 12: Algorithm design and
problem solving
Chapter 14: Programming and
data representation
Main aims
To enable learners to
understand the importance of algorithms
practise the skill of problem solving
learn the basics of programming in one chosen programming language.
It is suggested that Chapter 12 is worked through in parallel with Chapter 14 (Sections 14.1 to 14.13).
Possible programme of study Resources
Topics Syllabus Suggested Resources in the Resources in this Past-paper
section number coursebook guide questions
of 40 min.
lessons
1 Introduction to 9.1 1 Task 12.01 Exercise 12.01
computational
thinking
2 Introduction to 9.2 3 Task 12.02 Exercise 12.02 9608/21 Jun
algorithms 2018 Q1
3 The concept of 9.2 3 Worked Exercise 12.03
variables Example 12.01
Task 12.03
4 Introduction to 11.1 4 Question 14.01 Exercise 12.04
the Task 14.01
programming
environment
Original material © Cambridge University Press 2019
5 Data types 10.1 6 Task 14.02 Exercise 12.05
11.1 (Worked Worksheet
Example 12.01) 12.1/14.1
Exam-style Questions 1 & 2
Question 13.1
6 Logic 11.1 12 Task 12.04 Worksheet 9608/23 Jun
statements, 11.2 Worked 12.1/14.1 2015 Q2
Boolean Example 12.02 Questions 3 & 4 9608/22 Nov
expressions and Question 12.01 2015 Q1
selection Worked 9608/21 Nov
Example 12.03 2016 Q5
Task 14.03 9608/22 Nov
(Worked 2016 Q6
Example 12.03)
Task 14.04
(Worked
Example 12.02)
7 The CASE 11.2 4 Task 14.05 Worksheet
construct 12_14.5
8 Iteration 11.2 18 Worked Worksheet 9608/21 Jun
Example 12.04 12.1/14.1 2015 Q4
Question 12.02 Questions 6 to 12 9608/21 Nov
Worked 2015 Q5
Example 12.05 9608/21 Jun
Worked 2016 Q1
Example 12.06 9608/21 Jun
Worked 2016 Q2
Example 12.07 9608/21 Jun
Worked 2017 Q1
Example 12.08 9608/22 Jun
Task 12.05 2017 Q1
Worked
Example 12.09
Task 14.06
(Worked
Examples 12.05,
12.08 & 12.09)
Task 14.07
(Worked Examples
12.04 & 12.06)
Task 14.08
(Worked
Example 12.06)
Exam-style
Questions 12.1,
12.2 & 12.3
Exam-style
Question 14.1
9 Built-in functions 11.1 8 Discussion Point Worksheet 9608/21 Nov
12.1/14.1 2015 Q7a
Original material © Cambridge University Press 2019
Task 14.09 Questions 13 to 21 9608/22 Nov
(Worked Worksheet 2015 Q7a
Example 12.07) 12.2/14.2 9608/21 Jun
Discussion Point Question 1 2018 Q1a,b
Exam-style 9608/22 Jun
Question 14.2 2018 Q1a,b
9608/23 Jun
2018 Q1a,b
10 Stepwise 9.2 6 Worked Exercise 12.06 9608/21 Nov
refinement and 11.3 Example 12.10 Exercise 12.07 2015 Q6
modules Task 12.06 Exercise 12.08 9608/21 Jun
Worked Exercise 12.09 2015 Q2
Example 12.11 9608/21 Jun
Task 12.07 2016 Q3
Worked 9608/21 Nov
Example 12.12 2016 Q3
Task 14.10 9608/23 Nov
(Worked 2017 Q1a-c
Example 12.11) 9608/23 Nov
Task 14.11 2017 Q3a
(Worked
Example 13.05)
11 Parameters 11.3 9 Worked Exercise 12.10 9608/22 Nov
Example 12.13 2015 Q6
Task 14.12 9608/21 Jun
Discussion Point 2017 Q3
Exam-style 9608/22 Jun
Questions 14.3, 2017 Q3
14.4, 14.5, 14.6 9608/22 Jun
2017 Q4
Preparing for this chapter
Use the exercises in Worksheet 12.1/14.1 to get learners to write pseudocode first. They could also draw a
flowchart before coding their solutions in their chosen programming language.
If you are using Python, you might wish to introduce parameters sooner rather than later. This is because using
global variables in Python is tedious. Python was designed to use local variables by default.
You can set homework that consists of completing tasks that were started in class.
You will see that some of the flowcharts in this part include may include ‘Loop’ symbols within a circle. This is how
our recommended software Raptor produces these flowcharts, but the loop symbol will not be used in
examination papers so when drawing their own flowcharts, your students should omit the loop symbols.
Original material © Cambridge University Press 2019
Further reading
An excellent book for understanding the importance of algorithms is:
Algorithmics – The spirit of computing by David Harel (ISBN: 9780321117847)
To test flowchart solutions, the free software Raptor is excellent (http://raptor.martincarlisle.com/). Please note,
Raptor includes loop symbols in flowcharts which would be absent from flowcharts in examination papers.
Topic 1: Introduction to computational
thinking
Covering coursebook section 12.01 What is computational thinking?
Teaching guidance
Introducing the topic
You could have an introductory session that is a discussion or internet search about what the learners think
computational thinking is and why it is important.
Here is a link to a guide for teachers:
https://www.computingatschool.org.uk/computationalthinking
The Computing At School website has many other resources that teachers might find useful.
Engaging with the topic
Exercise 12.01
Discuss with learners what techniques might be used to solve a problem. They might give the following
suggestions:
Trial and error
Simulating a real system (for example, queuing at supermarket checkouts)
Similar problems with existing solutions
Divide and conquer (stepwise refinement)
Start with a simple part and build on that (bottom-up approach).
Original material © Cambridge University Press 2019
Topic 2: Introduction to algorithms
Covering coursebook sections 12.02 What is an algorithm? and 12.03 Expressing algorithms
Teaching guidance
Introducing the topic
It is important that learners understand the concept of an algorithm and that algorithms are not just used as a
step towards programming. Let learners think of other types of algorithms they have come across: knitting
patterns, steps in origami (paper folding), assembly instructions for a computer hardware system. Emphasise how
important it is that the steps are detailed enough to be followed successfully and that the steps are in the
correct order.
Engaging with the topic
Exercise 12.02
Use a map or a street plan and choose a starting point A and a destination B. Maybe start with a destination that
requires a simple route of four to five separate instructions and then try a destination that requires a more
complex route.
Write each instruction for getting from A to B on a separate piece of paper. Shuffle the pieces of paper and let
learners arrange the instructions into the correct order.
Choose another starting point X and another destination Y.
Get the learners to write instructions for how to get from X to Y.
Discuss as a class. Are all solutions the same? Are some solutions better than others? Are the instructions clear
enough to follow?
Now do Task 12.02 in the coursebook.
Use the algorithm of making a cup of tea (or coffee) from the Scheme Of Work to explain about selection
(do you take sugar?) and repetition (add some more sugar). Let learners draw a flowchart to represent
the algorithm.
Topic 3: The concept of variables
Covering coursebook section 12.04 Variables and 12.05 Assignments
Teaching guidance
Introducing the topic
It is very important that learners understand that the concept of a variable in computer science algorithms (and
programs) is different to the concept of a variable in mathematics. A simple way to visualise a variable in the
computer science context is to imagine computer memory consisting of a series of boxes. Each box can contain a
single value. If we want to use a value in one of these boxes, we refer to the name of the box.
Original material © Cambridge University Press 2019
Learners can imagine that an assignment means putting a value into the box. Putting a value into the box means
removing (overwriting) any value that was there previously. An assignment statement consists of an expression
on the right-hand side of the assignment operator and a variable identifier on the left-hand side of the
assignment operator. The expression on the right is evaluated and its result is assigned to the variable on the left.
Engaging with the topic
Exercise 12.03
If learners find variables a difficult concept, a role-play might help. Choose three learners to represent variables
(Value 1, Value 2 and Temp) and enact Figure 12.07 in the coursebook (swapping the values of two variables).
Before the role-play starts, make the following two assignments:
Value1 15 (give the learner playing the variable Value1 a card with 15 written on it)
Value2 34 (give the learner playing the variable Value2 a card with 34 written on it)
The learner playing the variable Temp can hold an empty card.
Now start the role-play:
Temp Value1 (the value shown on Value1’s card is written on Temp’s card)
Value1 Value2 (the value shown on Value2’s card is written on Value1’s card, covering up the previous value)
Value2 Temp (the value shown on Temp’s card is written on Value2’s card, covering up the previous value)
Now go through Worked Example 12.01.
Do Task 12.03.
Topic 4: Introduction to the programming
environment
Covering coursebook sections 14.01 Programming languages and 14.02 Programming basics
Introduction
The syllabus allows a choice between the following programming languages: Python, Visual Basic and Java.
The practical skills for Paper 4 build on the practical skills covered in Paper 2. It is therefore recommended that
learners choose the same high-level programming language for this paper as they do for Paper 2. This will give
learners the opportunity for extensive practice and allow them to acquire sufficient expertise.
Note that if Visual Basic is chosen, only VB.NET is appropriate for Paper 4 as this is the earliest version that
provides object-oriented programming features. VB6 and older versions are not appropriate.
Whether you decide to teach your learners Python, VB or Java might depend on your own expertise. It is
important that you are able to trouble-shoot learners’ programs when they get stuck and need help to find an
error (whether it is a syntax, a logic or a run-time error).
If you are new to programming yourself, you might wish to go for the newest language (Python 3). It is very easy
to install and currently very popular. Whichever language you choose, there are lots of websites for tutorials and
extra exercises (see the Scheme of Work for links).
Original material © Cambridge University Press 2019
Teaching guidance
Introducing the topic
Discuss the notes in the coursebook about your chosen programming environment, including:
How variables are declared (string data type only for now)
The syntax of assignment and input/output statements
Arithmetic operators.
Get learners to answer Question 14.01.
It is important that learners have hands-on experience of typing-in programs and getting them to run. They will
learn a lot from their mistakes if programs don’t run straight away due to syntax errors. In fact it might be a good
idea to give them some simple programs with deliberate mistakes to type in, so they get experience of how
syntax errors are reported, and how to spot an error and correct it.
Paper 2 for the 9618 syllabus requires learners to answer using pseudocode. This might lead to the idea that only
pseudocode needs to be taught. However, there is no way of reliably checking that a pseudocode algorithm is a
correct solution to a given problem. Therefore, it is highly recommended that learners have lots of experience of
writing, editing and running programs.
Engaging with the topic
Ask learners to do Task 14.01.
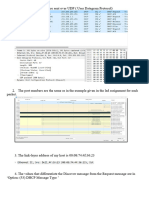
Exercise 12.04
For your chosen language, type in the code as displayed in the table. Use the comments in the table to explain the
resulting messages.
Python
1. EOL while
scanning
string literal
(quotes must
Figure 12.01 match)
The Prettyprint shows keywords and strings. There might be other syntax errors 2. Invalid syntax
that are reported one at a time when trying to run the module. highlighting
the second
quote on the
print line
(print
parameter
needs to be in
brackets)
3. Invalid syntax,
highlighting
yourName
Original material © Cambridge University Press 2019
(comma
required
between
separate print
list items)
4. NameError:
name
'yourName' is
not defined
(previously
used
YourName,
Python is
case-sensitive)
VB.NET
1. Underlined
variable name
because it is
not declared
2. Console.write
(bracket
underlined
with message
expression
Figure 12.02 expected)
The Prettyprint functionality helps the programmer to spot syntax errors. If auto- because
indent does not work, this suggests an error. double quotes
Auto-complete minimises misspelt keywords. required in VB
Errors are underlined and hovering the mouse pointer over the error shows 3. When
an explanation. running, the
name is not
output in the
message. This
is not because
the variable
name is not in
CamelCaps
(VB is not
case-sensitive)
but because a
comma is used
to separate
the print list
items. In VB,
use an &
Original material © Cambridge University Press 2019
Java
1. ; expected at
end of line 6
2. Unclosed
string literal
(double quote
required
in line 7).
3. Cannot find
symbol. Note
that String is
an object type
Figure 12.03 and therefore
Syntax errors are reported with a symbol in the left margin and red underline. must start
Hovering over the line shows the error message. with an
uppercase
letter. So line
8 needs to
read: String
yourName =
console.next();
4. In line 9
"package
system does
not exist" is
caused by the
lowercase
"system". This
is a very
common error .
5. Cannot find
symbol. Java is
case sensitive,
so yourName
and yourname
are different
identifiers.
6. No suitable
method found
(printlist
separator is a
+ not a
comma)
Original material © Cambridge University Press 2019
Topic 5: Data types
Covering coursebook sections 13.01 Data types and 14.03 Data types
Teaching guidance
Introducing the topic
At this point only introduce the simple data types: integer, real, char, string and Boolean.
Learners will already have used the string data type in Task 14.01. When you went through Worked Example
12.01 you would have used the integer and real data types. The next topic builds on the concept of
Boolean values.
Remind learners that some languages require variables to be declared before use (VB.NET and Java) whilst other
languages (Python) do not.
