Practical DAY 2
1. PING sweep. Run a TCP Netcat port scan on ports 3000-4000. The -w option specifies the
connection timeout in seconds and -z is used to specify zero-I/O mode, which will send no data
and is used for scanning:
nc -nvv -w 1 -z TARGETIP 3000-4000
2. Run a UDP Netcat port scan against ports 1-1000. This is done using the -u switch which
indicates a UDP scan:
nc -nv -u -z -w 1 TARGETIP 1-1000
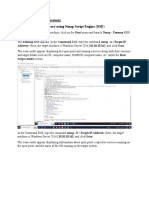
3. NMAP Host discovery
a) Before we start running scans blindly, let’s examine the amount of traffic sent by this type
of scan. We’ll scan one of the lab machines while monitoring the amount of traffic sent
to the target host using iptables. We will use several iptables options. First, we will use
the -I option to insert a new rule into a given chain, which in this case includes both the
INPUT (Inbound) and OUTPUT (Outbound) chains followed by the rule number. We will
use -s to specify a source IP address, -d to specify a destination IP address, and -j to
ACCEPT the traffic. Lastly, we will use the -Z option to zero the packet and byte counters
in all chains.
sudo iptables -I INPUT 1 -s TARGETIP -j ACCEPT
sudo iptables -I OUTPUT 1 -d TARGETIP -j ACCEPT
sudo iptables -Z
nmap TARGETIP
sudo iptables -vn -L
sudo iptables -Z
nmap -p 1-65535 TARGETIP
b) Stealth / SYN Scanning
Nmap’s preferred scanning technique is a SYN, or “stealth” scan. Execute the scan and check the
results
nmap -sS TARGETIP
c) TCP Connect Scanning
When a user running nmap does not have raw socket privileges, Nmap will default to the TCP
connect scan. We can use the -sT option to start a connect scan:
nmap -sT TARGETIP
d) When performing a UDP scan, Nmap will use a combination of two different methods to
determine if a port is open or closed. For most ports, it will use the standard “ICMP port
� unreachable” and for some common ports, such as port 161, which is used by SNMP, it will send
a protocol-specific SNMP packet in an attempt to get a response from an application bound to
that port. To perform a UDP scan, the -sU option is used and sudo is required to access raw
sockets:
sudo nmap -sU TARGETIP
e) Nmap Scripting Engine (NSE)
We can use the Nmap Scripting Engine (NSE)206 to launch user-created scripts in order to
automate various scanning tasks. These scripts perform a broad range of functions including DNS
enumeration, brute force attacks, and even vulnerability identification. NSE scripts are located in
the /usr/share/nmap/scripts directory.
Lets test the smb-os-discovery script attempts to connect to the SMB service on a target and
determine its operating system:
nmap TARGETIP --script=smb-os-discovery
f) Now try NSE script and perform dns-zone-transfer:
nmap --script=dns-zone-transfer -p 53 ns2.megacorpone.com
4. Vulnerability Scanning with Nmap
As an alternative to Nessus, we can also use the Nmap Scripting Engine (NSE)235 to perform
automated vulnerability scans. While NSE is not a full-fledged vulnerability scanner, it does have a
respectable library of scripts that can be used to detect and validate vulnerabilities. NSE scripts are
written in LUA and range in functionality from brute force and authentication to detecting and
exploiting vulnerabilities. For these purposes we will focus on the scripts in the “vuln” and “exploit”
categories, as the former detects a vulnerability and the latter attempts to exploit it.
However, there is overlap between these categories and some “vuln” scripts may essentially run
stripped-down exploits. For this reason, scripts are also further categorized as “safe” or “intrusive”
and we should take great care when executing the latter because they may crash a remote service
or take down the target.
On Kali, the NSE scripts can be found in the /usr/share/nmap/scripts/ directory. Opening any of the
*.nse files in a text editor shows the source of each script in a simple human-readable format.
This folder also contains a script.db file that serves as an index to all of the scripts.
a) Use nmap with --script vuln option to run all scripts in the “vuln” category against 2 target
VMs you have for the lab. Save the report with the results and compare to what you found
previously using Nessus.
b) Find an NSE script similar to the NFS Exported Share Information Disclosure that was
executed in the “Scanning with Individual Nessus Plugins” section. Once found, run the script
against the same targets. Describe the results.