Professional Documents
Culture Documents
Wordpress Security Analysis (Passive) : Blacklists & Threat Intel
Uploaded by
ShahriarOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Wordpress Security Analysis (Passive) : Blacklists & Threat Intel
Uploaded by
ShahriarCopyright:
Available Formats
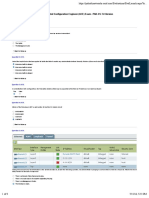
WordPress Security Analysis (Passive)
https://channelpriyo.news/
Results of a passive (non-intrusive) security analysis of the target WordPress site.
SERVER DETAILS
Web Server:
5
Apache
X-Powered-By:
Core Version issues
PHP/7.3.29
5.8.1 PHP Version:
7.3.29
Version is current Issues found during a high level
IP Address:
Found in Meta Generator analysis of the target.
185.151.30.170 (185.151.30.0/24)
Hosting Provider:
TWENTYI, GB (AS48254)
Shared Hosting:
500 sites found on IP
Blacklists & Threat Intel
Blacklist and threat intelligence sources were searched for references to the target IP address and hostname.
Dshield (host blocklist) CLEAN abuse.ch (feodo list) CLEAN
Alienvault OTX (blacklist) CLEAN URLhaus CLEAN
Cisco Talos (blacklist) CLEAN Spamhaus (drop / edrop) CLEAN
The nature of threat intelligence and blacklisting means false negatives and false positives are both possible. If the site
is utilizing shared hosting; a blacklisting may be due to a compromised site on any tenant on the host (as the IP address
is shared).
Referenced resources are used by security professionals around the world. Due to the nature of the work the sites contain links
to live malware.
1 Automated Security Analysis | hackertarget.com
WordPress Plugins
The following plugins were detected through analysis of the HTML source from the sites main page.
PLUGIN UPDATE STATUS ABOUT
latest release (17.3)
wordpress-seo (16.6.1) UPDATE
https://yoa.st/1uj
latest release (1.0.3)
bangla-font-solution UNKNOWN
https://themebing.com/plugins/bangla-font-solution
use-bangla-fonts (2.3.3) UNKNOWN latest release (1.0.0)
latest release (5.5.1)
contact-form-7 (5.4.1) UPDATE
https://contactform7.com/
latest release (8.1.0)
google-analytics-for-wordpress (7.17.0) UPDATE
https://www.monsterinsights.com/
Plugins are a source of many security vulnerabilities within WordPress installations, always keep them updated to the
latest version available and check the developers plugin page for information about security related updates and fixes.
There are likely more plugins installed than those listed here as the detection method used here is passive. While these results
give an indication of the status of plugin updates, a more comprehensive assessment can be performed by brute forcing the plugin
paths using a specialist tool.
2 Automated Security Analysis | hackertarget.com
WordPress Theme
The theme has been found by examining the path /wp-content/themes/ *theme name* /
THEME DETAILS URL
Jannah
While plugins get a lot of attention when it comes to security vulnerabilities, themes are another source of security
vulnerabilities within WordPress installations. Always keep themes updated to the latest version available and check the
developers theme page for information about updates and fixes.
The theme listed here is the active theme found in the HTML source of the page. Installed but not active themes may contain
security vulnerabilities. Remove any unused themes to minimise the attack surface of the WordPress installation.
User Enumeration
The first two user ID's were tested to determine if user enumeration is possible.
USERNAME ACCOUNT NAME
ID: 1 error getting page
ID: 2 news CHANNELPRIYO.NEWS
It is recommended to rename the admin user account to reduce the chance of brute force attacks occurring. Strong
passwords on all accounts are of course essential; renaming the admin account simply adds an extra layer of protection
especially useful against automated attackers (bots).
Keep in mind that if the author archives are enabled it is usually possible to enumerate all users within a WordPress
installation. Including a renamed admin account.
Only the first two user ID's were tested during this scan. Try the advanced membership options or a dedicated tool for a
thorough enumeration of users, themes and plugins.
3 Automated Security Analysis | hackertarget.com
Directory Indexing
In the test we attempted to list the directory contents of the uploads and plugins folders to determine if Directory
Indexing is enabled. This vulnerability type is known as information leakage and can reveal sensitive information
regarding your site configuration or content.
PATH STATUS
/wp-content/uploads/ indexing disabled
/wp-content/plugins/ indexing disabled
Directory indexing was tested on the /wp-content/uploads/ and /wp-content/plugins/ directores. Note that
other directories may have this web server feature enabled, so ensure you check other folders in your installation. It is
good practice to ensure directory indexing is disabled for your full WordPress installation either through the web server
configuration or .htaccess .