Engaging with the topic
Exercise 12.05
Show learners the pseudocode (in the table below) in the left column first. Let them guess what the program is
doing and how its readability might be improved. Discuss why it is useful to declare and name a constant (it aids
readability, but also it might be used in several places in a program, and if its value changes it only needs a change
in the declaration). Show them the program on the right.
INPUT x TAXRATE = 1.175 // tax rate may change
INPUT y INPUT ItemPrice1
INPUT z INPUT ItemPrice2
t (x+y)*1.175 - z INPUT VoucherAmount // amount to take off total
OUTPUT t ItemTotal ItemPrice1 + ItemPrice2
TotalToPay ItemTotal * TaxRate – VoucherAmount
OUTPUT TotalToPay
Discuss techniques for naming identifiers that aid readability (e.g. use of space, underscore, and uppercase
letters/CamelCaps). Often there are conventions for the use of names.
Discuss briefly the terms variable, constant, identifier, keyword (some languages use the term ‘reserved word’ for
keyword) and comment. Get learners to list all the variables, constants, identifiers, keywords and comments
present in the program. Check their answers, ensuring that the terms have been correctly understood.
Ask learners to do Task 14.02 now. Part 1 of this task looks at Worked Examples 12.02 to 12.11. It is appropriate
to discuss data types for these examples as they are encountered in later topics. You might wish them to only
look at identifier Table 12.02 for now. The other identifier tables can be covered later, when the programs are
written for them.
Ask learners to do Worksheet 12.1/14.1 Questions 1 and 2.
Opportunities for assessment
You could ask learners answer Exam-style Question 13.1.
Original material © Cambridge University Press 2019
Topic 6: Logic statements, Boolean expressions
and selection
Covering coursebook sections 12.06 Logic statements, 14.04 Boolean expressions, and 14.05 Selection
Teaching guidance
Introducing the topic
Learners sometimes have difficulty with more complex logic statements or changing from AND to OR.
Explain that:
For NOT(A AND B) to be TRUE is the same as for (NOT A) OR (NOT B) to be true. You might wish to show this using
a truth table:
A B A AND B NOT(A AND B) NOT A NOT B (NOT A) OR (NOT B)
TRUE TRUE TRUE FALSE FALSE FALSE FALSE
TRUE FALSE FALSE TRUE FALSE TRUE TRUE
FALSE TRUE FALSE TRUE TRUE FALSE TRUE
FALSE FALSE FALSE TRUE TRUE TRUE TRUE
This will be very important later on, when a post-condition loop might need changing to a pre-condition loop.
Engaging with the topic
Explain logic statements, then ask learners to do Task 12.04.
Go through the pseudocode for the number guessing game in Section 12.06 to show simple and complex
conditions.
Go through Worked Example 12.02. Ask Question 12.01.
Go through Worked Example 12.03.
Introduce the Boolean operators applicable for your chosen programming language. Explain the syntax of IF
statements for your programming language.
Ask learners to do Task 14.03.
When learners start to write programs with selection, it is time to introduce testing. Learners should decide what
the expected results are for their chosen test data before they run their program.
Discuss with learners how to choose suitable test data (normal, borderline and abnormal).
Normal data: data within the range of values the program should work with.
Borderline data: data at the extreme end of the range, just outside and just inside the boundary.
Sometimes we also need to look at extreme data values: very large or very small values.
Abnormal data: values the program should not accept.
Original material © Cambridge University Press 2019
Learners often confuse borderline and extreme data, and abnormal data, so you should mention this every time
they choose test data.
Explain the concept of nested IF statements and their syntax.
Ask learners to do Task 14.04.
Ask learners to do Worksheet 12.1/14.1 Questions 3 and 4.
Topic 7: The CASE construct
Covering coursebook section 14.05 Selection
Teaching guidance
Introducing the topic
Introduce the CASE statement as an alternative to nested IF statements. Learners should avoid using nested IF
statements when CASE statements are more appropriate. Python programmers need to use the IF ELIF
construct instead.
Give learners the syntax for the CASE statement.
Engaging with the topic
Ask learners to do Task 14.05.
Ask learners to do Worksheet 12.1/14.1 Questions 5.
Topic 8: Iteration
Covering coursebook sections 12.07 Loops and 14.06 Iteration
Teaching guidance
Introducing the topic
Learners sometimes find the concept of iteration difficult. Introducing trace tables (See coursebook Section 15.06)
and variable watch windows in a debugger can help learners to visualise what happens and help them
understand.
Engaging with the topic
Introduce FOR loops first. Go through Worked Example 12.05.
Go through dry-runs first on pseudocode without errors. Later show dry-running being used to find an error in the
program code.
Original material © Cambridge University Press 2019
Insist that pseudocode is indented correctly within a loop. Perhaps use a worked example but without
indentation to show how readability decreases without indentation.
Go through Worked Examples 12.08 and 12.09.
Introduce the syntax of a FOR loop.
Ask learners to do Task 14.06 and Worksheet 12.1/14.1 Questions 6 to 10.
Introduce conditional loops. Go through Worked Example 12.04. Ask Question 12.02.
Introduce the syntax for a WHILE loop.
Ask learners to do Tasks 12.05 and 14.08.
Go through Worked Example 12.04.
Introduce the syntax for a REPEAT loop.
Note that Python does not have a post-condition loop. You need to show how to work around this using a WHILE
loop and statements before entering the loop.
Ask learners to do Task 14.07.
Go through Worked Example 12.07. Learners should program this using a fixed number as the secret number
(random numbers are introduced in topic 9).
Ask learners to do Worksheet 12.1/14.1 Questions 11 and 12 first using a WHILE loop then a REPEAT loop.
Introduce nested loops. Go through Worked Example 12.09. Encourage learners to program this.
Opportunities for assessment
You could get your learners to tackle Exam-style Questions now or as an end-of-unit test.
Topic 9: Built-in functions
Covering coursebook section 14.07 Built-in functions
Teaching guidance
Introducing the topic
Remind learners that the ASCII and CHAR functions reinforce the idea that strings are actually stored as a series of
(binary) numbers and that comparison of characters is the comparison of their (binary) codes. Consequently it is
possible to perform a comparison between ‘2’ and ‘a’ and get a valid result.
Engaging with the topic
Ask learners to write a simple program that reads in a character and outputs the next or previous letter in the
alphabet by adding or subtracting from the ASCII value and converting back into a character.
Let learners explore the difference between for example the number 2 and the character 2 by outputting the
ASCII value of a digit.
Ask learners to do Worksheet 12.1/14.1 Question 13 and Worksheet 12.2/14.2 Question 1.
Original material © Cambridge University Press 2019
Ask learners to do Task 14.09 parts 1 and 2 (using a random number generator).
Ask learners to do Worksheet 12.1/14.1 Questions 14 to 22.
Explore other built-in functions available in the chosen programming environment. Also explore libraries that
need to be imported (for example the datetime library in Python).
Give your learners practical experience of reading the technical information on library routines and then using
routines.
Which built-in functions are available depends on the programming environment. The functions the learners need
to be familiar with are listed in the coursebook.
Python Docs provides help. Choose: library reference, built-in functions to get the following page:
Figure 12.04 Python Docs library reference
Using the Internet to find information about built-in functions is another method.
The link https://msdn.microsoft.com/en-us/library/32s6akha.aspx accesses the Microsoft Visual Studio 2015
website with links to various VB.NET built-in functions and how to use them.
Original material © Cambridge University Press 2019
Figure 12.05 Microsoft Developer Network
Differentiation
Challenging learners
Ask learners to do Worksheet 12.1/14.1 Question 18.
Original material © Cambridge University Press 2019
Topic 10: Stepwise refinement and modules
Covering coursebook sections 12.08 Stepwise refinement, 12.09 Modules, 14.08 Procedures, and 14.09 Functions
Teaching guidance
Introducing the topic
After completing Worked Example 12.10 and Task 12.06, let learners tackle each of the following exercises. For
each exercise, learners should return to the pseudocode from the previous exercise. They should amend the
pseudocode before changing their program to solve the enhanced problem.
Engaging with the topic
Exercise 12.06
Introduce a simple problem. For example, the following word-guessing game:
Player A chooses a secret word. Player B tries to guess the word. If Player B guesses the word correctly, the
message ‘Well done’ is output, otherwise the message ‘Sorry, incorrect’ is output and Player B gets another
chance to guess the word. Output the number of guesses it takes before Player B guesses the word. If after ten
guesses Player B has still not guessed the word, stop the game and output the secret word.
Let learners write the solution in structured English or pseudocode and/or draw a flowchart. Then they can code
the solution using their programming language.
Exercise 12.07
Ask learners to enhance the word-guessing game. Instead of Player A choosing a secret word, the program
generates a random number and uses this number to read a word from a text file of words.
Introduce two players taking turns to guess the word.
Go through Worked Example 12.11. Ask learners to do Task 12.07.
Go through how to declare procedures in the chosen programming language using the example in Section 14.09.
Ask learners to do Task 14.10.
Exercise 12.08
You could ask learners to make some of their earlier programs into modules with a menu to let the user choose
which program to run. For example, a Module ‘Show Menu’ could produce the following prompt:
1 Convert from km to miles
2 Convert inches into cm
3 Number guessing game
Enter your choice (1, 2 or 3):
The program should validate the input and then use a CASE statement to call the relevant module.
Before the learners add the program code for each of the modules, they should test that the menu system works
by outputting a message to confirm the choice. For example, if the user typed in 2, the stub testing should
produce the output ‘Convert inches to cm called’.
Original material © Cambridge University Press 2019
Go through Worked Example 12.12. This builds on the same example as Worked Example 12.11 but uses
functions instead of some of the procedures. This then allows discussion about the difference between local and
global variables.
Go through how to declare functions in the chosen programming language using the example in Section 14.10.
You could ask learners to continue to do Task 14.11.
Differentiation
Challenging learners
Exercise 12.09
Change the word-guessing game for one player by asking the player to guess just a single letter. If the letter does
not exist in the secret word, the player increases their penalty score. The program should show a symbol for each
letter of the word and when a letter has been guessed, this is shown. For example, if the secret word is
COMPUTER and the player has guessed the letter P, the program outputs ###P####. The game continues until the
word has been guessed. The output is the penalty score. Remove the limit on the number of guesses.
Topic 11: Parameters
Covering coursebook sections 14.10 Passing parameters to subroutines, 14.11 Passing parameters to functions,
14.12 Passing parameters to procedures, and 14.13 Putting it all together
Teaching guidance
Introducing the topic
Remind learners that they have met parameters already when using built-in functions (Topic 9). For example, the
function header of the pseudocode function:
LENGTH(ThisString : STRING) RETURNS INTEGER
shows that this function takes one parameter of data type STRING. The identifier ThisString is known as a
formal parameter. It will be replaced by the actual parameter when the function is called. Similarly, procedure
headers can have a parameter list with one or more parameters and the formal parameter(s) will get replaced by
actual parameters when the procedure is called.
Note: For ease of understanding, examples in the exercises use the same identifiers for formal and actual
parameters, but this is not a requirement.
Engaging with the topic
Exercise 12.10
Explain scope, call by value and call by reference using the pseudocode and programs below.
Include the underlying mechanisms:
Call by value
o creation of local variable and value copied to it
Original material © Cambridge University Press 2019
o no change to original variable value in call by value whatever changes are made to local variable copy
Call by reference
o two labels to the same item of data
o any change to local variable in call by reference changes original variable value.
Pseudocode
Get learners to work out what the output will be for each of the three programs. Then use the example code
for the programming language of your choice. Produce a handout with the relevant code. Let learners check
whether they predicted the output correctly.
Program Scope1 uses global variables throughout.
Program Scope2 uses local variables but no parameters.
Program Scope3 uses local variables in PROCEDURE C and parameters for PROCEDURE A and PROCEDURE B.
Note the difference between value and reference parameters.
