Professional Documents
Culture Documents
Lab - 1 - Network Scanning
Uploaded by
kusum0 ratings0% found this document useful (0 votes)
43 views1 pageNetwork scanning attacks allow attackers to gather information about networked devices by discovering open ports and services. This lab uses Kali Linux to scan a vulnerable Metasploitable virtual machine (VM) in three steps: [1] Find the IP address prefix of the VM subnet; [2] Use Nmap to scan the subnet and identify the VM's specific IP address; [3] Use Nmap to detect open ports and running services on the VM.
Original Description:
lab
Original Title
Lab_1_Network Scanning
Copyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentNetwork scanning attacks allow attackers to gather information about networked devices by discovering open ports and services. This lab uses Kali Linux to scan a vulnerable Metasploitable virtual machine (VM) in three steps: [1] Find the IP address prefix of the VM subnet; [2] Use Nmap to scan the subnet and identify the VM's specific IP address; [3] Use Nmap to detect open ports and running services on the VM.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
43 views1 pageLab - 1 - Network Scanning
Uploaded by
kusumNetwork scanning attacks allow attackers to gather information about networked devices by discovering open ports and services. This lab uses Kali Linux to scan a vulnerable Metasploitable virtual machine (VM) in three steps: [1] Find the IP address prefix of the VM subnet; [2] Use Nmap to scan the subnet and identify the VM's specific IP address; [3] Use Nmap to detect open ports and running services on the VM.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
You are on page 1of 1
Lab 01: Network scanning attacks
Presentation:
The objective of this Lab is to learn how an attacker uses the network scanning attack as a
main step in the process of compromising and networked device.
Note: It should be noted that the reproduction of this approach on a company's site
without its approval is punishable by law.
Part 01: Scanning a vulnerable VM using Kali Linux.
In order to accomplish this lab, we will choose the VM Metasploitable, which is a good start
for this kind of exercise.
Tasks of part 01:
1. Download the Metasploitable VM
(https://sourceforge.net/projects/metasploitable/files/Metasploitable2/)
- The machine is made to be launched with Vmware. You can launch it with
VirtualBox by creating a new VM. At the step of choosing the disk, answer that
you have the disk and then show it the path to the Metasploitable disk.
Configure the only network card available in host-only then launch the machine.
- It is obvious that you do not have root access for this machine, that is the
purpose of the exercise. The goal is to find a vulnerability that allows us to have
the root without knowing the root password!
- You can also download a Kali Linux VM to avoid installing the tools necessary to
complete this exercise.
2. Find the VM IP address prefix: Scanning the four billion possible IPv4 addresses to
find the right IP address for your VM is out of the question. four billion possible IPv4
addresses to find the right IP address for your VM as this is both inefficient and
illegal.
- So how do you find the right network prefix to scan?
- In a real case, how can the attacker get this information?
- Give a name to this step.
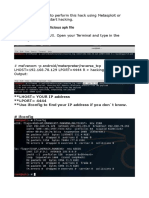
3. Find the IP address of the VM: Once you have found the right prefix, use the
network scan tool nmap network scan tool to identify the IP address of your VM.
- What type of scan is used by default? What are the differences between the the
different scan types available?
- How to make the scan stealthier and more discreet?
4. What services are running on this machine?
- What is this step called?
- How do you think this discovery works in practice?
