Professional Documents
Culture Documents
Risk Identification Process
Uploaded by
Віталій ІванюкCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Risk Identification Process
Uploaded by
Віталій ІванюкCopyright:
Available Formats
7/8/2021 TestOut LabSim
3.1 Risk Identification Process
As you study this section, answer the following questions:
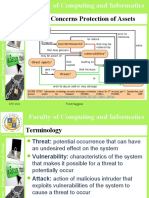
What assets are vulnerable?
What are the potential threats?
What vulnerabilities exist?
In this section, you will learn to:
Identify assets
Define potential threats
Discover threat vulnerabilities
The key terms for this section include:
Term Definition
Physical machines such as servers and workstations, intangibles such as intellectual
Asset
property, sales forecasts, product roadmaps, etc.
The cornerstone of security infrastructure, which is composed of Confidentiality, Integrity,
CIA Triad
and Availability.
Threat Anything that can damage a business's ability to generate revenue.
A weakness a threat actor could use to exploit and threaten systems. Could be both internal
Vulnerability
and external
This section helps you prepare for the following certification exam objectives:
Exam Objective
TestOut Cyber Defense Pro, v1.0 3.1 Risk Identification Process
3.1 Given a scenario, analyze data as part of security
monitoring
activities.
Impact analysis
Organization impact vs. localized impact
CompTIA CySA+ (CS0-002) Immediate vs. total
5.2 Given a scenario, apply security concepts in support of
organizational risk mitigation.
Risk identification process
Copyright © 2021 TestOut Corporation All rights reserved.
https://labsimapp.testout.com/v6_0_455/index.html/productviewer/1188/3.1 1/1
You might also like
- Software Testing For Security: ConclusionDocument5 pagesSoftware Testing For Security: ConclusionMeron SolomonNo ratings yet
- Managing Modern Security Operations Center & Building Perfect Career as SOC AnalystFrom EverandManaging Modern Security Operations Center & Building Perfect Career as SOC AnalystNo ratings yet
- Breach & Attack Simulation 101: Expert Tips InsideDocument20 pagesBreach & Attack Simulation 101: Expert Tips InsideRikrdo BarcoNo ratings yet
- Bitdefender GravityZone Business Security Premium Datasheet enDocument2 pagesBitdefender GravityZone Business Security Premium Datasheet enHalaNo ratings yet
- Bsi10 Ops PDFDocument5 pagesBsi10 Ops PDFTrong Thua HuynhNo ratings yet
- White Paper Automated Penetration Testing: Can IT Afford Not To?Document9 pagesWhite Paper Automated Penetration Testing: Can IT Afford Not To?gynxNo ratings yet
- Cybersecurity Tech Basics Vulnerability Management OverviewDocument5 pagesCybersecurity Tech Basics Vulnerability Management OverviewAlexandre XavierNo ratings yet
- IT Risk Management Based On COBIT 5 For Risk at Deutsche Telekom AG Joa Eng 0518Document7 pagesIT Risk Management Based On COBIT 5 For Risk at Deutsche Telekom AG Joa Eng 0518toanquoc.doanNo ratings yet
- SIEM Buyers Guide v6Document15 pagesSIEM Buyers Guide v6sagar.poladiyaNo ratings yet
- Plantilla Reporte eCPPTv2 v2Document14 pagesPlantilla Reporte eCPPTv2 v2HardWiseNo ratings yet
- Software Security TestingDocument8 pagesSoftware Security TestingChintan PanchalNo ratings yet
- How To Write AssignmentDocument6 pagesHow To Write Assignmentqueen heartNo ratings yet
