Professional Documents
Culture Documents
Software Defenses (Part 2) Virtualization and Malware: CS 475 Rachel Greenstadt April 23, 2015
Uploaded by
J A Y T R O N0 ratings0% found this document useful (0 votes)
7 views55 pagesThe document discusses using virtualization for malware detection. It describes how virtualization can provide isolation, tamper resistance, and safety to analyze malware in a controlled environment. Virtual machines allow malware to be run and have their behavior observed without risking harm to other systems. Features like rewind/replay also enable detailed analysis of malware behavior. Overall, virtualization provides useful tools for detecting malware in a safe, isolated manner.
Original Description:
Original Title
CS475-15-05
Copyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentThe document discusses using virtualization for malware detection. It describes how virtualization can provide isolation, tamper resistance, and safety to analyze malware in a controlled environment. Virtual machines allow malware to be run and have their behavior observed without risking harm to other systems. Features like rewind/replay also enable detailed analysis of malware behavior. Overall, virtualization provides useful tools for detecting malware in a safe, isolated manner.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
7 views55 pagesSoftware Defenses (Part 2) Virtualization and Malware: CS 475 Rachel Greenstadt April 23, 2015
Uploaded by
J A Y T R O NThe document discusses using virtualization for malware detection. It describes how virtualization can provide isolation, tamper resistance, and safety to analyze malware in a controlled environment. Virtual machines allow malware to be run and have their behavior observed without risking harm to other systems. Features like rewind/replay also enable detailed analysis of malware behavior. Overall, virtualization provides useful tools for detecting malware in a safe, isolated manner.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
You are on page 1of 55
Software Defenses (part 2)
Virtualization and Malware
CS 475 Rachel Greenstadt
April 23, 2015
Thursday, April 23, 15
Virtualization and
Security
• Background on virtualization
• Virtualization to protect software/platforms from malware
• Virtualization to detect malware
• Virtualized malware
Thursday, April 23, 15
What is virtualization?
Abstraction of computational resources
Thursday, April 23, 15
Examples of
virtualization
• Emulation – translate all instructions
• QEMU, Bochs
• Paravirtualization – requires changes to OS
• UML, Xen
• Native virtualization – require same architecture, most
instructions executed natively
• VMWare, virtual box
• More efficient due to hardware support (Intel-VT)
• OS-Level virtualization – same OS, isolate resources
• VServer, iOS
Thursday, April 23, 15
Virtualization and
Security
• Isolate and protect software from malicious programs
(malware)
• Sandbox programs in own address space
• Mediate with lean, secure VMM
• Detect malware
• Use emulation to run malware in a safe environment
• Stop, move, replay events in virtual machines
• Virtualized malware
• Rootkits that hide underneath OS
Thursday, April 23, 15
Virtualization for Isolation
• Presenting virtual interfaces to resources can limit and
control the access of malicious programs to resources
• A Virtual Machine Monitor (VMM) can do more rigorous
access control
Thursday, April 23, 15
Isolation
• Current applications have no isolation
• Solitaire can access network, camera, user documents,
passwords etc
• Programs execute in virtual machines (or sandboxes or
jails) that can only see its own files/processes
• Programs must request additional permissions from the
VMM
Thursday, April 23, 15
One Laptop Per Child
• OLPC project aims to
give all children laptops
• Cannot demand 6 year
old children secure
their machines
• Need way to allow
them to get hacked
and still be ok • Apple takes a similar
approach with iOS
• Answer: virtualization
Thursday, April 23, 15
Thin Hypervisor
• Existing OS kernels too big
and complex to avoid
vulnerability
• Small hypervisor does
scheduling, isolation
• Parent partition manages
permissions
• Keep hypervisor secure
• Push dangerous apps into
• Windows Server
virtual machines
Thursday, April 23, 15
Malware Detection
with Virtualization
• Many properties of virtualization useful for detecting
malicious software
• Tamper resistance
• Safety/Isolation
• Instrumentation
• Rewind/replay properties
Thursday, April 23, 15
What is Malware?
• Malware (malicious software) is any program
that works against the interest of the system’s
user or owner.
• Question: Is a program that spies on the web
browsing habits of the employees of a
company considered malware?
• What if the CEO authorized the installation of
the spying program?
Thursday, April 23, 15
Typical purposes of Malware
• Backdoor access:
– Attacker gains unlimited access to the machine.
• Denial-of-service (DoS) attacks:
– Infect a huge number of machines to try simultaneously to
connect to a target server in hope of overwhelming it and
making it crash.
• Vandalism:
– E.g., defacing a web site.
