Professional Documents
Culture Documents
How To Configure Tls With Sip Proxy: Barracuda Cloudgen Firewall
Uploaded by
Hari NarayananOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
How To Configure Tls With Sip Proxy: Barracuda Cloudgen Firewall
Uploaded by
Hari NarayananCopyright:
Available Formats
Barracuda CloudGen Firewall
How to Configure TLS with SIP Proxy
https://campus.barracuda.com/doc/17105777/
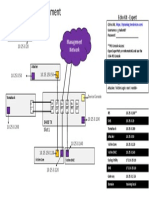
This article provides steps to configure SIP with TLS encryption in an example scenario where
the telephone is located in a different network from that of the PBX. The Barracuda NG Firewall
performs NAT between both networks. The SIP Proxy in the Barracuda NG Firewall translates the
network addresses in SIP messages to allow communication between the telephone and the PBX. The
example scenario is illustrated in the following diagram:
For more security, configure all peers to verify the validity of the certificates and provide their own
custom certificates. You can configure the peers not to verify the certificates, but this is a less secure
setup. If you are testing TLS, it is recommended that you test the scenario with the highest security,
because it is less fault-tolerant and more likely to produce problems in case of misconfiguration.
In this article:
Before You Begin
You must install OpenSSL to create a self-signed CA and the certificates. OpenSSL is already
installed in most Linux distributions. In Windows, you must install it separately.
This article provides steps for creating a self-signed root CA. If you disable the use of an
external CA in the SIP Proxy, an internal root CA is generated automatically. You can use this
root CA to sign the certificates for the client and the PBX instead of creating another one. The
root CA environment is located in
/var/phion/preserve/sipsprx/server_service/opensips/rootCA/.
This article provides steps for use with PhonerLite and Asterisk, but you can use any softphone
or PBX that supports TLS encryption. The configuration of Asterisk, except for the TLS settings,
as well as the standard configuration of the SIP Proxy are out of the scope of this article. An
already working setup with SIP over UDP or TCP is assumed.
How to Configure TLS with SIP Proxy 1 / 10
Barracuda CloudGen Firewall
Step 1. Create a Firewall Rule to Redirect the SIP/TLS Port to the SIP Proxy
Create an App Redirect firewall rule to redirect the SIP port to the SIP Proxy.
If you have specified SIPcf as the Service , edit the SIPcf Service Object to add TCP port 5061.
If you explicitly specified the ports in your redirect rule, add TCP port 5061 so that it is also
redirected.
Step 2. Create Private Keys and Certificates
Create the private keys and certificates for the softphone, SIP Proxy, and PBX .
For more information on how to create self-signed X.509 certificates, see How to Create Certificates
with XCA and How to Create Certificates for the SIP Proxy.
Asterisk: The certificate installed on the SIP Proxy must contain the IP address of the SIP Proxy
in the common name field. Otherwise, Asterisk will refuse to authenticate.
Step 3. Configure the SIP Proxy to Support TLS
To configure the TLS settings for the SIP Proxy:
How to Configure TLS with SIP Proxy 2 / 10
Barracuda CloudGen Firewall
1. Log into the Barracuda NG Firewall.
2. Open the Forwarding Settings page (Config > Full Config > Box > Virtual Servers >
ServerName EXPORT > Assigned Services > FirewallServiceName (Firewall) >
Forwarding Settings).
3. From the Configuration menu in the left pane, select VoIP/SIP.
4. Expand the Configuration Mode menu and click Switch to Advanced.
5. In the SIP Proxy TLS Settings section, select the Enable TLS Support check box.
6. Next to Private Key, click Ex/Import, select Import from File, and then select the
sipproxy-private.pem file that you generated.
7. Select the Use an External CA check box.
8. Next to External Root CA Certificate, click Ex/Import and select Import from PEM File.
9. Browse to the rootCA folder and select the cacert.pem file.
10. In SIP Proxy Certificate, import the sipproxy-cert.pem file in the tls folder.
It is recommended that you change the Certificate Security Level to High. This setting
provides protection from man-in-the-middle attacks by requiring the SIP Proxy to check
the validity of the certificates from the client and the server. If the certificates are invalid,
they are rejected.