4 Automated Security Analysis | hackertarget.com
Linked Sites
Details for each linked external host have been gathered. Includes blacklist check, ASN lookup for hosting provider and
geoip lookup. Links with poor reputation could indicate a compromise or may be a threat to users of the site.
LINKED / HOST IP COMPANY / HOST COUNTRY
www.youtube.com 74.125.141.136 (AS15169) GOOGLE US
First column check gives an indication of host IP address cross referenced against multiple threat intelligence providers and
blacklists.
5 Automated Security Analysis | hackertarget.com
Linked Javascript
Compromised sites will often be linked to malicious javascript or iframes in an attempt to attack users of your
site. Look over the listed scripts and investigate ones you are not sure. Legitimate scripts should be also examined as
removal of unused javascript code may speed up the site and reduce the attack surface.
LINKED JAVASCRIPT COMPANY / HOST COUNTRY
https://c0.wp.com/p/jetpack/9.8.1/_inc/build/photon/photon.min.js AUTOMATTIC US
https://channelpriyo.news/wp-content/themes/jannah/assets/js/
scripts.min.js?ver=5.0.7
TWENTYI, GB GB
https://pagead2.googlesyndication.com/pagead/js/adsbygoogle.js?
client=ca-pub-6011030602515114
GOOGLE US
https://c0.wp.com/c/5.8.1/wp-includes/js/dist/vendor/wp-polyfill.min.js AUTOMATTIC US
https://channelpriyo.news///www.googletagmanager.com/gtag/js?
id=UA-194956128-1
TWENTYI, GB GB
https://www.googletagmanager.com/gtag/js?id=UA-194956128-1 GOOGLE US
https://c0.wp.com/c/5.8.1/wp-includes/js/jquery/jquery-migrate.min.js AUTOMATTIC US
https://channelpriyo.news/wp-content/themes/jannah/assets/js/live-
search.js?ver=5.0.7
TWENTYI, GB GB
https://channelpriyo.news/wp-content/themes/jannah/assets/js/br-news.js?
ver=5.0.7
TWENTYI, GB GB
https://channelpriyo.news/wp-content/themes/jannah/assets/js/
desktop.min.js?ver=5.0.7
TWENTYI, GB GB
https://channelpriyo.news/wp-content/plugins/google-analytics-for-
wordpress/assets/js/frontend-gtag.min.js?ver=7.17.0
TWENTYI, GB GB
https://channelpriyo.news/wp-content/themes/jannah/assets/ilightbox/
lightbox.js?ver=5.0.7
TWENTYI, GB GB
https://channelpriyo.news///pagead2.googlesyndication.com/pagead/js/
adsbygoogle.js
TWENTYI, GB GB
https://c0.wp.com/c/5.8.1/wp-includes/js/dist/vendor/regenerator-
runtime.min.js
AUTOMATTIC US
https://channelpriyo.news/wp-content/plugins/bangla-font-solution/assets/
js/plugin.js
TWENTYI, GB GB
https://stats.wp.com/e-202142.js AUTOMATTIC US
https://channelpriyo.news/wp-content/plugins/contact-form-7/includes/js/
index.js?ver=5.4.1
TWENTYI, GB GB
https://channelpriyo.news/wp-content/themes/jannah/assets/js/
sliders.min.js?ver=5.0.7
TWENTYI, GB GB
https://c0.wp.com/c/5.8.1/wp-includes/js/jquery/jquery.min.js AUTOMATTIC US
6 Automated Security Analysis | hackertarget.com
First column check gives an indication of host IP address cross referenced against multiple threat intelligence providers and
blacklists. Keep in mind that legitimate scripts may have malicious code appended to them following a compromise.
