Professional Documents
Culture Documents
Dbms Da
Uploaded by
Anurag KarkiOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Dbms Da
Uploaded by
Anurag KarkiCopyright:
Available Formats
VELLORE INSTITUTE OF TECHNOLOGY, VELLORE
SCHOOL OF COMPUTER SCIENCE AND ENGINEERING
CSE2004 DATABASE MANAGEMENT SYSTEMS
FALL 2021-22 SLOT B1 AND B2
DIGITAL ASSIGNMENT 2
Instructions:
1. The answers can be scan of handwritten (preferable) or typed with computer generated
diagrams
2. Submit your own answers
Answer the following questions (5 x 4 = 20)
1. Characterising schedule based on recoverability (non-recoverable, recoverable,
cascadeless, strict) – give the most specific character of the schedule stating the reasons
a. S: w1(Y); r2(X); c2; c1; r3(Y); c3;
b. S: w1(X); r2(X); c2; c1; r3(Y); c3;
c. S: w1(Y); r2(X); c2; w3(Y); c3; c1;
2. Check the following schedule S for Conflict serializability and give the serial equivalent
schedule in case it is a conflict serializable one.
a. S: r1(A); r2(A); r3(A); w1(A); r2(C); r2(B); w2(B); w1(C);
b. S: r1(A); r2(A); r3(A); w1(A); r2(C); r2(B); w2(B); w1(C); w2(A)
3. Discuss the different deadlock prevention, detection and recovery schemes of lock based
concurrency control with suitable examples for each technique. Also state the advantages
and disadvantages for each procedure to handle deadlock.
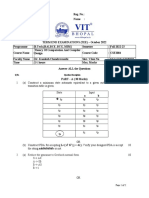
4. Convert the given transactions T1 and T2 or their concurrent execution using strict two
phase locking and comment on occurrence of a schedule with deadlock from the modified
transactions.
T1: T2:
read(A) read(B)
if (A > 50) B = B+20
A = A-50 write(B)
write(A) read(A)
read(B) A = A-20
B = B +50 write(A)
write(B)
end
5. Check whether the following partial schedule is valid under timestamp ordering protocol
with and without Thomas write rule. Assume initial timestamps of data items to be 0.
S: r3(A); r2(A); r1(B); w1(A); r2(C); r2(B); w2(B); w1(C); r1(A); c1; c2; c3
You might also like
- Charles University Admission AssignmentDocument4 pagesCharles University Admission AssignmentnizarNo ratings yet
- Dbms S5Document7 pagesDbms S5Avinash SinghNo ratings yet
- Transactions and Concurrency ControlDocument6 pagesTransactions and Concurrency Controlbhavesh agrawalNo ratings yet
- Dbms S4Document10 pagesDbms S4Avinash SinghNo ratings yet
- Transactions and Concurrency Control QuestionsDocument7 pagesTransactions and Concurrency Control Questionsbhavesh agrawalNo ratings yet
- DBMS Ques-3Document1 pageDBMS Ques-3XoroNo ratings yet
- DBMS Solution-7Document10 pagesDBMS Solution-721SUCA019 - HARI PRAKASH S B.C.A (SELF)No ratings yet
- Ps 5Document4 pagesPs 5Andres Nicolas ZartaNo ratings yet
- Study Material XII Computer ScienceDocument216 pagesStudy Material XII Computer Scienceutsav kakkadNo ratings yet
- Pyq 2020-2023 Sem2-1Document17 pagesPyq 2020-2023 Sem2-1Aditya RajNo ratings yet
- Sample Question Paper - 1 Class-Xii Sub: Computer ScienceDocument14 pagesSample Question Paper - 1 Class-Xii Sub: Computer ScienceSjhsjsjNo ratings yet
- Worksheet 3 CsipDocument7 pagesWorksheet 3 CsipPal KansaraNo ratings yet
- 3 - Exponential Log Functions Chapter ReviewDocument10 pages3 - Exponential Log Functions Chapter ReviewMath 30-1 EDGE Study Guide Workbook - by RTD LearningNo ratings yet
- DBMS E21 E22 E23 Cse3001 1Document2 pagesDBMS E21 E22 E23 Cse3001 1bhavuksaraswat32No ratings yet
- Concurrency Control Contents Concurrency Control Concurrency ControlDocument114 pagesConcurrency Control Contents Concurrency Control Concurrency Controlmohammad jafariNo ratings yet
- Csi ZG518 Ec-3m Second Sem 2021-2022Document8 pagesCsi ZG518 Ec-3m Second Sem 2021-2022anishjiNo ratings yet
- 2021 - Compiler Design (Csen 4111)Document5 pages2021 - Compiler Design (Csen 4111)poxemik697covbasecomNo ratings yet
- Compiler Construction NotesDocument5 pagesCompiler Construction Notespoxemik697covbasecomNo ratings yet
- KRM Term 1 ExamDocument9 pagesKRM Term 1 Examcookingfeverr.exprimentsNo ratings yet
- L-3/T - 2/EEE Date: 28/0312022: IS) +D (I, 3,6,7)Document19 pagesL-3/T - 2/EEE Date: 28/0312022: IS) +D (I, 3,6,7)Sanjid ElahiNo ratings yet
- KENDRIYA VIDYALAYA SANGATHAN, JABALPUR REGION FIRST PREBOARD EXAMINATION(2022-23) CLASS - XII Computer Science (083) MARKING SCHEMEDocument5 pagesKENDRIYA VIDYALAYA SANGATHAN, JABALPUR REGION FIRST PREBOARD EXAMINATION(2022-23) CLASS - XII Computer Science (083) MARKING SCHEMETRAP GAMINGNo ratings yet
