0% found this document useful (0 votes)
851 views29 pagesEAP-TLS Setup with NPS RADIUS Server
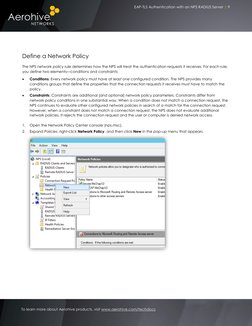
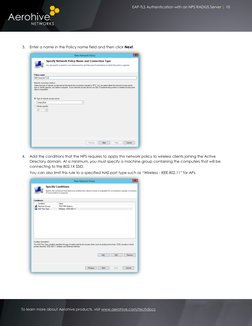
This document explains how to configure an 802.1X SSID, NPS RADIUS server, and Group Policy to provide wireless authentication through EAP-TLS. The configuration involves setting up an SSID that directs authentication requests to the NPS server, configuring the NPS server to accept EAP-TLS requests, and using Group Policy to deploy certificates and the wireless profile.
Uploaded by
pedirstuffCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd
0% found this document useful (0 votes)
851 views29 pagesEAP-TLS Setup with NPS RADIUS Server
This document explains how to configure an 802.1X SSID, NPS RADIUS server, and Group Policy to provide wireless authentication through EAP-TLS. The configuration involves setting up an SSID that directs authentication requests to the NPS server, configuring the NPS server to accept EAP-TLS requests, and using Group Policy to deploy certificates and the wireless profile.
Uploaded by
pedirstuffCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd
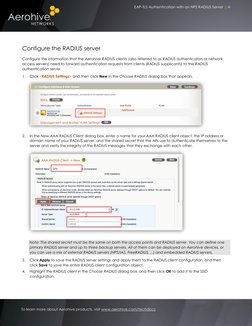
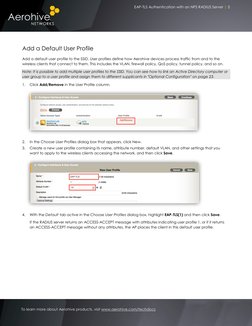
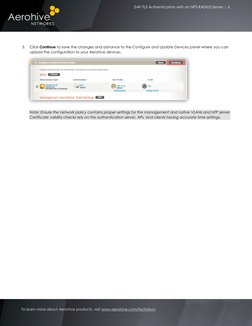
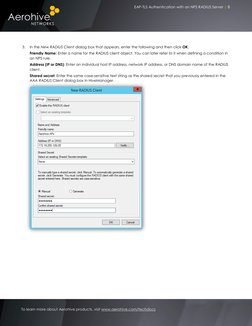
- Aerohive Configuration: Explains the configuration of Aerohive devices and NPS RADIUS server for 802.1X authentication, including creating an SSID.
- Windows Configuration: Covers the configuration of Windows systems to support EAP-TLS authentication through certification and group policies.
- Optional Configuration: Provides optional configurations including allowing EAP-TLS for corporate and BYOD access, including NPS rules.