Professional Documents
Culture Documents
Picus Battle Card February 2022
Uploaded by
Halil DemirCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Picus Battle Card February 2022
Uploaded by
Halil DemirCopyright:
Available Formats
Battlecard February 2022 v.
Company Overview The Picus Platform The Picus Platform (cont.)
Picus Security is the pioneer of Breach and Attack Simulation, a security Continuous Security Control Validation & Mitigation The Picus platform is offered as an annual subscription and priced
control validation methodology coalescing offensive (red team) and according to the number modules.
By simulating over 10k threats and attack scenarios, the Picus platform
defensive (blue team) security approaches. enables security teams to continuously test the effectiveness of security
Security controls which can be assessed include: Firewalls, IPSs, Web
controls across threat prevention and detection layers.
• Founded by industry veterans in 2013 Application Firewalls, Web Proxies, Mail and End Point Security.
• Offers the most complete Breach and Attack Simulation platform • Identify security weaknesses and visibility blind spots Using the threat library Picus can run an attack simulation (red team
• Global partner network in 20+ countries • Validate the effectiveness of controls and processes attack) and demonstrate the security efficacy of a client’s existing
• Offices in London, San Francisco, Milan, Dubai, Istanbul • Obtain a continuous view of an organisation’s security posture security controls. As part of its Blue Team module, Picus can then mitigate
• Recognised by industry thought leaders – Gartner Cool Vendor 2019, • Address exposures with prevention signatures and detection rules the attacks through integrations (via API) into these security controls.
Frost & Sullivan Leading BAS Vendor 2020 Picus has integrations with Palo Alto, Fortinet, Check Point, McAfee, F5,
• Track security scores and measure the impact of changes
Cisco, Splunk, IBM Q-Radar, Carbon Black, amongst others.
• Backed by credible investors – completed Series b $24m in Oct 2021
Customer Challenges
To minimise the risk of suffering data breaches and resultant financial
and reputational damage, all organisations need to ensure they have
suitable controls in place to continuously protect their data and assets.
This involves not just preventing threats but swiftly detecting and
responding to ones that are able to bypass defences.
However, ensuring a robust security posture at all times is increasingly
challenging. Common issues faced by security teams include:
• Keeping up with the rapidly evolving threat landscape. Indeed, 80% of
organisations are not confident that they are prepared to face major
cyberattacks
• Protecting a growing attack surface, including cloud workloads and
endpoints used by remote workers
• Managing, maintaining and monitoring multiple disparate security
tools, 24/7 – keeping them updated and configured correctly
• Obtaining a clear view of an organisation’s security posture at all times
and reporting accurate status to the board
Battlecard February 2022 v.1
Customer Benefits Customer Targets Sales Qualification Questions
Lower Risk Most Successful Verticals • Does your company have plans to deploy breach and attack simulation
• Swiftly identify and respond to changes technology?
• Enhance threat coverage • Finance, Banking & Insurance • Do you continually test your security controls using known attacker tools
• Avoid visibility blindspots • Manufacturing and methodologies?
• Improve mean time to detect and respond • Retails • How sure are you that your defences can block the latest threats?
• Telecommunications • How would you rate your company’s security resilience to ransomware?
Improve Productivity • Transport/Automotive • How effective are your current testing methodologies in identifying
• Reduce manual processes • Pharmaceutical misconfigured security controls?
• Improve SOC efficiency • Public Sector – Central Government and Universities • How effective is your current SIEM/SOC in alerting and detecting?
• Prioritise mitigation
Save Money Use Cases Objection Handling
• Rationalise investments
• Sweat your assets further Picus can be used for a variety of use cases and projects: How does Picus differ from vulnerability management?
• Justify spending decisions Vulnerability management tools are great solutions but with no
• Continuous security validation specific focus on adversarial techniques and behaviours. The Picus
• Reducing exposure to new cyber attacks BAS solution validates the readiness of all prevention and defence
Picus Customer Persona layers from people, process and technology angles against
• Rationalising cybersecurity investments through security validation
• Optimising SIEM and EDR threat detection capabilities sophisticated cyber threats and provides the agility required to
Picus clients typically have the following profile: address cyber attacks.
