Professional Documents
Culture Documents
Login and Writer
Uploaded by
Ravi GiriOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Login and Writer
Uploaded by
Ravi GiriCopyright:
Available Formats
Login
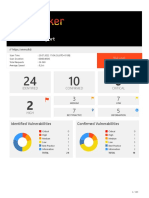
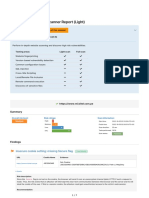
Summary
The table below shows the numbers of issues identified in different categories. Issues are classified according to severity as High, Medium, Low, Information or
False Positive. This reflects the likely impact of each issue for a typical organization. Issues are also classified according to confidence as Certain, Firm or Tentative.
This reflects the inherent reliability of the technique that was used to identify the issue.
Confidence
Certain Firm Tentative Total
High 0 0 0 0
Medium 0 0 0 0
Severity Low 2 0 0 2
Information 5 6 0 11
False Positive 0 0 0 0
The chart below shows the aggregated numbers of issues identified in each category. Solid colored bars represent issues with a confidence level of Certain, and the
bars fade as the confidence level falls.
Number of issues
0 2 4 6 8 10
High
Severity Medium
Low
Contents
1. Strict transport security not enforced
1.1. https://qa-cms.republicworld.com/dashboard/writer/
1.2. https://qa-cms.republicworld.com/login/
2. Frameable response (potential Clickjacking)
2.1. https://qa-cms.republicworld.com/dashboard/writer/
2.2. https://qa-cms.republicworld.com/login/
3. DOM data manipulation (DOM-based)
3.1. https://qa-cms.republicworld.com/dashboard/writer/
3.2. https://qa-cms.republicworld.com/dashboard/writer/
3.3. https://qa-cms.republicworld.com/login/
3.4. https://qa-cms.republicworld.com/login/
4. Backup file
4.1. https://qa-cms.republicworld.com/dashboard/writer~
4.2. https://qa-cms.republicworld.com/login~
5. Cacheable HTTPS response
5.1. https://qa-cms.republicworld.com/dashboard/writer/
5.2. https://qa-cms.republicworld.com/login/
6. TLS certificate
1. Strict transport security not enforced
Next
There are 2 instances of this issue:
/dashboard/writer/
/login/
Issue description
The application fails to prevent users from connecting to it over unencrypted connections. An attacker able to modify a legitimate user's network traffic could bypass
the application's use of SSL/TLS encryption, and use the application as a platform for attacks against its users. This attack is performed by rewriting HTTPS links as
HTTP, so that if a targeted user follows a link to the site from an HTTP page, their browser never attempts to use an encrypted connection. The sslstrip tool
automates this process.
To exploit this vulnerability, an attacker must be suitably positioned to intercept and modify the victim's network traffic.This scenario typically occurs when a client
communicates with the server over an insecure connection such as public Wi-Fi, or a corporate or home network that is shared with a compromised computer.
Common defenses such as switched networks are not sufficient to prevent this. An attacker situated in the user's ISP or the application's hosting infrastructure could
also perform this attack. Note that an advanced adversary could potentially target any connection made over the Internet's core infrastructure.
Issue remediation
The application should instruct web browsers to only access the application using HTTPS. To do this, enable HTTP Strict Transport Security (HSTS) by adding a
response header with the name 'Strict-Transport-Security' and the value 'max-age=expireTime', where expireTime is the time in seconds that browsers should
remember that the site should only be accessed using HTTPS. Consider adding the 'includeSubDomains' flag if appropriate.
Note that because HSTS is a "trust on first use" (TOFU) protocol, a user who has never accessed the application will never have seen the HSTS header, and will
therefore still be vulnerable to SSL stripping attacks. To mitigate this risk, you can optionally add the 'preload' flag to the HSTS header, and submit the domain for
review by browser vendors.