11. Click Send Changes and then click Activate.
12. To verify that the certificate file was accepted, view the log file of the SIP Proxy ( Server \
FirewallService \sipproxy). The file should look similar to the following:
INFO:core:check_for_krb: KRB5 cipher KRB5-DES-CBC3-MD5 found
INFO:core:init_tls_domains: Processing TLS domain [0.0.0.0:0]
How to Configure TLS with SIP Proxy 3 / 10
Barracuda CloudGen Firewall
WARNING:core:init_ssl_ctx_behavior: client verification NOT activated.
Weaker security. INFO:core:init_tls_domains: Processing TLS domain
[0.0.0.0:0] WARNING:core:init_ssl_ctx_behavior: server verification NOT
activated. Weaker security. NOTICE:core:main: version: opensips 1.8.2-
tls (x86_64/linux)
Step 4. Configure Asterisk to Support TLS
The following instructions are for Linux. In Windows, change the forward slash (/) path
separators to backslashes (\).
To configure TLS settings for the Asterisk server:
1. Connect to the Asterisk server through SSH.
2. Change to the /etc/asterisk directory and create a subdirectory named tls.
3. Copy the following files into the /etc/asterisk/tls directory:
The cacert.pem file from your rootCA folder.
The asterisk-keycert.pem file from your tls folder.
4. Change the user and group of /etc/asterisk/tls and all of its contents to the same user
Asterisk uses. Then change the permissions of both files to 0400.
$ cd /etc/asterisk
$ chown -R asterisk:asterisk tls/
$ chmod 0400 /etc/asterisk/tls/*
5. If you are using FreePBX, open the /etc/asterisk/sip_general_custom.conf file with a
text editor such as vi.
6. If you are not using FreePBX, open the /etc/asterisk/sip.conf file with a text editor such
as vi and search for the [general] section.
7. Add the following lines:
tlsenable=yes tlsbindaddr=0.0.0.0
tlscertfile=/etc/asterisk/tls/asterisk-keycert.pem
tlsdontverifyserver=no ;tlscipher=DES-CBC3-SHA tlsclientmethod=sslv23
tlscafile=/etc/asterisk/tls/cacert.pem
If you do not want Asterisk to verify the validity of the certificates, set tlsdontverifyserver
to yes .
8. Change the transport protocol of your SIP peers to TLS:
1. Open FreePBX and select Applications > Extensions.
2. Edit each of your extensions.
If you only want to allow your SIP peers to use TLS (which is more secure but breaks
the standard), set the transport parameter to TLS Only.
If you want to allow (but not force) TLS, set it to All – TLS Primary.
How to Configure TLS with SIP Proxy 4 / 10
Barracuda CloudGen Firewall
9. Apply the changes in FreePBX to reload the configuration.
10. To verify that the certificate was correctly configured:
1. Connect to the Asterisk CLI.
$ asterisk -r
2. Reload the configuration.
$ sip reload
If the certificate was correctly configured, Asterisk displays the following message:
SSL certificate ok.
Step 5. Import the Root CA into the Client (Windows)
You must import the root CA certificate that you have created in the previous configuration.
Otherwise, the client will reject the certificate of the server. To import the root CA into the client:
1. In Windows, click the Start menu and type mmc in the search field.
2. When the mmc program appears, click it.
3. Go to File > Add/Remove Snap-in.
How to Configure TLS with SIP Proxy 5 / 10
Barracuda CloudGen Firewall
4. In the Add/Remove Snap-in window, click Certificates from the list of available snap-ins and
then click Add.
5. In the Certificates Snap-in window, select Computer account, click Next, and then click
Finish.
6. Click OK.
7. In the Console window, expand Certificates (Local Computer) in the left pane.
8. Right-click Trusted Root Certification Authorities and select All Tasks > Import.
9. In the Certificate Import Wizard, click Next, click Browse, and then select the cacert.pem
file from the rootCA folder. If you do not see the cacert.pem file, change the file filter to All
Files (*.*).