• Enabling compliance
• 1,000-10,000 users • Pre-acquisition assessments We may consider using Picus after completing our main security
• Medium to good security maturity • Post-acquisition performance improvements investments such as WAF etc Please get in touch with us later.
• Assessing new controls before purchase It is strongly recommended that companies assess their existing
• NGFW, IPS, WAF investments already in place
defensive capabilities and shortcomings before committing to new
• SOC/SIEM is a plus as we add huge value and differentiation with cyber security investments. Threat-centric validation provides
Detection Analytics Door Opening Strategies invaluable insights for planning security investments with the right
• Common characteristics priorities.
• Short of staff Compliment Pen Testing - Supplement focused pen testing with a
• Trying to keep up with day-to-day operations broader, automated approach. Our team are already busy. We do not want to buy yet another tool.
• Moderate compliance requirements Based on surveys on different customer environments, Picus’ Customer
Replace Red Teaming - Use Picus’ solution to automate purple teaming Success Team found that Picus can increase efficiency by as much as
• Hybrid environments exercises, replacing expensive manual red teams 300%.
Investment Validation - Use Picus reporting function of Security We do not have the resources to take corrective action against Picus
Control Validation to evidence success of security investment continuous mitigation output.
Picus’ rich threat library, easy-to-use UI and mitigation and reporting
SOC/SIEM Optimisation - Use Picus Detection Analytics technology to content enables junior security team members as well as IT personnel with
extend the value of their current investment no security background to take corrective actions swiftly and confidently.
You might also like
- Calculate, Communicate and Compare Your Cyber Exposure Key BenefitsDocument2 pagesCalculate, Communicate and Compare Your Cyber Exposure Key BenefitsSantiago HuilcamaiguaNo ratings yet
- Market Guide For Managed Detection and Response ServicesDocument16 pagesMarket Guide For Managed Detection and Response Services123123123123123124215235No ratings yet
- GigamonDocument52 pagesGigamonsathiaseelans5356No ratings yet
- FY23 CEE GTM Enablement Playbook - Partner ReadyDocument18 pagesFY23 CEE GTM Enablement Playbook - Partner ReadySaurabh SaxenaNo ratings yet
- Breach and Attack SimulationsDocument11 pagesBreach and Attack SimulationsRama RaymondNo ratings yet
- IBM Security Systems Solutions For BankingDocument37 pagesIBM Security Systems Solutions For Bankingstriker0074No ratings yet
- Bringing Finops To Life Through Organizational and Cultural AlignmentDocument20 pagesBringing Finops To Life Through Organizational and Cultural AlignmentshovalNo ratings yet
- Refinitiv WC BrochureDocument12 pagesRefinitiv WC BrochurejimmiilongNo ratings yet
- Layers of Protection: Evolving Nature of Cyber-Threats in Payment SystemsDocument12 pagesLayers of Protection: Evolving Nature of Cyber-Threats in Payment SystemsWilfred DsouzaNo ratings yet
- Tidal Finance Smart Contract Audit SummaryDocument41 pagesTidal Finance Smart Contract Audit SummaryvuongtranvnNo ratings yet