- Data Structure Using 'C' 3 Hours 100: Third Semester Examination, 2016-17Document2 pagesData Structure Using 'C' 3 Hours 100: Third Semester Examination, 2016-17parvez ahmadNo ratings yet
- Set 1 Xii CS PB2 MSDocument4 pagesSet 1 Xii CS PB2 MSharshitapawar3010No ratings yet
- Test Id 64Document17 pagesTest Id 64Soumya MukherjeeNo ratings yet
- 2016 IT601 DBMS OldDocument3 pages2016 IT601 DBMS OldSUCHHANDA CHAKRABORTYNo ratings yet
- class 11 CS QP HYADocument4 pagesclass 11 CS QP HYAGracy amutharajNo ratings yet
- Database Test 2: 35 Questions on Database ConceptsDocument6 pagesDatabase Test 2: 35 Questions on Database ConceptsAKASH PALNo ratings yet
- Compiler Design Bcs Ai 3dDocument4 pagesCompiler Design Bcs Ai 3dSajal KunduNo ratings yet
- QP Class Xii CS PB 2022Document8 pagesQP Class Xii CS PB 2022SANJAY PARMARNo ratings yet
- Air Force Schools Computer Science Pre-Board Exam QuestionsDocument16 pagesAir Force Schools Computer Science Pre-Board Exam QuestionsARNAV TYAGINo ratings yet
- Comprehensive Study Material for IIT-JEE Main & AdvancedDocument13 pagesComprehensive Study Material for IIT-JEE Main & AdvancedMayank TiwaryNo ratings yet
- Complete Mathematics—JEE Main Problems and SolutionsDocument8 pagesComplete Mathematics—JEE Main Problems and SolutionsSanjay GuptaNo ratings yet
- Cse 205Document39 pagesCse 205sharminmin92No ratings yet
- ICT 9A04306 Digital Logic DesignDocument1 pageICT 9A04306 Digital Logic DesignMahaboob SubahanNo ratings yet
- Database Serializability and Two-Phase LockingDocument8 pagesDatabase Serializability and Two-Phase Lockingabinet kindieNo ratings yet
- CS GATE Paper 2009 Questions 1-20Document13 pagesCS GATE Paper 2009 Questions 1-20khemanand_2000No ratings yet
- KVPY SA 2017 Maths Question Answerkey SolutionsDocument1 pageKVPY SA 2017 Maths Question Answerkey SolutionsSaloni KumariNo ratings yet
- Csi ZG518 Ec-3r Second Sem 2021-2022Document8 pagesCsi ZG518 Ec-3r Second Sem 2021-2022anishjiNo ratings yet
- Gate-Cs 2006Document31 pagesGate-Cs 2006tomundaNo ratings yet
- 1694681565Document4 pages1694681565Jaimin PatelNo ratings yet
- CSE2004-Theory of Computation and Compiler Design-TEEDocument2 pagesCSE2004-Theory of Computation and Compiler Design-TEEUtkarsh KumarNo ratings yet
- Logarithm DPPDocument6 pagesLogarithm DPPMohini Devi100% (2)
- Baulko 4U Exam QuestionsDocument15 pagesBaulko 4U Exam QuestionsasjvbsajkvbasjkvasbvjkNo ratings yet
- Homework 1Document2 pagesHomework 1Vu LeNo ratings yet
- University of Zimbabwe: Time: 2 HoursDocument4 pagesUniversity of Zimbabwe: Time: 2 Hourslynn zigaraNo ratings yet
- 12th - CS Preboard - Set ADocument7 pages12th - CS Preboard - Set AtslingesswarNo ratings yet
- Normalization and database design fundamentalsDocument12 pagesNormalization and database design fundamentalsHande ÖzerNo ratings yet
- Cs337 Principles of Compiler Design - May-Jun2007Document3 pagesCs337 Principles of Compiler Design - May-Jun2007Akash GoswamiNo ratings yet
- Computer SC Specimen QP Class XiDocument7 pagesComputer SC Specimen QP Class XiAshutosh Raj0% (1)
- Class 11 Term 1 IscDocument10 pagesClass 11 Term 1 IscȺղʂհNo ratings yet
- General Linear Transformations Chapter: Multiple Choice & Free Response QuestionsDocument7 pagesGeneral Linear Transformations Chapter: Multiple Choice & Free Response QuestionsSaif BaneesNo ratings yet
- CT5 CS FinalDocument14 pagesCT5 CS FinalVivek KumarNo ratings yet
- KVPY SA 2017 Maths Question Answerkey SolutionsDocument16 pagesKVPY SA 2017 Maths Question Answerkey Solutionsvidyakumari808940No ratings yet
- Control System 1Document31 pagesControl System 1Rakibul Hasan RakibNo ratings yet
- XII CsDocument6 pagesXII CsHARIGANESHNo ratings yet
- Btech Cs 6 Sem Data Compression Kcs 064 2023Document2 pagesBtech Cs 6 Sem Data Compression Kcs 064 2023Yash ChauhanNo ratings yet
- Ex 2Document2 pagesEx 2statsoNo ratings yet
- GATE 2006 CS question paper with answersDocument17 pagesGATE 2006 CS question paper with answersKhushboo DhakadNo ratings yet
- Answers to Selected Problems in Multivariable Calculus with Linear Algebra and SeriesFrom EverandAnswers to Selected Problems in Multivariable Calculus with Linear Algebra and SeriesRating: 1.5 out of 5 stars1.5/5 (2)