10. Click Next and then click Finish.
Step 6. Configure PhonerLite
To configure PhonerLite:
1. Configure the SIP account you previously created in PhonerLite as usual.
2. Click the Configuration tab.
3. Click the Network tab and then specify the following settings:
Local port: 5061
How to Configure TLS with SIP Proxy 6 / 10
Barracuda CloudGen Firewall
Preferred connection type: TLS
4. Click the Certificate tab and then specify the following settings:
Client certificate – Click the ellipsis button (…). Then browse to and select the client-
keycert.pem file that you previously created.
check certificate from the remote site – If you want PhonerLite to verify the validity of
the certificates, select this check box.
Load Windows CA – Select this check box.
5. Click Save. PhonerLite should now be able to register successfully.
Troubleshooting
The most common issue that you might encounter is the client not being able to register into the PBX.
As a workaround, you can remove the requirement for certificate verification but this does not solve
the issue because your certificates might be misconfigured. Instead, it is strongly recommended you
check the log file of the SIP Proxy to find the cause. The log file is located in //sipproxy. The
following table describes commonly encountered issues and their solutions.
Issue and Symptom Cause Solution
How to Configure TLS with SIP Proxy 7 / 10
Barracuda CloudGen Firewall
Client Does Not Register
The client does not register. The log
displays one of the following error
messages:
• ERROR:core:tls_accept: some The client does not Ensure that you properly configured
error in SSL (ret=0, err=5, accept the certificate the certificates in the client and that
errno=0/Success): of the server. you imported the root CA certificate.
• ERROR:core:tls_accept: New
TLS connection from : failed
to accept: rejected by
client
Try the following solutions:
• Ensure that you have properly
configured the PBX and enabled TLS
support in it. The root CA certificate
must be imported into the PBX.
Verify that the cacert.pem file is
located in /etc/asterisk/tls,
There can be several
and that the file is readable by
causes:
Asterisk.
• The PBX is not
• Verify that the PBX is up and
Client Fails to Register correctly configured.
running, and that you correctly
The client fails to register and then • The PBX is switched
configured TLS.
quickly tries again. The log displays off or not running.
• To verify that TLS support is
the following message: • TLS support is not
enabled, run netstat -an |
ERROR:core:tls_accept: New configured in the PBX.
grep 5061 in the PBX and verify
TLS connection to <ip of the • A firewall is blocking
that port 5061 is open.
PBX>:5061 failed the connection.
• If there is another firewall between
• The PBX is rejecting
the SIP Proxy and the PBX (for
the certificate of the
example, in the operating system of
SIP Proxy.
the PBX host), verify that the SIP
ports are open.
• Ensure that the root CA certificate
is imported into the PBX. Verify that
the cacert.pem file is located
in /etc/asterisk/tls, and that
the file is readable by Asterisk.
How to Configure TLS with SIP Proxy 8 / 10
Barracuda CloudGen Firewall
Client Works Properly but Error
Messages are Still Displayed
The client can register and works
When a softphone is
properly, but the following error
closed, it sends a
messages are displayed in the log:
request to unregister.
ERROR:core:tls_connect:
However, some
SSL_ERROR_SYSCALL
softphones do not wait You do not need to worry about
err=Success(0)
for a response and quit these error messages unless
ERROR:core:tls_connect: New
immediately. The error something stops working.
TLS connection to :5061
messages indicate that
failed
the SIP Proxy is unable
ERROR:core:tls_connect: TLS
to contact the client
error: 5 (ret=0)
because it has quit.
err=Success(0)
ERROR:core:tcp_send: failed
to send
Asterisk requires
the Common
Name field of the
Asterisk Reports Client as certificate for the SIP As of version 11.2.1, there is no way
UNREACHABLE Proxy to match the to disable this check. You must
Asterisk reports the client as host name of the SIP create the certificate for the SIP
UNREACHABLE, although it should be Proxy. Asterisk takes Proxy again. When asked to enter
registered. The Asterisk log file the IP address of the the Common Name, enter the IP
(/var/log/asterisk/full) SIP Proxy that is seen address of the SIP Proxy that is
repeatedly displays the following as the hostname, but displayed in the error message of
message: you have entered Asterisk. After the certificate is
ERROR[xxxxx] tcptls.c: something else into generated, import it into the
Certificate common name did that field. For this configuration of the SIP Proxy as
not match () reason, Asterisk closes usual.
the connection with the
SIP Proxy, causing the
TCP send errors.
