Professional Documents
Culture Documents
Cyber Ass 2
Uploaded by
Matt HowellOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Cyber Ass 2
Uploaded by
Matt HowellCopyright:
Available Formats
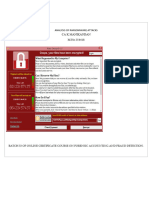
The Eternal Blue (MS17_010) exploit was found and allegedly developed by US NSA approximately 5
years(1) before leaked by Hacker group Shadow Brokers(2). It appears that the NSA found these
vulnerabilities, used them to create several exploits, of which, Eternal Blue is one, and failed to
disclose the weaknesses to Microsoft or anyone else. It was only until the Wanna Cry exploit was in
the wild, and had effected over 230,000 computers, that the US indicted two Koreans and a person
in the US. The exploit focus is on a vulnerability in SMB v1, basically the SMB Secondary Transactions
are malformed when the message request is greater than the SMB MaxBufferSize. (6) . Microsoft
released a patch immediately.(4). Yet this often relies on an update from the end user. So many
vulnerable systems remain! In fact, the ‘Eternal Rocks’ threat used 7 exploits from NSA leaked hacks
(3) This attack violates the CIA triad by damaging our confidence in the NSA, also, limiting availability
of files, after WannaCry uses the Eternal Blue exploit the compromised system is encrypted, thus
rendering it useless to the end user. The hacker will either use the exploit to just encrypt your files,
or demand money to unlock them. Police and Security Agencies all advise against paying the ransom,
which was in BitCoin, and thus untraceable, as it just encourages the attackers to keep using these
types of exploit(5). Plus there is no guarantee to recover your data, as they got sneakier and hid
behind VPN’s.
(1) https://en.wikipedia.org/wiki/EternalBlue
(2) https://www.avast.com/c-eternalblue
(3) https://www.csoonline.com/article/3197673/eternalrocks-network-worm-uses-7-nsa-hacking-
tools.html
(4) April 15, 2017. Microsoft Windows Shadow Brokers Nsa Hacks Patched
(5) Dummies' Guide to WannaCry - Infosecurity Magazine (infosecurity-magazine.com)
(6) SMB Exploited: WannaCry Use of "EternalBlue" | Mandiant
General
You might also like
- Cybersecurity: The Hacker Proof Guide To Cybersecurity, Internet Safety, Cybercrime, & Preventing AttacksFrom EverandCybersecurity: The Hacker Proof Guide To Cybersecurity, Internet Safety, Cybercrime, & Preventing AttacksNo ratings yet
- WannaCryRansomwareAttack AnEthicalOverlookDocument8 pagesWannaCryRansomwareAttack AnEthicalOverlookvignesh shivkumarNo ratings yet
- Case - Study - Wannatry AttackDocument11 pagesCase - Study - Wannatry AttackSHUBHAM PATIL SPNo ratings yet
- WannaCry Explained - A Perfect Ransomware Storm - CSO OnlineDocument6 pagesWannaCry Explained - A Perfect Ransomware Storm - CSO OnlineLushenthaNo ratings yet
- MN502 Overview of Network SecurityDocument10 pagesMN502 Overview of Network SecurityAniket ChatterjeeNo ratings yet
- IT Project: Sarthak Gupta Class X A' Roll No. 33Document8 pagesIT Project: Sarthak Gupta Class X A' Roll No. 33SahilGupta100% (1)
- Wannacry Aftershock: Peter MackenzieDocument14 pagesWannacry Aftershock: Peter MackenzieDavid AaguluNo ratings yet
- Ransomeware Attack in Cyber Security:A Case Study: NtroductionDocument4 pagesRansomeware Attack in Cyber Security:A Case Study: NtroductionbabajiNo ratings yet
- Wanna Cry On NewsDocument9 pagesWanna Cry On Newsmario ansoteguiNo ratings yet
- Ransomware - Evolution Mitigation and PreventionDocument13 pagesRansomware - Evolution Mitigation and PreventionMogabs MogabsNo ratings yet
- ENISADocument18 pagesENISAGamer LoverNo ratings yet
- Infrascale Enterprise Ransomware Survival Guide EbookDocument17 pagesInfrascale Enterprise Ransomware Survival Guide EbookDavid SilesNo ratings yet
- AssignmentDocument4 pagesAssignmentYasir LatifNo ratings yet
- Computer Worms: Sadique NayeemDocument20 pagesComputer Worms: Sadique NayeemSadique NayeemNo ratings yet
- Wipro CRS Threat Advisory - WannaCry Ransomware 1.1Document12 pagesWipro CRS Threat Advisory - WannaCry Ransomware 1.1pallavsinhaNo ratings yet
- Wanna Cry On NewsDocument11 pagesWanna Cry On NewsmarcosyasierNo ratings yet
- RansomwareDocument29 pagesRansomwarewaqas haiderNo ratings yet
- Manal Alhejaily Lab Assignment 3Document6 pagesManal Alhejaily Lab Assignment 3Manal SaeedNo ratings yet
- What Is RansomwareDocument6 pagesWhat Is RansomwareGerald TorresNo ratings yet
- Wanna CryDocument4 pagesWanna CrysicelosmavusoNo ratings yet
