Professional Documents
Culture Documents
Account Take Over Report PDF
Uploaded by
叶佩丽Original Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Account Take Over Report PDF
Uploaded by
叶佩丽Copyright:
Available Formats
Host Header Poisoning On Password Reset Functionality
Vulnerable page
https://itp.tarc.edu.my/
Summary
Host Header Injection on Password Reset Functionality that lead to 1 Click Account Takeover.
Steps to Reproduce
The HTTP Host header is a mandatory request header as of HTTP/1.1. It specifies the domain name
that the client wants to access. For example, when a user visits https://google.com/web-
security , their browser will compose a request containing a Host header as follows:
GET /web-security HTTP/1.1
Host: google.com
I realized that changing the value of Host Header while doing password reset on vulnerable page will
result in getting a password reset link with modified domain value.
Which means that attacker can redirect the victim to malicious domain by controling the Host Header
value while doing password reset on victim, with prerequisite that victim click on the link. Since the
password reset link contains password reset token, attacker could achieve Account Takeover by
resetting the victim password.
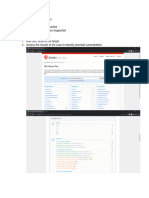
1. Browse to the vulnerable page: https://itp.tarc.edu.my/forgot-password
2. Insert the victim email (Must be valid user email), click SEND PASSWORD RESET LINK and intercept
the request with Burp suite:
3. Change the host header value with attacker controlled domain (You can use temporary hostname
provided by https://requestbin.com):
4. Send the request and you will receive a password reset link in victim email.
5. When clicking on the malicious password reset link, you are basically request to the malicious
domain with password reset token, attacker controlled domain will then receive the request and
obtain the password reset to achieve Account Takeover.
Additional Information
To make the malicious domain more alike and promising, attacker could register a domain that similar
to real TARC domain.
Supporting Materials
https://medium.com/@tameemkhalid786/host-header-injection-on-password-reset-functionality-an-
easy-p2-5c6263c2e3d4
https://hackerone.com/reports/226659
https://portswigger.net/web-security/host-header/exploiting/password-reset-poisoning
https://portswigger.net/web-security/host-header
Impact
Account Takeover
You might also like
- Defacing WebsiteDocument31 pagesDefacing WebsiteMAd BAdhNo ratings yet
- Api GuideDocument26 pagesApi GuideThiago MonteiroNo ratings yet
- PDFDocument28 pagesPDFAarati MahatoNo ratings yet
- Practical HTTP Host Header AttacksDocument5 pagesPractical HTTP Host Header AttacksSemeh ArbiNo ratings yet
- Unauthorized Url RedirectDocument5 pagesUnauthorized Url Redirectdonald adamasNo ratings yet
- Introduction To SSRFDocument9 pagesIntroduction To SSRFdawasov843No ratings yet
- Cross Site Requst FrogeryDocument8 pagesCross Site Requst Frogeryekrma dNo ratings yet
- Agenda: Date: 20/04/2021 Author: Sun Cyber Security ResearchDocument6 pagesAgenda: Date: 20/04/2021 Author: Sun Cyber Security ResearchNafiz NahiyanNo ratings yet
- Lesson 5: Web Based E Commerce Architecture: Topic: Uniform Resource LocatorDocument8 pagesLesson 5: Web Based E Commerce Architecture: Topic: Uniform Resource LocatorroselathikaNo ratings yet
- XSS in Joomla Acajoom ComponentDocument13 pagesXSS in Joomla Acajoom ComponentAlexandros SakellariouNo ratings yet
- Lab07 HTTPDocument4 pagesLab07 HTTPNMHHNo ratings yet
- Ignition Writeup: Introduction To NetworkingDocument11 pagesIgnition Writeup: Introduction To NetworkingMKNo ratings yet
- Unit2-2.1Handling Request HeadersDocument43 pagesUnit2-2.1Handling Request HeadersShweta JoshiNo ratings yet
- Browser Powered Desync AttacksDocument25 pagesBrowser Powered Desync AttacksKhang Tran DuyNo ratings yet
- Adding EmailDocument31 pagesAdding EmailhackerNo ratings yet
- Chapter 7WebSecurity8Apr2017Document17 pagesChapter 7WebSecurity8Apr2017Prima IntrusianoNo ratings yet
- Backstage API - Authentication and General API UsageDocument12 pagesBackstage API - Authentication and General API UsagekaraspideyNo ratings yet
- HTTP Status Code 2xx - SuccessDocument5 pagesHTTP Status Code 2xx - SuccessMichael CaninoNo ratings yet
- 13 Custom Auth ServerDocument9 pages13 Custom Auth ServervigneshNo ratings yet
- Demoblaze DataDocument10 pagesDemoblaze Datatraptanshparihar1No ratings yet
- Lab Exercise 1: Footprinting and Reconnaissance: Footprinting A Target NetworkDocument3 pagesLab Exercise 1: Footprinting and Reconnaissance: Footprinting A Target NetworkHamza KhalidNo ratings yet
