Professional Documents
Culture Documents
IICS Data Security
Uploaded by
ajaybhosalOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
IICS Data Security
Uploaded by
ajaybhosalCopyright:
Available Formats
FAQ: How data gets encrypted in IICS at rest and in transit.
Solution
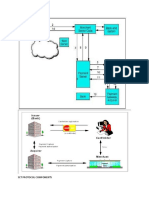
Data transmission security is a key aspect of securing data. In processing data, the Secure Agent communicates
with both the IICS host and data stores/SaaS applications.
This communication is secured as follows:
The Secure Agent initiates communication with Informatica Intelligent Cloud Services through a secure channel
and supports various tokens, such as username, SAML, or X.509 certificates. No inbound firewall ports need to
be opened at the user site for the user-hosted Secure Agent to communicate with the IICS host. The Secure
Agent code creates a virtual socket connection to communicate to the host and uses port 443 for all outbound
communication. The Secure Agent avoids data loss and transport delays by checking for availability before
connecting. The Secure Agent also performs network resiliency checks and retains full audit and session logs for
configurable duration to track any issue that may arise.
ENCRYPTION AT REST
The data is encrypted using the AES encryption algorithm. The AES encryption uses a 256-bit key with CBC and
PKC5 padding. Services like Integration Hub will store data on the IICS host in a multi-tenant data repository back
end.
ENCRYPTION IN TRANSIT
To defend against sniffer or man-in-the-middle attacks, the communication channel must be authenticated to
maintain its integrity, as well as ensure transport encryption. To achieve that, the Secure Agent authenticates
with the IICS host first using an SSL handshake and a digital certificate. All communication from the Secure
Agent to the IICS host is Transport Layer Security (TLS) 1.2 encrypted using AES256-SHA (256 bit) cipher.
The Secure Agent connects to source/target data stores and cloud applications using connectors. Connectors
are configured and support a variety of secure communication protocols like HTTPS, SFTP, FTPS, certificates,
etc. IICS leverages the underlying transport layer of these connector communication protocols to ensure that the
data is transmitted securely across data stores and applications. The data is transmitted encrypted via Transport
Layer Security (TLS) using AES (256 bit) cipher.
You might also like
- InternetsecurityprotocolsDocument30 pagesInternetsecurityprotocolsAvi SirikondaNo ratings yet
- Secure Networking 101 MACsec, IPsec, and SSL BasicsDocument10 pagesSecure Networking 101 MACsec, IPsec, and SSL BasicsazertyNo ratings yet
- Secure Socket Layer (SSL)Document47 pagesSecure Socket Layer (SSL)Wasif ImranNo ratings yet
- Security ProtocolsDocument4 pagesSecurity Protocolsapi-3701346No ratings yet
- Unit 5 Transport Level SecurityDocument81 pagesUnit 5 Transport Level SecurityBharath Kumar T VNo ratings yet
- Information System SecurityDocument5 pagesInformation System SecurityPurva SukhwalNo ratings yet
- Web SecurityDocument17 pagesWeb SecurityUchiha SasukeNo ratings yet
- Student Activity 1.3 Key: Internet Security: Ecurity UndamentalsDocument2 pagesStudent Activity 1.3 Key: Internet Security: Ecurity UndamentalsFmunoz MunozNo ratings yet
- SOP 10.1.1 Data EncryptionDocument7 pagesSOP 10.1.1 Data EncryptionAdam AdamNo ratings yet
- Cns QuizDocument2 pagesCns QuizDhivya SivakumarNo ratings yet
- Secure Socket Layer (SSL) : Divey Gupta Sunny Gajjar B.Tech-IV Computer Engg. NIT-SuratDocument22 pagesSecure Socket Layer (SSL) : Divey Gupta Sunny Gajjar B.Tech-IV Computer Engg. NIT-SuratSunny Kishorbhai GajjarNo ratings yet
- CS Module 4Document9 pagesCS Module 4OK BYENo ratings yet
- Network NotesDocument16 pagesNetwork Notesboka987No ratings yet
- Ipsec: Tcp/IpDocument12 pagesIpsec: Tcp/IpSaptarshi BhattacharjeeNo ratings yet
- DocumentDocument1 pageDocumentHassan AhmadNo ratings yet
- Transport Layer SecurityDocument3 pagesTransport Layer Securityfawas hamdiNo ratings yet
- Transport Layer Protection Cheat SheetDocument6 pagesTransport Layer Protection Cheat SheetRoman PotapovNo ratings yet
- Secure Communication Channels: Secure Sockets Layer (SSL)Document5 pagesSecure Communication Channels: Secure Sockets Layer (SSL)Mani ShankarNo ratings yet
- Chapter 3 InternetDocument29 pagesChapter 3 InternetPurvaNo ratings yet
- ShibdasChakrabortyDocument10 pagesShibdasChakrabortyshibdasc339No ratings yet
- SSLDocument122 pagesSSLKabilan KabilNo ratings yet
- Transport Layer Security: Presented by Abhiram SahuDocument19 pagesTransport Layer Security: Presented by Abhiram SahuAbhiram SahuNo ratings yet
- Vulnerabilities of The SSL Tls ProtocolDocument12 pagesVulnerabilities of The SSL Tls ProtocolManish AgarwalNo ratings yet