- WGU Cyberwarfare Task 1Document12 pagesWGU Cyberwarfare Task 1Christopher Tijerina100% (1)
- Cybercrime Is Any Criminal Activity That InvolvesDocument4 pagesCybercrime Is Any Criminal Activity That InvolvesNISHANT RNo ratings yet
- Ransomware Attacks in History of Cyber WorldDocument7 pagesRansomware Attacks in History of Cyber WorldIJRASETPublicationsNo ratings yet
- Computer Networks NoteDocument38 pagesComputer Networks NoteSimple GuptaNo ratings yet
- WannaCry Ransomware (2017)Document14 pagesWannaCry Ransomware (2017)Gilbran KhatamiNo ratings yet
- BrennDocument1 pageBrennmonzonesbrenncarloNo ratings yet
- 333Document4 pages333ewan ko bahNo ratings yet
- Critical Exploits For Sale On The Dark WebDocument20 pagesCritical Exploits For Sale On The Dark WebquantumkNo ratings yet
- School of Computer Sciences Universiti Sains Malaysia PenangDocument21 pagesSchool of Computer Sciences Universiti Sains Malaysia Penangaurox3dNo ratings yet
- Threat-Bulletin BadRabbit 10-2017 PDFDocument3 pagesThreat-Bulletin BadRabbit 10-2017 PDFKapil ChulaniNo ratings yet
- Talk of The Hour, Wannacrypt Ransomware: Technical ReportDocument5 pagesTalk of The Hour, Wannacrypt Ransomware: Technical ReportBerry SitepuNo ratings yet
- RANSOMWARE: Most Recent Threat To Computer Network Security: February 2017Document24 pagesRANSOMWARE: Most Recent Threat To Computer Network Security: February 2017AKASH MITTAL KEC STUDENT (CSE)No ratings yet
- Detection and Avoidance of Ransomware: S.Mahmudha Fasheem, P.Kanimozhi, B.AkoramurthyDocument6 pagesDetection and Avoidance of Ransomware: S.Mahmudha Fasheem, P.Kanimozhi, B.AkoramurthyalexusmatrixNo ratings yet
- Computer HackingDocument37 pagesComputer HackingArchu Deoli100% (1)
- Laporan Praktikum Keamanan Siber - Tugas 6 - Kelas C - Kelompok 3Document5 pagesLaporan Praktikum Keamanan Siber - Tugas 6 - Kelas C - Kelompok 3I Gede Arie Yogantara SubrataNo ratings yet
- Analysis of Ransomware AttacksDocument11 pagesAnalysis of Ransomware AttacksDanielleosunfeastNo ratings yet
- Activity 2 Audit On CISDocument4 pagesActivity 2 Audit On CISPaupauNo ratings yet
- Chapter 3: Tools and Methods Used in CybercrimeDocument34 pagesChapter 3: Tools and Methods Used in CybercrimeNarasimha MurthyNo ratings yet
- Static and Dynamic Analysis of Wannacry Ransomware: July 2018Document6 pagesStatic and Dynamic Analysis of Wannacry Ransomware: July 2018Schubert BalizaNo ratings yet
- Evil ZineDocument36 pagesEvil Zinen123v100% (1)
- Sia 06 Task Performance 1InfoSecDocument3 pagesSia 06 Task Performance 1InfoSecGela SiaNo ratings yet
- Know Your Enemy - IDocument3 pagesKnow Your Enemy - Izakharia1No ratings yet
- Most Dangerous Computer VirusesDocument5 pagesMost Dangerous Computer VirusesMuhammad Ali AliNo ratings yet
- Presentation 1Document17 pagesPresentation 1AKASH MITTAL KEC STUDENT (CSE)No ratings yet
- 14.1.11 Lab - Anatomy of MalwareDocument1 page14.1.11 Lab - Anatomy of Malwarekrisna mulyanaNo ratings yet
- Kasperski Tõlge 142 (Kahjurprogrammide Arengusuunad, 2005 Aasta Teine Kvartal)Document18 pagesKasperski Tõlge 142 (Kahjurprogrammide Arengusuunad, 2005 Aasta Teine Kvartal)vasjaNo ratings yet
- Wanna Cry On NewsDocument9 pagesWanna Cry On NewsAngelicaNo ratings yet
- IAS HomeworkDocument5 pagesIAS HomeworkanniNo ratings yet
- Clop RansomwareDocument20 pagesClop RansomwareJohn Kenneth CabreraNo ratings yet
- BTIT603: Cyber and Network Security: BotnetDocument15 pagesBTIT603: Cyber and Network Security: BotnetKajalNo ratings yet
- Ransomware Investigation Osint and Hunting - Overview PT1 2Document48 pagesRansomware Investigation Osint and Hunting - Overview PT1 2Aung Myo KhantNo ratings yet
- VirusesDocument4 pagesVirusesLiza SoberanoNo ratings yet
- The Osint Cyber War 2023-06-19Document26 pagesThe Osint Cyber War 2023-06-19David Sanchez TorresNo ratings yet
- Dilemma On RansomwareDocument6 pagesDilemma On RansomwareLeonil TangubNo ratings yet
- Anatomy of ThreatDocument4 pagesAnatomy of ThreatSatya PriyaNo ratings yet
- Darknet and Deepnet Mining For Proactive Cybersecurity Threat IntelligenceDocument6 pagesDarknet and Deepnet Mining For Proactive Cybersecurity Threat IntelligenceJorgeNo ratings yet
- 16.2.6 Lab - Research Network Security Threats - ILMDocument4 pages16.2.6 Lab - Research Network Security Threats - ILMMariano PereyraNo ratings yet
- Case StudyDocument13 pagesCase StudyShubham RaiNo ratings yet
- IAS Pre FiDocument4 pagesIAS Pre FiGela SiaNo ratings yet