How to Configure TLS with SIP Proxy 9 / 10
Barracuda CloudGen Firewall
Figures
1. pbx1.jpg
2. pbx_sip.jpg
3. pbx_sip_settings.jpg
4. pbx_asterisk.jpg
5. pbx_console.jpg
6. pbx_phonerlite.jpg
7. pbx_phonerlite_2.jpg
© Barracuda Networks Inc., 2021 The information contained within this document is confidential and proprietary to Barracuda Networks Inc. No
portion of this document may be copied, distributed, publicized or used for other than internal documentary purposes without the written consent of
an official representative of Barracuda Networks Inc. All specifications are subject to change without notice. Barracuda Networks Inc. assumes no
responsibility for any inaccuracies in this document. Barracuda Networks Inc. reserves the right to change, modify, transfer, or otherwise revise this
publication without notice.
How to Configure TLS with SIP Proxy 10 / 10
You might also like
- Lab3 SSL TLS Forward Proxy Decryption V1.1Document21 pagesLab3 SSL TLS Forward Proxy Decryption V1.1Cyber SkyNo ratings yet
- Certificates Troubleshooting GuideDocument10 pagesCertificates Troubleshooting GuideAndrei MateiNo ratings yet
- SSL For SharingDocument4 pagesSSL For Sharingshivraj zambareNo ratings yet
- Anyconnect VPN Phone With Certificate Authentication On An Asa Configuration ExampleDocument14 pagesAnyconnect VPN Phone With Certificate Authentication On An Asa Configuration Examplejorigoni2013No ratings yet
- SSL Decryption Certificates TN RevCDocument7 pagesSSL Decryption Certificates TN RevCChau NguyenNo ratings yet
- How To Implement and Test SSL Decryption Palo Alto Networks LiveDocument14 pagesHow To Implement and Test SSL Decryption Palo Alto Networks LiveChau NguyenNo ratings yet
- SW 6 10 Creating and Installing SSL Certificates DV 1 0Document11 pagesSW 6 10 Creating and Installing SSL Certificates DV 1 0Dzmitry KuzmiankouNo ratings yet
- CA Server Using Certificates and SSL in Windows: Student Name: Aishpreet Sran UID:18BCS2835 Section/Group: CSE-17/BDocument6 pagesCA Server Using Certificates and SSL in Windows: Student Name: Aishpreet Sran UID:18BCS2835 Section/Group: CSE-17/BAFAQ CUNo ratings yet
- What Is Asterisk?: What Do We Have? ConfigurationsDocument2 pagesWhat Is Asterisk?: What Do We Have? ConfigurationsClicku NetNo ratings yet
- Asterisk Security Hardening 1.0Document35 pagesAsterisk Security Hardening 1.0DIGIVOIP TUNISIANo ratings yet
- Pki OpensslDocument11 pagesPki OpensslgdeepthiNo ratings yet
- Deploying Certificates Cisco Meeting Server: Design your certificates for CMS services and integrate with Cisco UCM Expressway and TMSFrom EverandDeploying Certificates Cisco Meeting Server: Design your certificates for CMS services and integrate with Cisco UCM Expressway and TMSNo ratings yet
- Network Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityFrom EverandNetwork Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityNo ratings yet
- Common Errors in BW Related To SSLDocument24 pagesCommon Errors in BW Related To SSLKrishna Chaitanya SunkavalliNo ratings yet
- A.5. Creating Your Own CertificatesDocument7 pagesA.5. Creating Your Own CertificatesMaher Saad MechiNo ratings yet
- Supply and Installation of SSL Certificate For Central Statistics Agency (Csa) As-Built DocumentDocument14 pagesSupply and Installation of SSL Certificate For Central Statistics Agency (Csa) As-Built DocumentAhmedin abukiaNo ratings yet