PROGRAM Scope1 PROGRAM Scope2 PROGRAM Scope3
DECLARE X : INTEGER
DECLARE Y : INTEGER
PROCEDURE A PROCEDURE A PROCEDURE A(BYREF X :
X 5 DECLARE X : INTEGER INTEGER)
OUTPUT X X 5
X 5
ENDPROCEDURE OUTPUT X
OUTPUT X
ENDPROCEDURE
ENDPROCEDURE
PROCEDURE B PROCEDURE B(BYVALUE Y :
PROCEDURE B
INTEGER)
Y 7 DECLARE Y : INTEGER
OUTPUT Y Y 7
Y 7
ENDPROCEDURE OUTPUT Y OUTPUT Y
ENDPROCEDURE ENDPROCEDURE
PROCEDURE C PROCEDURE C PROCEDURE C
X 1 DECLARE X : INTEGER DECLARE X : INTEGER
Y 2 DECLARE Y : INTEGER DECLARE Y : INTEGER
OUTPUT X, Y X 1 X 1
CALL A Y 2 Y 2
CALL B OUTPUT X, Y OUTPUT X, Y
OUTPUT X, Y CALL A CALL A(X)
ENDPROCEDURE CALL B CALL B(Y)
OUTPUT X, Y OUTPUT X, Y
ENDPROCEDURE ENDPROCEDURE
Original material © Cambridge University Press 2019
CALL C CALL C CALL C
ENDPROGRAM ENDPROGRAM ENDPROGRAM
Python
Note that global variables have to Variables are local to the Parameters in Python are always
be declared as such in each procedure they are used in, unless passed by value. If you want to use
procedure. declared as global. the equivalent of reference
parameters you need to return
value(s). In effect, the subroutine is
used like a function.
def A(): def A(): def A(x):
global x x = 5 x = 5
x = 5 print("in A: ", x) print("in A: ", x)
print("in A: ", x) return x
def B(): def B(): def B(y):
global y y = 7 y = 7
y = 7 print("in B: ", y) print("in B: ", y)
print("in B: ", y) return y
def C(): def C(): def C():
global x, y x = 1 x = 1
x = 1 y = 2 y = 2
y = 2 print("in C, initial: print("in C, initial:
print("in C, initial: ", x, y, sep=' ') ", x, y, sep=' ')
", x, y, sep=' ') A() A(x)
A() B() y = B(y)
B() print("in C, final: print("in C, final:
print("in C, final: ", x, y, sep=' ') ", x, y, sep=' ')
", x, y, sep=' ')
C() C() C()
VB.NET
Module Module1 Module Module1 Module Module1
Dim X As Integer
Dim Y As Integer
Sub A() Sub A() Sub A(ByRef X As
X = 5 Dim X As Integer Integer)
Console.WriteLine(X) X = 5 X = 5
End Sub Console.WriteLine(X) Console.WriteLine(X)
End Sub End Sub
Sub B() Sub B()
Y = 7 Dim Y As Integer Sub B(ByVal Y As Integer)
Console.WriteLine(Y) Y = 7 Y = 7
End Sub Console.WriteLine(Y) Console.WriteLine(Y)
End Sub End Sub
Sub C() Sub C()
X = 1 Dim X As Integer Sub C()
Y = 2 Dim Y As Integer Dim X As Integer
X = 1 Dim Y As Integer
Original material © Cambridge University Press 2019
Console.WriteLine(X & Y = 2 X = 1
" " & Y) Console.WriteLine(X & Y = 2
A() " " & Y) Console.WriteLine(X &
B() A() " " & Y)
Console.WriteLine(X & B() A(X)
" " & Y) Console.WriteLine(X & B(Y)
End Sub " " & Y) Console.WriteLine(X &
End Sub " " & Y)
End Sub
Sub Main() Sub Main()
Sub Main() C() C()
C() Console.ReadLine() Console.ReadLine()
Console.ReadLine() End Sub End Sub
End Sub
End Module End Module
End Module
Java
Parameters in Java are always
passed by value. If you want to use
the equivalent of a reference
parameter you need to return the
value. In effect, the subroutine is
used like a function.
import import import
java.util.Scanner; java.util.Scanner; java.util.Scanner;
public class Main public class Main public class Main
{ { {
static int x;
static int y;
public static void a() public static void a() public static int a(int x)
{ { {
x = 5; int x = 5; x = 5;
System.out.println("in System.out.println("in System.out.println("in
A: " + x); A: " + x); A: " + x);
} } return x;
}
public static void b() public static void b() public static void b
(int y)
{ { {
y = 7; int y = 7; y = 7;
System.out.println("in System.out.println("in System.out.println("in
B: " + y); B: " + y); B: " + y);
} } }
Original material © Cambridge University Press 2019
public static void c() public static void c() public static void c()
{ { {
x = 1; int x = 1; int x = 1;
y = 2; int y = 2; int y = 2;
System.out.println("in System.out.println("in System.out.println("in
C, initial: " + x + " C, initial: " + x + " C, initial: " + x + "
" + y); " + y); " + y);
a(); a(); x = a(x);
b(); b(); b(y);
System.out.println("in System.out.println("in System.out.println("in
C, final: " + x + " " C, final: " + x + " " C, final: " + x + " "
+ y); + y); + y);
} } }
public static void public static void public static void
main(String[] args) main(String[] args) main(String[] args)
{ { {
c(); c(); c();
} } }
} } }
Ask learners to do Task 14.12.
Exercise 12.10
Encourage learners to produce a fully working program for the pyramid-drawing task.
Supporting learners
You could encourage learners who find this difficult to have a look at the detail in Section 14.14.
Original material © Cambridge University Press 2019
Worksheet 12.1/14.1: for testing basic
understanding
1 Write a program that will take as input the length and width of a rectangular garden and will calculate and
output the surface area.
2 Write a program that will take as input a temperature in degrees Fahrenheit and will convert and output the
temperature in degrees Celsius.
(Hint: DegreesC = (DegreesF – 32) * 5/9)
3 Write a program that will take as input the air temperature in degrees Celsius and will output a message to
say whether it is freezing (below 1 degree) or not.
4 Amend your program from Question 3 to say whether the water in a container is frozen, liquid or boiling.
5 Write a program that will take as input an integer between 1 and 12 (inclusive). The program should output
the name of the month corresponding to the number input. For example, an input of 2 will output ‘February’.
Hint: use a CASE statement.
6 Write a program that will take as input a positive integer and will output integers counting from 1 to the
number input. For example, an input of 5 will output: 1 2 3 4 5
7 Amend your program from Question 6 to count down from the number input to 1. For example, an input of 5
will output: 5 4 3 2 1
8 Amend your program from Question 9 to take as input a second integer to be used as the counting interval.
For example, the input of 20, 4 will output: 1 5 9 13 17
9 Write a program that will take as input ten numbers and output the largest number.
10 Amend your program from Question 9 to output the smallest number.
11 Write a program that asks the user for an integer between 1 and 5 (inclusive). The program should check that
the input is within the range and if not, prompt the user for a valid integer until the input is within the range.
12 Write a program that will take as input two positive integers. The program should output integers counting
from the first integer to the second integer. For example, the input 3, 7 will output: 3 4 5 6 7
13 Write a program that will take as input a character and output the ASCII code for that character.
14 Write a program that will take as input an ASCII code. The program is to output the character with that
ASCII code.
15 Write a program that will take as input a string and output the number of characters in the input string.
16 Write a program that will take as input a string and output the two leftmost characters.
17 Amend your program from Question 16 to output the two rightmost characters.
18 Write a program that takes as input a string. The program is to calculate the middle position and output the
middle character. If the string length is an even number the two middle characters are to be output.
19 Write a program that will take two input strings: a first name and surname. The program should produce the
full name by concatenating the first name and surname with a space in between them then to output the full
name.
20 Amend your program from Question 19 to produce a name string made up from the first letter of the first
name, a space and the surname.
Original material © Cambridge University Press 2019
21 Write a program that will take as input a number with a decimal point and output the nearest whole number.
22 Write a program that generates and outputs five random numbers. Run the program several times to ensure
they are not the same numbers each time.
Original material © Cambridge University Press 2019
Teaching guidance
Part 2: Fundamental problem solving and
programming skills
Chapter 13: Data types and structures
Chapter 14: Programming and data
representation
Main aims
To enable learners to:
manipulate standard (built-in) data structures
manipulate abstract data structures
learn standard algorithms for searching, sorting and file handling.
It is suggested that Chapter 13 is worked through in parallel with Chapter 14 (Sections 14.14 and 14.15).
Possible programme of study Resources
Topics Syllabus Suggested Resources in the Resources in Past-paper
section number of coursebook this guide questions
40 min.
lessons
1 Records 10.1 2 Task 13.02 Exercise 13.01
Exercise 13.02
2 1D arrays 10.2 4 Worked Example 13.01 Worksheet
Task 13.03 13.1/14.1
Task 14.13.1 Questions 1, 2 & 3
Task 13.07
3 Searching and 10.2 4 Worked Example 13.02 Exercise 13.03 9608/22 Nov
sorting Task 13.04 Exercise 13.04 2017 Q2
Task 14.13.2 Exercise 13.05
Worked Example 13.03
Task 13.05
Task 14.13.3
Exam-style
Question 13.3
Original material © Cambridge University Press 2019
4 2D arrays 10.2 8 Worked Example 13.04 Worksheet 9608/21 Jun
Task 13.06 13.1/14.1 2018 Q6
Worked Example 13.05 Questions 4 & 5 9608/22 Jun
Task 14.14 part 1 2018 Q6
Task 14.14 part 2 9608/23 Jun
2018 Q6
9608/22 Nov
2015 Q4
5 Text files 10.3 8 Task 13.08 Worksheet 9608/21 Jun
Task 14.15 13.1/14.1 2017 Q2
Questions 6 & 7 9608/22 Jun
Worksheet 2017 Q2
13.2/14.2 9608/21 Nov
Question 1 2017 Q5
9608/22 Nov
2017 Q5
9608/21 Jun
2018 Q5
9608/22 Jun
2018 Q7
9608/23 Jun
2018 Q5
6 Stacks and 10.4 4 Task 13.09
queues Task 13.10
Exam-style
Question 13.2
7 Linked lists 10.4 5 Task 13.11 Exercise 13.06
Exercise 13.07
Exercise 13.08
Preparing for this chapter
Homework should consist of finishing off programs started in class.
The syllabus for 9618 requires pseudocode answers for Paper 1. For Paper 4, learners are required to be able to
program. It is advisable that learners have plenty of practical experience of programming as it will help their
understanding and skill level for writing solutions using pseudocode.
Further reading
An excellent facility for demonstrating different sorting algorithms can be found at:
http://www.sorting-algorithms.com/
Very good notes and diagrams for abstract data types can be found at:
http://www.teach-ict.com/as_as_computing/ocr/H447/F453/3_3_5/data_structures/miniweb/index.htm
Original material © Cambridge University Press 2019
Topic 1: Records
Covering coursebook section 13.02 The record type
Teaching guidance
Introducing the topic
Some learners might find declaring a user-defined type difficult. The concept of a record type could be compared
to designing a form to collect data about a particular person, thing or event. The dot notation might need more
explanation: the identifier before the dot is the person/thing/event. The identifier after the dot is the field (the
label of the box if it is a paper form to be filled in).
Here are some examples for ‘forms’:
Forms to enter data about job vacancies (job title, company, hourly rate of pay, hours)
Forms to enter data about events held at a public venue (date, event title, ticket price, duration in hours)
Forms to enter data about goods stocked in a shop (item description, item code, price, number of items in stock).
Engaging with the topic
You could ask learners to do Task 13.02.
Exercise 13.01
Ask learners to design a form for data to be held about one of the above examples. The boxes for the information
to be entered should have concise labels. Using pseudocode, they need to declare a record type with fields to
store the data. Then they should decide on some example data for one or two items. Using pseudocode, ask them
to write variable declarations and assignment statements for these fields.
Exercise 13.02
Ask learners to use their programming language to write programming statements from the pseudocode
generated in Exercise 13.01. Output statements should be added to ensure the data is stored correctly.
Topic 2: Arrays
Covering coursebook sections 13.03 Arrays, 13.04 One-dimensional arrays, and 14.14 Arrays
Teaching guidance
Introducing the topic
Introduce the concept of an array structure using Worked Example 13.01.
Explain the pseudocode syntax for declaring and using an array. Ask learners to do Task 13.03.
Now explain the syntax for arrays in the chosen programming language.
Original material © Cambridge University Press 2019
Engaging with the topic
Ask learners to convert their pseudocode for Task 13.03 into program code.
Ask learners to do Task 14.13 Part 1.
Ask learners to do Worksheet 13.1/14.1 Questions 1 to 3. These could be done using pseudocode first.
Introduce the concept of arrays of user-defined types: arrays of records.
Differentiation
Challenging learners
Ask learners to do Task 13.07.
Topic 3: Searching and sorting
Covering coursebook sections 13.04 One-dimensional arrays and 14.14 Arrays
Teaching guidance
Introducing the topic: Searching
Introduce the concepts of linear search and how the algorithm can be efficiently designed when using a 1D array
and a loop.
Go through Worked Example 13.02.
Engaging with the topic
Ask learners do Task 13.04 and Task 14.13 part 2.
Introducing the topic: Sorting
Introduce the concepts of bubble sort and let learners use cards with different numbers and manually work
through the process.
Go through Worked Example 13.03.
Engaging with the topic
Ask learners to do Task 14.14 part 3.
Ask learners to do Task 13.05.
Ask learners to attempt to write the algorithm of the previous exercise from memory.
Original material © Cambridge University Press 2019
Exercise 13.03
Provide learners with a detailed algorithm to dry-run recording their steps in a trace table (See Chapter 15,
section 15.06). This will reinforce their understanding of the mechanism of a bubble sort.
Exercise 13.04
Ask learners to write their own programs from the most efficient bubble-sort algorithm and test their programs.
This is a good example of where a variable watch could be used to check that the program is sorting or
searching correctly.
Opportunities for assessment
You could ask learners to do Exam-style Question 13.3.
Differentiation
Challenging learners
Exercise 13.05
You can encourage learners to write programs for each of the bubble sort algorithms shown in Worked Example
13.03 and include output statements at the beginning of each loop to trace the progress of each algorithm. Then
different data sets can be used to demonstrate how the two algorithms behave.
Let learners summarise the essential characteristics of the bubble sort and linear search algorithms:
Bubble sort
Starting at the top of the list, work down the list comparing adjacent items, swapping them if they are in the
wrong order. This is done repeatedly. With each iteration of the outer loop the next largest item moves into its
final position. For efficiency there is one item fewer in the comparison each time round the outer loop. If no
swaps have been made during one whole iteration of the outer loop, the list is sorted.