- Security Effectiveness Report 2020Document22 pagesSecurity Effectiveness Report 2020Marius Iulian RosuNo ratings yet
- Addressing Misalignment Between Information Security Metrics and Business-Driven Security ObjectivesDocument7 pagesAddressing Misalignment Between Information Security Metrics and Business-Driven Security Objectivesgispa87No ratings yet
- Implementing Agile Security Response: The Essential ChecklistDocument7 pagesImplementing Agile Security Response: The Essential Checklistfalcon.peregrine7775No ratings yet
- Core IDC 404UDocument8 pagesCore IDC 404UgynxNo ratings yet
- Csol 530 02 sp21Document16 pagesCsol 530 02 sp21api-593553237No ratings yet
- Security Operations Center: How To Build ADocument35 pagesSecurity Operations Center: How To Build Aep230842No ratings yet
- Calculate, Communicate and Compare Your Cyber Exposure Key BenefitsDocument2 pagesCalculate, Communicate and Compare Your Cyber Exposure Key BenefitsSantiago HuilcamaiguaNo ratings yet
- Cisco Technical Security Assessment AagDocument3 pagesCisco Technical Security Assessment Aaglakbabi1035No ratings yet
- Ds Endpoint SecurityDocument7 pagesDs Endpoint SecuritydeisecairoNo ratings yet
- White Paper - Defending InfrastructureDocument20 pagesWhite Paper - Defending InfrastructureDan McClintockNo ratings yet
- Analysis and Evaluating Security of Component-Based Software Development: A Security Metrics FrameworkDocument11 pagesAnalysis and Evaluating Security of Component-Based Software Development: A Security Metrics FrameworkSuhail Qadir MirNo ratings yet
- Risk Triage For Security Vulnerability AnnouncementsDocument7 pagesRisk Triage For Security Vulnerability AnnouncementstonnycultNo ratings yet
- Microsoft Zero Trust TEI StudyDocument43 pagesMicrosoft Zero Trust TEI StudysbhaktaNo ratings yet
- 06 Art A User-Centric Machine Learning Framework For Cyber Security Operations CenterDocument3 pages06 Art A User-Centric Machine Learning Framework For Cyber Security Operations CenterlcoqzxnmNo ratings yet
- Methods For The Prevention, Detection and Removal of Software Security VulnerabilitiesDocument6 pagesMethods For The Prevention, Detection and Removal of Software Security VulnerabilitiesPham Dinh ChungNo ratings yet
- Tekgem IACS Cyber Security AssessmentDocument8 pagesTekgem IACS Cyber Security AssessmentLynsey StephensonNo ratings yet
- Forrester TechTideDocument36 pagesForrester TechTidetomerNo ratings yet
- Cyber Incident Response PlaybookDocument11 pagesCyber Incident Response PlaybookRamganeshBalan100% (3)
- The Cyber Exposure Score: How Secure IsDocument14 pagesThe Cyber Exposure Score: How Secure IsRicardo VoltaireNo ratings yet
- Kenna VMDocument25 pagesKenna VMnav pNo ratings yet
- Microsoft Security Best PracticesDocument265 pagesMicrosoft Security Best PracticesahmedNo ratings yet
- Anonymised Infrastructure Penetration Testing ReportDocument67 pagesAnonymised Infrastructure Penetration Testing ReportRavi GiriNo ratings yet
- Web Application Penetrating Testing MethodologyDocument36 pagesWeb Application Penetrating Testing Methodologyzaoui danteNo ratings yet
- DownloadDocument12 pagesDownloadmanav.mahajan2994No ratings yet
- 15655-FE-Mandiant-Defender's Advantage-Executive Summary-03Document6 pages15655-FE-Mandiant-Defender's Advantage-Executive Summary-03LinKanXNo ratings yet