• Resource Theft:
– E.g., stealing other user’s computing and network resources,
such as using your neighbors’ Wireless Network.
• Information Theft:
– E.g., stealing other user’s credit card numbers.
Thursday, April 23, 15
Types of Malware
• Viruses
• Worms
• Trojan Horses
• Backdoors
• Mobile code
• Adware
• Sticky software
Thursday, April 23, 15
Viruses
• Viruses are self-replicating programs that
usually have a malicious intent.
• Old fashioned type of malware that has
become less popular since the widespread
use of the Internet.
• The unique aspect of computer viruses is
their ability to self-replicate.
• However, someone (e.g., user) must execute
them in order for them to propagate.
Thursday, April 23, 15
Viruses (Cont’d)
• Some viruses are harmful (e.g.,):
– delete valuable information from a computer’s
disk,
– freeze the computer.
• Other viruses are harmless (e.g.,):
– display annoying messages to attract user
attention,
– just replicate themselves.
Thursday, April 23, 15
Viruses: Operation
• Viruses typically attach themselves to
executable program files
– e.g., .exe files in MS Windows
• Then the virus slowly duplicates itself
into many executable files on the
infected system.
• Viruses require human intervention to
replicate.
Thursday, April 23, 15
Origin of the term
computer virus
• The term computer virus was first used in an
academic publication by Fred Cohen in his 1984
paper Experiments with Computer Viruses.
• However, a mid-1970s science fiction novel by David
Gerrold, When H.A.R.L.I.E. was One, includes a
description of a fictional computer program called
VIRUS.
• John Brunner's 1975 novel The Shockwave Rider
describes programs known as tapeworms which
spread through a network for deleting data.
• The term computer virus also appears in the comic
book Uncanny X-Men in 1982.
Thursday, April 23, 15
The first computer viruses
• A program called Elk Cloner is credited with being the
first computer virus to appear "in the wild". Written in
1982 by Rich Skrenta, it attached itself to the Apple
DOS 3.3 operating system and spread by floppy disk.
• The first PC virus was a boot sector virus called
(c)Brain, created in 1986 by two brothers, Basit and
Amjad Farooq Alvi, operating out of Lahore, Pakistan.
Thursday, April 23, 15
Worms
• Worms are malicious programs that use the Internet
to spread.
• Similar to a virus, a worm self-replicates.
• Unlike a virus, a worm does not need human
intervention to replicate.
• Worms have the ability to spread uncontrollably in a
very brief period of time.
– Almost every computer system in the world is attached to the
same network.
Thursday, April 23, 15
Worms: Operation
• A worm may spread because of a software
vulnerability exploit:
– Takes advantage of the OS or an application program with
program vulnerabilities that allow it to hide in a seemingly
innocent data packet.
• A worm may also spread via e-mail.
– Mass mailing worms scan the user’s contact list and mail
themselves to every contact on such a list.
– In most cases the user must open an attachment to trigger
the spreading of the worm (more like a virus).
Thursday, April 23, 15
Trojan horses
• A Trojan Horse is a seemingly innocent
application that contains malicious code
that is hidden somewhere inside it.
• Trojans are often useful programs that
have unnoticeable, yet harmful, side
effects.
Thursday, April 23, 15
Trojan horses: Operation (1)
• Embed a malicious element inside an
otherwise benign program.
• The victim:
1. receives the infected program,
2. launches it,
3. remains oblivious of the fact that the system has
been infected.
– The application continues to operate
normally to eliminate any suspicion.
Thursday, April 23, 15
Trojan horses: Operation (2)
• Fool users into believing that a file containing a
malicious program is really an innocent file such as a
video clip or an image.
• This is easy to do on MS Windows because file types
are determined by their extension as opposed to
examining the file headers.
• E.g.,
– “A Great Picture.jpg .exe”
– The .exe might not be visible in the browser.
– The Trojan author can create a picture icon that is the
default icon of MS Windows for .jpg files.
Thursday, April 23, 15
Backdoors
• A backdoor is malware that creates a
covert access channel that the attacker
can use for:
– connecting,
– controlling,
– spying,
– or otherwise interacting with the victim’s
system.
Thursday, April 23, 15
Backdoors: Operation
• Backdoors can be embedded in actual
programs that, when executed, enable the
attacker to connect to and to use the system
remotely.
• Backdoors may be planted into the source
code by rogue software developers before
the product is released.
– This is more difficult to get away with if the
program is open source.
Thursday, April 23, 15
Mobile code
• Mobile code is a class of benign programs that are:
– meant to be mobile,
– meant to be executed on a large number of systems,
– not meant to be installed explicitly by end users.