- Generating A Certificate Signing Request (CSR) : CertificatesDocument4 pagesGenerating A Certificate Signing Request (CSR) : CertificatesmohamedNo ratings yet
- SSL GuideDocument9 pagesSSL Guidehelgebaly65No ratings yet
- Encrypting Voice Calls in Elastix and Fail2banDocument8 pagesEncrypting Voice Calls in Elastix and Fail2banGodspower InibuNo ratings yet
- Comprehensive Guide to Setting Up TLS on IronPort ESADocument5 pagesComprehensive Guide to Setting Up TLS on IronPort ESAsvinoth1981No ratings yet
- A VPN Gateway SetupDocument6 pagesA VPN Gateway Setupachmadzulkarnaen100% (1)
- LPI 303-200: SecurityDocument39 pagesLPI 303-200: SecurityBrahim HAMDI100% (1)
- Helix, HackingDocument15 pagesHelix, Hackingjegreen3No ratings yet
- Connect SSL Guide PDFDocument17 pagesConnect SSL Guide PDFshaahin13631363No ratings yet
- Install and Configure Self Signed CertificateDocument4 pagesInstall and Configure Self Signed CertificatePravinNo ratings yet
- Digital Certificates v3Document22 pagesDigital Certificates v3Cinthia Arcos LeiteNo ratings yet
- 18 Setting Up Letsencrypt On Freebsd Younis Said HaniwriterDocument5 pages18 Setting Up Letsencrypt On Freebsd Younis Said HaniwriterNJ LinNo ratings yet
- Enabling SSL On JBoss WildFly Application ServerDocument3 pagesEnabling SSL On JBoss WildFly Application ServerRobert PhoNo ratings yet
- Rsa Netwitness Platform: Blue Coat Proxysg SgosDocument14 pagesRsa Netwitness Platform: Blue Coat Proxysg SgosShirley Diossana GarayNo ratings yet
- Install SSL Certificate on Tomcat ServerDocument13 pagesInstall SSL Certificate on Tomcat Serverbhaip123No ratings yet
- Everything You Wanted To Know About OpensslDocument10 pagesEverything You Wanted To Know About OpensslnakhomNo ratings yet
- FREESWITCH WebRTC 260321 0800 10632Document5 pagesFREESWITCH WebRTC 260321 0800 10632Gazdac ClaudiuNo ratings yet
- Administration Console and CLI Certificate Tools - Zimbra - Tech CenterDocument17 pagesAdministration Console and CLI Certificate Tools - Zimbra - Tech CenterfacundopaganiNo ratings yet
- Creating A Self-Signed Certificate Using Openssl For Use With Microsoft Internet Information Services (Iis) 5Document4 pagesCreating A Self-Signed Certificate Using Openssl For Use With Microsoft Internet Information Services (Iis) 5Nikhil PoojariNo ratings yet
- Install SSL certificates for Qlik NPrintingDocument2 pagesInstall SSL certificates for Qlik NPrintingManuel Gomez FredesNo ratings yet
- Faq Tomcat Soap SSLDocument9 pagesFaq Tomcat Soap SSLhelixneuNo ratings yet
- Nginx Web Server Security Hardening GuideDocument12 pagesNginx Web Server Security Hardening Guidescrib_nokNo ratings yet
- Preface: Howto Set Up Certificate Based Vpns With Check Point Appliances - R80.X EditionDocument35 pagesPreface: Howto Set Up Certificate Based Vpns With Check Point Appliances - R80.X Edition000-924680No ratings yet
- SSL Configuration in SAP PI 7.10Document11 pagesSSL Configuration in SAP PI 7.10Lal NairNo ratings yet
- CSR Certificate CUBE Configure Sip Tls Between Cucm CubeDocument8 pagesCSR Certificate CUBE Configure Sip Tls Between Cucm CubealioossNo ratings yet
- How To Install Third Party SSL Certificates For IPSec VPNDocument15 pagesHow To Install Third Party SSL Certificates For IPSec VPNmartinhache2014No ratings yet
