Professional Documents
Culture Documents
Generated On Mar., 23 Nov. 2021 18:22:47 Summary of Alerts: High Medium Low Informational
Uploaded by
Raksasa RepulsiveOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Generated On Mar., 23 Nov. 2021 18:22:47 Summary of Alerts: High Medium Low Informational
Uploaded by
Raksasa RepulsiveCopyright:
Available Formats
ZAP Scanning Report
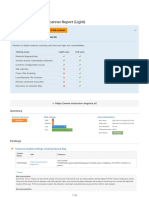
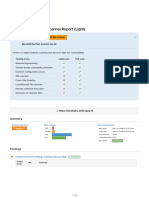
Summary of Alerts Generated on mar., 23 nov. 2021 18:22:47
Risk Level Number of Alerts
High 0
Medium 6
Low 14
Informational 3
Alerts
Name Risk Level Number of Instances
Cross-Domain Misconfiguration Medium 8
CSP: Wildcard Directive Medium 6
X-Frame-Options Header Not Set Medium 2
Absence of Anti-CSRF Tokens Low 2
Cookie No HttpOnly Flag Low 2
Cookie Without SameSite Attribute Low 2
Cookie Without Secure Flag Low 1
Cross-Domain JavaScript Source File Inclusion Low 2
CSP: Notices Low 6
Incomplete or No Cache-control and Pragma HTTP Header Set Low 1
X-Content-Type-Options Header Missing Low 4
Content-Type Header Missing Informational 1
Timestamp Disclosure - Unix Informational 8
Alert Detail
Medium (Medium) Cross-Domain Misconfiguration
Description Web browser data loading may be possible, due to a Cross Origin Resource Sharing (CORS) misconfiguration on the web server
URL https://hackthissite.org/missions/
Method GET
Evidence Access-Control-Allow-Origin: *
URL https://hackthissite.org/killing/all/humans/
Method GET
Evidence Access-Control-Allow-Origin: *
URL https://hackthissite.org/
Method GET
Evidence Access-Control-Allow-Origin: *
URL https://hackthissite.org/sitemap.xml
Method GET
Evidence Access-Control-Allow-Origin: *
URL https://hackthissite.org/robots.txt
Method GET
Evidence Access-Control-Allow-Origin: *
URL https://hackthissite.org/manifest.webmanifest
Method GET
Evidence Access-Control-Allow-Origin: *
URL https://hackthissite.org/hp.php
Method GET
Evidence Access-Control-Allow-Origin: *
Instances 7
Ensure that sensitive data is not available in an unauthenticated manner (using IP address white-listing, for instance).
Solution
Configure the "Access-Control-Allow-Origin" HTTP header to a more restrictive set of domains, or remove all CORS headers entirely, to allow the web browser
to enforce the Same Origin Policy (SOP) in a more restrictive manner.
The CORS misconfiguration on the web server permits cross-domain read requests from arbitrary third party domains, using unauthenticated APIs on this
domain. Web browser implementations do not permit arbitrary third parties to read the response from authenticated APIs, however. This reduces the risk
Other information
somewhat. This misconfiguration could be used by an attacker to access data that is available in an unauthenticated manner, but which uses some other form
of security, such as IP address white-listing.
Reference http://www.hpenterprisesecurity.com/vulncat/en/vulncat/vb/html5_overly_permissive_cors_policy.html
CWE Id 264
WASC Id 14
Source ID 3
Medium (Medium) Cross-Domain Misconfiguration
Description Web browser data loading may be possible, due to a Cross Origin Resource Sharing (CORS) misconfiguration on the web server
URL http://hackthissite.org/
Method GET
Evidence Access-Control-Allow-Origin: *
Instances 1
Ensure that sensitive data is not available in an unauthenticated manner (using IP address white-listing, for instance).
Solution
Configure the "Access-Control-Allow-Origin" HTTP header to a more restrictive set of domains, or remove all CORS headers entirely, to allow the web browser
to enforce the Same Origin Policy (SOP) in a more restrictive manner.
The CORS misconfiguration on the web server permits cross-domain read requests from arbitrary third party domains, using unauthenticated APIs on this
domain. Web browser implementations do not permit arbitrary third parties to read the response from authenticated APIs, however. This reduces the risk
Other information
somewhat. This misconfiguration could be used by an attacker to access data that is available in an unauthenticated manner, but which uses some other form
of security, such as IP address white-listing.
Reference http://www.hpenterprisesecurity.com/vulncat/en/vulncat/vb/html5_overly_permissive_cors_policy.html
CWE Id 264
WASC Id 14
Source ID 3
Medium (Medium) CSP: Wildcard Directive
The following directives either allow wildcard sources (or ancestors), are not defined, or are overly broadly defined:
script-src, script-src-elem, script-src-attr, style-src, style-src-elem, style-src-attr, img-src, connect-src, frame-ancestors, font-src, media-src, object-src,
Description
manifest-src, worker-src, prefetch-src
The directive(s): frame-ancestors are among the directives that do not fallback to default-src, missing/excluding them is the same as allowing anything.
