0% found this document useful (0 votes)
438 views15 pagesWindows Forensics: Dr. Phil Polstra @ppolstra PHD, Cissp, Ceh
Uploaded by
karlaCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd
0% found this document useful (0 votes)
438 views15 pagesWindows Forensics: Dr. Phil Polstra @ppolstra PHD, Cissp, Ceh
Uploaded by
karlaCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd
- Introduction: Introduces the author and the purpose of the Windows Forensics course, setting context for the entire document.
- About Me: Details the author's professional background and expertise, establishing credibility in the field of digital forensics.
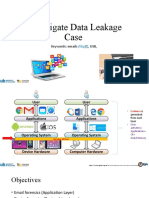
- Live Response Techniques: Covers strategies for live response including human interactions, creating kits, and determining data collection methods.
- Filesystem and Disk Analysis: Explains analyzing filesystems using tools like TSK and Autopsy, and delves into disk editors and filesystems.
- Network and File Forensics: Examines network forensics involving packet captures, and file forensics including file signatures and web browsing history.
- Memory Forensics and Malware Analysis: Discusses advanced forensics techniques related to memory, malware analysis, and registry forensics.
- Course Goals and Conclusion: Outlines the course's overarching objectives, emphasizing open-source tools and hands-on exercises.