References
HTTP Strict Transport Security
sslstrip
HSTS Preload Form
Vulnerability classifications
CWE-523: Unprotected Transport of Credentials
CAPEC-94: Man in the Middle Attack
CAPEC-157: Sniffing Attacks
1.1. https://qa-cms.republicworld.com/dashboard/writer/
Next
Summary
Severity: Low
Confidence: Certain
Host: https://qa-cms.republicworld.com
Path: /dashboard/writer/
Request
GET /dashboard/writer/ HTTP/1.1
Host: qa-cms.republicworld.com
Accept-Encoding: gzip, deflate
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.5845.111 Safari/537.36
Connection: close
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Sec-CH-UA: ".Not/A)Brand";v="99", "Google Chrome";v="116", "Chromium";v="116"
Sec-CH-UA-Platform: Windows
Sec-CH-UA-Mobile: ?0
Response
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Mon, 28 Aug 2023 10:07:10 GMT
Content-Type: text/html; charset=utf-8
Connection: close
X-Powered-By: Next.js
ETag: "luov05329geli"
Vary: Accept-Encoding
Content-Length: 18918
<!DOCTYPE html><html lang="en"><head><meta charSet="utf-8"/><title>Republic Digital</title><meta name="description" content="Republic Digital"/><meta
name="keywords" content=""/><meta name="viewport"
...[SNIP]...
1.2. https://qa-cms.republicworld.com/login/
Previous Next
Summary
Severity: Low
Confidence: Certain
Host: https://qa-cms.republicworld.com
Path: /login/
Request
GET /login/ HTTP/1.1
Host: qa-cms.republicworld.com
Accept-Encoding: gzip, deflate
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.5845.111 Safari/537.36
Connection: close
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Sec-CH-UA: ".Not/A)Brand";v="99", "Google Chrome";v="116", "Chromium";v="116"
Sec-CH-UA-Platform: Windows
Sec-CH-UA-Mobile: ?0
Response
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Mon, 28 Aug 2023 11:27:11 GMT
Content-Type: text/html; charset=utf-8
Connection: close
X-Powered-By: Next.js
ETag: "152mete46jce1b"
Vary: Accept-Encoding
Content-Length: 18191
<!DOCTYPE html><html lang="en"><head><meta charSet="utf-8"/><title>Republic Digital</title><meta name="description" content="Republic Digital"/><meta
name="keywords" content=""/><meta name="viewport"
...[SNIP]...
2. Frameable response (potential Clickjacking)
Previous Next
There are 2 instances of this issue:
/dashboard/writer/
/login/
Issue description
If a page fails to set an appropriate X-Frame-Options or Content-Security-Policy HTTP header, it might be possible for a page controlled by an attacker to load it
within an iframe. This may enable a clickjacking attack, in which the attacker's page overlays the target application's interface with a different interface provided by
the attacker. By inducing victim users to perform actions such as mouse clicks and keystrokes, the attacker can cause them to unwittingly carry out actions within
the application that is being targeted. This technique allows the attacker to circumvent defenses against cross-site request forgery, and may result in unauthorized
actions.
Note that some applications attempt to prevent these attacks from within the HTML page itself, using "framebusting" code. However, this type of defense is normally
ineffective and can usually be circumvented by a skilled attacker.
You should determine whether any functions accessible within frameable pages can be used by application users to perform any sensitive actions within the
application.
Issue remediation
To effectively prevent framing attacks, the application should return a response header with the name X-Frame-Options and the value DENY to prevent framing
altogether, or the value SAMEORIGIN to allow framing only by pages on the same origin as the response itself. Note that the SAMEORIGIN header can be partially
bypassed if the application itself can be made to frame untrusted websites.
