Professional Documents
Culture Documents
Gujarat Technological University
Uploaded by
parth0 ratings0% found this document useful (0 votes)
14 views1 pageThis document is an exam for the subject of Information and Network Security. It contains 5 questions assessing knowledge of topics like symmetric and asymmetric key cryptography algorithms, hashing, digital signatures, SSL, Kerberos, PKI, and types of cryptographic attacks. The exam has a total of 70 marks and instructs students to attempt all questions, make assumptions where necessary, and includes figures indicating the full marks for each subsection.
Original Description:
Original Title
171611-2170709-INS
Copyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentThis document is an exam for the subject of Information and Network Security. It contains 5 questions assessing knowledge of topics like symmetric and asymmetric key cryptography algorithms, hashing, digital signatures, SSL, Kerberos, PKI, and types of cryptographic attacks. The exam has a total of 70 marks and instructs students to attempt all questions, make assumptions where necessary, and includes figures indicating the full marks for each subsection.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
14 views1 pageGujarat Technological University
Uploaded by
parthThis document is an exam for the subject of Information and Network Security. It contains 5 questions assessing knowledge of topics like symmetric and asymmetric key cryptography algorithms, hashing, digital signatures, SSL, Kerberos, PKI, and types of cryptographic attacks. The exam has a total of 70 marks and instructs students to attempt all questions, make assumptions where necessary, and includes figures indicating the full marks for each subsection.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
You are on page 1of 1
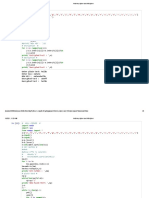
Seat No.: ________ Enrolment No.
___________
GUJARAT TECHNOLOGICAL UNIVERSITY
BE - SEMESTER–VII(NEW) • EXAMINATION – WINTER 2016
Subject Code:2170709 Date:21/11/2016
Subject Name:Information and Network Security
Time:10.30 AM to 1.00 PM Total Marks: 70
Instructions:
1. Attempt all questions.
2. Make suitable assumptions wherever necessary.
3. Figures to the right indicate full marks.
Q.1 (a) What is symmetric key cryptography? What are the challenges of symmetric 07
key cryptography? List out various symmetric key algorithms and explain
Caesar cipher in detail.
(b) P and Q are two prime numbers. P=7, and Q=17. Take public key E=5. If plain 07
text value is 6, then what will be cipher text value according to RSA algorithm?
Explain in detail.
Q.2 (a) Explain one time Pad in detail. What are the practical issues of this algorithm? 07
(b) Explain Byte substitution and Shift row operation of AES in detail. 07
OR
(b) Explain DES key generation process in detail. 07
Q.3 (a) What is PKI? What are the components of PKI? Explain Certificate Authority 07
in detail.
(b) “Only Hashing dose not ensures integrity of message in network 07
communication” – Justify your answer with suitable example.
OR
Q.3 (a) Consider the scenario where user A wants to send bulk data (data is in GBs) to 07
user B using networking. Data exchange has to be done in confidential manner.
The key which is used for encryption can be intercepted by an attacker. Which
is the most efficient and protected way to achieve secure communication?
Justify your answer in detail.
(b) What is SSL? Which security services does it offers? How does it works? 07
Q.4 (a) What is Kerberos? How Kerberos authenticates the users for authorized service 07
access?
(b) Write a short note on “Digital Signature Algorithm”. 07
OR
Q.4 (a) Explain Diffie - Hellman key exchange algorithm 07
(b) Differentiate between hashing and encryption. What are the practical 07
applications of hashing? Compare MD5 and SHA1 hashing algorithms.