Linear search
Start at the beginning of the list. Compare each item until the wanted item is found. This can be used on an unordered
list.
Ask learners to write program code for their solution to Exam-style Question 13.03.
Topic 4: 2D arrays
Covering coursebook sections 13.03 Arrays, 13.05 Two-dimensional arrays, and 14.14 Arrays
Teaching guidance
Introducing the topic
Introduce pseudocode syntax for 2D arrays.
Go through Worked Example 13.04.
Introduce programming language syntax for 2D arrays.
Original material © Cambridge University Press 2019
Engaging with the topic
Ask learners to do Task 13.06, then Worksheet 13.1/14.1 Questions 4 and 5 using pseudocode.
You can use Worked Example 13.05 to reinforce use of 2D arrays as well as step-wise refinement and use
of modules.
Ask learners to do Task 14.14 Part 1.
Differentiation
Challenging learners
Ask learners to do Task 14.14 part 2.
You could ask learners to write program code for Task 13.06, Worksheet 13.1/14.1 Questions 4 and 5.
Topic 5: Text files
Covering coursebook sections 13.06 Text files
Teaching guidance
Learners often find file handling quite difficult. Lots of practice is required! Although in the Paper 2 exam learners
will be required to use the pseudocode statements for file handling solutions, real understanding will be easier to
develop if learners have practical experience of programming file handling. Opening a file in a text editor to check
that their program has successfully written to the file is an important learning process.
Introducing the topic
First look at the pseudocode file handling statements and explain that a file needs to be opened in the correct
mode before reading/writing/appending. A file needs to be closed before the program stops or the file might
be corrupted.
The pseudocode for reading a file until the end of the file is reached uses the End-of-File (EoF) function. Learners
often misunderstand how the EoF function works. This function returns a Boolean value: FALSE if the end of the
file has not yet been reached, TRUE if the end-of-file marker (present in the file) has been reached.
However, different programming environments use different methods. See Section 14.15 for details of the chosen
programming language.
Discuss the programming language syntax of the file operation statements to clarify how they work in the chosen
programming language. It might be beneficial to look at the file before and after a number of operations have
been carried out on it. This should help learners to understand the file operations better and how the text lines
are actually stored.
Remember text files can be created and read using a text editor, such as Notepad, to check the successful
operation of a file-handling program.
Ensure the text file is stored locally or explain to learners how to add the file path of the data file
(for example “C:/Tally.TXT”).
For Python programs, the file location is the same as the program source file.
Original material © Cambridge University Press 2019
For VB.NET programs the file location is within the Debug folder in the bin folder of the source code location.
For Java programs the file location is the top level of the project folder.
Engaging with the topic
Ask learners to do Worksheet 13.1/14.1 Questions 6 and 7.
Ask learners do Task 14.15.
Differentiation
Challenging learners
Ask learners to do Worksheet 13.2/14.2 Question 1.
Topic 6: Stacks and queues
Covering coursebook sections 13.07 Abstract Data Types, 13.08 Stacks, and 13.09 Queues
Teaching guidance
Introducing the topic
For Paper 2, learners are not required to write pseudocode for these structures, but they should be able to add,
edit and delete data from these structures.
The diagrams in the coursebook show a stack with the first element at the bottom of a vertically drawn set of
boxes. To ensure learners are able to adjust pointer(s) correctly when pushing a data item onto a stack or popping
a data item off a stack, diagrams could be presented in different orientations, such as a stack with boxes drawn
across the page or the base of the stack as the first element in a vertical set of boxes.
Engaging with the topic
Ask learners to do Task 13.09.
The mechanism for data items joining a queue and leaving a queue depend how the front of the queue is set up.
To help learners visualise this, cards with data written on them could be laid onto a sheet of paper with an empty
grid and two cards acting as front of queue and end of queue pointers, respectively.
You could ask learners to do Task 13.10.
Opportunities for assessment
Ask learners to complete Exam-style Question 13.02.
Original material © Cambridge University Press 2019
Topic 7: Linked lists
Covering coursebook sections 13.10 Linked lists
Teaching guidance
Introducing the topic
It is very important that learners understand the concept of a linked list. It might help to have lots of cards that
look like nodes in the diagrams in the coursebook, with data items on them. Learners find it easier to order
numeric data, rather than alphabetical data, so some random numbers on the cards would be good.
Get learners to use pieces of string to represent pointers.
Exercise 13.06
You could ask learners to practise adding nodes in the correct place to the linked list.
The position of the nodes should not change, only the way they are connected using the ‘string pointers’.
Ask learners how an empty list might be represented.
You can then encourage learners to derive algorithms for the following cases:
1 adding an item to an empty list
2 adding an item to the beginning of a non-empty list
3 adding an item to the end of a non-empty list
4 adding an item within a non-empty list
5 removing the only item from a list
6 removing an item from the end of a list with more than one item
7 removing an item from the beginning of a list with more than one item
8 removing an item from within a list with more than two items.
Engaging with the topic
Ask learners to do Task 13.11.
Introduce the concept of nodes being represented as records and stored in an array. For illustration, a record
consists of just the key field and the pointer field.
Exercise 13.07
Discuss with learners how a stack is a special type of linked list. Which of the cases 1 to 8 are not required if the
linked list is to be used like a stack?
Exercise 13.08
Discuss with learners how a queue is a special type of linked list. Which of the cases 1 to 8 are not required if the
linked list is to be used like a queue?
Original material © Cambridge University Press 2019
Worksheet 13.1/14.1: for testing basic
understanding
1 Write a program to initialise an array with ten elements. Each element is to contain the number 0.
The program should output the contents of the array.
2 Amend your program from Question 1 so the first element contains 1, the second element contains 2,
and so on.
3 Amend your program from Question 1. After initialisation the program should ask repeatedly for an integer
between 1 and 10 until the input is terminated by 0. For each input, the relevant array element content
should be increased by 1. For example, if the input is 5, the fifth element should be incremented by 1.
4 Write a program to initialise a 5 × 5 array. Each element should contain the number 0. The program should
output the contents of the array.
5 Amend your program from Question 4. After initialisation the program should ask repeatedly for two integers
between 1 and 5 until the input is terminated by 0. The two input numbers should be used as coordinates
(row number followed by column number) and the contents of the relevant array element is to be increased
by 1.
For example, if the first two input numbers are 2 and 3, the array contents should be:
00000
00100
00000
00000
00000
6 Create a text file with several lines of text in a text editor (for example NotePad).
Write a program to read this text file and output the contents.
7 Amend your program from Question 6 to output the text from the first text file to another text file. Open the
newly created text file in a text editor to check the program worked successfully.
Original material © Cambridge University Press 2019
Worksheet 13.2/14.2: more challenging
questions
1 Amend your program from Worksheet 13.1/14.1 Question 6 to add another line of text to the text file
(append). Check in the text editor that the program worked successfully.
Original material © Cambridge University Press 2019
Chapter 1: Information Representation:
Answers to coursebook questions and
tasks and to Worksheet questions
Syllabus sections covered: 1.1, 1.2 & 1.3
From the coursebook
Task 1.01
Denary 96 becomes hexadecimal 60
Denary 215 becomes hexadecimal D7
Denary 374 becomes hexadecimal 176
The following table shows the binary equivalent followed by the hexadecimal for the three denary values.
256 128 64 32 16 8 4 2 1
0 0 1 1 0 0 0 0 0
For 96
6 0
1 1 0 1 0 1 1 1
For 215
D 7
1 0 1 1 1 0 1 1 0
For 374
1 7 6
For 96 learners might recognise that 96 is 6 x 16 and so the conversion to the hexadecimal 60 can be done
immediately.
The slow but steady route can be illustrated for the conversion of 374. The initial conversion to binary uses
successive division by two, noting the remainder each time and then reversing the remainders.
The remainders are 0 1 1 0 1 1 1 0 1 which in reverse give the binary as: 101110110. For conversion to
hexadecimal, groupings of four bits are converted starting at the least significant (RH) end. The 0110 converts to
6, the 0111 to 7 so the hexadecimal representation is 176.
The more advanced students might use a short cut. Noting that 374 is greater than 162 a three-digit hexadecimal
representation is expected. Calculating 374 – 256 leaves 118. This can be seen to consist of 7 16s with 6
remaining, hence 176.
Hexadecimal B4 becomes denary 180
Hexadecimal FF becomes denary 255
Original material © Cambridge University Press 2019
Hexadecimal 3A2C becomes denary 14892
The conversion of B4 and FF by first converting each hexadecimal digit to a corresponding 4-bit binary
representation is illustrated in the following table.
128 64 32 16 8 4 2 1
For B4 B 4
1 0 1 1 0 1 0 0
For FF F F
1 1 1 1 1 1 1 1
For B4 the binary then converts to 128 + 32 + 16 + 4
For FF the binary then converts to 128 + 64 + 32 + 16 + 8 + 4 + 2 + 1
For FF learners might remember that the maximum value that can be stored in 8 bits is 255 so the working out is
not needed.
The same approach could be used for converting 3A2C but an alternative is to use the equivalent of the method
illustrated in Worked Example 1.01. The calculation proceeds from left to right as follows: 3 x 16 = 48 then + 10 =
58 then x 16 = 928 then + 2 = 930 then x 16 = 14 880 then + 12 = 14 892.
You can reassure your learners that conversion to denary for more than two hexadecimal digits would not be
expected in an exam question. Calculators are not allowed in exams so more than two hexadecimal digits would
be unfair.
Question 1.01
Internally never: hexadecimal numbers are primarily used for representation of binary codes for a person to read.
A computer can, therefore, create hexadecimal representations for output. Alternatively, they could possibly be
used for input provided that they were to be converted immediately to binary.
Task 1.02
Table 1.08 in the coursebook shows the binary value for -7 to be 1001. (You could note that there could have
been any number of leading bits set to 1 without the conversion being affected other than to produce leading
zeros in the final answer). Using the method of retaining the least significant bit and switching the others gives
0111 which is +7.
Task 1.03
1011 = -23 + 21 + 20 = -8 + 2 + 1 = -5
111011 = -25 + 24 + 23 + 21 + 20 = -32 + 16 + 8 + 2 + 1 = -5
Original material © Cambridge University Press 2019
Task 1.04
The method is to take the two’s complement of the binary value for 35 and to add this to the binary value for 67.
The binary equivalent of denary 35 is 00100011, conversion to two’s complement gives 11011101. Binary for 67 is
01000011. Addition gives (1)00100000. Students should note that there is a carry bit that cannot be stored in the
byte but this does not matter because the result in the byte is the binary code for denary 32, the correct answer.
Question 1.02
6 bits only allows 64 codes. Including both upper case and lower case letters would use up 52 of these. Thus, only
upper case letters were coded.
Task 1.05
Suitable examples would be:
Circle, centre coordinates, radius, outline colour, outline style, fill colour.
Rectangle, coordinates of the bottom left corner, coordinates of bottom right corner, length, outline colour,
outline style, fill colour.
Extension Question 1.01
This is an open-ended question. Learners should be advised not to concern themselves too much with the details
of the methods, just a name would suffice. However, they should be finding out at least whether the compression
is lossless or lossy.
Exam-style Questions
(with mark allocation in brackets):
1 a i 38 195 from 215 + 212 and so on (1 + 1)
ii 9533 from 4-bit groupings (1 + 1)
b Any example involving presentation of a hexadecimal representation of a binary code to make it easier for
someone to read (1).
c i 10010101 because the most significant LHS bit is 1 (1).
ii -107 from -27 + 24 and so on and 51 from 25 + 24 and so on (1 + 1).
d Only one representation of zero. Allows simple computation for addition and subtraction. (1 + 1)
e Many options here, some possibilities (1 each, max 3) are:
BCD values either two per byte or just one per byte using just four bits
Two ASCII characters either using seven bits from each byte or using the full byte including a parity bit
One Unicode character using the two bytes
Original material © Cambridge University Press 2019
Bitmap code with any variation from 16 single-bit pixels for black and white through two pixels with
each byte representing one of 256 colour codes to the two bytes representing a colour depth of 16
Values for sampled sound, sensibly using four bits, one byte or two bytes to represent one sampled
value
A machine code instruction using the two bytes
A memory address using both bytes
Although not yet covered in the syllabus a floating-point representation.