References
Web Security Academy: Clickjacking
X-Frame-Options
Vulnerability classifications
CWE-693: Protection Mechanism Failure
CAPEC-103: Clickjacking
2.1. https://qa-cms.republicworld.com/dashboard/writer/
Previous Next
Summary
Severity: Information
Confidence: Firm
Host: https://qa-cms.republicworld.com
Path: /dashboard/writer/
Request
GET /dashboard/writer/ HTTP/1.1
Host: qa-cms.republicworld.com
Accept-Encoding: gzip, deflate
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.5845.111 Safari/537.36
Connection: close
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Sec-CH-UA: ".Not/A)Brand";v="99", "Google Chrome";v="116", "Chromium";v="116"
Sec-CH-UA-Platform: Windows
Sec-CH-UA-Mobile: ?0
Response
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Mon, 28 Aug 2023 10:07:10 GMT
Content-Type: text/html; charset=utf-8
Connection: close
X-Powered-By: Next.js
ETag: "luov05329geli"
Vary: Accept-Encoding
Content-Length: 18918
<!DOCTYPE html><html lang="en"><head><meta charSet="utf-8"/><title>Republic Digital</title><meta name="description" content="Republic Digital"/><meta
name="keywords" content=""/><meta name="viewport"
...[SNIP]...
2.2. https://qa-cms.republicworld.com/login/
Previous Next
Summary
Severity: Information
Confidence: Firm
Host: https://qa-cms.republicworld.com
Path: /login/
Request
GET /login/ HTTP/1.1
Host: qa-cms.republicworld.com
Accept-Encoding: gzip, deflate
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.5845.111 Safari/537.36
Connection: close
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Sec-CH-UA: ".Not/A)Brand";v="99", "Google Chrome";v="116", "Chromium";v="116"
Sec-CH-UA-Platform: Windows
Sec-CH-UA-Mobile: ?0
Response
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Mon, 28 Aug 2023 11:27:11 GMT
Content-Type: text/html; charset=utf-8
Connection: close
X-Powered-By: Next.js
ETag: "152mete46jce1b"
Vary: Accept-Encoding
Content-Length: 18191
<!DOCTYPE html><html lang="en"><head><meta charSet="utf-8"/><title>Republic Digital</title><meta name="description" content="Republic Digital"/><meta
name="keywords" content=""/><meta name="viewport"
...[SNIP]...
3. DOM data manipulation (DOM-based)
Previous Next
There are 4 instances of this issue:
/dashboard/writer/
/dashboard/writer/
/login/
/login/
Issue background
DOM-based vulnerabilities arise when a client-side script reads data from a controllable part of the DOM (for example, the URL) and processes this data in an
unsafe way.
DOM data manipulation arises when a script writes controllable data to a field within the DOM that is used within the visible UI or client-side application logic. An
attacker may be able to use the vulnerability to construct a URL that, if visited by another application user, will modify the appearance or behavior of the client-side
UI. An attacker may be able to leverage this to perform virtual defacement of the application, or possibly to induce the user to perform unintended actions.
Burp Suite automatically identifies this issue using dynamic and static code analysis. Static analysis can lead to false positives that are not actually exploitable. If
Burp Scanner has not provided any evidence resulting from dynamic analysis, you should review the relevant code and execution paths to determine whether this
vulnerability is indeed present, or whether mitigations are in place that would prevent exploitation.
Issue remediation
The most effective way to avoid DOM-based DOM data manipulation vulnerabilities is not to dynamically write to DOM data fields any data that originated from any
untrusted source. If the desired functionality of the application means that this behavior is unavoidable, then defenses must be implemented within the client-side
code to prevent malicious data from being stored. In general, this is best achieved by using a whitelist of permitted values.
References
Web Security Academy: DOM data manipulation
Vulnerability classifications
CWE-20: Improper Input Validation
CAPEC-153: Input Data Manipulation
3.1. https://qa-cms.republicworld.com/dashboard/writer/
Previous Next
Summary
Severity: Information
Confidence: Firm
Host: https://qa-cms.republicworld.com
Path: /dashboard/writer/
Issue detail
The application may be vulnerable to DOM-based DOM data manipulation. Data is read from location.href and passed to history.replaceState.