- Create Windows CA Certificate Templates For CUCMDocument32 pagesCreate Windows CA Certificate Templates For CUCMDavid Van HerckNo ratings yet
- W2K16 Active Directory Certificate Services Lab Build PDFDocument56 pagesW2K16 Active Directory Certificate Services Lab Build PDFAnchal SinghNo ratings yet
- Enabling TLS in Oracle Apps R12.2Document41 pagesEnabling TLS in Oracle Apps R12.2Nawab Sharief100% (1)
- SOC Prime SSL Framework v.1.5.2 GuideDocument17 pagesSOC Prime SSL Framework v.1.5.2 GuidenawabkabirNo ratings yet
- How To Secure A FTP Server Using SSLTLS For Secure File Transfer in CentOS 7Document9 pagesHow To Secure A FTP Server Using SSLTLS For Secure File Transfer in CentOS 7Conecta Con DiosNo ratings yet
- Crypto TLSDocument11 pagesCrypto TLSAuliya RusyidaNo ratings yet
- PAN9 EDU210 Lab 11Document20 pagesPAN9 EDU210 Lab 11GenestapowerNo ratings yet
- ESA Wildcard CA Usage TemplateDocument3 pagesESA Wildcard CA Usage TemplateAnonymous cs4BLczENo ratings yet
- Tocf5.Tocf SSLDocument18 pagesTocf5.Tocf SSLbobby briganteNo ratings yet
- The Implementation of COAP SecurityDocument9 pagesThe Implementation of COAP SecurityMohamed Yassine GaraliNo ratings yet
- Generating SSL CertificateDocument8 pagesGenerating SSL Certificatelrc3No ratings yet
- Install Certificate With Lets EncriptyDocument6 pagesInstall Certificate With Lets EncriptyEduin CadeteNo ratings yet
- SSL Interception On Proxy SG - 02 PDFDocument15 pagesSSL Interception On Proxy SG - 02 PDFGsk SkNo ratings yet
- SSL Insight Certificate Installation GuideDocument15 pagesSSL Insight Certificate Installation GuideluisNo ratings yet
- Site To Site IPsec VPNDocument27 pagesSite To Site IPsec VPNRasakiRraskiNo ratings yet
- Forticlient v1.0 Windows App User GuideDocument14 pagesForticlient v1.0 Windows App User GuideJuliano F MadeiraNo ratings yet
- Manual de Creación de Entidad Certificadora LocalDocument7 pagesManual de Creación de Entidad Certificadora LocalMelvin Alvaro Sorto MembreñoNo ratings yet
- Fusion Payment and Positive Pay File Transmission Using SFTP PUT ProtocolDocument10 pagesFusion Payment and Positive Pay File Transmission Using SFTP PUT Protocolsudhirpatil15No ratings yet
- Install Squid Proxy Server On CentOSDocument5 pagesInstall Squid Proxy Server On CentOSMir Farhan Ali AbediNo ratings yet
- URL Fuzzer - Discover Hidden Files and Directories Report (Light)Document1 pageURL Fuzzer - Discover Hidden Files and Directories Report (Light)Hari NarayananNo ratings yet
- URL Fuzzer - Discover Hidden Files and Directories Report (Light)Document2 pagesURL Fuzzer - Discover Hidden Files and Directories Report (Light)Hari NarayananNo ratings yet
- List of Overseas IndianDocument213 pagesList of Overseas Indiansanjay67640No ratings yet
- List of Software Companies in India PDFDocument44 pagesList of Software Companies in India PDFsanthoshinou50% (2)
- ANNEXURE I List of Indian InstitutionsDocument40 pagesANNEXURE I List of Indian InstitutionsamtalksNo ratings yet
- List of Overseas IndianDocument213 pagesList of Overseas Indiansanjay67640No ratings yet
- List of Software Companies in India PDFDocument44 pagesList of Software Companies in India PDFsanthoshinou50% (2)
- Section25 Companies 6nov2008Document70 pagesSection25 Companies 6nov2008Raj KadamNo ratings yet