2 a i There are many credit-worthy options such as mention of drawing list, individual objects, properties,
attributes, geometric data or by example (1 each, max 2).
ii ‘Uses a matrix of pixels’ is a sufficient answer but also creditworthy would be to state that a pixel has a
colour and a position (1 for pixel + 1 added comment).
iii Vector graphic. This should be justified by saying there is a re-calculation for the magnified image;
might get credit for saying that a bitmap becomes pixelated on magnification or that a vector graphic
does not. (1 for vector graphic + 1 for reason)
b i 640 x 480 = 307 200 pixels; each pixel has 16 bits which is two bytes. The best continuation is to divide
2 x 307 200 by 1024 to get 600 KiB. An alternative correct calculation is to divide by 1000 to get 614.4
kB. (1 for value + 1 for units)
ii A bitmap file has a header metadata that defines the colour depth and the dimensions of the image
matrix (1).
c i Run-length encoding, which replaces a consecutive series of identical codes by one code value plus a
value for the number of repetitions (1 for approach + 1 for explanation).
ii One possibility is to reduce the colour depth by changing each pixel code to an approximation stored
with fewer bits. An alternative is to identify regions of the image where colour changes are small and
to use just one code for all pixels in that region so that run-time encoding can then be applied. (1 for
approach + 1 for explanation)
3 a i Sound is transmitted as a continuous waveform and is, therefore, an analogue phenomenon. Normal
practice nowadays is to store a representation of the sound in digital form. The ADC is used to convert
the analogue signal to a digital representation. (1 for analogue sound + 1 for digital storage)
ii The sampling rate is simply the number of samples of the sound intensity taken per unit time (1). The
rate chosen should be in accordance with Nyquist’s theorem (1). The sound intensity is measured
when a sample is taken. The value obtained has to be stored as a digital value (1). The number of bits
used for this defines the sampling resolution (1). If more bits are used the values that can be stored
are more closely spaced so that the approximation to the actual intensity value is more accurate (1).
b i A band-limiting filter (1)
ii To remove higher frequency components that the human ear would not be able to hear (1) and that
would have such a high frequency that Nyquist’s theorem would not be satisfied with any sensible
sampling rate used (1)
4 This is Question 1 in 9608 Paper 13 June 2015. At the time of writing the published mark scheme is available
on the CAIE School Support Hub (requires registration). The Examiners Report for the June 2015 series is also
available there and this may contain comments specific to this question.
The following are what the author of this chapter in the Teacher Resource would suggest as reasonable
answers, with alternatives suggested where appropriate.
Original material © Cambridge University Press 2019
a i 124 is represented by 01111100 in two’s complement binary and −77 is represented by 10110011 in
two’s complement binary.
a ii 124 is represented by 7C in hexadecimal and −77 is represented by B3 in hexadecimal.
b i 359 is represented by 0011 0101 1001 in BCD.
ii A description is required, examples of what could be included are:
Used as a code when a denary digit is to be displayed
In a digital clock or watch display
In a calculator display
Accurate representation of denary numbers containing decimal fractions
For currency values.
Cambridge International AS & A Level Computer Science 9608 paper 13 Q1 June 2015
5 This is Question 4 in 9608 Paper 12 November 2015. The mark scheme is available on the CAIE School
Support Hub. (requires registration). At the time of writing the published mark scheme is available on the
CAIE School Support Hub. The Examiners Report for the June 2015 series is also available there and this may
contain comments specific to this question.
The following are what the author of this chapter in the Teacher Resource would suggest as reasonable
answers, with alternatives suggested where appropriate
a
The explanation is best starting with the definition of sampling resolution being the number of bits
used to store the sampled sound value. An alternative is to state that the sampling resolution defines
the number of values that are available for choosing the one that is closest to the measured analogue
value.
The sampling process involves quantisation because only a limited number of digital values are
available for matching the measured analogue value
More bits means a higher sampling resolution and therefore a better match between the digital value
chosen and the analogue value measured
This leads to a more accurate representation of the sound.
The definition of sampling rate is the number of samples taken per second
Increasing the sampling rate improves the accuracy of the representation of the sound.
44100 16 2
b i 176400
8
4 60 176400
ii
1024 1024
c
The fundamental fact is that the human ear is an imperfect hearing device
Therefore lossless compression is not essential; lossy compression can be used
The MP3 format can make use of the following facts:
Original material © Cambridge University Press 2019
Some sounds cannot be heard by the human ear
Some sounds are less well heard than others
A softer sound in the presence of a louder sound will not be heard well.
Cambridge International AS & A Level Computer Science 9608 paper 12 Q4 November 2015
Worksheet 1.1: for testing basic understanding
1 C&E
2 C
Note that 145 could be the representation for an unsigned integer, 91 could be the representation for two BCD
digits (packed) and -111 could be the representation for a two’s complement integer
3 a
27 26 25 24 23 22 21 20
128s 64s 32s 16s 8s 4s 2s 1s
1 0 1 0 0 1 1 0
b Even. The total denary equivalent is obtained by adding together the denary equivalent for each bit
position. The value of each bit, either 0 or 1, shows whether the denary equivalent (2 raised to a power) is
included in the number. The least significant bit represents 2 raised to the power 0. All even numbers
therefore have a 0 as the least significant bit; all odd numbers have a 1.
c 128 + 32 + 4 + 2 = 166
d Negative because it starts with a 1 for the most significant bit.
e -128 + 32 +4 + 2 = -90
4 9, because 373 is greater than 255 but less than 511. 8 bits can store the 28 different values 0 – 255. 9 bits can
store 0 – 511.
5 a 60 to reach 00000 then a further 230 gives 60 + 230 = 290 in total.
b You just get a negative number as an answer.
c 99940 converts to 00059 in nine’s complement then converts to 00060 in ten’s complement. We then get
the same addition as when using common sense: 00060 + 00230 = 00290.
6 Bitmap size is the number of pixels multiplied by the number of bits used to represent one pixel (the colour
depth). Size is normally specified in bytes not bits, so the calculation is 1024 x 768 x 1 for the size in
bytes = 786432.
Sound file size is length of time multiplied by the sampling rate multiplied by the number of bits used to store
one sample (the sampling resolution). So the calculation for the number of bytes is 5 x 60 x 100 x 2 =60000.
The bitmap file is the larger of the two.
7 Lossy compression is useful for media files such as sound, bitmap image or video. This is because the user
might be happy with a slightly inferior quality. Sometimes the human senses cannot detect the difference in
quality. In other cases, the benefits of smaller file size outweigh the disadvantages of the loss in quality.
Lossless compression is essential for a document containing text. It is essential that the content and therefore
the information conveyed are unaltered.
Original material © Cambridge University Press 2019
Worksheet 1.2: more challenging questions
1 a
1 0 0 1 0 1 1 1 0 1 0 1
0 1 1 1 0 1 1 0 1 0 0 0
Because a currency value only has two digits to represent the fractional part, these two numbers in BCD
can occupy one byte. The implied decimal point is between this byte and the byte representing the whole
number value.
There are several points to note. With just two bytes the range of possible values is very small. In any real
system, there would be an agreed number of bytes to represent a value, always with just one byte
representing the fractional part. The use of the term ‘decimal point’ is valid here because BCD is a
character code for the decimal digits 0 – 9. The term ‘binary point’ should be used only when the
representation is of a binary number value.
b 17.43
c
1 0 0 1 0 1 1 1 0 1 0 1
+ 0 1 1 1 0 1 1 0 1 0 0 0
= 1 0 0 0 0 1 1 0 1 1 1 0 1
When you add the fractional parts, the result is a sequence of binary digits that is not recognisable as a
BCD value.
The addition of the whole number parts has suffered overflow.
d
0 1 0 1
+ 1 0 0 0
= 1 1 0 1
+ 0 1 1 0
= 1 0 0 1 1
+ 1 1 0 1
+ 0 1 1 0
= 1 0 1 0 0
+ 1 0 0 0 0
+ 0 1 1 0
= 0 0 0 1 0 1 1 1
Note how the calculation starts with the codes for the second decimal place BCD values then moves on
successively through the higher value BCD codes. At each stage, the initial result has 0110 added to it. At
each stage after the first one, any carry digit is included in the calculation. The final answer shows the
four BCD codes correctly representing the value 17.43.
However, note that the correction factor is used only when an individual addition has produced either an
unrecognisable non-BCD character or there has been an overflow. In the example above, it had to be
used three times.
e Four bits provide 16 distinct combinations. Six of these are not BCD codes; only codes 0000 to 1001 are
needed to represent decimal digits. Because 0110 is binary for decimal 6, this, used as a correction factor,
Original material © Cambridge University Press 2019
converts an unrecognisable combination into one that is a BCD code. For example, if an addition had
produced 1010 initially (e.g. by adding 0111 to 0011) the corrected answer would
be 0001 0000.
f In any binary value, each bit represents a power of two. For the fractional part of a number, this still
applies. An exact value can only exist if the fractional part is a combination of 1/2, 1/4, 1/8, 1/16 and so
on. Decimal .75 is a combination of 1/2 and 1/4. The binary equivalent is .11 giving an exact conversion.
For 7.68 the ‘multiplication by two and record whole number parts’ method as illustrated in worked
example 16.01 of the coursebook can be used to convert the .68 fractional part. This converts to
.1010111 as a close approximation.
2 True, False, False
3 All are False
A picture element or pixel is the smallest identifiable component of a bitmap image. The number of bits per
pixel is sometimes referred to as the colour depth. A drawing list contains a command for each object
included in the image where each command has a list of attributes that define the properties of the object.
The resolution of a bitmapped image is the product of the number of pixels per row times the number of
rows.
4 a At each branch point, the left-hand branch is used for a 0 and the right-hand branch for a 1.
b
c No. To understand why, it is necessary to consider the implication of the prefix property. For two binary
digits, there are four combinations. Here 10 and 01 have been used to represent letters; 00 and 11 have
been carried forward to form part of three-digit codes. For three digits there are eight combinations but
four of these cannot be used to code letters because they begin with 01 or 10. In this scheme 110 and
111 have been used to code letters; 000 and 001 have been carried forward for four-digit codes.
Crucially, the scheme uses 0000, 0001, 0010 and 0011 to code letters leaving none to be carried forward.
Another way of seeing this is to look at the tree and note that the lowest level has no free spaces.
d The scheme should use two of the four codes with four digits to code letters. The remaining two four-
digit codes can be used to provide four distinct five-digit codes. Two of the original four-digit codes have
been lost but four new five-digit codes have been created so overall, two more letters are coded.
Original material © Cambridge University Press 2019
Chapter 2: Communication and
networking technologies: Answers to
coursebook questions and tasks and to
Worksheet questions
Syllabus section covered: 2.1
From the coursebook
Question 2.01
Individual pairs might be shielded with foil. A cable containing multiple twisted pairs might have an outer
shielding of foil or braid. Shielding is used to minimise interference. Interference between individual pairs in a
cable is called crosstalk.
Task 2.01
Distance to travel is 15000 km
Speed of light is approximately 3 x 108 m s-1
Time taken = distance divided by speed:
15000 km divided by 300000 km s-1 = 0.05 s
Question 2.02
This is not a question with a fixed answer.
Task 2.02
Best approach probably to work in KiB units. The number of bits leaving the buffer in two seconds at 300 Kbps is
300 x 1000 x 2. In KiB this is (300 x 1000 x 2)/(1024 x 8). A similar calculation using 1 000 000 instead of 300 gives
the number of KiB entering the buffer in two seconds. The amounts for different times are just simple multiples of
these values. The difference between inflow and outflow gives net gain. This allows a rough estimate of the time
taken to fill to be made. This in turn allows a rough estimate of the time to empty to be made. Exact values need
algebra but there is no need to insist on an exact answer.
Original material © Cambridge University Press 2019
Task 2.03
Type of answer should be: 11000011 01101001 00000110 00100101 / 00011000, where spaces are shown
between the bytes just for readability and where it has been assumed that the suffix is represented in a byte.
Corresponding dotted decimal form is 195.105.6.37/24.
Extension Question 2.01
Number of addresses possible is 2128 which is 3.4 x 1038.
Earth radius = 6371 km. Formula for surface area is 4πr2. r2 in m2 is 6371 x 1000 x 6371 x 1000 = 4.06 x 1013 so
surface area = 5.1 x 1014. Therefore, dividing the number of addresses by this area shows that there could be
about 6.7 x 1923 addresses per square metre. Quite a few!
Exam-style Questions
(with mark allocation in brackets):
1 a i Twisted pair, coaxial or fibre optic NOT copper. (1 for an example, 2 for all)
ii Bandwidth, which defines the rate of data transfer. Attenuation, which defines how much the signal
degrades over time. Interference, which is how much the signal might be affected by external factors.
(1 per factor + 1 per explanation, max 4)
b i Might be answered by choosing from radio, microwave or infrared. Radio can penetrate walls, infrared
has the best bandwidth are two possibilities. Alternatively, might argue that within a room or a
building wireless is sensible. (1 + 1 for explanation)
ii No infrastructure needed, no drilling holes in walls or digging tunnels underground. (1)
iii If wireless is used outside a building it can be affected by weather conditions. Not guided. More
interference likely. (1)
c i Public switched telephone network, POTS, or provides telephone connections. (1)
ii Could provide dial-up connection through a modem to allow data transfer (1). Could provide a leased
line dedicated data connection (1). These would allow connections between buildings on the site (1).
Alternatively could provide access points for WiFi set up in individual rooms or buildings (1). Note that
the three marks for this question require some detail in the explanation. Should explain that
connections between buildings could involve PSTN support. (Max 3)
2 a i Database (1), server (1)
ii Any application that involves a website accessible via a URL that includes a domain name. Email using
an email address that includes a domain name. (1 for each name + 1 for each description, max 4)
b i Dotted decimal (1). Each byte in the 32-bit address is given its denary equivalent value (1).
ii Class C (1) because the top three bits are 110 when denary 205 is converted to binary (1).
iii Addressing is hierarchical (1). NetID is used for navigation through the Internet (1). Once the
communication reaches the network the hostID is used to locate the exact destination (1).