Q.5 (a) Write a short note on Message Authentication Code. 07
(b) Write a short note on:
i. Cipher text only attack 04
ii. Timing attack 03
OR
Q.5 (a) What is SSH? How does SSH works? 07
(b) Write a short note on “Hill Cipher”. 07
*************
You might also like
- CISA EXAM-Testing Concept-Digital SignatureFrom EverandCISA EXAM-Testing Concept-Digital SignatureRating: 3.5 out of 5 stars3.5/5 (5)
- CISSP-Domain 3-Cryptography Ver 2021Document14 pagesCISSP-Domain 3-Cryptography Ver 2021Rajaram K.VNo ratings yet
- Gujarat Technological UniversityDocument1 pageGujarat Technological UniversityShweta JhaNo ratings yet
- Gujarat Technological UniversityDocument1 pageGujarat Technological UniversityRahul SharmaNo ratings yet
- Gtu Computer 3170720 Winter 2022Document1 pageGtu Computer 3170720 Winter 2022Farhan MansuriNo ratings yet
- InsDocument2 pagesInsALL THINGS0% (1)
- Gujarat Technological University: InstructionsDocument2 pagesGujarat Technological University: InstructionsShweta JhaNo ratings yet
- Gujarat Technological UniversityDocument2 pagesGujarat Technological Universityneeraj sharmaNo ratings yet
- Summer 2013 PDFDocument1 pageSummer 2013 PDFShweta JhaNo ratings yet
- Gujarat Technological UniversityDocument2 pagesGujarat Technological UniversityShweta JhaNo ratings yet
- Gtu Computer 3170720 Summer 2022Document2 pagesGtu Computer 3170720 Summer 2022Farhan MansuriNo ratings yet
- Be Summer 2022Document2 pagesBe Summer 2022Jenish LathiyaNo ratings yet
- Instructions:: Gujarat Technological UniversityDocument1 pageInstructions:: Gujarat Technological UniversityShweta JhaNo ratings yet
- CNS W2023-3161606Document2 pagesCNS W2023-3161606Archi JariwalaNo ratings yet
- Gujarat Technological UniversityDocument2 pagesGujarat Technological Universityyicef37689No ratings yet
- Gujarat Technological UniversityDocument2 pagesGujarat Technological UniversityShweta JhaNo ratings yet
- Cryptography and System Security - May 2019 MUDocument1 pageCryptography and System Security - May 2019 MUFaraazNo ratings yet
- CNS S2023-3161606Document2 pagesCNS S2023-3161606Archi JariwalaNo ratings yet
- Gujarat Technological UniversityDocument1 pageGujarat Technological Universityyicef37689No ratings yet
- Gujarat Technological UniversityDocument3 pagesGujarat Technological Universitymalaviyaurvashi39No ratings yet
- Gujarat Technological University: What Is Cybersecurity?Document1 pageGujarat Technological University: What Is Cybersecurity?malaviyaurvashi39No ratings yet
- Cs 703 A Cryptography and Information Security Dec 2020Document2 pagesCs 703 A Cryptography and Information Security Dec 2020RahulNo ratings yet
- Gujarat Technological University: InstructionsDocument1 pageGujarat Technological University: InstructionsRockey SharmaNo ratings yet
- Gujarat Technological UniversityDocument1 pageGujarat Technological UniversityvehotiwuNo ratings yet
- (CS6701 PTCS6701)Document3 pages(CS6701 PTCS6701)Russian CarxgameNo ratings yet
- SEIT3062 - Ravirajsinh ChauhanDocument2 pagesSEIT3062 - Ravirajsinh ChauhanYASH CHAHODIYANo ratings yet
- Network Security and Cryptography - R2015 - 11!11!2019Document2 pagesNetwork Security and Cryptography - R2015 - 11!11!2019Lavanth DynoNo ratings yet
- Mcse 302 C Network Security Jun 2020Document2 pagesMcse 302 C Network Security Jun 2020harsh rimzaNo ratings yet
- Information Assurance & Network SecurityDocument2 pagesInformation Assurance & Network SecurityPayal AacharyaNo ratings yet
- CNS 2017Document4 pagesCNS 2017Dr-Samson ChepuriNo ratings yet
- Information Assurance & Network Security: B.E. (Computer Engineering) Seventh Semester (CBS)Document2 pagesInformation Assurance & Network Security: B.E. (Computer Engineering) Seventh Semester (CBS)YashaswiNo ratings yet