You might also like
- Lab4 Instruction Part1Document9 pagesLab4 Instruction Part1Abdulrhman AlshameriNo ratings yet
- Lab Exercises - XFSC-7021-MC1 - Network Security Kali Linux - 49070 - OnlineDocument2 pagesLab Exercises - XFSC-7021-MC1 - Network Security Kali Linux - 49070 - Onlinegojan39660No ratings yet
- Experiment - 3: Advanced Cyber Security - 4028Document12 pagesExperiment - 3: Advanced Cyber Security - 4028JITESH SINGHNo ratings yet
- Lab 1 - Kali Linux, Network Scanning - Social EngineeringDocument5 pagesLab 1 - Kali Linux, Network Scanning - Social EngineeringH̸͟͞уυи HOON88No ratings yet
- Lab-M04-02 Team 6Document10 pagesLab-M04-02 Team 6api-377949857No ratings yet
- Lab 5 - Using The Nmap Scripting Engine (NSE) and Metasploit To Exploit Windows XPDocument9 pagesLab 5 - Using The Nmap Scripting Engine (NSE) and Metasploit To Exploit Windows XPLokesh Vaddi100% (1)
- Hunting For Vulnerabilities Using MetasploitDocument12 pagesHunting For Vulnerabilities Using MetasploitKshitiz GoyalNo ratings yet
- Lab 3: Scanning and Reconnaissance: CSC 5991 Cyber Security PracticeDocument13 pagesLab 3: Scanning and Reconnaissance: CSC 5991 Cyber Security PracticeNathaniel CrosleyNo ratings yet
- 3.3.3. LAB PRACTICE - MSF Hacking Windows10 Lab1 v1-1Document12 pages3.3.3. LAB PRACTICE - MSF Hacking Windows10 Lab1 v1-1CONTACTS CONTACTSNo ratings yet
- CAEForum21 Fu Armitage 1Document36 pagesCAEForum21 Fu Armitage 1cyrus mwangiNo ratings yet
- Lab 19 MetasploitDocument11 pagesLab 19 Metasploitoscar tebar100% (1)
- Step 1: Creating A Malicious Apk FileDocument4 pagesStep 1: Creating A Malicious Apk FileANUJ HUNDIANo ratings yet
- Lab+ +Hacking+Windows+XP+via+MS11 006+Windows+Shell+Graphics+Processing+Document13 pagesLab+ +Hacking+Windows+XP+via+MS11 006+Windows+Shell+Graphics+Processing+Mohcine OubadiNo ratings yet
- Lab - Isolated Compromised Host Using 5-TupleDocument33 pagesLab - Isolated Compromised Host Using 5-TupleSlaimi RaniaNo ratings yet
- Easy ModeDocument9 pagesEasy Modemindhackers161No ratings yet
- Ethical Hacking Course - Practice 2 - How To Recognize A GoalDocument27 pagesEthical Hacking Course - Practice 2 - How To Recognize A GoalVandhana PramodhanNo ratings yet
- Ethical Hacking LABDocument27 pagesEthical Hacking LABVandhana PramodhanNo ratings yet
- Keep Calm and Hack The BoxDocument24 pagesKeep Calm and Hack The Boxnana100% (1)
- Ethical Hacking Project WorkDocument16 pagesEthical Hacking Project Workravi tejaNo ratings yet
- Kioptrix 1 MachineDocument11 pagesKioptrix 1 MachineRUCHI KUMARINo ratings yet
- Lab - Exploring Endpoint Attacks: RequirementsDocument16 pagesLab - Exploring Endpoint Attacks: RequirementsMohcine OubadiNo ratings yet
- Lab 8 - Gaining Access of Metasploitable Machine Using Metasploit FrameworkDocument1 pageLab 8 - Gaining Access of Metasploitable Machine Using Metasploit FrameworkPratham PandeyNo ratings yet
- CS 502Document46 pagesCS 502Ur MnNo ratings yet
- CEH GuidelinesDocument66 pagesCEH GuidelinesEurico da SilvaNo ratings yet
- Lab 4: Metasploit Framework: CSC 4992 Cyber Security PracticeDocument22 pagesLab 4: Metasploit Framework: CSC 4992 Cyber Security Practiceleyowof787No ratings yet
- Laboratory Setup: Step 1: Download Metasploitable, Which Is A Linux Machine. It Can Be Downloaded FromDocument13 pagesLaboratory Setup: Step 1: Download Metasploitable, Which Is A Linux Machine. It Can Be Downloaded FromTajria SultanaNo ratings yet
- Lab4 Instruction PDFDocument22 pagesLab4 Instruction PDFTester MaheNo ratings yet