Request
GET /dashboard/writer/ HTTP/1.1
Host: qa-cms.republicworld.com
Accept-Encoding: gzip, deflate
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.5845.111 Safari/537.36
Connection: close
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Sec-CH-UA: ".Not/A)Brand";v="99", "Google Chrome";v="116", "Chromium";v="116"
Sec-CH-UA-Platform: Windows
Sec-CH-UA-Mobile: ?0
Response
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Mon, 28 Aug 2023 10:07:10 GMT
Content-Type: text/html; charset=utf-8
Connection: close
X-Powered-By: Next.js
ETag: "luov05329geli"
Vary: Accept-Encoding
Content-Length: 18918
<!DOCTYPE html><html lang="en"><head><meta charSet="utf-8"/><title>Republic Digital</title><meta name="description" content="Republic Digital"/><meta
name="keywords" content=""/><meta name="viewport"
...[SNIP]...
Dynamic analysis
Data is read from location.href and passed to history.replaceState.
The following value was injected into the source:
https://qa-cms.republicworld.com/dashboard/writer/?u6uuq0xojk=u6uuq0xojk%27%22`'"/u6uuq0xojk/><u6uuq0xojk/\>f5bl4pujtq&#u6uuq0xojk=u6uuq0xojk%27%22`'"/u6uuq0xojk/><u6uu
The previous value reached the sink as:
/dashboard/writer/?u6uuq0xojk=u6uuq0xojk%27%22`'"/u6uuq0xojk/><u6uuq0xojk/\>f5bl4pujtq&#u6uuq0xojk=u6uuq0xojk%27%22`'"/u6uuq0xojk/><u6uuq0xojk/\>f5bl4pujtq&
The stack trace at the source was:
at Object._0x5ed253 [as proxiedGetterCallback] (<anonymous>:1:625634)
at get href [as href] (<anonymous>:1:323401)
at t.getURL (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:80890)
at new $ (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:64216)
at t.createRouter (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:26747)
at Object.<anonymous> (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:15009)
at Generator.next (<anonymous>)
at r (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:137)
at l (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:334)
The stack trace at the sink was:
at Object.AdTdD (<anonymous>:1:618162)
at History.replaceState (<anonymous>:1:618402)
at $.changeState (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:55927)
at https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:64339
3.2. https://qa-cms.republicworld.com/dashboard/writer/
Previous Next
Summary
Severity: Information
Confidence: Firm
Host: https://qa-cms.republicworld.com
Path: /dashboard/writer/
Issue detail
The application may be vulnerable to DOM-based DOM data manipulation. Data is read from location.href and passed to history.replaceState.
Request
GET /dashboard/writer/ HTTP/1.1
Host: qa-cms.republicworld.com
Accept-Encoding: gzip, deflate
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.5845.111 Safari/537.36
Connection: close
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Sec-CH-UA: ".Not/A)Brand";v="99", "Google Chrome";v="116", "Chromium";v="116"
Sec-CH-UA-Platform: Windows
Sec-CH-UA-Mobile: ?0
Response
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Mon, 28 Aug 2023 10:07:10 GMT
Content-Type: text/html; charset=utf-8
Connection: close
X-Powered-By: Next.js
ETag: "luov05329geli"
Vary: Accept-Encoding
Content-Length: 18918
<!DOCTYPE html><html lang="en"><head><meta charSet="utf-8"/><title>Republic Digital</title><meta name="description" content="Republic Digital"/><meta
name="keywords" content=""/><meta name="viewport"
...[SNIP]...
Dynamic analysis
Data is read from location.href and passed to history.replaceState.