- LAB HANDOUT - Tenable - SC Specialist CourseDocument113 pagesLAB HANDOUT - Tenable - SC Specialist Coursenet flixNo ratings yet
- Apptio Pilot Outcomes V1.1Document1 pageApptio Pilot Outcomes V1.1Lucy RickardNo ratings yet
- 1.01 - Guardium Data Protection OverviewDocument20 pages1.01 - Guardium Data Protection OverviewishtiaqNo ratings yet
- The Definitive Guide To Data ClassificationDocument38 pagesThe Definitive Guide To Data ClassificationTeddy SukardiNo ratings yet
- GNS3 - Creating The Simplest TopologyDocument18 pagesGNS3 - Creating The Simplest Topologyclu5t3rNo ratings yet
- LogRhythm Software Install Guide 7.8.0 RevADocument105 pagesLogRhythm Software Install Guide 7.8.0 RevAtaha deghiesNo ratings yet
- Modern Vulnerability Management Key Benefits: Eliminate Blind SpotsDocument2 pagesModern Vulnerability Management Key Benefits: Eliminate Blind SpotsSantiago HuilcamaiguaNo ratings yet
- OctoboxDocument11 pagesOctoboxSatadal GuptaNo ratings yet
- Tenablesc UserGuideDocument665 pagesTenablesc UserGuideLucas RealNo ratings yet
- Future Telco 2014 enDocument324 pagesFuture Telco 2014 enVladimir PodshivalovNo ratings yet
- Tenable Automates NIST Cybersecurity Framework Technical Controls - Tenable Network SecurityDocument3 pagesTenable Automates NIST Cybersecurity Framework Technical Controls - Tenable Network SecuritybsomaNo ratings yet
- SecurityCenter 5.0 InstallationDocument27 pagesSecurityCenter 5.0 Installationjosu_rcNo ratings yet
- Cloud Computing Security IssuesDocument23 pagesCloud Computing Security IssuesAdarsh Varma100% (1)
- Illumio Adaptive Security For NutanixDocument3 pagesIllumio Adaptive Security For NutanixGopi ChowdaryNo ratings yet
- NetopsDocument81 pagesNetopsAshrafur RahmanNo ratings yet
- Nessus 8 7 PDFDocument446 pagesNessus 8 7 PDFNaresh AvulaNo ratings yet
- ACS Recognition of Prior Learning (RPL) FormDocument6 pagesACS Recognition of Prior Learning (RPL) Formpatel6742No ratings yet
- Gartner SOAR 2019Document17 pagesGartner SOAR 2019Oscar Gopro SEISNo ratings yet
- Gartner Market Guide For Security Orchestration, AutomationDocument16 pagesGartner Market Guide For Security Orchestration, AutomationpippoNo ratings yet
- Crowdstrike 2019 Overwatch ReportDocument61 pagesCrowdstrike 2019 Overwatch ReportRittickNo ratings yet
- Dell Secureworks - Accelerating Incident Response MssirtiDocument13 pagesDell Secureworks - Accelerating Incident Response MssirtiVizay KotikalapudiNo ratings yet
- The Complete Guide to Data Security: Protect Sensitive Data at Rest, in Use and in TransitDocument22 pagesThe Complete Guide to Data Security: Protect Sensitive Data at Rest, in Use and in TransitJohan Prevot RNo ratings yet
- Gartner Siem FailuresDocument10 pagesGartner Siem FailuresTaha KhanNo ratings yet
- Module 2 Existing Threat Modeling Approaches (COMPLETE)Document68 pagesModule 2 Existing Threat Modeling Approaches (COMPLETE)KESTREL KELLNER CERVANTESNo ratings yet
- Mosaic One: Promote Operate CareDocument3 pagesMosaic One: Promote Operate CareNipun SahniNo ratings yet
- Zscaler Private Access: Fast, Secure Access To Private Applications With Cloud-Delivered Zero Trust Network Access (ZTNA)Document4 pagesZscaler Private Access: Fast, Secure Access To Private Applications With Cloud-Delivered Zero Trust Network Access (ZTNA)Katie AdamsNo ratings yet
