Professional Documents
Culture Documents
Ideas
Ideas
Uploaded by
r0wy 2300 ratings0% found this document useful (0 votes)
4 views1 pageThis document discusses scanning multiple subnets to check for open ports using vulnerable protocols like FTP and SMB, and using banner requests to identify vulnerable versions of those protocols. It also mentions automating vulnerability scanning to check for exploits against printers.
Original Description:
Copyright
© © All Rights Reserved
Available Formats
TXT, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentThis document discusses scanning multiple subnets to check for open ports using vulnerable protocols like FTP and SMB, and using banner requests to identify vulnerable versions of those protocols. It also mentions automating vulnerability scanning to check for exploits against printers.
Copyright:
© All Rights Reserved
Available Formats
Download as TXT, PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
4 views1 pageIdeas
Ideas
Uploaded by
r0wy 230This document discusses scanning multiple subnets to check for open ports using vulnerable protocols like FTP and SMB, and using banner requests to identify vulnerable versions of those protocols. It also mentions automating vulnerability scanning to check for exploits against printers.
Copyright:
© All Rights Reserved
Available Formats
Download as TXT, PDF, TXT or read online from Scribd
You are on page 1of 1
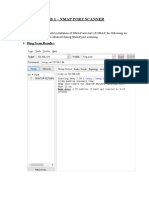
be able to scan multiple subnets
check open ports for vulnerable protocols, ftp, smb etc.
use banner requests to check if it is a vulnerable version of this protocol
Automate vulnerability scanning for printer exploit
You might also like
- Vulnerability Analysis - HolDocument30 pagesVulnerability Analysis - Holmuh julyawanNo ratings yet
- PDF 24Document13 pagesPDF 24milonNo ratings yet
- Catch Me, If You Can Evading Network Signatures With Web-Based Polymorphic WormsDocument9 pagesCatch Me, If You Can Evading Network Signatures With Web-Based Polymorphic WormsJohn GacheruNo ratings yet
- Keep Calm and Hack The BoxDocument24 pagesKeep Calm and Hack The Boxnana100% (1)
- Linux Forensics CheatsheetDocument1 pageLinux Forensics CheatsheetTrong NguyenNo ratings yet
- WUMprepDocument3 pagesWUMprepCarlos LuisNo ratings yet
- Proxy For FTP: Project DescriptionDocument1 pageProxy For FTP: Project DescriptionpavaniNo ratings yet
- A Full Website Hacking TutorialDocument50 pagesA Full Website Hacking Tutorialmodupe100% (1)
- Attacking Metasploitable2 VM Server Cameron WDocument20 pagesAttacking Metasploitable2 VM Server Cameron Wapi-502019278No ratings yet
- Buffer Overflow: White PaperDocument4 pagesBuffer Overflow: White PapergynxNo ratings yet
- MSF IiDocument12 pagesMSF IiGlowing StarNo ratings yet
- Linux - SFTP Command Help and ExamplesDocument65 pagesLinux - SFTP Command Help and ExamplesLuc ChantelNo ratings yet
- VulnerabilitatiDocument12 pagesVulnerabilitatiIon DanNo ratings yet
- Pertemuan 7 Kelas Pentest - Metasploit - FinalDocument89 pagesPertemuan 7 Kelas Pentest - Metasploit - Finalsebenarnya gimanaNo ratings yet
- PentestTools TcpPortScan ReportDocument1 pagePentestTools TcpPortScan ReportMario Sernaque RumicheNo ratings yet
- Nmap PentestingDocument12 pagesNmap PentestingAnonymous Hb8sb2yM100% (1)
- Lab 5Document4 pagesLab 5kuljit kaurNo ratings yet
- Lab 1 - Nmap Port Scanner: Ping Scan ResultsDocument8 pagesLab 1 - Nmap Port Scanner: Ping Scan ResultsHema LathaNo ratings yet
- XyxudoDocument2 pagesXyxudoannu092380No ratings yet
- Lab - Exploring Endpoint Attacks: RequirementsDocument16 pagesLab - Exploring Endpoint Attacks: RequirementsMohcine OubadiNo ratings yet
- Exploits: Dalia SolomonDocument39 pagesExploits: Dalia SolomonnickNo ratings yet
- Lab 5Document4 pagesLab 5Derick cheruyotNo ratings yet
- Execution: 2. Literature ReviewDocument5 pagesExecution: 2. Literature Reviewapi-552030871No ratings yet
- Hacking Module 03Document69 pagesHacking Module 03Jitendra Kumar Dash100% (1)
- Port ScanningDocument10 pagesPort ScanningletharjicNo ratings yet