7 Automated Security Analysis | hackertarget.com
You might also like
- VLab Demo - Using ASM For Web Vulnerabilities - V12.0.0.01Document21 pagesVLab Demo - Using ASM For Web Vulnerabilities - V12.0.0.01Marcos ValleNo ratings yet
- Itu Ethical Hacking Lab Setup Guide UpdatedDocument50 pagesItu Ethical Hacking Lab Setup Guide UpdatedJacobus Booysen100% (1)
- Ethical Hacking Lab Setup Guide UpdatedDocument50 pagesEthical Hacking Lab Setup Guide UpdatedisaballerNo ratings yet
- Sample Death CertificateDocument4 pagesSample Death Certificatenashobo67% (3)
- High Orbit Ion CannonDocument0 pagesHigh Orbit Ion CannonCalperniaUSANo ratings yet
- Web Services in SAP Business ByDesign PDFDocument72 pagesWeb Services in SAP Business ByDesign PDFashwiniNo ratings yet
- Suzuki VITARA Service Manual PDFDocument835 pagesSuzuki VITARA Service Manual PDFGuenther Boelter100% (1)
- Wordpress Security Analysis (Passive) : Blacklists & Threat IntelDocument6 pagesWordpress Security Analysis (Passive) : Blacklists & Threat IntelPratama ProjectionNo ratings yet
- Wordpress Security Analysis (Passive) : Blacklists & Threat IntelDocument6 pagesWordpress Security Analysis (Passive) : Blacklists & Threat IntelHassnain HaiderNo ratings yet
- WordPress Security Issues FoundDocument7 pagesWordPress Security Issues FoundHassnain HaiderNo ratings yet
- Wordpress Security Analysis (Passive) : Blacklists & Threat IntelDocument6 pagesWordpress Security Analysis (Passive) : Blacklists & Threat IntelCoskun OzelNo ratings yet
- High Risk Vulnerabilities Found in Web Vulnerability ScanDocument6 pagesHigh Risk Vulnerabilities Found in Web Vulnerability Scanबी० के० शर्माNo ratings yet
- Back Door Into Java EE Application ServersDocument17 pagesBack Door Into Java EE Application ServerssmjainNo ratings yet
- Group Number: - Member NamesDocument8 pagesGroup Number: - Member NamesBlazeRutherNo ratings yet
- Cai Dat Tieng VietDocument14 pagesCai Dat Tieng Vietnq_abcNo ratings yet
- Web Server Technologies in 40 CharactersDocument48 pagesWeb Server Technologies in 40 Characterssivakrishna_munagaNo ratings yet
- Developer ExampleDocument87 pagesDeveloper ExamplehardironNo ratings yet
- PCNSE7 - Pass Palo Alto Networks Certified Network Security Engineer ExamDocument37 pagesPCNSE7 - Pass Palo Alto Networks Certified Network Security Engineer ExamSaurabh Gupta100% (1)
- Important Github Repositories For Security: Created TagsDocument5 pagesImportant Github Repositories For Security: Created TagsTechnical SupportNo ratings yet
- Vlab Demo - Using ASM For Web Vulnerabilities - v12.0.C PDFDocument22 pagesVlab Demo - Using ASM For Web Vulnerabilities - v12.0.C PDFVaishak PdNo ratings yet
- BrowserStack DocumentDocument29 pagesBrowserStack DocumentSagar SinghNo ratings yet
- Prefer Secure Origins For Powerful New Features - The Chromium ProjectsDocument4 pagesPrefer Secure Origins For Powerful New Features - The Chromium ProjectsPriscilla Felicia HarmanusNo ratings yet
- WP Web Browser Emerge Under AttackDocument15 pagesWP Web Browser Emerge Under AttackehaunterNo ratings yet
- OWASP - A4 XXE InjectionDocument23 pagesOWASP - A4 XXE InjectionShantanu ShuklaNo ratings yet
- Palo Alto Networks - Testking.PCNSE7.v2016-09-07.by - Pierre.51qDocument36 pagesPalo Alto Networks - Testking.PCNSE7.v2016-09-07.by - Pierre.51qCyrille IKOUMNo ratings yet
- W3af - A Framework To Own The WebDocument28 pagesW3af - A Framework To Own The WebhugobenzaquenNo ratings yet
- ResourceslistDocument17 pagesResourceslistBen FranksNo ratings yet
- Firefox Add-OnsDocument9 pagesFirefox Add-OnsWhite Box SecurityNo ratings yet
- A Full Website Hacking TutorialDocument50 pagesA Full Website Hacking Tutorialmodupe100% (1)
- Acunetix Audit of 116.66.206.28Document16 pagesAcunetix Audit of 116.66.206.28M Fauzi NirwansyahNo ratings yet