- Delliote - Us-Risk-Cyber-Ia-Urgent-Call-To-ActionDocument10 pagesDelliote - Us-Risk-Cyber-Ia-Urgent-Call-To-Actionjazzbond007No ratings yet
- 1.lyallpur Khalsa College Jalandhar, 2.guru Nanak Dev University, AmritsarDocument15 pages1.lyallpur Khalsa College Jalandhar, 2.guru Nanak Dev University, AmritsarsuzanalupuNo ratings yet
- START HERE - Microsoft Security Workshop - Engagement and Delivery GuideDocument9 pagesSTART HERE - Microsoft Security Workshop - Engagement and Delivery Guideabyru2001No ratings yet
- C2M2 Implementation GuideDocument13 pagesC2M2 Implementation GuideKPNo ratings yet
- CSSLP Brochure ForPDFDocument6 pagesCSSLP Brochure ForPDFjoekkuNo ratings yet
- ISACA WP Vulnerability Assessment 1117Document17 pagesISACA WP Vulnerability Assessment 1117Sripal S100% (2)
- Make FAIR Practical For Your Business - Safe SecurityDocument3 pagesMake FAIR Practical For Your Business - Safe SecuritypankajsclNo ratings yet
- Rapid 7 Insight VM and AppsecDocument52 pagesRapid 7 Insight VM and AppsecPrasanth Prasad ParvathyNo ratings yet
- Unit 9: Computer and Information Systems SecurityDocument35 pagesUnit 9: Computer and Information Systems SecurityHussen AbdulkadirNo ratings yet
- Security Concerns Protection of Assets: Succeed We MustDocument10 pagesSecurity Concerns Protection of Assets: Succeed We MustTimo AlexNo ratings yet
- Vulnerability Management Maturity Model: - Work in ProgressDocument4 pagesVulnerability Management Maturity Model: - Work in ProgressMircea PetrescuNo ratings yet
- 2019 June 5 Safety PresentationFinalDocument21 pages2019 June 5 Safety PresentationFinalHesham HamyNo ratings yet
- ISO 27001 Metrics and Implementation Guide PDFDocument13 pagesISO 27001 Metrics and Implementation Guide PDFNauman Khalid100% (1)
- User Centric Machine LearningDocument9 pagesUser Centric Machine LearningSenait MebrahtuNo ratings yet
- CISSP Summary V1.1Document25 pagesCISSP Summary V1.1marutidivekar50% (2)
- Evaluation of Threat ModelsDocument5 pagesEvaluation of Threat ModelsInternational Journal of Innovative Science and Research TechnologyNo ratings yet
- Securing The Modern Enterprise SToRMDocument15 pagesSecuring The Modern Enterprise SToRMMildred EchezanoNo ratings yet
- 02 Threat ModelingDocument85 pages02 Threat Modelingfaaizhussain100% (1)
- Enterprise Security Asignment 1Document14 pagesEnterprise Security Asignment 1koiNo ratings yet
- Centerity CyberOps - Cyber Observability Brochure - September 2020Document3 pagesCenterity CyberOps - Cyber Observability Brochure - September 2020AngelobyFirulaisNo ratings yet
- NIS2 WebinarDocument52 pagesNIS2 WebinarMario DurandNo ratings yet
- Threat Actor Type FactsDocument2 pagesThreat Actor Type FactsВіталій ІванюкNo ratings yet
- Threat Research FactsDocument2 pagesThreat Research FactsВіталій ІванюкNo ratings yet
- Security Control Categories and Types FactsDocument2 pagesSecurity Control Categories and Types FactsВіталій ІванюкNo ratings yet
- Penetration Testing and Threat HuntingDocument2 pagesPenetration Testing and Threat HuntingВіталій ІванюкNo ratings yet
- Tailings Storage Facilities Management 2004Document69 pagesTailings Storage Facilities Management 2004jacs127100% (1)
- Scanner MCQ CA+Inter+Audit May+24Document127 pagesScanner MCQ CA+Inter+Audit May+24carlsen magNo ratings yet