URL https://hackthissite.org/missions/
Method GET
Parameter Content-Security-Policy
child-src 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; form-action 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; upgrade-
Evidence
insecure-requests; report-uri https://hackthissite.report-uri.com/r/d/csp/enforce
URL https://hackthissite.org/killing/all/humans/
Method GET
Parameter Content-Security-Policy
child-src 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; form-action 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; upgrade-
Evidence
insecure-requests; report-uri https://hackthissite.report-uri.com/r/d/csp/enforce
URL https://hackthissite.org/hp.php
Method GET
Parameter Content-Security-Policy
child-src 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; form-action 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; upgrade-
Evidence
insecure-requests; report-uri https://hackthissite.report-uri.com/r/d/csp/enforce
URL https://hackthissite.org/
Method GET
Parameter Content-Security-Policy
child-src 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; form-action 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; upgrade-
Evidence
insecure-requests; report-uri https://hackthissite.report-uri.com/r/d/csp/enforce
URL https://hackthissite.org/sitemap.xml
Method GET
Parameter Content-Security-Policy
child-src 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; form-action 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; upgrade-
Evidence
insecure-requests; report-uri https://hackthissite.report-uri.com/r/d/csp/enforce
Instances 5
Solution Ensure that your web server, application server, load balancer, etc. is properly configured to set the Content-Security-Policy header.
The response contained multiple CSP headers, one or more of them contained a report-uri directive and therefore they could not be merged. The first
Other information
identified header/policy was analyzed.
http://www.w3.org/TR/CSP2/
http://www.w3.org/TR/CSP/
http://caniuse.com/#search=content+security+policy
Reference
http://content-security-policy.com/
https://github.com/shapesecurity/salvation
https://developers.google.com/web/fundamentals/security/csp#policy_applies_to_a_wide_variety_of_resources
CWE Id 16
WASC Id 15
Source ID 3
Medium (Medium) CSP: Wildcard Directive
The following directives either allow wildcard sources (or ancestors), are not defined, or are overly broadly defined:
script-src, script-src-elem, script-src-attr, style-src, style-src-elem, style-src-attr, img-src, connect-src, frame-ancestors, font-src, media-src, object-src,
Description
manifest-src, worker-src, prefetch-src
The directive(s): frame-ancestors are among the directives that do not fallback to default-src, missing/excluding them is the same as allowing anything.
URL http://hackthissite.org/
Method GET
Parameter Content-Security-Policy
child-src 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; form-action 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; upgrade-
Evidence
insecure-requests; report-uri https://hackthissite.report-uri.com/r/d/csp/enforce
Instances 1
Solution Ensure that your web server, application server, load balancer, etc. is properly configured to set the Content-Security-Policy header.
The response contained multiple CSP headers, one or more of them contained a report-uri directive and therefore they could not be merged. The first
Other information
identified header/policy was analyzed.
http://www.w3.org/TR/CSP2/
http://www.w3.org/TR/CSP/
http://caniuse.com/#search=content+security+policy
Reference
http://content-security-policy.com/
https://github.com/shapesecurity/salvation
https://developers.google.com/web/fundamentals/security/csp#policy_applies_to_a_wide_variety_of_resources
CWE Id 16
WASC Id 15
Source ID 3
Medium (Medium) X-Frame-Options Header Not Set
Description X-Frame-Options header is not included in the HTTP response to protect against 'ClickJacking' attacks.
URL https://hackthissite.org/
Method GET
Parameter X-Frame-Options
Instances 1
Most modern Web browsers support the X-Frame-Options HTTP header. Ensure it's set on all web pages returned by your site (if you expect the page to be
Solution framed only by pages on your server (e.g. it's part of a FRAMESET) then you'll want to use SAMEORIGIN, otherwise if you never expect the page to be
framed, you should use DENY. ALLOW-FROM allows specific websites to frame the web page in supported web browsers).
Reference https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
CWE Id 16
WASC Id 15
Source ID 3
Medium (Medium) X-Frame-Options Header Not Set
Description X-Frame-Options header is not included in the HTTP response to protect against 'ClickJacking' attacks.
URL http://hackthissite.org/
Method GET
Parameter X-Frame-Options
Instances 1
Most modern Web browsers support the X-Frame-Options HTTP header. Ensure it's set on all web pages returned by your site (if you expect the page to be
Solution framed only by pages on your server (e.g. it's part of a FRAMESET) then you'll want to use SAMEORIGIN, otherwise if you never expect the page to be
framed, you should use DENY. ALLOW-FROM allows specific websites to frame the web page in supported web browsers).
Reference https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
CWE Id 16
WASC Id 15
Source ID 3
Low (Medium) Absence of Anti-CSRF Tokens
No Anti-CSRF tokens were found in a HTML submission form.
Una solicutud falsa entre sitios en un ataque que compromete y obliga a una víctima a enviar su solicitud HTTP a un destino objetivo sin su conocimiento o
intención para poder realizar una acción como víctima. La causa oculta es la funcionalidad de la aplicación utilizando acciones de URL/formulario que pueden
ser adivinados de forma repetible. La naturaleza del ataque es que CSRG explota la confianza que un sitio web proporciona a un usuario. Por el contrario, las
cadenas de comandos de los sitios cruzados (XSS) explotan la confianza que un usuario proporciona en un sitio web. Al igual que XSS, los ataques CSRG
no son de forma necesaria de sitios cruzados, pero hay la posibilidad de que si pueden serlo. La falsificación de las solicitudes ente los sitios también se
conoce como CSRF, XSRG, ataques con un solo clic, montaje de sesión, diputado confundido y navegación en alta mar.
Los ataques de CSRG son muy efectivos en varias situaciones, que incluyen:
Description
*La victima tiene una sesión activa en el sitio de destino.
*La víctima se autoriza por medio de la autenticación HTTP en el sitio de destino.
*La víctima se encuentra en la misma red local que el sitio de destino.
CSRF se ha utilizado especialmente para poder realizar una acción contra un sitio objetivo utilizando los privilegios de la víctima, pero se han revelado
técnicas recientes para difundir información al obtener el acceso a la respuesta. El riesgo de divulgación de información aumenta de forma drástica cuando el
sitio de destino se encuentra vulnerable a XSS, porque XSS se puede utilizar como una plataforma para CSRF, lo que le permite al atacante que opere desde
adentro de los líites de la misma política de origen.