• Most mobile code is designed to create a more active
web browsing experience.
– E.g., Java applets, ActiveX controls.
Thursday, April 23, 15
Mobile code (Cont’d)
• Java scripts are distributed in source
code form making them easy to
analyze.
• ActiveX components are conventional
executables that contain native IA-32
machine code.
• Java applets are in bytecode form,
which makes them easy to decompile.
Thursday, April 23, 15
Mobile code: Operation
• Web sites quickly download and launch a program on
the end user’s system.
• User might see a message that warns about a
program that is about to be installed and launched.
– Most users click OK to allow the program to run.
– They may not consider the possibility that malicious code is
about to be downloaded and executed on their system.
Thursday, April 23, 15
Adware
• Adware is a program that forces unsolicited
advertising on end users.
• Adware is a new category of malicious
programs that has become very popular.
• Adware is usually bundled with free software
that is funded by the advertisements
displayed by the Adware program.
Thursday, April 23, 15
Adware: Operation (1)
• The program gathers statistics about the end
user’s browsing and shopping habits.
– The data might be transferred to a remote server.
• Then the Adware uses the information to
display targeted advertisements to the end
user.
Thursday, April 23, 15
Adware: Operation (2)
• Adware can be buggy and can limit the
performance of the infected machine.
– E.g., MS IE can freeze for a long time
because an Adware DLL is poorly
implemented and does not use
multithreading properly.
• Ironically, buggy Adware defeats the
purpose of the Adware itself.
Thursday, April 23, 15
Malvertising
• Malicious online ads as a source of malware
• Visit malicious site (spam/phish, social
network, SEO, compromised site, malware ads
on legit site)
• Landing site (often dynamic) / malware
payload
• Flash 0-day Dec 2014 - Feb 2015, popular ad network, HanJuan
exploit kit. Targeted. Reputable sites (huffington post, dailymotion,
nydailynews, others in alexa top 1000)
Thursday, April 23, 15
Sticky software
• Sticky software implements methods that prevent or
deter users from uninstalling it manually.
• One simple solution is not to offer an uninstall
program.
• Another solution in Windows involves:
– installing registry keys that instruct Windows to always
launch the malware as soon as the system is booted.
– The malware monitors changes to the registry and replace
the keys of they are deleted by the user.
– The malware uses two mutually monitoring processes to
ensure that the user does not terminate the malware before
deleting the keys.
Thursday, April 23, 15
Future Malware
• Today’s malware is just the tip of the iceberg.
• The next generation of malware may take
control of the low levels of the computer
system (e.g., BIOS, Firmware).
– The antidote software will be in the control of the
malware …
• Also the theft of valuable information can
result in holding it for ransom.
Thursday, April 23, 15
Information-stealing worms
• Present-day malware does not take
advantage of cryptography much.
• Asymmetric encryption creates new
possibilities for the creation of
information-stealing worms.
• A worm encrypts valuable data on the
infected system using an asymmetric
cipher and hold the data as ransom.
Thursday, April 23, 15
Information-stealing
worms:Operation
1. The Kleptographic worm embeds a public
encryption key in its body.
2. It starts encrypting every bit of valuable data on the
host using the public key.
3. Decryption of the data is impossible without the
private key.
4. Attacker blackmails the victim demanding ransom.
5. Attacker exchanges the private key for the ransom
while maintaining anonymity.
– Theoretically possible using zero-knowledge proofs
– Attacker proves that he has the private key without exposing it.
Thursday, April 23, 15
BIOS/Firmware Malware
• Antivirus programs assume that there is always some
trusted layer of the system.
• Naïve antivirus programs scan the hard drive for
infected files using the high-level file-system service.
• A clever virus can intercept file system calls and
present to the virus with fake versions
(original/uninfected) of the files on disk.
• Sophisticated antivirus programs reside at a low
enough level (in OS kernel) so that malware cannot
distort their view of the system.
Thursday, April 23, 15
BIOS/Firmware Malware:
Operations (1)
• What is the malware altered an extremely low level
layer of the system?
• Most CPUs/hardware devices run very low-level code
that implements each assembly language instruction
using low level instructions (micro-ops).
• The micro-ops code that runs inside the processor is
called firmware.
• Firmware can be updated using a firmware-updating
program.
Thursday, April 23, 15
BIOS/Firmware Malware:
Operations (2)
• Malicious firmware can (in theory) be
included in malware that defeats
antivirus programs.
• The hardware will be compromised by
the malicious firmware.