- Network Security Lab Manual DraftDocument29 pagesNetwork Security Lab Manual DraftShraddha PatilNo ratings yet
- Qulalys Sample ReportDocument6 pagesQulalys Sample Reporteagleboy007No ratings yet
- Linux Privilege EscalationDocument20 pagesLinux Privilege EscalationJuancaNo ratings yet
- Pen Testing Tools Cheat SheetDocument39 pagesPen Testing Tools Cheat Sheetsetyahangga3No ratings yet
- Nmap The Art of Port Scanning PDFDocument6 pagesNmap The Art of Port Scanning PDFJapari JaporaNo ratings yet
- Ubuntu Manpage - Crack, Reporter - Programs To Break Password FilesDocument4 pagesUbuntu Manpage - Crack, Reporter - Programs To Break Password FilesZoro Le RoiNo ratings yet
- Scanning Windows Deeper With The Nmap Scanning Engine: by Ron BowesDocument27 pagesScanning Windows Deeper With The Nmap Scanning Engine: by Ron BowesSalah BouchelaghemNo ratings yet
- Penetrator-Schematics Web PDFDocument2 pagesPenetrator-Schematics Web PDFmzamolo999No ratings yet
- NMAP - Information GatheringDocument6 pagesNMAP - Information GatheringRockstar GmailNo ratings yet
- 11-Class - Vulnerability Analysis and Exploitation - Information SecurityDocument25 pages11-Class - Vulnerability Analysis and Exploitation - Information SecuritySyeda Insharah RiazNo ratings yet
- Section 10 Understanding Common Endpoint Attacks LabDocument25 pagesSection 10 Understanding Common Endpoint Attacks LabritaNo ratings yet
- Scripting For Bash Vulnerability Shellshock ReportDocument5 pagesScripting For Bash Vulnerability Shellshock ReportnaomisowunmiNo ratings yet
- Dsniff DownloadDocument3 pagesDsniff DownloadAntónioNo ratings yet
- Comprehensive Guide On Metasploitable 2 Service ExploitationDocument24 pagesComprehensive Guide On Metasploitable 2 Service ExploitationAMAR SATAPPA CHAVAREKARNo ratings yet
- InceptionDocument10 pagesInceptionNguyễn ThịnhNo ratings yet
- OSCP Methodology NotesDocument41 pagesOSCP Methodology NotesGaétan NG100% (1)
- (FreeCourseWeb - Com) Software and Hardware ListDocument1 page(FreeCourseWeb - Com) Software and Hardware ListAbhinesh KumarNo ratings yet
- FF ServerDocument50 pagesFF Serverl6ginNo ratings yet
- Nmap 101Document25 pagesNmap 101Erpan ErpanNo ratings yet
- Control Standard Impact Procedure: 1.1 Environment 1.1.1Document43 pagesControl Standard Impact Procedure: 1.1 Environment 1.1.1Mike JobsNo ratings yet
- Cracking The Lens: Targeting HTTP's Hidden Attack Surface: OutlineDocument17 pagesCracking The Lens: Targeting HTTP's Hidden Attack Surface: OutlineoooNo ratings yet
- 04 - Useful ToolsDocument24 pages04 - Useful ToolsMatheus Biagini PereiraNo ratings yet
- Exploiting of Metasploit Machine Assessment Report: Assignment-3Document29 pagesExploiting of Metasploit Machine Assessment Report: Assignment-3venkatesh reddyNo ratings yet
- Ratio MasterDocument4 pagesRatio MasterManuela CulicaNo ratings yet
- RabbitMQ ArchitectureDocument8 pagesRabbitMQ ArchitectureSakthivel PNo ratings yet
- Lab - Isolated Compromised Host Using 5-TupleDocument33 pagesLab - Isolated Compromised Host Using 5-TupleSlaimi RaniaNo ratings yet
- Burp Suite: Cheat Sheet v1.0Document2 pagesBurp Suite: Cheat Sheet v1.0huynhphuc112No ratings yet
- Spos Unit 2 PPT 2022 CompressedDocument89 pagesSpos Unit 2 PPT 2022 Compressedअभिजित शिंदेNo ratings yet
- Relevant TryHackMe Pentesting Report by Dorota Kozlowska 1646244313 PDFDocument22 pagesRelevant TryHackMe Pentesting Report by Dorota Kozlowska 1646244313 PDFHanzo HayabutoNo ratings yet
- Path To CloudDocument92 pagesPath To CloudRAJA NAVEENNo ratings yet
- Virus Analysis 2Document2 pagesVirus Analysis 2prjaimitoNo ratings yet
- Us 18 Thomas It's A PHP Unserialization Vulnerability Jim But Not As We ...Document28 pagesUs 18 Thomas It's A PHP Unserialization Vulnerability Jim But Not As We ...dancagoNo ratings yet
- Black-Box Penetration Test 1Document29 pagesBlack-Box Penetration Test 1Leonardo FerreiraNo ratings yet
- Digital Assignment: Name: Ananth Sasank REG NO:19BIT0308Document11 pagesDigital Assignment: Name: Ananth Sasank REG NO:19BIT0308Youngling HunterNo ratings yet
- AllDocument48 pagesAlldont4getNo ratings yet