URL https://hackthissite.org/
Method GET
Evidence <form id="loginform" method="post" action="/user/login">
Instances 1
Frase: Arquitectura y Diseño
Utilice una biblioteca o marco comprobado que no acepte que ocura esta debilidad o que proporcione construcciones que permitan que esta debilidad sea
mas sencilla de evitar.
Por ejemplo, utilice el paquete anti-CSRG como el CSRGuard de OWASP.
Fase: Implementación
Asegúrese de que su aplicación esté libre de fallas de secuencias de comandos entre sitios, ya que la mayoría de las defensas de CSRF pueden detenerse
por alto por medio del uso de secuencias de comandos manejadas por el atacante.
Fase: Arquitectura y Diseño
Origina un nonce único para cada uno de los formularios, coloque el nonce en el formularo y confirme la independencia al obtener el formulario. Asegúrese
de que el nonce no sea predecible (CWE-330).
Solution
Usted tiene que tener en cuenta que esto puede pasar desapercibido utilizando XSS.
Identificar las operaciones que sean especialmente peligrosas. Cuando el usuario desarrolla una operación peligrosa, envíe una solicitud de confirmación de
forma separada para poder garantizar que el usuario tenga la intención de desarrollar esa operación.
Usted tiene que tener en cuenta que esto puede pasar desapercibido utilizando XSS.
Utilice el control de gestión de la sesión de ESAPI.
Este control introduce un elemento para CSRF.
No utilice el método GET para ninguna de las solicitudes que puedan desencadenar un cambio de estado.
Fase: Implementación
Revise que la solicitud se creó en la página esperada. Esto podría quebrar la funcionalidad auténtica, ya que los usuarios o los representantes puede ser que
hayan desactivado el envío de Referer por motivos de privacidad.
No known Anti-CSRF token [anticsrf, CSRFToken, __RequestVerificationToken, csrfmiddlewaretoken, authenticity_token, OWASP_CSRFTOKEN, anoncsrf,
Other information
csrf_token, _csrf, _csrfSecret, __csrf_magic, CSRF] was found in the following HTML form: [Form 1: "username" "password" "btn_submit" ].
http://projects.webappsec.org/Cross-Site-Request-Forgery
Reference
http://cwe.mitre.org/data/definitions/352.html
CWE Id 352
WASC Id 9
Source ID 3
Low (Medium) Absence of Anti-CSRF Tokens
No Anti-CSRF tokens were found in a HTML submission form.
Una solicutud falsa entre sitios en un ataque que compromete y obliga a una víctima a enviar su solicitud HTTP a un destino objetivo sin su conocimiento o
intención para poder realizar una acción como víctima. La causa oculta es la funcionalidad de la aplicación utilizando acciones de URL/formulario que pueden
ser adivinados de forma repetible. La naturaleza del ataque es que CSRG explota la confianza que un sitio web proporciona a un usuario. Por el contrario, las
cadenas de comandos de los sitios cruzados (XSS) explotan la confianza que un usuario proporciona en un sitio web. Al igual que XSS, los ataques CSRG
no son de forma necesaria de sitios cruzados, pero hay la posibilidad de que si pueden serlo. La falsificación de las solicitudes ente los sitios también se
conoce como CSRF, XSRG, ataques con un solo clic, montaje de sesión, diputado confundido y navegación en alta mar.
Los ataques de CSRG son muy efectivos en varias situaciones, que incluyen:
Description
*La victima tiene una sesión activa en el sitio de destino.
*La víctima se autoriza por medio de la autenticación HTTP en el sitio de destino.
*La víctima se encuentra en la misma red local que el sitio de destino.
CSRF se ha utilizado especialmente para poder realizar una acción contra un sitio objetivo utilizando los privilegios de la víctima, pero se han revelado
técnicas recientes para difundir información al obtener el acceso a la respuesta. El riesgo de divulgación de información aumenta de forma drástica cuando el
sitio de destino se encuentra vulnerable a XSS, porque XSS se puede utilizar como una plataforma para CSRF, lo que le permite al atacante que opere desde
adentro de los líites de la misma política de origen.
URL http://hackthissite.org/
Method GET
Evidence <form id="loginform" method="post" action="/user/login">
Instances 1
Frase: Arquitectura y Diseño
Utilice una biblioteca o marco comprobado que no acepte que ocura esta debilidad o que proporcione construcciones que permitan que esta debilidad sea
mas sencilla de evitar.
Por ejemplo, utilice el paquete anti-CSRG como el CSRGuard de OWASP.
Fase: Implementación
Asegúrese de que su aplicación esté libre de fallas de secuencias de comandos entre sitios, ya que la mayoría de las defensas de CSRF pueden detenerse
por alto por medio del uso de secuencias de comandos manejadas por el atacante.
Fase: Arquitectura y Diseño
Origina un nonce único para cada uno de los formularios, coloque el nonce en el formularo y confirme la independencia al obtener el formulario. Asegúrese
de que el nonce no sea predecible (CWE-330).
Solution
Usted tiene que tener en cuenta que esto puede pasar desapercibido utilizando XSS.
Identificar las operaciones que sean especialmente peligrosas. Cuando el usuario desarrolla una operación peligrosa, envíe una solicitud de confirmación de
forma separada para poder garantizar que el usuario tenga la intención de desarrollar esa operación.
Usted tiene que tener en cuenta que esto puede pasar desapercibido utilizando XSS.
Utilice el control de gestión de la sesión de ESAPI.