Original material © Cambridge University Press 2019
c Because the netID is defined by the topmost 24 bits i.e. the first three bytes, the hostID is defined by the
remaining byte (1). Denary 152 converts to binary 10011000 (1).
3 1 mark each for any of the following up to a maximum of 6:
The website makes the video available on sufficient servers to match demand.
A suitable level of compression is used before transmission.
Bit rate for transmission is adequate.
The receiver has adequate bandwidth available.
The receiver has media player software installed.
There is a buffer used to temporarily store incoming data.
The media player controls the input to the buffer.
The output from the buffer is at the rate required for viewing the video.
The buffer has a high- and low-water mark.
4 a In an intranet/private network (1) which uses TCP/IP technology (1)
b 1 mark each for any of the following up to a maximum of 4:
There are a defined set of IP addresses designated as only for private use.
All other IP addresses are for public use.
Only public IP addresses are recognised on the Internet.
NAT used to translate a public IP address into one or more private IP addresses.
Public IP addresses are not used in an intranet.
One individual private IP addresses can be used in an unlimited number of different intranets.
5 This is Question 9 in 9608 Paper 12 November 2015. At the time of writing the published mark scheme is
available on the CAIE School Support Hub (requires registration). The Examiners Report for the June 2015
series is also available there and this may contain comments specific to this question.
The following are what the author of this chapter in the Teacher Resource would suggest as reasonable
answers with alternatives suggested where appropriate.
a i 0B.40.FF.5A
ii The expected answer is a description of an IPv4 address as illustrated in part (a)(i); the explanation
could include:
The address is defined in 32 bits
The address is conceptually treated as consisting of four sections each occupying one byte
Each one byte section may be represented by two hexadecimal digits or by a denary number in the
range 0 – 255
The first part of the address defines a network ID and the second part a host ID.
b • The explanation could begin with definitions of terms:
o URL is Uniform Resource Locator
o DNS is Domain Name System or Domain Name Service depending on which source you choose
(it also is sometimes used for Domain Name Server but that usage is best disregarded here).
Original material © Cambridge University Press 2019
The most important aspects regarding the use of a URL are:
o It is a user-friendly version of an IP address
o The URL includes a domain name
o A browser uses a URL and in particular sends a URL to the DNS.
The most important aspects regarding the use of a DNS are:
o It uses a database that matches a URL to the corresponding IP address
o There is a hierarchical structure to the DNS and its database
o The database on an individual DNS server will only have data for a limited range of URLs.
The above facts can be included in an answer that provides a narrative which begins with the user
entering the URL into the browser and ends with the resource identified by the URL being located.
Cambridge International AS & A Level Computer Science 9608 paper 12 Q9 June 2015
6 This is Question 7 in 9608 Paper 11 June 2016. At the time of writing the published mark scheme is available
on the CAIE School Support Hub (requires registration). The Examiners Report for the June 2015 series is also
available there and this may contain comments specific to this question.
The following are what the author of this chapter in the Teacher Resource would suggest as reasonable
answers with alternatives suggested where appropriate.
a Internet Protocol
b • Invalid (6AA and BBBB are too big)
Valid
Invalid (257 is too big)
Invalid (J is not valid in a hexadecimal representation).
c The most important facts are:
The Internet is a public internetwork which uses public IP addresses
Each public IP address is unique
An organisation can have a private network (an intranet) which uses the same IP protocols that are
used in the Internet
A private network uses private IP addresses
A private IP address is unique in a private network but the same address can be used in different
private networks
The connection of a private network to the Internet requires the use of Network Address Translation
(NAT)
A private network is recognised in the Internet by its single unique public IP address.
Cambridge International AS & A Level Computer Science 9608 paper 11 Q7 June 2016
Original material © Cambridge University Press 2019
Worksheet 2.1: for testing basic understanding
1 a Twisted pair and coaxial.
b Twisted pair.
c The individual twisted pairs have different twisting rates.
d The tubular construction keeps the electromagnetic field confined within the cable.
2 a 3, 1, 2
b 2, 3, 1
3 a Bandwidth is a controlling factor for the rate of data transmission.
Attenuation is the loss of signal strength as it travels further and further. This is a factor affecting the
need for repeaters.
The capability for directional focusing and for penetration through a wall are two factors that are self-
explanatory.
b Bandwidth increases with increasing frequency, so is best for infrared.
Attenuation also increases with increasing frequency so it is worst for infrared.
Penetration through a wall increases with increasing wavelength and so is best with radio waves.
Directional focusing capability increases with increasing frequency so is best for infrared.
4 A True, B False, C False, D True
It can be helpful to remember that infrared is the nearest to visible light which can be focussed but will not
penetrate a wall. The terminology associated with radio is misleading. For example, VHF (very high frequency)
has a high frequency compared to other types of radio wave but not compared to infrared.
5 The global positioning system (GPS) is provided by medium earth orbit (MEO) satellites where ten are needed
for global coverage. The cellular phone network is supplemented by low earth orbit (LEO) satellites where
fifty are needed for global coverage.
6 a When there is a shared transmission medium.
b Check the voltage on the transmission medium.
If this indicates activity wait a random time before checking again.
If no activity is detected start transmission.
Continuously check for a collision.
If no collision is detected continue transmission.
If a collision is detected stop transmission of the message and transmit a jamming signal to warn all end-
stations; after a random time try again.
c No, Ethernet broadcasts a message. There is no acknowledgement mechanism. If there is evidence of a
collision a message will be transmitted again but if there is no such evidence it is assumed that the
message will be received.
Original material © Cambridge University Press 2019
7 True, True, False, False, False
PSTN stands for Public Switched Telephone Network. A telecom (telecommunications company) is often
called a PSTN. POTS (plain old telephone service) is an informal name for a PSTN. A PSTN often acts as an ISP
(Internet service provider). The Internet is an internetwork, not a WAN and the world-wide-web is a
distributed application running on the Internet. A leased line service is permanently connected, dial-up is
not required.
8 Each individual denary value corresponds to the binary code stored in one byte. One byte can store values
from 0 to 255. Only the first code has all four values in this range.
9 192.38.45.255 is class C, 128.38.45.255 is class B and 64.38.45.255 is class A.
The first value is definitive; for class A the most significant bit in the first byte is 0 so values from 128 upward
are excluded. For class B the most significant bit is 1 but the next bit is 0 so values from 128 up to 191
are available.
10 http identifies the protocol being used.
:// indicates the end of the protocol definition.
www indicates that a web address is being defined.
mirc.co.uk is the domain name (the user-friendly version of the IP address).
The domain mirc is a subdomain of the domain co which in turn is a subdomain of the domain uk.
help/jarkko2.txt is the pathname of a file located on the host identified by the domain name.
Worksheet 2.2: more challenging questions
1 a The values to be used for altitude are 1000 km for the LEO satellite (given in the question) and 35786 km
for the GEO satellite (constant).
Speed of light ≈ 299800 km s_1.
1000 35786
Time to reach nearest point is ≈ 3.3 ms for LEO and ≈ 119 ms for GEO.
299800 299800
b
Original material © Cambridge University Press 2019
The above diagram could be used. Here S is the satellite, N the nearest point on the surface of the Earth, F is
the furthest point accessible and C is the centre of the Earth. A scale drawing would allow the distance from
S to F to be measured. Otherwise, geometry could be used; in particular Pythagoras’ theorem because the
line from S to F is a tangent and therefore at right angles to the radius from C to F.
NC NS
2
So SF CF 2
Using the value 6375 km for the radius of the Earth, the calculations are:
For LEO the distance to the furthest point accessible ≈ 3708 km and the time taken is ≈ 12 ms.
For GEO the distance to the furthest point accessible ≈ 41676 km and the time taken is ≈ 139 ms.
Considering that a typical processor speed is at least 1 GHz, giving a clock cycle of less than a billionth of a
second, the times for satellite communications in milliseconds are very significant. The differences in
these times depending on the position on the Earth’s surface are also very significant but less so for GEO
because the extreme distance to the satellite dominates the time taken.
2 a Sub-netting uses a coding scheme for the hostID – which for a class C IP address uses eight bits.
To represent 30 workstations in a LAN, five bits will be needed because this allows 32 different codes.
There are three bits left to identify the LAN, so eight LANs can be created. If only 14 workstations are to
be connected in one LAN, only four bits are needed to represent them with individual codes.
This leaves four bits to identify LANs so 16 can be created.
b
Note that only the byte representing the hostID part of the IP address is shown for each workstation. In
each byte the two least significant bits are used to identify the workstation and the next two are used to
identify the LAN. The four most significant bits are unused so could be set to any value.
Original material © Cambridge University Press 2019
Chapter 12: Algorithm Design and
Problem Solving
Answers to coursebook questions and tasks
Syllabus sections covered: 9
It is suggested that Chapter 12 and 13 are worked through in parallel with Chapter 14.
Task 12.01
Task 12.02
The following are examples of answers. These examples show the sort of detail students should show in their
answers.
To make a sandwich To walk from college to shop To log on to computer
Cut two slices of bread Exit college through the main Power up computer
Spread butter on one side entrance Wait for log-on screen
of each slice of bread Turn right and walk to T- Enter username in first text
Lay a slice of cheese on the junction box
buttered side of one slice of Turn left and walk 50 metres Enter password in second
bread Cross the road: you now stand text box
Cover the cheese with the in front of the shop. Press Enter.
second slice of buttered
bread, the buttered side
facing the cheese.
Original material © Cambridge University Press 2019
Task 12.03
Identifier Explanation
Inches Length as a whole number of inches
Cm The result from using the given formula: Cm = Inches * 2.54
OUTPUT "Enter inches: "
INPUT Inches
Cm Inches * 2.54
OUTPUT Cm, " cm"
Task 12.04
IF Age < 12 OR Age > 60 THEN fare is free
Question 12.01
The Greater Than signs (>) have to be replaced by Smaller Than signs (<):
IF Number1 < Number2
THEN // Number1 is smaller
IF Number1 < Number3
THEN
OUTPUT Number1
ELSE
OUTPUT Number3
ENDIF
ELSE // Number2 is smaller
IF Number2 < Number3
THEN
OUTPUT Number2
ELSE
OUTPUT Number3
ENDIF
ENDIF
Question 12.02
First part
The logic statement for Until has to be changed:
INPUT BiggestSoFar
Counter 1
REPEAT
INPUT NextNumber
Counter Counter + 1
IF NextNumber > BiggestSoFar
THEN
BiggestSoFar NextNumber
Original material © Cambridge University Press 2019
ENDIF
UNTIL Counter = 100
OUTPUT BiggestSoFar
Second part
An extra input is required and again the logic statement for Until has to be changed:
INPUT MaxNumbers
INPUT BiggestSoFar
Counter 1
REPEAT
INPUT NextNumber
Counter Counter + 1
IF NextNumber > BiggestSoFar
THEN
BiggestSoFar NextNumber
ENDIF
UNTIL Counter = MaxNumbers
OUTPUT BiggestSoFar
Task 12.05
If it is not known how many times the loop will need to be executed, a REPEAT loop (or a WHILE loop) is more
appropriate. To be able to calculate the average, a count needs to be kept of how many numbers have been
added together. Note that using a REPEAT loop the rogue value is counted as a number, so calculating the
average needs to use (Count – 1)
Using a REPEAT loop:
RunningTotal 0
Count 0
REPEAT
INPUT NextNumber
RunningTotal RunningTotal + NextNumber
Count Count + 1
UNTIL NextNumber = 0
OUTPUT RunningTotal
Average RunningTotal / (Count – 1)
OUTPUT Average
Using a WHILE loop (note that rogue value is not counted as a number):
RunningTotal 0
Count 0
INPUT NextNumber
WHILE NextNumber <> 0 DO
Count Count + 1
RunningTotal RunningTotal + NextNumber
INPUT NextNumber
ENDWHILE
OUTPUT RunningTotal
Original material © Cambridge University Press 2019
Average RunningTotal / Count
OUTPUT Average
Task 12.06
01 // Set up initial values
01.1 INPUT symbol
01.2 // Input Max Number Of Symbols
01.2.1 REPEAT
01.2.2 INPUT MaxNumberOfSymbols
01.2.3 UNTIL MaxNumberOfSymbols MOD 2 = 1
01.3 NumberOfLeadingSpaces (MaxNumberOfSymbols - 1) / 2
01.4 NumberOfSymbols 1
01.5 NumberOfMiddleSpaces -1
02 REPEAT
03 // Output number of leading spaces
03.1 FOR i 1 TO NumberOfLeadingSpaces
03.2 OUTPUT Space // without moving to next line
03.3 NEXT i
04 // Output symbol, middle spaces, symbol
04.01 IF NumberOfSymbols = 1 // top of pyramid
04.02 THEN
04.03 OUTPUT Symbol
04.04 ELSE
04.05 IF NumberOfSymbols < MaxNumberOfSymbols
04.06 THEN
04.07 OUTPUT Symbol
04.08 FOR i 1 TO NumberOfMiddleSpaces
04.09 OUTPUT Space // no new line
04.10 NEXT i
04.11 OUTPUT Symbol
04.12 ELSE // output the final line
04.13 FOR i 1 TO NumberOfSymbols
04.14 OUTPUT Symbol // no new line
04.15 NEXT i
04.16 ENDIF
04.17 ENDIF
04.18 OUTPUT Newline // move to next line
05 // Adjust values for next row
05.1 NumberOfLeadingSpaces NumberOfLeadingSpaces - 1
05.2 NumberOfMiddleSpaces NumberOfMiddleSpaces + 2
05.3 NumberOfSymbols NumberOfSymbols + 2
06 UNTIL NumberOfSymbols > MaxNumberOfSymbols
A better solution is to treat the tip and the base of the triangle separately and use the REPEAT loop for the other
lines.