- Network Security Lab Manual DraftDocument29 pagesNetwork Security Lab Manual DraftShraddha PatilNo ratings yet
- Lab 2 - StudentDocument7 pagesLab 2 - StudentsalwaNo ratings yet
- Attacking Metasploitable2 VM Server Cameron WDocument20 pagesAttacking Metasploitable2 VM Server Cameron Wapi-502019278No ratings yet
- Lab 8 - Configuring Site-To-Site VPN Using CLIDocument9 pagesLab 8 - Configuring Site-To-Site VPN Using CLIlee leeNo ratings yet
- Security & Ethical Hacking p2Document29 pagesSecurity & Ethical Hacking p2Vipin NarangNo ratings yet
- Pentest Lab Setup: WWW - Uat.eduDocument8 pagesPentest Lab Setup: WWW - Uat.eduapi-549068032No ratings yet
- Metasploit BackdoorDocument3 pagesMetasploit BackdoorAreefNo ratings yet
- How Hackers Use Your IP Address To Hack Your Computer & How To Stop It Null ByteDocument6 pagesHow Hackers Use Your IP Address To Hack Your Computer & How To Stop It Null ByteChasiful AnwarNo ratings yet
- Nmap Explication and Basic Arguments: Author: - Bad - BoyDocument7 pagesNmap Explication and Basic Arguments: Author: - Bad - BoySivi KarudijanNo ratings yet
- Metasploitable Exploits and Hardening GuideDocument10 pagesMetasploitable Exploits and Hardening GuideelmaestrosbokNo ratings yet
- CS443 ProjectDocument1 pageCS443 ProjectAbdulrhman AlshameriNo ratings yet
- My Linux Attack Commands-ADocument51 pagesMy Linux Attack Commands-Aapogee.protectionNo ratings yet
- 6.system HackingDocument50 pages6.system Hackingcafenight2547No ratings yet
- Penetration Testing ReportDocument25 pagesPenetration Testing Reportmatifj4n0987No ratings yet
- Ethical Hacking Attacks Using Kali LinuxDocument24 pagesEthical Hacking Attacks Using Kali Linuxmindhackers161No ratings yet
- Vulnarability Scan With NMAP & Intrusion Attacks With and MetasploitDocument17 pagesVulnarability Scan With NMAP & Intrusion Attacks With and MetasploitRania BenamaraNo ratings yet
- 2 Footprinting and ReconnaissanceDocument152 pages2 Footprinting and Reconnaissanceshiva kumarNo ratings yet
- Kali Linuxg Cookbook Books - pdf-1Document5 pagesKali Linuxg Cookbook Books - pdf-1Vijay VijjuNo ratings yet
- VAPT Mooc Course NotesDocument10 pagesVAPT Mooc Course NotesFatema TahaNo ratings yet
- Lab+ +Password+Cracking+Using+MimikatzDocument8 pagesLab+ +Password+Cracking+Using+MimikatzMohcine OubadiNo ratings yet
- Cracking Linux Passwords and Pentesting With Grep2Document17 pagesCracking Linux Passwords and Pentesting With Grep2kashif majeed janjuaNo ratings yet
- AIA Final Exam NotesDocument4 pagesAIA Final Exam NotesViraj Dissanayake100% (1)
- Wifi Password CrackingDocument13 pagesWifi Password CrackingAyeah GodloveNo ratings yet
- Blackhat PDFDocument70 pagesBlackhat PDFPablo ZambranoNo ratings yet
- CTF - DC1 - Lab FileDocument11 pagesCTF - DC1 - Lab Filecyber mediaNo ratings yet
- Vulscan 2Document4 pagesVulscan 2mindhackers161No ratings yet
- 04 - Useful ToolsDocument24 pages04 - Useful ToolsMatheus Biagini PereiraNo ratings yet
- Praktikum Ethical HackingDocument144 pagesPraktikum Ethical HackingKido KaindeNo ratings yet
- Backtrack Tutorial PDF STDDocument46 pagesBacktrack Tutorial PDF STDCésar Paz100% (1)
- Footprinting, Reconnaissance, Scanning and Enumeration Techniques of Computer NetworksFrom EverandFootprinting, Reconnaissance, Scanning and Enumeration Techniques of Computer NetworksNo ratings yet
- ETHICAL HACKING GUIDE-Part 2: Comprehensive Guide to Ethical Hacking worldFrom EverandETHICAL HACKING GUIDE-Part 2: Comprehensive Guide to Ethical Hacking worldNo ratings yet