Este control introduce un elemento para CSRF.
No utilice el método GET para ninguna de las solicitudes que puedan desencadenar un cambio de estado.
Fase: Implementación
Revise que la solicitud se creó en la página esperada. Esto podría quebrar la funcionalidad auténtica, ya que los usuarios o los representantes puede ser que
hayan desactivado el envío de Referer por motivos de privacidad.
No known Anti-CSRF token [anticsrf, CSRFToken, __RequestVerificationToken, csrfmiddlewaretoken, authenticity_token, OWASP_CSRFTOKEN, anoncsrf,
Other information
csrf_token, _csrf, _csrfSecret, __csrf_magic, CSRF] was found in the following HTML form: [Form 1: "username" "password" "btn_submit" ].
http://projects.webappsec.org/Cross-Site-Request-Forgery
Reference
http://cwe.mitre.org/data/definitions/352.html
CWE Id 352
WASC Id 9
Source ID 3
Low (Medium) Cookie No HttpOnly Flag
A cookie has been set without the HttpOnly flag, which means that the cookie can be accessed by JavaScript. If a malicious script can be run on this page
Description
then the cookie will be accessible and can be transmitted to another site. If this is a session cookie then session hijacking may be possible.
URL https://hackthissite.org/
Method GET
Parameter HackThisSite
Evidence Set-Cookie: HackThisSite
Instances 1
Solution Ensure that the HttpOnly flag is set for all cookies.
Reference https://owasp.org/www-community/HttpOnly
CWE Id 16
WASC Id 13
Source ID 3
Low (Medium) Cookie No HttpOnly Flag
A cookie has been set without the HttpOnly flag, which means that the cookie can be accessed by JavaScript. If a malicious script can be run on this page
Description
then the cookie will be accessible and can be transmitted to another site. If this is a session cookie then session hijacking may be possible.
URL http://hackthissite.org/
Method GET
Parameter HackThisSite
Evidence Set-Cookie: HackThisSite
Instances 1
Solution Ensure that the HttpOnly flag is set for all cookies.
Reference https://owasp.org/www-community/HttpOnly
CWE Id 16
WASC Id 13
Source ID 3
Low (Medium) Cookie Without SameSite Attribute
A cookie has been set without the SameSite attribute, which means that the cookie can be sent as a result of a 'cross-site' request. The SameSite attribute is
Description
an effective counter measure to cross-site request forgery, cross-site script inclusion, and timing attacks.
URL https://hackthissite.org/
Method GET
Parameter HackThisSite
Evidence Set-Cookie: HackThisSite
Instances 1
Solution Ensure that the SameSite attribute is set to either 'lax' or ideally 'strict' for all cookies.
Reference https://tools.ietf.org/html/draft-ietf-httpbis-cookie-same-site
CWE Id 16
WASC Id 13
Source ID 3
Low (Medium) Cookie Without SameSite Attribute
A cookie has been set without the SameSite attribute, which means that the cookie can be sent as a result of a 'cross-site' request. The SameSite attribute is
Description
an effective counter measure to cross-site request forgery, cross-site script inclusion, and timing attacks.
URL http://hackthissite.org/
Method GET
Parameter HackThisSite
Evidence Set-Cookie: HackThisSite
Instances 1
Solution Ensure that the SameSite attribute is set to either 'lax' or ideally 'strict' for all cookies.
Reference https://tools.ietf.org/html/draft-ietf-httpbis-cookie-same-site
CWE Id 16
WASC Id 13
Source ID 3
Low (Medium) Cookie Without Secure Flag
Description A cookie has been set without the secure flag, which means that the cookie can be accessed via unencrypted connections.
URL https://hackthissite.org/
Method GET
Parameter HackThisSite
Evidence Set-Cookie: HackThisSite
Instances 1
Whenever a cookie contains sensitive information or is a session token, then it should always be passed using an encrypted channel. Ensure that the secure
Solution
flag is set for cookies containing such sensitive information.
https://owasp.org/www-project-web-security-testing-guide/v41/4-Web_Application_Security_Testing/06-Session_Management_Testing/02-
Reference
Testing_for_Cookies_Attributes.html
CWE Id 614
WASC Id 13
Source ID 3
Low (Medium) Cross-Domain JavaScript Source File Inclusion
Description The page includes one or more script files from a third-party domain.
URL https://hackthissite.org/
Method GET
Parameter https://data.htscdn.org/js/jquery-1.8.1.min.js
Evidence <script type="text/javascript" src="https://data.htscdn.org/js/jquery-1.8.1.min.js"></script>
Instances 1
Solution Ensure JavaScript source files are loaded from only trusted sources, and the sources can't be controlled by end users of the application.
Reference
CWE Id 829
WASC Id 15
Source ID 3
Low (Medium) Cross-Domain JavaScript Source File Inclusion
Description The page includes one or more script files from a third-party domain.
URL http://hackthissite.org/
Method GET
Parameter https://data.htscdn.org/js/jquery-1.8.1.min.js
Evidence <script type="text/javascript" src="https://data.htscdn.org/js/jquery-1.8.1.min.js"></script>
Instances 1
Solution Ensure JavaScript source files are loaded from only trusted sources, and the sources can't be controlled by end users of the application.
Reference
CWE Id 829
WASC Id 15
Source ID 3
Low (Medium) CSP: Notices
Warnings:
1:1: The child-src directive is deprecated as of CSP level 3. Authors who wish to regulate nested browsing contexts and workers SHOULD use the frame-src
and worker-src directives, respectively.
Description
1:159: The upgrade-insecure-requests directive is an experimental directive that will be likely added to the CSP specification.