- SC 103 Endpoint and Intercept X Sales Overview v2.0.0Document19 pagesSC 103 Endpoint and Intercept X Sales Overview v2.0.0Anderson Traslaviña AlvarezNo ratings yet
- SaaS FinOps Maturity Model - ChargebeeDocument19 pagesSaaS FinOps Maturity Model - ChargebeeJoão DobbinNo ratings yet
- The Ten Most Critical API Security RisksDocument31 pagesThe Ten Most Critical API Security RisksnehaNo ratings yet
- Rsa Securid Access Rsa Securid Authentication API Developers GuideDocument43 pagesRsa Securid Access Rsa Securid Authentication API Developers GuideJohny JiménezNo ratings yet
- EDR (Endpoint Detection and Response) Report From PeerSpot 2023-06-03 18qyDocument41 pagesEDR (Endpoint Detection and Response) Report From PeerSpot 2023-06-03 18qyJosue HernandezNo ratings yet
- Tenable Csis Compliance WhitepaperDocument22 pagesTenable Csis Compliance Whitepapernaushad73No ratings yet
- GPRS Radio Parameters GuideDocument70 pagesGPRS Radio Parameters GuidePuneet YadavNo ratings yet
- Amdocs Actix Analyzer 5G NSA NR Datasheet 2020Document3 pagesAmdocs Actix Analyzer 5G NSA NR Datasheet 2020Alexandre AyehNo ratings yet
- Tenable SC For Cyber ArkDocument23 pagesTenable SC For Cyber ArkRajesh Annamareddi ChoudariNo ratings yet
- OWASP API Security Top 10 (2019)Document31 pagesOWASP API Security Top 10 (2019)socialspiderNo ratings yet
- Network As A Service (Naas) Data Analysis, Business, and Operational Efficiency MethodologyDocument33 pagesNetwork As A Service (Naas) Data Analysis, Business, and Operational Efficiency MethodologyCarlosRivasNo ratings yet
- Top Use CasesDocument55 pagesTop Use CasesToan NguyenNo ratings yet
- Guide to the Evolving Threat LandscapeDocument35 pagesGuide to the Evolving Threat LandscapeAnonymous yPkSRRrNo ratings yet
- Inventory Management (SRAN16.1 - 01)Document20 pagesInventory Management (SRAN16.1 - 01)Didier SepulvedaNo ratings yet
- OWASP TopnDocument1 pageOWASP TopnMilanNo ratings yet
- Liquid Staking ReportDocument88 pagesLiquid Staking ReportUme GozieNo ratings yet
- Gartner Market Share Analysis - Security Consulting, Worldwide, 2012Document9 pagesGartner Market Share Analysis - Security Consulting, Worldwide, 2012Othon CabreraNo ratings yet
- Home About Service Resources: Articles Academia Glossary Book List LinksDocument14 pagesHome About Service Resources: Articles Academia Glossary Book List Linkslarry HNo ratings yet
- 3G Security OverviewDocument21 pages3G Security Overviewmohan542100% (1)
- 02-Mentor Client Network Analysis ToolsDocument47 pages02-Mentor Client Network Analysis ToolsMuoi NguyenNo ratings yet
- PCI For DummiesDocument68 pagesPCI For DummiessrujanNo ratings yet
- Intrusion Tests - Red Team: There Are Two Kinds of People: Those Who Know They Have Experienced A Cyber-Attack and YouDocument2 pagesIntrusion Tests - Red Team: There Are Two Kinds of People: Those Who Know They Have Experienced A Cyber-Attack and YouNazire EricNo ratings yet
- Cisco Technical Security Assessment AagDocument3 pagesCisco Technical Security Assessment Aaglakbabi1035No ratings yet
- CYBER SECURITY HANDBOOK Part-2: Lock, Stock, and Cyber: A Comprehensive Security HandbookFrom EverandCYBER SECURITY HANDBOOK Part-2: Lock, Stock, and Cyber: A Comprehensive Security HandbookNo ratings yet