- Can Lawyers Give Clients A Guarantee?Document7 pagesCan Lawyers Give Clients A Guarantee?San Fernando Valley Bar AssociationNo ratings yet
- Business Plan SampleDocument42 pagesBusiness Plan SampleDanangNo ratings yet
- 2 Projectriskmanagement 110110060847 Phpapp01Document12 pages2 Projectriskmanagement 110110060847 Phpapp01Vic RabayaNo ratings yet
- Fundamentals of Oil and Gas Law (UWI)Document56 pagesFundamentals of Oil and Gas Law (UWI)NT CeeNo ratings yet
- Theory of ProfitDocument10 pagesTheory of ProfitKajal Patil100% (1)
- Gold Outlook 2024Document9 pagesGold Outlook 2024acc1qhuyNo ratings yet
- 8 Dr. Li v. Spouses SolimanDocument53 pages8 Dr. Li v. Spouses SolimanRubierosseNo ratings yet
- Financial Literacy and Financial Risk Tolerance of Individual Investors: Multinomial Logistic Regression ApproachDocument11 pagesFinancial Literacy and Financial Risk Tolerance of Individual Investors: Multinomial Logistic Regression ApproachlaluaNo ratings yet
- Competency-Based Curriculum Bread and Pastry Tm1Document66 pagesCompetency-Based Curriculum Bread and Pastry Tm1Melanie Lampera100% (1)
- WHW News Edition 1, 2014Document20 pagesWHW News Edition 1, 2014Women's Health WestNo ratings yet
- 2021-06 GDCRE - Corporate Presentation - InvestorDocument16 pages2021-06 GDCRE - Corporate Presentation - InvestorNoamNo ratings yet
- Impartiality enDocument6 pagesImpartiality enعبدالعزيز بدرNo ratings yet
- Suicide and Suicide Risk Factors: A Literature Review: CPD ArticleDocument5 pagesSuicide and Suicide Risk Factors: A Literature Review: CPD ArticleKKN 11 UMY 2017No ratings yet
- Case Study 2 V2Document22 pagesCase Study 2 V2Hemanth RaoNo ratings yet
- Quiz Day 6Document2 pagesQuiz Day 6Volt ManzanoNo ratings yet
- HSE Plan TA2015 in Porvoo - S1Document23 pagesHSE Plan TA2015 in Porvoo - S1tomas budrysNo ratings yet
- ACT 141-Module 1-Assurance ServicesDocument98 pagesACT 141-Module 1-Assurance ServicesJade Angelie FloresNo ratings yet
- Food Control For Consumers Regulators and Producers 1994 Food ControlDocument4 pagesFood Control For Consumers Regulators and Producers 1994 Food ControlSamirAleixoNo ratings yet
- Case A: Parth Sheth 1/22/14Document2 pagesCase A: Parth Sheth 1/22/14Parth ShethNo ratings yet
- Checklist of Mandatory Documentation Required by ISO 45001 enDocument12 pagesChecklist of Mandatory Documentation Required by ISO 45001 enashraf91% (11)
- Investing in Frontier MarketsDocument22 pagesInvesting in Frontier MarketsNavin Ratnayake100% (1)
- Index Internal Auditor 2004 - 2016Document222 pagesIndex Internal Auditor 2004 - 2016pembazak100% (1)
- PER Performance Objectives AchieveDocument15 pagesPER Performance Objectives AchieveUsmanKhalidNo ratings yet
- EBA New Report On SRTDocument99 pagesEBA New Report On SRTRobin MichaelNo ratings yet
- CBC in Massage Therapy NC Ii NewDocument50 pagesCBC in Massage Therapy NC Ii NewRico EsponillaNo ratings yet
- Audit - Mock Board Examination - Sy2019-20Document15 pagesAudit - Mock Board Examination - Sy2019-20Mark Domingo MendozaNo ratings yet
- HSE Management System: Practice Safety and Environmental Protection in OperationsDocument14 pagesHSE Management System: Practice Safety and Environmental Protection in OperationsAamir BashirNo ratings yet
- Bahrain Standards - Module 01 General SpecificationsDocument15 pagesBahrain Standards - Module 01 General SpecificationsBilal ShahNo ratings yet