Info Items:
1:186: A draft of the next version of CSP deprecates report-uri in favour of a new report-to directive.
URL https://hackthissite.org/killing/all/humans/
Method GET
Parameter Content-Security-Policy
child-src 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; form-action 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; upgrade-
Evidence
insecure-requests; report-uri https://hackthissite.report-uri.com/r/d/csp/enforce
URL https://hackthissite.org/
Method GET
Parameter Content-Security-Policy
child-src 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; form-action 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; upgrade-
Evidence
insecure-requests; report-uri https://hackthissite.report-uri.com/r/d/csp/enforce
URL https://hackthissite.org/sitemap.xml
Method GET
Parameter Content-Security-Policy
child-src 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; form-action 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; upgrade-
Evidence
insecure-requests; report-uri https://hackthissite.report-uri.com/r/d/csp/enforce
URL https://hackthissite.org/hp.php
Method GET
Parameter Content-Security-Policy
child-src 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; form-action 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; upgrade-
Evidence
insecure-requests; report-uri https://hackthissite.report-uri.com/r/d/csp/enforce
URL https://hackthissite.org/missions/
Method GET
Parameter Content-Security-Policy
child-src 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; form-action 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; upgrade-
Evidence
insecure-requests; report-uri https://hackthissite.report-uri.com/r/d/csp/enforce
Instances 5
Solution Ensure that your web server, application server, load balancer, etc. is properly configured to set the Content-Security-Policy header.
The response contained multiple CSP headers, one or more of them contained a report-uri directive and therefore they could not be merged. The first
Other information
identified header/policy was analyzed.
http://www.w3.org/TR/CSP2/
http://www.w3.org/TR/CSP/
http://caniuse.com/#search=content+security+policy
Reference
http://content-security-policy.com/
https://github.com/shapesecurity/salvation
https://developers.google.com/web/fundamentals/security/csp#policy_applies_to_a_wide_variety_of_resources
CWE Id 16
WASC Id 15
Source ID 3
Low (Medium) CSP: Notices
Warnings:
1:1: The child-src directive is deprecated as of CSP level 3. Authors who wish to regulate nested browsing contexts and workers SHOULD use the frame-src
and worker-src directives, respectively.
Description
1:159: The upgrade-insecure-requests directive is an experimental directive that will be likely added to the CSP specification.
Info Items:
1:186: A draft of the next version of CSP deprecates report-uri in favour of a new report-to directive.
URL http://hackthissite.org/
Method GET
Parameter Content-Security-Policy
child-src 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; form-action 'self' hackthissite.org *.hackthissite.org htscdn.org *.htscdn.org; upgrade-
Evidence
insecure-requests; report-uri https://hackthissite.report-uri.com/r/d/csp/enforce
Instances 1
Solution Ensure that your web server, application server, load balancer, etc. is properly configured to set the Content-Security-Policy header.
The response contained multiple CSP headers, one or more of them contained a report-uri directive and therefore they could not be merged. The first
Other information
identified header/policy was analyzed.
http://www.w3.org/TR/CSP2/
http://www.w3.org/TR/CSP/
http://caniuse.com/#search=content+security+policy
Reference
http://content-security-policy.com/
https://github.com/shapesecurity/salvation
https://developers.google.com/web/fundamentals/security/csp#policy_applies_to_a_wide_variety_of_resources
CWE Id 16
WASC Id 15
Source ID 3
Low (Medium) Incomplete or No Cache-control and Pragma HTTP Header Set
Description The cache-control and pragma HTTP header have not been set properly or are missing allowing the browser and proxies to cache content.
URL https://hackthissite.org/robots.txt
Method GET
Parameter Cache-Control
Instances 1
Whenever possible ensure the cache-control HTTP header is set with no-cache, no-store, must-revalidate; and that the pragma HTTP header is set with no-
Solution
cache.
Reference https://cheatsheetseries.owasp.org/cheatsheets/Session_Management_Cheat_Sheet.html#web-content-caching
CWE Id 525
WASC Id 13
Source ID 3
Low (Medium) X-Content-Type-Options Header Missing
The Anti-MIME-Sniffing header X-Content-Type-Options was not set to 'nosniff'. This allows older versions of Internet Explorer and Chrome to perform MIME-
Description sniffing on the response body, potentially causing the response body to be interpreted and displayed as a content type other than the declared content type.
Current (early 2014) and legacy versions of Firefox will use the declared content type (if one is set), rather than performing MIME-sniffing.
URL https://hackthissite.org/
Method GET
Parameter X-Content-Type-Options
URL https://hackthissite.org/robots.txt
Method GET
Parameter X-Content-Type-Options
URL https://hackthissite.org/manifest.webmanifest
Method GET
Parameter X-Content-Type-Options
Instances 3
Ensure that the application/web server sets the Content-Type header appropriately, and that it sets the X-Content-Type-Options header to 'nosniff' for all web
pages.
Solution
If possible, ensure that the end user uses a standards-compliant and modern web browser that does not perform MIME-sniffing at all, or that can be directed
by the web application/web server to not perform MIME-sniffing.
This issue still applies to error type pages (401, 403, 500, etc.) as those pages are often still affected by injection issues, in which case there is still concern for
Other information browsers sniffing pages away from their actual content type.
At "High" threshold this scan rule will not alert on client or server error responses.
http://msdn.microsoft.com/en-us/library/ie/gg622941%28v=vs.85%29.aspx
Reference
https://owasp.org/www-community/Security_Headers
CWE Id 16
WASC Id 15
Source ID 3
Low (Medium) X-Content-Type-Options Header Missing
The Anti-MIME-Sniffing header X-Content-Type-Options was not set to 'nosniff'. This allows older versions of Internet Explorer and Chrome to perform MIME-
Description sniffing on the response body, potentially causing the response body to be interpreted and displayed as a content type other than the declared content type.