• Not easy to do in practice because
firmware update files are encrypted
(private key inside the processor).
Thursday, April 23, 15
Antivirus programs
• Antivirus programs identify malware by looking for
unique signatures in the code of each program (i.e.,
potential virus) on a computer.
– A signature is a unique sequence of code found in a part of
the malicious program.
• The antivirus program maintains a frequently updated
database of virus signatures.
– The goal is for the database to contain a signature for every
known malware program.
• Well known antivirus software includes:
– Symantec (http://www.symantec.com)
– McAfee (http://www.mcafee.com)
Thursday, April 23, 15
Polymorphic viruses
• Polymorphism is a technique that thwarts
signature-based identification programs.
• Polymorphic viruses randomly encode or
encrypt the program code in a semantics-
preserving way.
• The idea is to encrypt the code with a random
key and decrypt it at runtime.
– Each copy of the code is different because of the
use of a random key.
Thursday, April 23, 15
Polymorphic viruses:
Decryption technique
• A decryption technique that polymorphic
viruses employ involves “XORing” each
byte with a randomized key that was
saved by the parent virus.
• The use of XOR-operations has the
additional advantage that the encryption
and decryption routine are the same:
– a xor b = c
– c xor b = a
Thursday, April 23, 15
Polymorphic viruses:
Weaknesses
• Many antivirus programs scan for virus signatures in
memory.
– I.e., after the polymorphic virus has been decrypted.
• If the virus code that does the decryption is static,
then the decryption code can be used as a signature.
• This limitation can be addressed (somewhat) if the
decryption code is scrambled (superficially):
– randomize the use of registers,
– add no-ops in the code, …
Thursday, April 23, 15
Metamorphic viruses
• Instead of encrypting the program’s body and
making slight alterations in the decryption
engine, alter the entire program each time it
is replicated.
• This makes it extremely difficult for antivirus
writers to use signature-matching techniques
to identify malware.
• Metamorphism requires a powerful code
analysis engine that needs to be embedded
into the malware.
Thursday, April 23, 15
Metamorphic viruses:
Operation
• Metamorphic engine scans the code and generates a
different version of it every time the program is
duplicated.
• The metamorphic engine performs a wide variety of
transformations on the malware and on the engine
itself.
– Instruction and register randomization.
– Instruction ordering
– Reversing (negating) conditions
– Insertion of “garbage” instructions
– Reordering of the storage location of functions
Thursday, April 23, 15
Emulation/Virtualization
in Anti-Virus Tools
• Modern viruses use polymorphism/metamorphism to evade
detection by signature
• One way to detect this malware is through emulation in
an isolated virtual machine
• Specific emulation techniques can be countered by virus
authors (due to limitations on previous slide)
• Result: security through obscurity works here, want to
use a different anti-virus tool than the masses
Thursday, April 23, 15
Limitations of Using
Virtualization for Malware
• Rice's theorem – nontrivial properties of computer programs
cannot be determined automatically
• Semantic gap – more context inside of a virtual
machine than outside of it
• An operating system sees processes and files versus
registers, disk blocks and memory pages outside
• Instrumentation can help (but possibly corruptible)
Thursday, April 23, 15
Bridging the Semantic
Gap
• Xuxian Jiang et al ACM CCS 2007
• Recreate internal state externally in the VMM (bridge the
semantic gap)
• Reconstruct files/directories from raw virtual disk
• Reconstruct process information from virtual memory
• Compare internal view with reconstructed view to find
root kits
• View reconstruction good enough to run out-of-the-box
anti-virus software (Symantec, Kapersky, McAfee, F-
Secure, etc)
Thursday, April 23, 15
Finding Malicious
Websites
• web 2.0 means websites can infect machines using browser
vulnerabilities
• Compromised hosting facilities mean not just sketchy
websites
• Google used VMs to analyze web-based malware
• Run IE in a virtual machine
• Record all HTTP fetches, new processes, changes to
registry and file systems
Thursday, April 23, 15
Anti-VM Malware
• Flash 0-day discussed earlier checked to
see if client was using a VM or web proxy
• Did not infect (defense?)
• Today’s sophisticated malware has anti-VM
anti-analysis features
Thursday, April 23, 15
Virtualized Malware
• Not all added security, new opportunities for malware
• Virtualized rootkits
• Side Channel attacks
• Bugs in VMMs
Thursday, April 23, 15
Take the “Blue Pill”
• Developed by Joanna Rutkowska
• VMM as root kit
• Instead of hiding your control of a compromised system
in the kernel, insert thin hypervisor below it
• Runs at a higher level of privilege, so can still control the
machine
• Hard to detect within the OS
Thursday, April 23, 15
Techniques to Detect
Virtualized Malware
• Very difficult to hide that virtualization is happening
• Timing issues
• TLB profiling
• Defeating these requires a big code base
• Hard to distinguish “good” VMM from “bad” VMM
Thursday, April 23, 15
Side Channel Attacks
• How isolated are virtual machines?