- Windows Local Privilege Escalation - HackTricksDocument56 pagesWindows Local Privilege Escalation - HackTrickssergeysenNo ratings yet
- WordPress XXE Attack via MP3 File UploadDocument14 pagesWordPress XXE Attack via MP3 File UploadNafiz NahiyanNo ratings yet
- MMP 4.0 InstallDocument9 pagesMMP 4.0 InstallUsman SherNo ratings yet
- Category Sub-Category Status: Pre-Scan AnalysisDocument53 pagesCategory Sub-Category Status: Pre-Scan AnalysisVusraNo ratings yet
- Station Addon Developers Guide v4Document33 pagesStation Addon Developers Guide v4evandropintonetoNo ratings yet
- Audit Report: Audited On December 02 2011Document76 pagesAudit Report: Audited On December 02 2011jhonhackodigeNo ratings yet
- S G A - SDocument8 pagesS G A - SsubhadipbhadraNo ratings yet
- Windows Privilege Escalation ScriptsDocument56 pagesWindows Privilege Escalation ScriptsvybiNo ratings yet
- Apache 2.0 Hardening GuideDocument13 pagesApache 2.0 Hardening GuideLovelyn ArokhamoniNo ratings yet
- Web PentestDocument9 pagesWeb PentestsatheeshbabunNo ratings yet
- Test - Accredited Configuration Engineer (ACE) Exam - PAN-OS 7.0 VersionDocument13 pagesTest - Accredited Configuration Engineer (ACE) Exam - PAN-OS 7.0 VersiongustavoNo ratings yet
- Effectiveness of AVs in Detecting Web Application BackdoorsDocument8 pagesEffectiveness of AVs in Detecting Web Application BackdoorsblwztrainingNo ratings yet
- PAN ACE7.0 100% PassDocument112 pagesPAN ACE7.0 100% PassRobert Martin87% (31)
- 内网渗透测试 外链Document9 pages内网渗透测试 外链andyNo ratings yet
- Bypassing Corporate Email FilteringDocument45 pagesBypassing Corporate Email FilteringAungkhineNo ratings yet
- Kali Linux Reference Guide - A P - Sheimo, MatthewDocument122 pagesKali Linux Reference Guide - A P - Sheimo, MatthewOscar BarufaldiNo ratings yet
- 1z0-820.exam.75q: Number: 1z0-820 Passing Score: 800 Time Limit: 120 MinDocument68 pages1z0-820.exam.75q: Number: 1z0-820 Passing Score: 800 Time Limit: 120 MinTchakalaFissaleNo ratings yet
- APIsec University - Become An API Security ExpertDocument10 pagesAPIsec University - Become An API Security ExperttestNo ratings yet
- web security PDFDocument31 pagesweb security PDFsamweli.mwakatobeNo ratings yet
- CreditrtsDocument4 pagesCreditrtsJohnathan HarkarNo ratings yet
- PentestTools WebsiteScanner ReportDocument4 pagesPentestTools WebsiteScanner ReportdeldengcNo ratings yet
- Understanding Security, and Some Best PracticesDocument11 pagesUnderstanding Security, and Some Best PracticesRoy SilvesterNo ratings yet
- Session 2 VU21997Document48 pagesSession 2 VU21997cryptailmineNo ratings yet
- Authorized User License Administrator GuideDocument14 pagesAuthorized User License Administrator GuideQuennie Abellon QuimanNo ratings yet
- Build your own Malware SandboxDocument19 pagesBuild your own Malware SandboxImagekingNo ratings yet
- WeemanDocument4 pagesWeemanJamesMarshallNo ratings yet
- Hacking Websites With Havij v1Document36 pagesHacking Websites With Havij v1Sonya Reddy100% (1)
- Burp Suit TipsDocument105 pagesBurp Suit TipsLuis De SantanaNo ratings yet
- Vicker Lws SlideDocument70 pagesVicker Lws SlidevickerleungNo ratings yet
- © 2018 Caendra Inc. - Hera For Ptpv5 - Linux Exploitation (Remote Exploitation & Post-Exploitation)Document22 pages© 2018 Caendra Inc. - Hera For Ptpv5 - Linux Exploitation (Remote Exploitation & Post-Exploitation)Saw GyiNo ratings yet
- Cracking The Lens: Targeting HTTP's Hidden Attack Surface: OutlineDocument17 pagesCracking The Lens: Targeting HTTP's Hidden Attack Surface: OutlineoooNo ratings yet
- Visual SourceSafe 2005 Software Configuration Management in PracticeFrom EverandVisual SourceSafe 2005 Software Configuration Management in PracticeNo ratings yet