Current (early 2014) and legacy versions of Firefox will use the declared content type (if one is set), rather than performing MIME-sniffing.
URL http://hackthissite.org/
Method GET
Parameter X-Content-Type-Options
Instances 1
Ensure that the application/web server sets the Content-Type header appropriately, and that it sets the X-Content-Type-Options header to 'nosniff' for all web
pages.
Solution
If possible, ensure that the end user uses a standards-compliant and modern web browser that does not perform MIME-sniffing at all, or that can be directed
by the web application/web server to not perform MIME-sniffing.
This issue still applies to error type pages (401, 403, 500, etc.) as those pages are often still affected by injection issues, in which case there is still concern for
Other information browsers sniffing pages away from their actual content type.
At "High" threshold this scan rule will not alert on client or server error responses.
http://msdn.microsoft.com/en-us/library/ie/gg622941%28v=vs.85%29.aspx
Reference
https://owasp.org/www-community/Security_Headers
CWE Id 16
WASC Id 15
Source ID 3
Informational (Medium) Content-Type Header Missing
Description The Content-Type header was either missing or empty.
URL https://hackthissite.org/manifest.webmanifest
Method GET
Instances 1
Solution Ensure each page is setting the specific and appropriate content-type value for the content being delivered.
Reference http://msdn.microsoft.com/en-us/library/ie/gg622941%28v=vs.85%29.aspx
CWE Id 345
WASC Id 12
Source ID 3
Informational (Low) Timestamp Disclosure - Unix
Description A timestamp was disclosed by the application/web server - Unix
URL https://hackthissite.org/sitemap.xml
Method GET
Evidence 31536000
URL https://hackthissite.org/robots.txt
Method GET
Evidence 31536000
URL https://hackthissite.org/hp.php
Method GET
Evidence 31536000
URL https://hackthissite.org/manifest.webmanifest
Method GET
Evidence 31536000
URL https://hackthissite.org/missions/
Method GET
Evidence 31536000
URL https://hackthissite.org/killing/all/humans/
Method GET
Evidence 31536000
URL https://hackthissite.org/
Method GET
Evidence 31536000
Instances 7
Solution Manually confirm that the timestamp data is not sensitive, and that the data cannot be aggregated to disclose exploitable patterns.
Other information 31536000, which evaluates to: 1970-12-31 19:00:00
Reference http://projects.webappsec.org/w/page/13246936/Information%20Leakage
CWE Id 200
WASC Id 13
Source ID 3
Informational (Low) Timestamp Disclosure - Unix
Description A timestamp was disclosed by the application/web server - Unix
URL http://hackthissite.org/
Method GET
Evidence 31536000
Instances 1
Solution Manually confirm that the timestamp data is not sensitive, and that the data cannot be aggregated to disclose exploitable patterns.
Other information 31536000, which evaluates to: 1970-12-31 19:00:00
Reference http://projects.webappsec.org/w/page/13246936/Information%20Leakage
CWE Id 200
WASC Id 13
Source ID 3
You might also like
- Web Penetration Testing with Kali Linux - Second EditionFrom EverandWeb Penetration Testing with Kali Linux - Second EditionNo ratings yet
- (Divi Report) Daptatech RepDocument5 pages(Divi Report) Daptatech RepcarlosNo ratings yet
- ETHICAL HACKING GUIDE-Part 3: Comprehensive Guide to Ethical Hacking worldFrom EverandETHICAL HACKING GUIDE-Part 3: Comprehensive Guide to Ethical Hacking worldNo ratings yet
- (Divi Report) TokenlabDocument12 pages(Divi Report) TokenlabcarlosNo ratings yet
- Cargill Web Application Scanning ReportDocument27 pagesCargill Web Application Scanning ReportHari KingNo ratings yet
- OWASP ZAP Scan ReportDocument101 pagesOWASP ZAP Scan ReportSyafri muhammadNo ratings yet
- Vulnerabiliades - DiccionarioDocument142 pagesVulnerabiliades - DiccionarioJohan MorilloNo ratings yet
- CiscoDocument92 pagesCiscoari sirwanNo ratings yet
- ZAP Scanning Report: Site: Https://webapps - Bps.go - IdDocument4 pagesZAP Scanning Report: Site: Https://webapps - Bps.go - Idyoga_wpNo ratings yet
- ResultDocument83 pagesResultMaryamNo ratings yet
- ZAP Scanning: Project 2Document24 pagesZAP Scanning: Project 2Sabyasachi duttaNo ratings yet
- Category Sub-Category Status: Pre-Scan AnalysisDocument53 pagesCategory Sub-Category Status: Pre-Scan AnalysisVusraNo ratings yet
- Exploiting Cors Misconfigurations: For Bitcoins and BountiesDocument31 pagesExploiting Cors Misconfigurations: For Bitcoins and BountiesYash Sancheti100% (1)