- Gujarat Technological UniversityDocument2 pagesGujarat Technological Universitythakornikita001.nt10No ratings yet
- CRYPTOGAPHYDocument4 pagesCRYPTOGAPHYVivek ShuklaNo ratings yet
- Gujarat Technological UniversityDocument1 pageGujarat Technological UniversityAnonymous Cc3oNYTLNo ratings yet
- 07a81903 InformationsecurityDocument6 pages07a81903 InformationsecuritySharanya ThirichinapalliNo ratings yet
- Gujarat Technological UniversityDocument1 pageGujarat Technological UniversityHardik PatoliyaNo ratings yet
- Computer Engineering Department: Gtu Important Questions Bank Subject Name: Information Ecurity Subject Code SemesterDocument5 pagesComputer Engineering Department: Gtu Important Questions Bank Subject Name: Information Ecurity Subject Code SemesterKaushal PardasaniNo ratings yet
- Cryptography and Network Security Feb 2020Document1 pageCryptography and Network Security Feb 2020Akshita dammuNo ratings yet
- Cryptography Quest Bank 02Document7 pagesCryptography Quest Bank 02Gurpreet SinghNo ratings yet
- MCA-505 (E) : M.C.A. V Semester Network SecurityDocument2 pagesMCA-505 (E) : M.C.A. V Semester Network Securityabhinavgiri17No ratings yet
- B.Tech IV Year I Semester (R15) Regular Examinations November/December 2018Document5 pagesB.Tech IV Year I Semester (R15) Regular Examinations November/December 2018pruthviNo ratings yet
- University QuestionsDocument24 pagesUniversity QuestionsVasantha KumariNo ratings yet
- Be Winter 2019Document1 pageBe Winter 2019Madhav janiNo ratings yet
- Gujarat Technological UniversityDocument5 pagesGujarat Technological Universityharshchauhan70166No ratings yet
- Subject Code-3507: Roll No. ....................... Exam Code: S-20Document2 pagesSubject Code-3507: Roll No. ....................... Exam Code: S-20Ashish SharmaNo ratings yet
- (WWW - Entrance-Exam - Net) - Download DOEACC C Level Network Security & Cryptography Sample Paper 1Document2 pages(WWW - Entrance-Exam - Net) - Download DOEACC C Level Network Security & Cryptography Sample Paper 1Mukesh BhambhaniNo ratings yet
- 15A05702 Information SecurityDocument1 page15A05702 Information SecurityBilal AhmedNo ratings yet
- iVvTesXmTyGkgjFEXsaITQ - CM2025 Past Exam Mar 2023Document5 pagesiVvTesXmTyGkgjFEXsaITQ - CM2025 Past Exam Mar 2023chaudhary.ahmadNo ratings yet
- Directional CouplerDocument1 pageDirectional CouplerMRINAAL GOSAINNo ratings yet
- TE - SemVI - Cryptography - System SecurityDocument4 pagesTE - SemVI - Cryptography - System SecuritySURABHI NAIK192074No ratings yet
- Is 2007Document1 pageIs 2007nikita_07036880No ratings yet
- Gujarat Technological UniversityDocument2 pagesGujarat Technological UniversityDevangNo ratings yet
- (WWW - Entrance-Exam - Net) - Download DOEACC C Level Network Security & Cryptography Sample Paper 2Document2 pages(WWW - Entrance-Exam - Net) - Download DOEACC C Level Network Security & Cryptography Sample Paper 2DEBLEENA VIJAYNo ratings yet
- Network Security and Cryptography - R2015 - 26!04!2019Document2 pagesNetwork Security and Cryptography - R2015 - 26!04!2019Lavanth DynoNo ratings yet
- R05411202 InformationsecurityDocument4 pagesR05411202 InformationsecuritySamiullah MohammedNo ratings yet
- Jntuworld: Network Security and CryptographyDocument1 pageJntuworld: Network Security and CryptographycomputerstudentNo ratings yet
- L77Str.: 2,02T, Seiviester Compltttrr, (NSC) 2017)Document2 pagesL77Str.: 2,02T, Seiviester Compltttrr, (NSC) 2017)Venkat KiranNo ratings yet
- 2010 - .May - June-2010Document1 page2010 - .May - June-2010nitte5768No ratings yet
- Mcse 302 C Network Security Dec 2020Document3 pagesMcse 302 C Network Security Dec 2020harsh rimzaNo ratings yet