• Can they spy on each other?
• VMs share the resources of a single host
• If multiple VMs try to use the same resource they may
notice
• Mitigated by only allowing each machine a specified
share of the resource
• But not completely, and at great efficiency loss
Thursday, April 23, 15
Conclusions
• Virtualization has important security implications
• “Arms race” between hackers and defenders
• Lot of interesting work in this space
Thursday, April 23, 15
You might also like
- Penetration Testing Fundamentals-2: Penetration Testing Study Guide To Breaking Into SystemsFrom EverandPenetration Testing Fundamentals-2: Penetration Testing Study Guide To Breaking Into SystemsNo ratings yet
- Software Defenses (Part 2) Virtualization and Malware: CS 475 Rachel Greenstadt April 23, 2015Document55 pagesSoftware Defenses (Part 2) Virtualization and Malware: CS 475 Rachel Greenstadt April 23, 2015J A Y T R O NNo ratings yet
- The Malware Menagerie: Roger ClarkeDocument12 pagesThe Malware Menagerie: Roger Clarkekittysingla40988No ratings yet
- Cyber AttacksDocument35 pagesCyber AttacksAskar SerekeNo ratings yet
- Security Cyber: Codrin Herţanu, Colonel, PH.DDocument23 pagesSecurity Cyber: Codrin Herţanu, Colonel, PH.DCristina PaliuNo ratings yet
- SIS MalwareDocument45 pagesSIS MalwareShporetNo ratings yet
- Cyber Espionage, Infiltration and Combating Techniques: - by Atul Agarwal & CERT-INDocument22 pagesCyber Espionage, Infiltration and Combating Techniques: - by Atul Agarwal & CERT-INyawahabNo ratings yet
- Chapter 19: Malicious Software: Fourth Edition by William StallingsDocument23 pagesChapter 19: Malicious Software: Fourth Edition by William Stallingsmsdeepikalal7No ratings yet
- Day 2Document28 pagesDay 2aNo ratings yet
- Slide-Worm Part 1Document39 pagesSlide-Worm Part 1Nhật HuyNo ratings yet
- Day 1Document70 pagesDay 1aNo ratings yet
- Cce-Edusat Session For Computer FundamentalsDocument37 pagesCce-Edusat Session For Computer FundamentalsGemark AlmacenNo ratings yet
- 7 - Security Malware Threats Section PDFDocument23 pages7 - Security Malware Threats Section PDFnallamalli subramanyamNo ratings yet
- Mal WareDocument24 pagesMal WareJomon JosephNo ratings yet
- Malicious SoftwaresDocument23 pagesMalicious Softwaresjyoti sakreNo ratings yet
- Ch.14 Network Threats and MitigationDocument32 pagesCh.14 Network Threats and Mitigationvictorbittar29No ratings yet
- Documento 1 CiberDocument117 pagesDocumento 1 CiberoggunomiNo ratings yet
- Lecture 1Document37 pagesLecture 1melakmubettyNo ratings yet
- Legal-Ethics-Lecture 3Document40 pagesLegal-Ethics-Lecture 3Dustin OdoiNo ratings yet
- Virtualization - Dark Web Forensics Using Csi Linux: Deborah K. Wells, Lecturer, CWUDocument48 pagesVirtualization - Dark Web Forensics Using Csi Linux: Deborah K. Wells, Lecturer, CWUpicturesbyprathameshNo ratings yet
- Chapter - 7Document97 pagesChapter - 7Miretu JaletaNo ratings yet
- Lecture 3 - Program SecurityDocument60 pagesLecture 3 - Program SecurityAbdulelah AlnhariNo ratings yet
- Nad Ns Unit6-Part1Document20 pagesNad Ns Unit6-Part1Akshay UtaneNo ratings yet
- Chapter 2-Computer System ThreatDocument37 pagesChapter 2-Computer System Threatminase TesfayeNo ratings yet
- Insiderthreats 150305131515 Conversion Gate01Document14 pagesInsiderthreats 150305131515 Conversion Gate01Anoop PattatNo ratings yet
- Introduction (Viruses, Bombs, Worms) - Types of Viruses - Characteristics of Viruses - Categories of Viruses - Computer SecurityDocument36 pagesIntroduction (Viruses, Bombs, Worms) - Types of Viruses - Characteristics of Viruses - Categories of Viruses - Computer SecurityMd Sajjad HossainNo ratings yet