- Owasp Zap Scanner Output 2024-02-29Document21 pagesOwasp Zap Scanner Output 2024-02-29b.nandhu2810No ratings yet
- Developer Report: Acunetix Website Audit 23 December, 2021Document7 pagesDeveloper Report: Acunetix Website Audit 23 December, 2021BAGAS TRI RAMADANA -No ratings yet
- Phase2 Security ReportDocument64 pagesPhase2 Security ReportAnonymous r3xb805ENo ratings yet
- VAPT TrainingDocument4 pagesVAPT Trainingkatruvale737No ratings yet
- Executive: Acunetix Security AuditDocument3 pagesExecutive: Acunetix Security AuditIbrahim qashtaNo ratings yet
- Website Vulnerability Scanner Report (Light)Document4 pagesWebsite Vulnerability Scanner Report (Light)MasBaNo ratings yet
- 2022 12 27 ZAP ReportDocument7 pages2022 12 27 ZAP ReportRandomG05No ratings yet
- CEH CheatsheetDocument5 pagesCEH CheatsheetVolkan Geyik100% (1)
- Threat Analysis Report: Hash Values File Details EnvironmentDocument28 pagesThreat Analysis Report: Hash Values File Details Environmenttodo nothingNo ratings yet
- Web Application Audit Report: Demo AccountDocument12 pagesWeb Application Audit Report: Demo AccountSamuel KonanNo ratings yet
- Comprehensive Report: Acunetix Threat Level 3Document37 pagesComprehensive Report: Acunetix Threat Level 3Yudha Trias RusmanaNo ratings yet
- Delhi Ford 1Document18 pagesDelhi Ford 1Vivek GautamNo ratings yet
- PentestTools WebsiteScanner ReportDocument4 pagesPentestTools WebsiteScanner ReportdeldengcNo ratings yet
- Comprehensive Report: Acunetix Threat Level 3Document23 pagesComprehensive Report: Acunetix Threat Level 3bugtestNo ratings yet
- Comprehensive Report: Acunetix Threat Level 3Document38 pagesComprehensive Report: Acunetix Threat Level 3Yudha Trias RusmanaNo ratings yet
- 5255 - 44 - 20112023 12 - 00 - 00 A. M.Document129 pages5255 - 44 - 20112023 12 - 00 - 00 A. M.fredyNo ratings yet
- 2022 08 CySADocument15 pages2022 08 CySAPhuc EVNHCMC-Dang Nguyen HongNo ratings yet
- Quick Report: Acunetix Security AuditDocument25 pagesQuick Report: Acunetix Security AuditCristian RamirezNo ratings yet
- Threat Analysis ReportDocument18 pagesThreat Analysis Reporttodo nothingNo ratings yet
- Ridho Abdul MajidDocument24 pagesRidho Abdul MajidRidho Abdul MajidNo ratings yet
- Robert Arias 20163930 Ubuntu Test 2 - ZnhxabDocument38 pagesRobert Arias 20163930 Ubuntu Test 2 - ZnhxabNico RosarioNo ratings yet
- Website Vulnerability Scanner Report (Light)Document5 pagesWebsite Vulnerability Scanner Report (Light)Ilija DodevskiNo ratings yet
- What To Hunt As Beginner...Document16 pagesWhat To Hunt As Beginner...Atkale AjitNo ratings yet
- Information Disclosure VulnerabilityDocument8 pagesInformation Disclosure Vulnerabilitysetyahangga3No ratings yet
- Website Vulnerability Scanner Report (Light)Document6 pagesWebsite Vulnerability Scanner Report (Light)alex681219No ratings yet
- Hacker101 Syllabus PDFDocument1 pageHacker101 Syllabus PDFBelinda AdriyantiNo ratings yet
- Devops Technical TestDocument6 pagesDevops Technical TestRichard PhillipsNo ratings yet
- A Specimen of Network Security Scan ReportDocument68 pagesA Specimen of Network Security Scan ReportM. Saad JumaniNo ratings yet
- Reporte 3Document20 pagesReporte 3Israel AlbaNo ratings yet
- Report For Foophones: by Utkarsh MunraDocument37 pagesReport For Foophones: by Utkarsh Munrasuraj fbNo ratings yet
- Suip - Biz: Localbitcoins Vds Donation FeedbackDocument1 pageSuip - Biz: Localbitcoins Vds Donation Feedbackryo020288No ratings yet
- Hardening Enterprise Apache Installations: Sander TemmeDocument39 pagesHardening Enterprise Apache Installations: Sander Temmewcai88No ratings yet
- Website Vulnerability Scanner Report (Light)Document6 pagesWebsite Vulnerability Scanner Report (Light)Stevi NangonNo ratings yet
- Cisa Notes 2 (AutoRecovered)Document66 pagesCisa Notes 2 (AutoRecovered)si lut liNo ratings yet
- PentestTools WebsiteScanner ReportDocument5 pagesPentestTools WebsiteScanner ReportmiguelNo ratings yet
- Owasp Top 10 Attacks and Mitigation: Detox TechnologiesDocument25 pagesOwasp Top 10 Attacks and Mitigation: Detox TechnologiesShitesh SachanNo ratings yet
- PentestTools WebsiteScanner ReportDocument4 pagesPentestTools WebsiteScanner ReporttcNo ratings yet
- Website Vulnerability Scanner Report (Light)Document5 pagesWebsite Vulnerability Scanner Report (Light)Muhammad LuludNo ratings yet
- Cybersecurity Preliminary Audit ForDocument15 pagesCybersecurity Preliminary Audit ForWaldo WooNo ratings yet
- Owasp Zap Hostedscan Report 2024-02-12Document17 pagesOwasp Zap Hostedscan Report 2024-02-12faizan.rezaNo ratings yet