- 47439Document3 pages47439abolfazl sheverinNo ratings yet
- Network Computing (Rt605) : Hyper Text Transfer ProtocolDocument19 pagesNetwork Computing (Rt605) : Hyper Text Transfer ProtocolHaritha BalakrishnanNo ratings yet
- API Developer Portal-Acquiring Your Access Token GuideDocument9 pagesAPI Developer Portal-Acquiring Your Access Token GuideLuca Ele Ale Stefi100% (1)
- Assignment No 4Document18 pagesAssignment No 4Jusil T. GaiteNo ratings yet
- OAuth2 in Python PDFDocument19 pagesOAuth2 in Python PDFJuan Pablo OrantesNo ratings yet
- Attacking Basic Auth With Burp Suiteâ (Session 1)Document24 pagesAttacking Basic Auth With Burp Suiteâ (Session 1)vifeneb962No ratings yet
- Tugas Networking BaruDocument3 pagesTugas Networking BaruArb LightNo ratings yet
- Thomas Musyoka Notes: Key Problem Factors in Web SecurityDocument4 pagesThomas Musyoka Notes: Key Problem Factors in Web SecurityThomas Musyoka PhilipNo ratings yet
- Magic UrlDocument15 pagesMagic Urlaurox3dNo ratings yet
- Bsides Hussein PresentationxDocument70 pagesBsides Hussein Presentationxxss100% (1)
- Lab CSRFDocument4 pagesLab CSRFgabhajayNo ratings yet
- Messages For HTML Pages, Images, Scripts and Styles Sheets. Web ServersDocument12 pagesMessages For HTML Pages, Images, Scripts and Styles Sheets. Web ServersDyrie Christine EcoNo ratings yet
- Solution: Wireshark Lab: HTTPDocument7 pagesSolution: Wireshark Lab: HTTPHaoTian YangNo ratings yet
- Whitepaper - DCE - OAuth2.0 ImplementationDocument9 pagesWhitepaper - DCE - OAuth2.0 ImplementationSowmya NagarajaNo ratings yet
- cs253 Final 2019 SolutionsDocument4 pagescs253 Final 2019 SolutionsfoosaaNo ratings yet
- Wireshark HTTP Lab.2Document1 pageWireshark HTTP Lab.2Miguel Angel Alvarado RamosNo ratings yet
- Detailed Documentation: Serving Widget As UserDocument6 pagesDetailed Documentation: Serving Widget As Usergetcall linkNo ratings yet
- Display Multiple Form and Tree View For Same ModelDocument18 pagesDisplay Multiple Form and Tree View For Same ModelIdris AstriNo ratings yet
- Book of Tips by Aditya Shende PDFDocument23 pagesBook of Tips by Aditya Shende PDFvenomNo ratings yet
- Web Security: Different Web Application Attacks Client Side AttackDocument9 pagesWeb Security: Different Web Application Attacks Client Side AttackZain Alabeeden AlarejiNo ratings yet
- Open Redirect BountiesDocument5 pagesOpen Redirect BountieṡNo ratings yet
- Internet Information Service (IIS)Document19 pagesInternet Information Service (IIS)thanhtin2109No ratings yet
- Updates To Facebook Login - Enforcing HTTPSDocument2 pagesUpdates To Facebook Login - Enforcing HTTPSjgh pjiojNo ratings yet
- Technical DetailsDocument6 pagesTechnical DetailsKafi AkbarNo ratings yet
- HTTP Authentication - HttpWatchDocument3 pagesHTTP Authentication - HttpWatchHector David ZenitNo ratings yet
- Cross-Site Request Forgery: Collin JacksonDocument31 pagesCross-Site Request Forgery: Collin JacksonAde Haryanto SagalaNo ratings yet
- WMS Experiment-1.3Document5 pagesWMS Experiment-1.3Kriti BharatNo ratings yet
- 2019-12-10 - Error - Page Request SmugglingDocument4 pages2019-12-10 - Error - Page Request SmugglingvishnuNo ratings yet
- Unit 3 CGI Using PERLDocument25 pagesUnit 3 CGI Using PERLumesh701No ratings yet
- 2 HTTP2Document104 pages2 HTTP2robinshrestha089No ratings yet
- 0752 HTTP Headers PDFDocument6 pages0752 HTTP Headers PDFHidayat HijaziNo ratings yet
- Source Code Disclosure Over HTTPDocument10 pagesSource Code Disclosure Over HTTPCiorcian CiorciNo ratings yet
- Cookies: COEN 351 E-Commerce SecurityDocument27 pagesCookies: COEN 351 E-Commerce SecurityShiva NethaNo ratings yet
- Session ManagementDocument23 pagesSession ManagementbrocktheboneNo ratings yet
- ProxiesDocument4 pagesProxiesMarc Rivera100% (1)
- Error CodesDocument15 pagesError Codesmani_ee231No ratings yet
- Vulnerability Report For Enlitech Web Application URL TestedDocument5 pagesVulnerability Report For Enlitech Web Application URL Testedtestm testerNo ratings yet
- Quick Guide for Creating Wordpress Websites, Creating EPUB E-books, and Overview of Some eFax, VOIP and SMS ServicesFrom EverandQuick Guide for Creating Wordpress Websites, Creating EPUB E-books, and Overview of Some eFax, VOIP and SMS ServicesNo ratings yet
- SS 2021 2022 PDFDocument3 pagesSS 2021 2022 PDF叶佩丽No ratings yet
- SS 2022 2023 PDFDocument2 pagesSS 2022 2023 PDF叶佩丽No ratings yet
- SS 2016 2017 Sept MidtermDocument3 pagesSS 2016 2017 Sept Midterm叶佩丽No ratings yet
- SS 2018 2019 Midterm SeptDocument2 pagesSS 2018 2019 Midterm Sept叶佩丽No ratings yet
- SS 2018 2019 Sept MidtermDocument2 pagesSS 2018 2019 Sept Midterm叶佩丽No ratings yet