- Malware: (Malicious Ware)Document25 pagesMalware: (Malicious Ware)samwel sittaNo ratings yet
- Linux System Safety: ThreatsDocument8 pagesLinux System Safety: ThreatsdennyNo ratings yet
- ch04 MalwareDocument41 pagesch04 MalwareUdkhul Rogodan Chalata DoaNo ratings yet
- 3vulnerability Management DICTDocument41 pages3vulnerability Management DICTLGU GALIMUYODNo ratings yet
- CCNA Enterprise 200 301 Modul5Document79 pagesCCNA Enterprise 200 301 Modul5Foryanto J. Wiguna100% (2)
- Viruses Worms and Other MalawareDocument49 pagesViruses Worms and Other MalawareMayank SinghNo ratings yet
- What Is Internet Security - Web Services - Security Threats - Security AttacksDocument17 pagesWhat Is Internet Security - Web Services - Security Threats - Security AttacksUday VermaNo ratings yet
- System SecurityDocument18 pagesSystem SecurityamirNo ratings yet
- CSCLDocument9 pagesCSCLNe PaliNo ratings yet
- 02 - Information SecurityDocument47 pages02 - Information SecurityNonthaphon VattanataysanunNo ratings yet
- Overview of Computer SecurityDocument42 pagesOverview of Computer SecurityChamp HillaryNo ratings yet
- Ethical Hacking UpdtedDocument15 pagesEthical Hacking UpdtedvamshimatangiNo ratings yet
- Lecture 11 VirtualizationDocument22 pagesLecture 11 Virtualizationaishwarya mishraNo ratings yet
- Network Vulnerability Scanning: By:-Prachee Ratnaparkhi Msc-Ii, Roll - No. 17Document14 pagesNetwork Vulnerability Scanning: By:-Prachee Ratnaparkhi Msc-Ii, Roll - No. 17Seema KotalwarNo ratings yet
- DFN5033-NETWORK Security: Chapter 2: Vulnerabilities, Threats and AttacksDocument15 pagesDFN5033-NETWORK Security: Chapter 2: Vulnerabilities, Threats and AttacksChitra TamilchelvanNo ratings yet
- Vulnerability Assessment and Penetration TestingDocument25 pagesVulnerability Assessment and Penetration TestingYonas MengistuNo ratings yet
- Mooc 4Document17 pagesMooc 4Sparsh DhamaNo ratings yet
- Cloud Virtualization TechnologyDocument49 pagesCloud Virtualization TechnologyNarmatha ThiyagarajanNo ratings yet
- Lec-3 Network SecurityDocument18 pagesLec-3 Network Securityzabi nooristaniNo ratings yet
- Topic 3 - Malicious CodeDocument19 pagesTopic 3 - Malicious Codes.l.mills86No ratings yet
- Course - 1 - Introduction On Malware Analysis - (33 PG)Document36 pagesCourse - 1 - Introduction On Malware Analysis - (33 PG)ayan deyNo ratings yet
- Malware Goes Mobile: Presented By: Poorvi Jain T.E. Comp Roll No. 39Document24 pagesMalware Goes Mobile: Presented By: Poorvi Jain T.E. Comp Roll No. 39Manish JoshiNo ratings yet
- Cryptography and Network Security: Third Edition by William Stallings Lecture Slides by Lawrie BrownDocument23 pagesCryptography and Network Security: Third Edition by William Stallings Lecture Slides by Lawrie Brownm_a_HNo ratings yet
- 2-System Security-06-05-2023Document41 pages2-System Security-06-05-2023pritish.kheraNo ratings yet
- IS - Week # 9Document42 pagesIS - Week # 9fayezshahid167No ratings yet
- Malware Infographics by SlidesgoDocument31 pagesMalware Infographics by SlidesgobhasuNo ratings yet
- CISCO Cybersecurity Final Exam Solution by PariDocument6 pagesCISCO Cybersecurity Final Exam Solution by Paribc160200544 Mah JabeenNo ratings yet
- Chapter 8 - Securing Information SystemsDocument28 pagesChapter 8 - Securing Information SystemsIrvan 69No ratings yet
- Chapter 10 - Software Flaws and MalwareDocument19 pagesChapter 10 - Software Flaws and MalwareJasminNo ratings yet