- 10a - Web SecurityDocument14 pages10a - Web SecurityAlif FaisalNo ratings yet
- 33小铺扫描附件Document9 pages33小铺扫描附件ni koNo ratings yet
- Wapiti Vulnerability Report: Target: Http://123.231.148.147:8081/webserviceDocument7 pagesWapiti Vulnerability Report: Target: Http://123.231.148.147:8081/webservicePlokodot PlokodotNo ratings yet
- Active Recon Cheat SheetDocument3 pagesActive Recon Cheat Sheetlbb1987No ratings yet
- TOP TEN OWASP Vs ChatGPT For CybersecurityDocument14 pagesTOP TEN OWASP Vs ChatGPT For Cybersecuritysawako.not.sadako1008No ratings yet
- Browser Security I (Slides)Document56 pagesBrowser Security I (Slides)Dan VollekNo ratings yet
- OSCP Methodology NotesDocument41 pagesOSCP Methodology NotesGaétan NG100% (1)
- (PDF) Solucion Eje 3Document9 pages(PDF) Solucion Eje 3Keiner ZarateNo ratings yet
- Funciones Basicas SeleniumDocument42 pagesFunciones Basicas SeleniumRaksasa RepulsiveNo ratings yet
- Lectura 1 Actividad 2Document14 pagesLectura 1 Actividad 2Christian Bernal SánchezNo ratings yet
- Plan Lector 3 CAP 2019Document8 pagesPlan Lector 3 CAP 2019Anonymous onELU9sc9No ratings yet
- Understanding Itu G709 Standard For Optical NetworksDocument60 pagesUnderstanding Itu G709 Standard For Optical NetworksFida Mohammad100% (1)
- Lab 6.2 Configuring CBAC: Learning ObjectivesDocument8 pagesLab 6.2 Configuring CBAC: Learning ObjectivesejulkyNo ratings yet
- En FMBT-21 Um B A4Document92 pagesEn FMBT-21 Um B A4Sami DaoudNo ratings yet
- 2023-03-10 Nmap Default ReportDocument1 page2023-03-10 Nmap Default ReportHarisNo ratings yet
- Crypto ASSIGNMENT 1Document6 pagesCrypto ASSIGNMENT 1deekshithj ShettyNo ratings yet
- Annexure A TecGRsDocument62 pagesAnnexure A TecGRsRuchir ChaturvediNo ratings yet
- Networking BasicsDocument53 pagesNetworking BasicsSahil Showkat100% (1)
- s2s VPN User GuideDocument57 pagess2s VPN User GuidealozieNo ratings yet
- Ccnpv7 Route Lab7-2 BGP As Path InstructorDocument11 pagesCcnpv7 Route Lab7-2 BGP As Path Instructortaco19933No ratings yet
- Top 100 Common PortsDocument1 pageTop 100 Common PortsRafa EstepaNo ratings yet
- Capture Config Ipmd MRD AmbarawaDocument19 pagesCapture Config Ipmd MRD AmbarawaAnonymous Lr84U3PCNo ratings yet
- 12 - 4G - Parameter - SON PDFDocument27 pages12 - 4G - Parameter - SON PDFSatria WibowoNo ratings yet
- Noc18 cs38 Assignment2Document4 pagesNoc18 cs38 Assignment2Pallab ChakrabortyNo ratings yet
- HP ProCurve Switch 2510 SeriesDocument8 pagesHP ProCurve Switch 2510 SeriesArjo BoledNo ratings yet
- FW3505 19.5v1 Introducing Authentication On Sophos FirewallDocument17 pagesFW3505 19.5v1 Introducing Authentication On Sophos FirewallAndré MouraNo ratings yet
- Full Ipa Server Client SetupDocument13 pagesFull Ipa Server Client SetupSri WasteNo ratings yet
- 4 .2.1 Client - Server: P Art1Document18 pages4 .2.1 Client - Server: P Art1ariNo ratings yet
- Build & Deploy Secure Shorewall Firewall Protected Network v1.2Document9 pagesBuild & Deploy Secure Shorewall Firewall Protected Network v1.2Kefa RabahNo ratings yet
- DS-2CD1323G0-IU 2 MP IR Fixed Turret Network CameraDocument5 pagesDS-2CD1323G0-IU 2 MP IR Fixed Turret Network CameraAhmed Abd El AziZNo ratings yet
- Unit-5: Communication Technologies: NetworkDocument14 pagesUnit-5: Communication Technologies: NetworkHari CNo ratings yet
- 10.3.1.2 Packet Tracer - Skills Integration Challenge InstructionsDocument2 pages10.3.1.2 Packet Tracer - Skills Integration Challenge InstructionsMarc Wallin50% (2)
- Types of Computer MisuseDocument10 pagesTypes of Computer MisuseSamNo ratings yet
- BSNL BB Error Codes in ADSL TechnologyDocument4 pagesBSNL BB Error Codes in ADSL TechnologyburraganeshNo ratings yet
- Simple Plan For Networking A Small Scale HospitalDocument10 pagesSimple Plan For Networking A Small Scale HospitalRakhita Darshana GajanayakeNo ratings yet
- Lab - Determine The MAC Address of A Host: TopologyDocument5 pagesLab - Determine The MAC Address of A Host: TopologyAnuj PatelNo ratings yet
- CCENT Lab 4 1 Configuring Static Routes v1.0.1Document43 pagesCCENT Lab 4 1 Configuring Static Routes v1.0.1Bijay LamaNo ratings yet
- Unit 1 - Part2 - Multiple AccessDocument44 pagesUnit 1 - Part2 - Multiple AccessSimran100% (1)
- Bv9ARM GuideDocument249 pagesBv9ARM GuideAndrei LazarNo ratings yet
- Ethernet Packet Rate and Throughput Calculations - Ciena CommunityDocument8 pagesEthernet Packet Rate and Throughput Calculations - Ciena Communityy_m_algbaliNo ratings yet
- Netflow Con FlowDocument11 pagesNetflow Con FlowAngel Mendoza LoredoNo ratings yet