Original material © Cambridge University Press 2019
Task 12.07
CALL SetValues
CALL OutputTopRow
CALL AdjustValuesForNextRow
REPEAT
CALL OutputLeadingSpaces
CALL OutputRow
CALL AdjustValuesForNextRow
UNTIL NumberOfSymbols = MaxNumberOfSymbols
CALL OutputBaseRow
PROCEDURE SetValues
INPUT symbol
// Input Max Number Of Symbols
REPEAT
INPUT MaxNumberOfSymbols
UNTIL MaxNumberOfSymbols MOD 2 = 1
NumberOfLeadingSpaces (MaxNumberOfSymbols - 1) / 2
NumberOfSymbols 1
NumberOfMiddleSpaces -1
ENDPROCEDURE
PROCEDURE OutputTopRow
CALL OutputLeadingSpaces
OUTPUT Symbol
OUTPUT Newline
ENDPROCEDURE
PROCEDURE AdjustValuesForNextRow
NumberOfLeadingSpaces NumberOfLeadingSpaces - 1
NumberOfMiddleSpaces NumberOfMiddleSpaces + 2
NumberOfSymbols NumberOfSymbols + 2
ENDPROCEDURE
PROCEDURE OutputLeadingSpaces
FOR i 1 TO NumberOfLeadingSpaces
OUTPUT Space // without moving to next line
NEXT i
ENDPROCEDURE
PROCEDURE OutputRow
OUTPUT Symbol
FOR i 1 TO NumberOfMiddleSpaces
OUTPUT Space // don’t move to next line
NEXT i
Original material © Cambridge University Press 2019
OUTPUT Symbol
OUTPUT Newline // move to the next line
ENDPROCEDURE
PROCEDURE OutputBaseRow
FOR i 1 TO NumberOfSymbols
OUTPUT Symbol
NEXT i
OUTPUT Newline
ENDPROCEDURE
Exam-style Questions in Chapter 12
1
Weighting 10
Total 0
FOR Count 1 TO 9
INPUT Digit
Value Digit * Weighting
Total Total + Value
Weighting Weighting – 1
Count Count + 1
NEXT Count
Remainder Total MOD 11
CheckDigit 11 – Remainder
IF CheckDigit = 10
THEN
CheckDigit X
ENDIF
Marking guidance:
1 mark for initialising Weighting and Total correctly
1 mark for correct loop structure
1 mark for correct input statement within loop
1 mark for correct assignment to Value within loop
1 mark for correct assignment to Total within loop
1 mark for correct updating of Weighting and Count
1 mark for correct assignment to Remainder
1 mark for correct assignment to CheckDigit
1 mark for correct IF statement structure and correct Boolean expression
Original material © Cambridge University Press 2019
2
Positive 0
Negative 0
REPEAT
INPUT Number
IF Number > 0
THEN
Positive Positive + 1
ELSE
Negative Negative + 1
UNTIL Number = 0
Marking guidance:
1 mark for initialising Positive correctly
1 mark for initialising Negative correctly
1 mark for correct REPEAT loop structure and correct Boolean expression
1 mark for correct input statement within the loop
1 mark for correct IF THEN ELSE structure within loop
1 mark for correct Boolean expression
1 mark for correctly incrementing Positive and Negative
3
RogueValue -1
Total 0
Count 0
INPUT Number
WHILE Number <>RogueValue DO
Count Count + 1
Total Total + Number
INPUT Number
ENDWHILE
If Count > 0
THEN
Average Total / Count
OUTPUT Average
ENDIF
Marking guidance:
1 mark for initialising RogueValue
1 mark for initialising Total and Count correctly
1 mark for INPUT statement before loop
1 mark for correct loop structure and correct Boolean expression
Original material © Cambridge University Press 2019
1 mark for correct assignments to Count and Total within loop
1 mark for correct input statement as last statement within loop
1 mark for correct IF statement structure and correct Boolean expression
1 mark for correct assignment to Average and output Average
Original material © Cambridge University Press 2019
Pseudocode solutions for Chapter 12:
Programming Exercises
12.06 DECLARE SecretWord : STRING
DECLARE Guess : STRING
DECLARE NumberOfGuesses : INTEGER
INPUT SecretWord
NumberOfGuesses 0
REPEAT
INPUT Guess
NumberOfGuesses NumberOfGuesses + 1
IF Guess = SecretWord
THEN
OUTPUT "Well Done"
ELSE
OUTPUT "Sorry, incorrect"
ENDIF
UNTIL (Guess = SecretWord) OR (NumberOfGuesses = 10)
OUTPUT NumberOfGuesses
IF Guess <> SecretWord
THEN
OUTPUT SecretWord
ENDIF
12.07 DECLARE SecretWord : STRING
DECLARE Guess : STRING
DECLARE NumberOfGuesses : INTEGER
DECLARE MyFile : STRING
DECLARE Count : INTEGER
MyFile "TextFile.txt"
OPENFILE MyFile FOR READ
WordNumber RANDOM
Count 0
WHILE (NOT EOF(MyFile)) AND (Count < WordNumber)
READFILE MyFile, SecretWord
Count Count + 1
ENDWHILE
CLOSEFILE MyFile
NumberOfGuesses 0
REPEAT
INPUT Guess
NumberOfGuesses NumberOfGuesses + 1
IF Guess = SecretWord
THEN
OUTPUT "Well Done"
ELSE
OUTPUT "Sorry, incorrect"
ENDIF
UNTIL (Guess = SecretWord) OR (NumberOfGuesses = 10)
Original material © Cambridge University Press 2019
OUTPUT NumberOfGuesses
IF Guess <> SecretWord
THEN
OUTPUT SecretWord
ENDIF
12.08 PROCEDURE ShowMenu
OUTPUT "1. Convert from km to miles"
OUTPUT "2. Convert inches into cm"
OUTPUT "3. Number guessing game"
OUTPUT "Enter your choice (1, 2 or 3)"
INPUT Choice
CASE OF Choice
1 : CALL KmToMiles
2 : CALL InchesToCm
3 : CALL NumberGuessingGame
OTHERWISE OUTPUT "Not a valid choice"
ENDPROCEDURE
12.09 DECLARE SecretWord : STRING
DECLARE NumberOfLetters : INTEGER
DECLARE Letter : CHAR
DECLARE GuessedSoFar : STRING
DECLARE PenaltyScore : INTEGER
DECLARE Count : INTEGER
INPUT SecretWord
NumberOfLetters LENGTH(SecretWord)
GuessedSoFar ""
FOR Count 1 TO NumberOfLetters
GuessedSoFar GuessedSoFar & "#"
NEXT Count
PenaltyScore 0
REPEAT
INPUT Letter
FOR Count 1 TO NumberOfLetters
IF SecretWord[Count] = Letter
THEN
GuessedSoFar[Count] Letter
ELSE
PenaltyScore PenaltyScore + 1
ENDIF
NEXT Count
UNTIL (GuessedSoFar = SecretWord)
OUTPUT PenaltyScore
Original material © Cambridge University Press 2019
Pseudocode solutions for Worksheets
12.1/14.1 and 12.2/14.2
1 DECLARE Length : INTEGER
DECLARE Width : INTEGER
DECLARE Area : INTEGER
INPUT Length
INPUT Width
Area Length * Width
OUTPUT Area
2 DECLARE DegreesF : INTEGER
DECLARE DegreesC : REAL
INPUT DegreesF
DegreesC (DegreesF – 32) * 5 / 9
OUTPUT DegreesC
3 DECLARE Temperature : INTEGER
INPUT Temperature
IF Temperature < 1
THEN
OUTPUT "It is freezing"
ELSE
OUTPUT "It is not freezing"
ENDIF
4 DECLARE Temperature: INTEGER
INPUT Temperature
IF Temperature < 1
THEN
OUTPUT "The water is frozen"
ELSE
IF Temperature > 100
THEN
OUTPUT "The water is boiling"
ELSE
OUTPUT "It is liquid"
ENDIF
ENDIF
5 DECLARE MonthNumber : INTEGER
INPUT MonthNumber
CASE OF MonthNumber
1: OUTPUT "January"
2: OUTPUT "February"
3: OUTPUT "March"
4: OUTPUT "April"
5: OUTPUT "May"
6: OUTPUT "June"
7: OUTPUT "July"
8: OUTPUT "August"
9: OUTPUT "September"
10: OUTPUT "October"
Original material © Cambridge University Press 2019
11: OUTPUT "November"
12: OUTPUT "December"
OTHERWISE OUTPUT "Invalid month number"
ENDCASE
6 DECLARE MaxNumber : INTEGER
DECLARE Counter : INTEGER
INPUT MaxNumber
FOR Counter 1 TO MaxNumber
OUTPUT Counter
NEXT
7 DECLARE MacNumber : INTEGER
DECLARE Counter : INTEGER
INPUT MaxNumber
FOR Counter MaxNumber TO 1 STEP -1
OUTPUT Counter
NEXT
8 DECLARE MaxNumber : INTEGER
DECLARE Interval : INTEGER
DECLARE Counter : INTEGER
INPUT MaxNumber
INPUT Interval
FOR Counter 1 TO MaxNumber STEP Interval
OUTPUT Counter
NEXT
9 DECLARE Number : INTEGER
DECLARE LargestSoFar : INTEGER
DECLARE Counter : INTEGER
INPUT LargestSoFar
FOR Counter 2 TO 10
INPUT Number
IF Number > LargestSoFar
THEN
LargestSoFar Number
ENDIF
NEXT
OUTPUT LargestSoFar
10 DECLARE Number : INTEGER
DECLARE SmallestSoFar : INTEGER
DECLARE Counter : INTEGER
INPUT SmallestSoFar
FOR Counter 2 TO 10
INPUT Number
IF Number < SmallestSoFar
THEN
SmallestSoFar Number
ENDIF
NEXT
OUTPUT SmallestSoFar
11 Using a post-condition loop:
DECLARE Number : INTEGER
REPEAT
OUTPUT "Enter a whole number between 1 and 5"
INPUT Number
UNTIL (Number >= 1) AND (Number <= 5)
Original material © Cambridge University Press 2019
Using a pre-condition loop:
DECLARE Number : INTEGER
OUTPUT "Enter a whole number between 1 and 5"
INPUT Number
WHILE (Number < 1) OR (Number > 5)
OUTPUT "Enter a whole number between 1 and 5"
INPUT Number
ENDWHILE
12 DECLARE MinNumber : INTEGER
DECLARE MaxNumber : INTEGER
DECLARE Counter : INTEGER
INPUT MinNumber
INPUT MaxNumber
FOR Counter MinNumber TO MaxNumber
OUTPUT Counter
NEXT
13 DECLARE Character : CHAR
DECLARE CharCode : INTEGER
INPUT Character
CharCode ASC(Character)
OUTPUT CharCode
14 DECLARE Character : CHAR
DECLARE CharCode : INTEGER
INPUT CharCode
Character CHR(CharCode)
OUTPUT Character
15 DECLARE Text : STRING
DECLARE TextLength : INTEGER
INPUT Text
TextLength LENGTH(Text)
OUTPUT TextLength
16 DECLARE Text : STRING
DECLARE LeftMostText : STRING
INPUT Text
LeftMostText LEFT(Text, 2)
OUTPUT LeftMostText
17 DECLARE Text : STRING
DECLARE RightMostText : STRING
INPUT Text
RightMostText RIGHT(Text, 2)
OUTPUT RightMostText
18 DECLARE Text : STRING
DECLARE TextLength : INTEGER
DECLARE Middle : INTEGER
INPUT Text
TextLength LENGTH(Text)
IF TextLength MOD 2 = 0
THEN // even number of characters
Middle TextLength DIV 2
OUTPUT MID(Text, Middle, 2)
ELSE // odd number of characters
Middle (TextLength + 1) DIV 2
OUTPUT MID(Text, Middle, 1)
Original material © Cambridge University Press 2019
ENDIF
19 DECLARE FirstName : STRING
DECLARE Surname : STRING
DECLARE FullName : STRING
INPUT FirstName
INPUT Surname
FullName FirstName & " " & Surname
OUTPUT FullName
20 DECLARE FirstName : STRING
DECLARE Surname : STRING
DECLARE NameString : STRING
INPUT FirstName
INPUT Surname
NameString LEFT(FirstName, 1) & " " & Surname
OUTPUT NameString
21 DECLARE Number : REAL
DECLARE NearestWholeNumber : INTEGER
INPUT Number
Number Number + 0.5
NearestWholeNumber INT(Number)
22 DECLARE Number : INTEGER
DECLARE Counter : INTEGER
FOR Counter 1 TO 5
Number RANDOM()
OUTPUT Number
NEXT
Original material © Cambridge University Press 2019
Chapter 13: DataTypes and structures:
Answers to coursebook questions and
tasks
Syllabus sections covered: 10
It is suggested that Chapters 12 and 13 are worked through in parallel with Chapter 14.