- CNS R16 Q Paper-May 2019Document2 pagesCNS R16 Q Paper-May 2019Raghu NangunuriNo ratings yet
- Gujarat Technological UniversityDocument1 pageGujarat Technological UniversityVishant ChaudharyNo ratings yet
- A Study On Efficient OTP Generation Using Stream CDocument7 pagesA Study On Efficient OTP Generation Using Stream Cthành nguyễnNo ratings yet
- Appendix A: Introduction To Cryptographic Algorithms and ProtocolsDocument80 pagesAppendix A: Introduction To Cryptographic Algorithms and ProtocolsDipesh ShresthaNo ratings yet
- Blowfish AlgorithmDocument4 pagesBlowfish AlgorithmInternational Organization of Scientific Research (IOSR)100% (3)
- Cryptography: Computer Science & Engineering Information TechnologyDocument90 pagesCryptography: Computer Science & Engineering Information Technologykundankeshari2537No ratings yet
- (Information Security and Cryptography) Jean-Philippe Aumasson, Willi Meier, Raphael C.-W. Phan, Luca Henzen (Auth.) - The Hash Function BLAKE-Springer-Verlag Berlin Heidelberg (2014)Document237 pages(Information Security and Cryptography) Jean-Philippe Aumasson, Willi Meier, Raphael C.-W. Phan, Luca Henzen (Auth.) - The Hash Function BLAKE-Springer-Verlag Berlin Heidelberg (2014)sampahNo ratings yet
- CNS 5Document4 pagesCNS 5SYITB207 Aachal ModakNo ratings yet
- Playfair Cipher 2Document19 pagesPlayfair Cipher 2Abhishek DaveNo ratings yet
- RC5 Cipher - WikipediaDocument5 pagesRC5 Cipher - WikipediaCARLOSMIGUEZNo ratings yet
- UNIT - I (Part 2)Document109 pagesUNIT - I (Part 2)asdadsaNo ratings yet
- Cryptography and Network SecurityDocument22 pagesCryptography and Network SecuritysanjuNo ratings yet
- Secure Hash Algorithm (Sha-256)Document22 pagesSecure Hash Algorithm (Sha-256)sri harshaphaniNo ratings yet
- CSS TopperDocument135 pagesCSS TopperRushi ShahNo ratings yet
- Cryptopp FaqsDocument15 pagesCryptopp FaqstalalzxxNo ratings yet
- EncryptionDocument49 pagesEncryptionJacky VajwaNo ratings yet
- Performance Evaluation of Cryptographic Algorithms: DES, 3DES, Blowfish, Twofish, and ThreefishDocument11 pagesPerformance Evaluation of Cryptographic Algorithms: DES, 3DES, Blowfish, Twofish, and ThreefishomaaaNo ratings yet
- 2015051923000001Document1 page2015051923000001Fernando PMNo ratings yet
- Auto Key Cipher and Hill CipherDocument6 pagesAuto Key Cipher and Hill CipherDamam SakethNo ratings yet
- GMPGMPH Ma MC Me Meh MK MM MMH Mu Opn Rc2 Rc3 Rc4 Rc5 Rc6 Rc7 Rc8 Rc9 College Code & NameDocument1 pageGMPGMPH Ma MC Me Meh MK MM MMH Mu Opn Rc2 Rc3 Rc4 Rc5 Rc6 Rc7 Rc8 Rc9 College Code & NamePraful N KNo ratings yet
- (Update) Post Test Week 6 - Attempt ReviewwDocument5 pages(Update) Post Test Week 6 - Attempt ReviewwDita NoviyantiNo ratings yet
- 02 Cryptographic ToolsDocument116 pages02 Cryptographic ToolsMoh Abdul Rehman MustafaNo ratings yet
- Is CombinedDocument566 pagesIs Combinedlolzcat3454No ratings yet
- Hill Cipher PDFDocument2 pagesHill Cipher PDFPadmajaNo ratings yet
- Block CiphersDocument25 pagesBlock CiphersAnkur Agrawal100% (1)
- Help Mla Crypto SWDocument150 pagesHelp Mla Crypto SWJulio César Carroll JiménezNo ratings yet
- Substitution TechniquesDocument17 pagesSubstitution TechniquesChetan ChauhanNo ratings yet
- Cryptograpy and Network Security HandoutDocument78 pagesCryptograpy and Network Security HandoutDr Narayana Swamy RamaiahNo ratings yet
- The Bouncy Castle FIPS Java APIDocument97 pagesThe Bouncy Castle FIPS Java APIKrishna TelgaveNo ratings yet
- Simplified DES 1: 2.1 Key GenerationDocument3 pagesSimplified DES 1: 2.1 Key GenerationRimbun Ferianto SrNo ratings yet
- Simpli Ed DES 1: 2.1 Key GenerationDocument3 pagesSimpli Ed DES 1: 2.1 Key GenerationAli hassanNo ratings yet