- Threats Are Divided in Major Two Categories: Internet SecurityDocument98 pagesThreats Are Divided in Major Two Categories: Internet SecurityAman RoyNo ratings yet
- CS 356 - Lecture 9 Malicious Code: Spring 2013Document33 pagesCS 356 - Lecture 9 Malicious Code: Spring 2013rasha hassanNo ratings yet
- G4 EHD Wapiti PresentationDocument16 pagesG4 EHD Wapiti PresentationAsima TahirNo ratings yet
- Reviewer APC 5 (AutoRecovered)Document8 pagesReviewer APC 5 (AutoRecovered)Jhon Angelo M. PintorNo ratings yet
- CH - 2 Computer ThreatDocument76 pagesCH - 2 Computer ThreatmubareklibenNo ratings yet
- CS 475: Lecture 6: Symmetric Key CryptographyDocument36 pagesCS 475: Lecture 6: Symmetric Key CryptographyJ A Y T R O NNo ratings yet
- CS 475: Network Attacks and Defenses: Rachel GreenstadtDocument38 pagesCS 475: Network Attacks and Defenses: Rachel GreenstadtJ A Y T R O NNo ratings yet
- CS 475: Lecture 8 Hashes, HMAC, and Authentication: Rachel Greenstadt May 12, 2015Document42 pagesCS 475: Lecture 8 Hashes, HMAC, and Authentication: Rachel Greenstadt May 12, 2015J A Y T R O NNo ratings yet
- Usability and PsychologyDocument55 pagesUsability and PsychologyJ A Y T R O NNo ratings yet
- CS475: Lecture 1 Computer and Network Security: Rachel Greenstadt March 31, 2015Document54 pagesCS475: Lecture 1 Computer and Network Security: Rachel Greenstadt March 31, 2015J A Y T R O NNo ratings yet
- Cs 475: Lecture 4: Software Security DefensesDocument64 pagesCs 475: Lecture 4: Software Security DefensesJ A Y T R O NNo ratings yet
- CS 475: Lecture 7 Asymmetric Crypto: Rachel Greenstadt May 7, 2015Document26 pagesCS 475: Lecture 7 Asymmetric Crypto: Rachel Greenstadt May 7, 2015J A Y T R O NNo ratings yet
- Lesson 5-Wireless NetworkDocument38 pagesLesson 5-Wireless NetworkJ A Y T R O NNo ratings yet
- CS 475: Lecture 3 Software Vulnerabilities: Rachel Greenstadt April 14, 2015Document42 pagesCS 475: Lecture 3 Software Vulnerabilities: Rachel Greenstadt April 14, 2015J A Y T R O NNo ratings yet
- Work and Wealth: Ethics For The Information AgeDocument28 pagesWork and Wealth: Ethics For The Information AgeJ A Y T R O NNo ratings yet
- Privacy: Ethics For The Information AgeDocument32 pagesPrivacy: Ethics For The Information AgeJ A Y T R O NNo ratings yet
- Catalysts For Change: Ethics For The Information AgeDocument24 pagesCatalysts For Change: Ethics For The Information AgeJ A Y T R O NNo ratings yet
- Lesson 5-Wireless NetworkDocument38 pagesLesson 5-Wireless NetworkJ A Y T R O NNo ratings yet
- Lesson 4-Network ArchitectureDocument49 pagesLesson 4-Network ArchitectureJ A Y T R O NNo ratings yet
- Structured AnalysisDocument35 pagesStructured AnalysisJ A Y T R O NNo ratings yet
- LESSON 2-Network-CablingDocument46 pagesLESSON 2-Network-CablingJ A Y T R O NNo ratings yet
- Systems Analysis and DesignDocument31 pagesSystems Analysis and DesignJ A Y T R O NNo ratings yet
- Systems Analysis and Design: 03 Managing The Information Systems ProjectDocument40 pagesSystems Analysis and Design: 03 Managing The Information Systems ProjectJ A Y T R O NNo ratings yet
- System Design (Cont'd) : - Designed Strategies (Discussed in Previous Class)Document29 pagesSystem Design (Cont'd) : - Designed Strategies (Discussed in Previous Class)J A Y T R O NNo ratings yet
- Systems Analysis and Design: 02 The Origins of SoftwareDocument17 pagesSystems Analysis and Design: 02 The Origins of SoftwareJ A Y T R O NNo ratings yet
- Systems Analysis and Design: CS 231 Akim State University College Safianu OmarDocument47 pagesSystems Analysis and Design: CS 231 Akim State University College Safianu OmarJ A Y T R O NNo ratings yet