- ITECH1102 Networking & SecurityDocument6 pagesITECH1102 Networking & SecuritySarah EvanNo ratings yet
- Zte ZXR10 T160G/T64GDocument281 pagesZte ZXR10 T160G/T64GSenthil Rajan33% (3)
- ETH002 - 2 Relays at 16A: Technical DocumentationDocument13 pagesETH002 - 2 Relays at 16A: Technical DocumentationcimlonNo ratings yet
- Powerconnect-8024 User's Guide En-UsDocument1,294 pagesPowerconnect-8024 User's Guide En-Usbakir_abdelNo ratings yet
- Name:: Information Security Management Lab Digital Assignment 1Document8 pagesName:: Information Security Management Lab Digital Assignment 1Sai SandeepNo ratings yet
- Dell Networking z9100 Spec SheetDocument4 pagesDell Networking z9100 Spec SheetlonnieNo ratings yet
- Overview of Comp NWsDocument42 pagesOverview of Comp NWsfahana abdul vahabNo ratings yet
- Openscape Session Border Controller V10: Deployment ScenariosDocument8 pagesOpenscape Session Border Controller V10: Deployment ScenariosiNo ratings yet
- Diya Shaji S7 Ece Roll No: 22Document8 pagesDiya Shaji S7 Ece Roll No: 22Diya ShajiNo ratings yet
- Introduction To TCP - IPDocument16 pagesIntroduction To TCP - IPShriramkumar SinghNo ratings yet
- 3.1 GCP - Routes - and - Firewalls PDFDocument14 pages3.1 GCP - Routes - and - Firewalls PDFgauravecec1980No ratings yet
- Chap 3 CNDocument25 pagesChap 3 CN48Nara Amit GopalNo ratings yet
- Student 8 IP assignment configurationDocument1 pageStudent 8 IP assignment configurationBruno NunesNo ratings yet
- CRS3xx Series Switches - RouterOS - MikroTikDocument18 pagesCRS3xx Series Switches - RouterOS - MikroTikChuks ValentineNo ratings yet
- Centralized IAM supports complianceDocument4 pagesCentralized IAM supports complianceashishvdNo ratings yet
- OWD090901 (Slide) UGW9811 V900R009C01 System Overview-20120319-B-V1.1Document51 pagesOWD090901 (Slide) UGW9811 V900R009C01 System Overview-20120319-B-V1.1WalterLooKungVizurragaNo ratings yet
- LTRUCC-2150 Berlin2017Document44 pagesLTRUCC-2150 Berlin2017Ezo'nun BabasıNo ratings yet
- MTX 4104 Mgcp-Ncs ReferenceDocument276 pagesMTX 4104 Mgcp-Ncs ReferenceeduardoantonsNo ratings yet
- Fortigate SSL VPN With LDAP User AuthenticationDocument52 pagesFortigate SSL VPN With LDAP User AuthenticationAnonymous k2SY4zdI3No ratings yet
- Linux SRVDocument235 pagesLinux SRVMarius SofariuNo ratings yet
- Soal Mtcna Terbaru PDFDocument4 pagesSoal Mtcna Terbaru PDFmariska adilasariNo ratings yet
- MACSec Op Test SuiteDocument37 pagesMACSec Op Test SuiteAbhimanyu AdityaNo ratings yet
- Module 2Document7 pagesModule 2هبة عمار كاظمNo ratings yet
- Setup a transparent firewall with pfSenseDocument5 pagesSetup a transparent firewall with pfSenseKo Aye ChanNo ratings yet
- Cisco IOS IP Configuration Guide: Release 12.2Document624 pagesCisco IOS IP Configuration Guide: Release 12.2eterrazas100% (1)
- Lab 1 - BGP PeeringDocument72 pagesLab 1 - BGP PeeringSnowie OWNo ratings yet
- Chapter 1 Computer Network and InternetDocument50 pagesChapter 1 Computer Network and InternetDu TrầnNo ratings yet
- Cisco TD-Book-Wrapper PDFDocument162 pagesCisco TD-Book-Wrapper PDFJulio ApNo ratings yet
- DESIGNING AND SUPPORTING COMPUTER NETWORK FileDocument28 pagesDESIGNING AND SUPPORTING COMPUTER NETWORK FileKarandeep Singh100% (4)
- Data Center Network FailureDocument90 pagesData Center Network Failurefalberto08No ratings yet