- Ipsec Internet Protocol SecurityDocument8 pagesIpsec Internet Protocol SecurityRamakrishna ReddyNo ratings yet
- 1secure ShellDocument39 pages1secure ShellJayaprasannaNo ratings yet
- NSC Unit - 3 - 221210 - 134942Document29 pagesNSC Unit - 3 - 221210 - 134942SurenderNo ratings yet
- 6-Web Application SecurityDocument36 pages6-Web Application Securityep230842No ratings yet
- Transport Layer Security (TLS)Document14 pagesTransport Layer Security (TLS)svmc bcaNo ratings yet
- Lecture11 - Week 11Document30 pagesLecture11 - Week 11Vishwa MoorthyNo ratings yet
- Transport Layer Security (TLS)Document14 pagesTransport Layer Security (TLS)svmc bcaNo ratings yet
- Presented By: Kulwinder Priyanka PriyaDocument70 pagesPresented By: Kulwinder Priyanka PriyaPriya RainaNo ratings yet
- SSL PresentationDocument10 pagesSSL Presentationtreesachandt100% (1)
- Network Security Unit 4Document32 pagesNetwork Security Unit 4Satyam PandeyNo ratings yet
- Security in e - CommerceDocument4 pagesSecurity in e - CommerceAlex T BinoyNo ratings yet
- Pki Entities: Certificate Authority (CA)Document15 pagesPki Entities: Certificate Authority (CA)Arifur RahmanNo ratings yet
- Week-10 Transport Layer SecurityDocument12 pagesWeek-10 Transport Layer SecurityHala GharibNo ratings yet
- VPN Security ProtocolsDocument7 pagesVPN Security Protocolsmhds0hail0705No ratings yet
- Cyber-Security Toolbox Edition 3Document35 pagesCyber-Security Toolbox Edition 3Laurent DuradNo ratings yet
- Tectia SSH Server For Linux On IBM System ZDocument2 pagesTectia SSH Server For Linux On IBM System ZJohnNo ratings yet
- CSS 4Document20 pagesCSS 4Imran K DhanjiNo ratings yet
- Gyan Prakash's Research PaperDocument8 pagesGyan Prakash's Research Papercoolbooy6996No ratings yet
- Information Security Unit3Document6 pagesInformation Security Unit3anushk jainNo ratings yet
- CNS WBDocument45 pagesCNS WBPrakash RajNo ratings yet
- Ipsec ThesisDocument8 pagesIpsec Thesistiffanyrosehartford100% (1)
- ITNE 3013 Advanced Network and Information SecurityDocument4 pagesITNE 3013 Advanced Network and Information SecurityRupesh PandeyNo ratings yet
- DiniDocument20 pagesDiniiraj shaikhNo ratings yet
- DCOM 258 Lab 14 PKI & Encryption ProtocolsDocument4 pagesDCOM 258 Lab 14 PKI & Encryption ProtocolsShaamim U AhmedNo ratings yet
- Web SecurityDocument16 pagesWeb SecurityhussamNo ratings yet
- Transport Level Security PresentationDocument30 pagesTransport Level Security PresentationAhimbisibwe BakerNo ratings yet
- Security: in SIP-Based NetworksDocument11 pagesSecurity: in SIP-Based Networkshuongpv_vtn1No ratings yet
- Unit 4 - Presentation2Document28 pagesUnit 4 - Presentation2parthjethva1407No ratings yet
- Web SecurityDocument18 pagesWeb Securitykrii24u8No ratings yet
- SSL VPN For CLNDocument29 pagesSSL VPN For CLNVJ SNGNo ratings yet
- Newcomer 08Document36 pagesNewcomer 08vmeshalkinNo ratings yet
- IntroductionDocument3 pagesIntroductionELDER LAGGAHNo ratings yet
- SSL - Secure Sockets LayerDocument15 pagesSSL - Secure Sockets Layerhareem100No ratings yet
- Ip SecurityDocument10 pagesIp SecuritySaqib ShariffNo ratings yet
- Securing .NET Web Services with SSL: How to Protect “Data in Transit” between Client and Remote ServerFrom EverandSecuring .NET Web Services with SSL: How to Protect “Data in Transit” between Client and Remote ServerNo ratings yet
- Tableau Training PlanDocument4 pagesTableau Training PlanajaybhosalNo ratings yet
- Steps Settings Change Cloned MachineDocument3 pagesSteps Settings Change Cloned MachineajaybhosalNo ratings yet
- Lab Activity Sets ScenarioDocument1 pageLab Activity Sets ScenarioajaybhosalNo ratings yet
- Quiz Sample2Document5 pagesQuiz Sample2ajaybhosalNo ratings yet
- SAML SetupDocument3 pagesSAML SetupajaybhosalNo ratings yet
- Module 5 - Cloud Mapping Designer - TransformationsDocument26 pagesModule 5 - Cloud Mapping Designer - TransformationsajaybhosalNo ratings yet
- DWC ClassBook Lesson01Document15 pagesDWC ClassBook Lesson01ajaybhosalNo ratings yet
- Module 3 - Synchronization Task and Data Transfer TaskDocument37 pagesModule 3 - Synchronization Task and Data Transfer TaskajaybhosalNo ratings yet
- Module 4 - Cloud Mapping DesignerDocument22 pagesModule 4 - Cloud Mapping DesignerajaybhosalNo ratings yet
- Module 2Document12 pagesModule 2ajaybhosalNo ratings yet
- Module 1Document23 pagesModule 1ajaybhosalNo ratings yet
- Scenario Based QuestionsDocument14 pagesScenario Based QuestionsajaybhosalNo ratings yet
- Sprint Case - Study IICS - UpdatedDocument3 pagesSprint Case - Study IICS - UpdatedajaybhosalNo ratings yet
- SHWETHA Resume PDFDocument2 pagesSHWETHA Resume PDFajaybhosalNo ratings yet
- CDE-Foundation TOCDocument5 pagesCDE-Foundation TOCajaybhosalNo ratings yet