- Foundation Dynamic Web Pages with Python: Create Dynamic Web Pages with Django and FlaskFrom EverandFoundation Dynamic Web Pages with Python: Create Dynamic Web Pages with Django and FlaskNo ratings yet
- M Miraz Hossain Is A Writer, Artist, Lyricist, Entrepreneur and Social WorkerDocument5 pagesM Miraz Hossain Is A Writer, Artist, Lyricist, Entrepreneur and Social WorkerShahriarNo ratings yet
- IPVanish VPNDocument1 pageIPVanish VPNShahriarNo ratings yet
- Death Certificate 2014 09 111 000229 0 EGDocument1 pageDeath Certificate 2014 09 111 000229 0 EGShahriarNo ratings yet
- HTML formatting challenge for Chapter 03 contentDocument2 pagesHTML formatting challenge for Chapter 03 contentmariaNo ratings yet
- J QueryDocument24 pagesJ Queryviral1valueNo ratings yet
- Web Services With REST and ICFDocument12 pagesWeb Services With REST and ICFvbvrkNo ratings yet
- rusDw3Ze CleanedDocument197 pagesrusDw3Ze CleanedAbahati TvNo ratings yet
- Front-End Developer Handbook 2019 PDFDocument145 pagesFront-End Developer Handbook 2019 PDFAvinash Agrawal96% (28)
- Asp.Net 4.0 Features and EnhancementsDocument13 pagesAsp.Net 4.0 Features and EnhancementsNukleerBaslikNo ratings yet
- Chapter 5 HTML BasicsDocument24 pagesChapter 5 HTML BasicsAyenachew LegesseNo ratings yet
- Install Apache on Ubuntu 20.04Document11 pagesInstall Apache on Ubuntu 20.04Obelisco WirelessNo ratings yet
- AS - Worksheet 1 - VII - ICT - HTML - Advanced FeaturesDocument3 pagesAS - Worksheet 1 - VII - ICT - HTML - Advanced FeaturesShubh JainNo ratings yet
- Textbook Solutions Expert Q&A Practice: Find Solutions For Your HomeworkDocument4 pagesTextbook Solutions Expert Q&A Practice: Find Solutions For Your HomeworkLucky Asr AwaisNo ratings yet
- Limitations in Classic ASP: Server Controls Are Tags That Are Understood by The ServerDocument11 pagesLimitations in Classic ASP: Server Controls Are Tags That Are Understood by The ServerHoshank SehtNo ratings yet
- Questions on Servlets and HTTP methods under 40 charsDocument5 pagesQuestions on Servlets and HTTP methods under 40 charssumant_414No ratings yet
- Web Engineering Lab 12Document6 pagesWeb Engineering Lab 12Eesha ArifNo ratings yet
- Mc5024-Web Design ModelDocument2 pagesMc5024-Web Design ModelMsec McaNo ratings yet
- Ahmad Khan: GhazanfarDocument2 pagesAhmad Khan: GhazanfarTanha LarkaNo ratings yet
- Made by HvanhtuanDocument41 pagesMade by HvanhtuanHuoiNo ratings yet
- Mapa Distritos de Córdoba WikiDocument2 pagesMapa Distritos de Córdoba WikijaimeNo ratings yet
- ClaimDocument9 pagesClaimdustboyNo ratings yet
- Javascript Introduction: Javascript Can Change HTML ContentDocument41 pagesJavascript Introduction: Javascript Can Change HTML ContentKhoiril 25No ratings yet
- Chapter 4 - Web Page DevelopmentDocument41 pagesChapter 4 - Web Page DevelopmentNurul IzatiNo ratings yet
- Business application midterm document on Tim Berners-Lee and the invention of the World Wide WebDocument15 pagesBusiness application midterm document on Tim Berners-Lee and the invention of the World Wide WebDioner RayNo ratings yet
- Webpage Design MODULEDocument129 pagesWebpage Design MODULEJanine CallanganNo ratings yet
- Chapter 17 Web Designing1 PDFDocument15 pagesChapter 17 Web Designing1 PDFRoopa S100% (1)
- Marvellous Angular - Routing PDFDocument4 pagesMarvellous Angular - Routing PDFSagar B BeloteNo ratings yet
- Loadrunner Questions:: Example 1Document27 pagesLoadrunner Questions:: Example 1Lavanya GunasekaranNo ratings yet
- Peter Losh Resume - Online MarketingDocument3 pagesPeter Losh Resume - Online Marketingpklosh100% (1)
- Sample Question - Bank - IPDocument3 pagesSample Question - Bank - IPnoelprojects11No ratings yet
- FW Media Agency PresentationDocument18 pagesFW Media Agency PresentationBatsukh PurevdorjNo ratings yet