- Iso 27002 Information SecurityDocument4 pagesIso 27002 Information SecurityNorah Al-ShamriNo ratings yet
- Bitdefender EndpointSecurityToolsForWindows UsersGuide EnUSDocument50 pagesBitdefender EndpointSecurityToolsForWindows UsersGuide EnUSIrina NastasescuNo ratings yet
- Waples, Gill, and Fisher - Does CCTV Displace Crime PDFDocument19 pagesWaples, Gill, and Fisher - Does CCTV Displace Crime PDFMiguel Luigi CalayagNo ratings yet
- RajanDocument3 pagesRajanvijetameenaNo ratings yet
- Quantum CryptographyDocument7 pagesQuantum Cryptographyvidhya_bineeshNo ratings yet
- Network Security-Virus Attacks and Defence Using Antivirus SoftwareDocument3 pagesNetwork Security-Virus Attacks and Defence Using Antivirus SoftwareAhsan SakheeNo ratings yet
- User PHPDocument2 pagesUser PHPVansh RanaNo ratings yet
- UntitledDocument13 pagesUntitledSMPIT Harum BrebesNo ratings yet
- ABC Technologies - Case StudyDocument15 pagesABC Technologies - Case StudyNitin PandeyNo ratings yet
- Authshield Lab-2 Factor Authentication SolutionsDocument31 pagesAuthshield Lab-2 Factor Authentication SolutionsAuthShield LabNo ratings yet
- The Why and How of Adopting Zero Trust Model in OrganizationsDocument6 pagesThe Why and How of Adopting Zero Trust Model in OrganizationsBaloch Lens PhotographerNo ratings yet
- Guide For Salesforce AdminSuperSetDocument4 pagesGuide For Salesforce AdminSuperSetpradeepNo ratings yet
- Blog On Cyber LawDocument7 pagesBlog On Cyber Lawkumarpreet003No ratings yet
- PoS V2Document6 pagesPoS V2rajeevrocksNo ratings yet
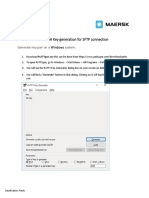
- Generate SSH keys Windows PuTTYDocument7 pagesGenerate SSH keys Windows PuTTYIsaiSin20No ratings yet
- Ethical Hacking CourseDocument22 pagesEthical Hacking CourseDeviLNo ratings yet
- 6.2.1.11 Lab - Anatomy of MalwareDocument1 page6.2.1.11 Lab - Anatomy of MalwareMelissa Fisk50% (2)
- Man in The Middle AttackDocument7 pagesMan in The Middle AttackYusuph Kileo100% (1)
- M3u Playlist 2022Document9 pagesM3u Playlist 2022Carlos DanelonNo ratings yet
- Ch08 Securing Information SystemsDocument43 pagesCh08 Securing Information SystemsPatrickNo ratings yet
- Vtu Network Security (10ec832) Unit-7 Notes.Document10 pagesVtu Network Security (10ec832) Unit-7 Notes.jayanthdwijesh h pNo ratings yet
- Incident Response Playbooks 1687937708Document21 pagesIncident Response Playbooks 1687937708macNo ratings yet
- Research Paper On Cyber Security 2020Document2 pagesResearch Paper On Cyber Security 2020JohnNo ratings yet
- 22SCE151Cryptography and Network SecurityDocument3 pages22SCE151Cryptography and Network SecuritytnagaviNo ratings yet
- 1.4 Phishing Attacks: Allegro - Worksheet 10Document7 pages1.4 Phishing Attacks: Allegro - Worksheet 10Wanderer Soul100% (2)
- Access Control Policy: TechnicalDocument6 pagesAccess Control Policy: TechnicalaalmotaaNo ratings yet
- Encryption and Hashing: Presented by Fatma HAMOUDADocument18 pagesEncryption and Hashing: Presented by Fatma HAMOUDADamak SanaNo ratings yet
- Three Level Password AuthenticationDocument7 pagesThree Level Password AuthenticationMoses KabeteNo ratings yet
- Security ClassworkDocument2 pagesSecurity ClassworkEavdiuNo ratings yet
- cl0p Lockbit New Data Breaches Sector AlertDocument5 pagescl0p Lockbit New Data Breaches Sector AlertSuek BanaNo ratings yet