Task 13.01
Identifier Explanation Data type
BiggestSoFar Stores the biggest number input so far INTEGER/REAL
NextNumber The next number to be input INTEGER/REAL
Stores how many numbers have been
Counter INTEGER
input so far
Identifier Explanation Data type
SecretNumber The number to be guessed INTEGER
NumberOfGuesses The number of guesses the player has made INTEGER
Guess The number the player has input as a guess INTEGER
Identifier Explanation Data type
RunningTotal Stores the sum of the numbers input so far INTEGER/REAL
Counter How many numbers have been input INTEGER
NextNumber The next number input INTEGER/REAL
Average The average of the numbers input REAL
Identifier Explanation Data type
NumberOfRows Stores the number of rows of the grid INTEGER
NumberOfColumns Stores the number of columns of the grid INTEGER
Symbol Stores the chosen character symbol CHAR
RowCounter Counts the number of rows INTEGER
ColumnCounter Counts the number of columns INTEGER
Original material © Cambridge University Press 2019
Identifier Explanation Data type
Symbol The character symbol to form the pyramid CHAR
MaxNumberOfSymbols The number of symbols in the final row INTEGER
NumberOfSpaces The number of spaces to be output in the INTEGER
current row
NumberOfSymbols The number of symbols to be output in the INTEGER
current row
Task 13.02
1
TYPE BookType
Title : STRING
YearOfPublication : INTEGER
Price : REAL
ISBN : STRING
ENDTYPE
2
DECLARE Book : BookType
Book.Title "Computer Science"
Book.YearOfPublication 2015
Book.Price 15.99
Book.ISBN "9781107546738"
Original material © Cambridge University Press 2019
Task 13.03
Arrays with friends’ names and ages similar to:
Task 13.04
MaxIndex 19
INPUT SearchValue
Found FALSE
Index −1
REPEAT
Index Index + 1
IF Name[Index] = SearchValue
THEN
Found TRUE
ENDIF
UNTIL FOUND = TRUE OR Index >= MaxIndex
IF Found = TRUE
THEN
OUTPUT "Age:", Age[Index]
ELSE
OUTPUT "Name not found"
ENDIF
Task 13.05
n MaxIndex – 1
REPEAT
NoMoreSwaps TRUE
FOR j 0 TO n
IF MyList[j] < MyList[j + 1]
THEN
Temp MyList[j]
MyList[j] MyList[j + 1]
Original material © Cambridge University Press 2019
MyList[j + 1] Temp
NoMoreSwaps FALSE
ENDIF
NEXT j
n n – 1
UNTIL NoMoreSwaps = TRUE
Task 13.06
1
DECLARE Board : ARRAY[1..3, 1..3] OF CHAR
2
CONSTANT Space = ' '
DECLARE Row, Column : INTEGER
FOR Row 1 TO 3
FOR Column 1 TO 3
Board[Row, Column] Space
NEXT Column
NEXT Row
3
Board[1, 1] 'A'
4
Board[2, 2] 'B'
Task 13.07
DECLARE BookArray : ARRAY[1..200] OF BookType
Book[1].Title "Computer Science"
Book[1].YearOfPublication 2015
Book[1].Price 15.99
Book[1].ISBN "9781107546738"
Task 13.08
1
OPENFILE "GameData.txt" FOR WRITE
FOR Row 1 TO 3
FOR Column 1 TO 3
WRITEFILE "GameData.txt", Board[Row, Column]
NEXT Column
NEXT Row
Original material © Cambridge University Press 2019
CLOSEFILE "GameData.txt"
2
OPENFILE "GameData.txt" FOR READ
FOR Row 1 TO 3
FOR Column 1 TO 3
READFILE "GameData.txt", Board[Row, Column]
NEXT Column
NEXT Row
CLOSEFILE "GameData.txt"
Task 13.09
1
Task 13.10
1
Original material © Cambridge University Press 2019
2
Task 13.11
Exam-style Questions
1
Variable Example value Data type
ColourCode “034AB45” STRING
ProductionDate 2018/03/31 DATE
Weight 67.45 REAL
NumberInStock 98 INTEGER
SizeCode ‘X’ CHAR
Completed FALSE BOOLEAN
Marking guidance:
1 mark for each 2 correct entries in the data type column
Original material © Cambridge University Press 2019
2
Marking guidance:
1 mark for each correct column
3 a
Identifier Data type Explanation
UserList ARRAY[0..20] OF STRING 1D array to store user IDs
PasswordList ARRAY[0..20] OF STRING 1D array to store passwords
MaxIndex INTEGER Number of elements in each array
MyUserID STRING User ID entered to login
MyPassword STRING Password entered to login.
UserIdFound BOOLEAN FALSE if user ID not found in
UserList
TRUE if ID found in Userlist
LoginOK BOOLEAN FALSE if user ID not found, or
passwords don’t match
TRUE if password correctly
entered for existing user ID
Index INTEGER Pointer to current array element
Marking guidance:
1 mark for each 2 correct data types
1 mark for correct identifier PasswordList
1 mark for each correct cell completed in Explanation column
b
MaxIndex ← 20
INPUT MyUserID
INPUT MyPassword
UserIdFound ← FALSE
LoginOK ← FALSE
Index ← −1
Original material © Cambridge University Press 2019
REPEAT
Index ← Index + 1
IF UserList[Index] = MyUserID
THEN
UserIdFound ← TRUE
ENDIF
UNTIL UserIdFound = TRUE OR Index = MaxIndex
IF UserIdFound = TRUE
THEN
IF PasswordList[Index] = MyPassword
THEN
LoginOK ← TRUE
ENDIF
ENDIF
IF LoginOK = TRUE
THEN
OUTPUT "Login successful"
ELSE
OUTPUT "User ID and/or password incorrect"
ENDIF
Marking guidance:
1 mark for each correctly completed gap (shown by dotted lines)
c i
TYPE UserRecord
UserID : STRING
Password : STRING
ENDTYPE
Marking guidance:
1 mark for correct TYPE statement structure
1 mark for 2 fields correctly declared
ii
DECLARE User : ARRAY[0..20] OF UserRecord
Marking guidance:
1 mark for correct array declaration structure (i.e. DECLARE User : ARRAY[0..20])
1 mark for correct giving data type (i.e. OF UserRecord)
Original material © Cambridge University Press 2019
You might also like
- The Yellow House: A Memoir (2019 National Book Award Winner)From EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Rating: 4 out of 5 stars4/5 (98)
- Nguyen Tien Dat - HDCPDocument6 pagesNguyen Tien Dat - HDCPĐạt NguyễnNo ratings yet
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceFrom EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceRating: 4 out of 5 stars4/5 (895)
- Learners Activity Sheet 4 UpdatedDocument8 pagesLearners Activity Sheet 4 UpdatedJohn Raymund MabansayNo ratings yet
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeFrom EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeRating: 4 out of 5 stars4/5 (5794)
- Ponuda LaptopaDocument6 pagesPonuda LaptopaFranjo IličićNo ratings yet
- Grit: The Power of Passion and PerseveranceFrom EverandGrit: The Power of Passion and PerseveranceRating: 4 out of 5 stars4/5 (588)
- Dee3061 Computer Aided Design (Cad) - SDocument6 pagesDee3061 Computer Aided Design (Cad) - Skshika meganathanNo ratings yet
- Shoe Dog: A Memoir by the Creator of NikeFrom EverandShoe Dog: A Memoir by the Creator of NikeRating: 4.5 out of 5 stars4.5/5 (537)
- Error 20225 PDFDocument2 pagesError 20225 PDFAmberNo ratings yet
- Never Split the Difference: Negotiating As If Your Life Depended On ItFrom EverandNever Split the Difference: Negotiating As If Your Life Depended On ItRating: 4.5 out of 5 stars4.5/5 (838)
- CS 302 ProjectDocument29 pagesCS 302 Projectsampe12No ratings yet
- On Fire: The (Burning) Case for a Green New DealFrom EverandOn Fire: The (Burning) Case for a Green New DealRating: 4 out of 5 stars4/5 (73)
- V130 33 R34 - Instal Guide - 10 08Document10 pagesV130 33 R34 - Instal Guide - 10 08stgpereiraNo ratings yet
- COMPUTER APPLICATIONS - Excel NotesDocument2 pagesCOMPUTER APPLICATIONS - Excel NotesPamela WilliamsNo ratings yet
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryFrom EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryRating: 3.5 out of 5 stars3.5/5 (231)
- Google Company Overview PDFDocument3 pagesGoogle Company Overview PDFJillNo ratings yet
- Team of Rivals: The Political Genius of Abraham LincolnFrom EverandTeam of Rivals: The Political Genius of Abraham LincolnRating: 4.5 out of 5 stars4.5/5 (234)
- Topic: 1.3.5 Memory, Storage Devices and Media: Two Types Primary Memory Secondary MemoryDocument13 pagesTopic: 1.3.5 Memory, Storage Devices and Media: Two Types Primary Memory Secondary MemoryAthuai DoorNo ratings yet
- The Little Book of Hygge: Danish Secrets to Happy LivingFrom EverandThe Little Book of Hygge: Danish Secrets to Happy LivingRating: 3.5 out of 5 stars3.5/5 (399)
- Write Optimized Dso Delta LoadDocument2 pagesWrite Optimized Dso Delta Loadsatyasap007No ratings yet
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureFrom EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureRating: 4.5 out of 5 stars4.5/5 (474)
- Iserv - Corporate ProfileDocument24 pagesIserv - Corporate ProfileMambo KingNo ratings yet
- UX LawsDocument2 pagesUX LawsChayatal BangladeshNo ratings yet
- The Emperor of All Maladies: A Biography of CancerFrom EverandThe Emperor of All Maladies: A Biography of CancerRating: 4.5 out of 5 stars4.5/5 (271)
- Installation Instruction CABA WinDocument22 pagesInstallation Instruction CABA WinCesar Antonio Sanchez GonzalezNo ratings yet
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaFrom EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaRating: 4.5 out of 5 stars4.5/5 (266)
- W3Schools Quiz Results1Document8 pagesW3Schools Quiz Results1GAUTAMI UPPADANo ratings yet
- SQL JOIN OBSERVATIONSDocument9 pagesSQL JOIN OBSERVATIONSBalwant SinghNo ratings yet
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersFrom EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersRating: 4.5 out of 5 stars4.5/5 (344)
- Red Hat System Administration I 1.4 PracticeDocument9 pagesRed Hat System Administration I 1.4 PracticestefygrosuNo ratings yet
- Hacker's Armory For System Hacking - Password Recovery Tools PDFDocument3 pagesHacker's Armory For System Hacking - Password Recovery Tools PDFniranjan shettiNo ratings yet
- Accelerating Convolutional Neural Network by Exploiting Sparsity On GpusDocument11 pagesAccelerating Convolutional Neural Network by Exploiting Sparsity On GpusAmeyNo ratings yet
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreFrom EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreRating: 4 out of 5 stars4/5 (1090)
- 4525CSQR Introduction To Web Development - Coursework AS1Document9 pages4525CSQR Introduction To Web Development - Coursework AS1Asad AfaqNo ratings yet
- This Study Resource Was: - Are A Set of Rules That Determine The Execution of A TransactionDocument8 pagesThis Study Resource Was: - Are A Set of Rules That Determine The Execution of A TransactionSeyed BillalganiNo ratings yet
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyFrom EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyRating: 3.5 out of 5 stars3.5/5 (2219)
- Ad Iit YaDocument2 pagesAd Iit YavenkateshgunturuNo ratings yet
- The Unwinding: An Inner History of the New AmericaFrom EverandThe Unwinding: An Inner History of the New AmericaRating: 4 out of 5 stars4/5 (45)
- Immersive Gaming, Anywhere.: Lenovo™ Legion Y720 LaptopDocument2 pagesImmersive Gaming, Anywhere.: Lenovo™ Legion Y720 LaptopMarie Joy GarmingNo ratings yet
- CS2357 - OOAD VIVA QUESTIONSDocument5 pagesCS2357 - OOAD VIVA QUESTIONSHemanand DuraiveluNo ratings yet
- UMLDocument31 pagesUMLMuhammad Iqrash Awan67% (3)
- Project Presentation Template - (Review-I)Document19 pagesProject Presentation Template - (Review-I)Pradhumnya RangdaleNo ratings yet
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)From EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Rating: 4.5 out of 5 stars4.5/5 (119)
- Materi 1. Foundation For IT Audit and Control Part 1Document9 pagesMateri 1. Foundation For IT Audit and Control Part 1Eka Dila100% (1)
- MC770 / MC780 MPS3537mc / MPS4242mc Maintenance Manual: Downloaded From Manuals Search EngineDocument217 pagesMC770 / MC780 MPS3537mc / MPS4242mc Maintenance Manual: Downloaded From Manuals Search EngineNajeeb UllahNo ratings yet
- KRMDocument46 pagesKRMozgocerNo ratings yet
- Her Body and Other Parties: StoriesFrom EverandHer Body and Other Parties: StoriesRating: 4 out of 5 stars4/5 (821)