- Systems Analysis and DesignDocument29 pagesSystems Analysis and DesignJ A Y T R O NNo ratings yet
- How Much Bandwidth Do You Have? (& How Much Do You Need?)Document7 pagesHow Much Bandwidth Do You Have? (& How Much Do You Need?)J A Y T R O NNo ratings yet
- Securing The CloudDocument8 pagesSecuring The CloudKhanh le MinhNo ratings yet
- Cyber CrimeDocument30 pagesCyber CrimejinNo ratings yet
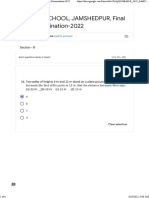
- LOYOLA SCHOOL, JAMSHEDPUR. Final Term Examination-2022 2Document6 pagesLOYOLA SCHOOL, JAMSHEDPUR. Final Term Examination-2022 2csmanienNo ratings yet
- Serial Nod 32Document3 pagesSerial Nod 32Leyner FrvNo ratings yet
- How To Implement SSL Decryption PDFDocument11 pagesHow To Implement SSL Decryption PDFvijoynew5233No ratings yet
- Social Engineering Awareness Policy: 1. OverviewDocument3 pagesSocial Engineering Awareness Policy: 1. Overviewstr webNo ratings yet
- Dlbcsidpits01 Course BookDocument120 pagesDlbcsidpits01 Course BookMars DefterNo ratings yet
- Legal Ethical and Sociaetal Issues PDFDocument67 pagesLegal Ethical and Sociaetal Issues PDFjonnefer masangyaNo ratings yet
- Wa0006Document3 pagesWa000621UGDF005 Akhΐl.KNo ratings yet
- Cryptography: Dr. Irfan RafiqueDocument81 pagesCryptography: Dr. Irfan Rafiquezargham.razaNo ratings yet
- DHCP Handbook 2ed 2003 enDocument11 pagesDHCP Handbook 2ed 2003 enErmin SehicNo ratings yet
- 6th Sem Seminar ReportDocument23 pages6th Sem Seminar ReportRajan RajanNo ratings yet
- Modern Work 1-3. Bencsik László - M365 Security És Sales SzcenáriókDocument54 pagesModern Work 1-3. Bencsik László - M365 Security És Sales SzcenáriókErcümentNo ratings yet
- Kopijahe (SFILEDocument2 pagesKopijahe (SFILEAde NurkamalNo ratings yet
- 1.0.1.2 Class Activity - Top Hacker Shows Us How It Is DoneDocument2 pages1.0.1.2 Class Activity - Top Hacker Shows Us How It Is DoneM ArdiansyahNo ratings yet
- Activity Sheet # 3Document4 pagesActivity Sheet # 3JaeNo ratings yet
- Carti OnlineDocument2 pagesCarti Onlineandreea_maftei_200760770% (10)
- Security Risk AssessmentDocument5 pagesSecurity Risk AssessmentCROSTNo ratings yet
- TCIB-MB User Security Policies v1Document5 pagesTCIB-MB User Security Policies v1Rana Abdul Rehman0% (1)
- HOW TO CASHOUT Remitly Method WCCDocument3 pagesHOW TO CASHOUT Remitly Method WCCcody100% (8)
- CNS W2023-3161606Document2 pagesCNS W2023-3161606Archi JariwalaNo ratings yet
- Crypt EloDocument25 pagesCrypt Eloze355rNo ratings yet
- General Security Concepts and Their Use in IXOS ProductsDocument17 pagesGeneral Security Concepts and Their Use in IXOS ProductsRicardo ChiappeNo ratings yet
- Java Cryptography TutorialDocument48 pagesJava Cryptography Tutorialwaris rNo ratings yet
- Introduction, Basics of Cryptography, Secret Key CryptographyDocument48 pagesIntroduction, Basics of Cryptography, Secret Key CryptographySudha SreedeviNo ratings yet
- Botnet Takedowns and The 4th AmendmentDocument33 pagesBotnet Takedowns and The 4th AmendmentKesia Jadelin Secondary StudentNo ratings yet
- Rapport Threat INT V01-1Document30 pagesRapport Threat INT V01-1feresenaNo ratings yet
- Email Security: Trend MicroDocument2 pagesEmail Security: Trend MicroXiménez MarcoNo ratings yet
- Network Security Essentials 4th Edition William Stallings Test BankDocument13 pagesNetwork Security Essentials 4th Edition William Stallings Test BankLinus Linus100% (1)
- Information Security - Video TranscriptDocument3 pagesInformation Security - Video TranscriptYussa AsasinaNo ratings yet