The following value was injected into the source:
https://qa-cms.republicworld.com/dashboard/writer/?mu0jnceeex=mu0jnceeex%27%22`'"/mu0jnceeex/><mu0jnceeex/\>m3d0jhhqz3&#mu0jnceeex=mu0jnceeex%27%22`'"/mu0jnceeex/><mu0j
The previous value reached the sink as:
/dashboard/writer/?mu0jnceeex=mu0jnceeex%27%22`%27%22/mu0jnceeex/%3E%3Cmu0jnceeex/\%3Em3d0jhhqz3&#mu0jnceeex=mu0jnceeex%27%22%60'%22/mu0jnceeex/%3E%3Cmu0jnceeex/\%3Em3d
The stack trace at the source was:
at Object._0x5ed253 [as proxiedGetterCallback] (<anonymous>:1:625634)
at get href [as href] (<anonymous>:1:323401)
at t.getURL (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:80890)
at Object.<anonymous> (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:8647)
at Generator.next (<anonymous>)
at r (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:137)
at l (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:334)
at https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:393
at new Promise (<anonymous>)
at Object.<anonymous> (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:275)
at Object.V (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:9060)
at t.initialize (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:7070)
at 14642 (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:15845)
at s (https://qa-cms.republicworld.com/_next/static/chunks/webpack-cc2d95a59395ec34.js:1:167)
at https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:90459
at s.O (https://qa-cms.republicworld.com/_next/static/chunks/webpack-cc2d95a59395ec34.js:1:603)
at https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:90481
at f (https://qa-cms.republicworld.com/_next/static/chunks/webpack-cc2d95a59395ec34.js:1:4786)
at https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:51
The stack trace at the sink was:
at Object.AdTdD (<anonymous>:1:618162)
at History.replaceState (<anonymous>:1:618402)
at $.changeState (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:55927)
at https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:55382
at Generator.next (<anonymous>)
at r (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:137)
at l (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:334)
This was triggered by a message event.
3.3. https://qa-cms.republicworld.com/login/
Previous Next
Summary
Severity: Information
Confidence: Firm
Host: https://qa-cms.republicworld.com
Path: /login/
Issue detail
The application may be vulnerable to DOM-based DOM data manipulation. Data is read from location.href and passed to history.replaceState.
Request
GET /login/ HTTP/1.1
Host: qa-cms.republicworld.com
Accept-Encoding: gzip, deflate
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.5845.111 Safari/537.36
Connection: close
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Sec-CH-UA: ".Not/A)Brand";v="99", "Google Chrome";v="116", "Chromium";v="116"
Sec-CH-UA-Platform: Windows
Sec-CH-UA-Mobile: ?0
Response
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Mon, 28 Aug 2023 11:27:11 GMT
Content-Type: text/html; charset=utf-8
Connection: close
X-Powered-By: Next.js
ETag: "152mete46jce1b"
Vary: Accept-Encoding
Content-Length: 18191
<!DOCTYPE html><html lang="en"><head><meta charSet="utf-8"/><title>Republic Digital</title><meta name="description" content="Republic Digital"/><meta
name="keywords" content=""/><meta name="viewport"
...[SNIP]...
Dynamic analysis
Data is read from location.href and passed to history.replaceState.
The following value was injected into the source:
https://qa-cms.republicworld.com/login/?zy01owz10n=zy01owz10n%27%22`'"/zy01owz10n/><zy01owz10n/\>p69djil9o9&#zy01owz10n=zy01owz10n%27%22`'"/zy01owz10n/><zy01owz10n/\>p6
The previous value reached the sink as:
/login/?zy01owz10n=zy01owz10n%27%22`'"/zy01owz10n/><zy01owz10n/\>p69djil9o9&#zy01owz10n=zy01owz10n%27%22`'"/zy01owz10n/><zy01owz10n/\>p69djil9o9&
The stack trace at the source was:
at Object._0x5ed253 [as proxiedGetterCallback] (<anonymous>:1:625634)
at get href [as href] (<anonymous>:1:323401)
at t.getURL (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:80890)
at new $ (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:64216)
at t.createRouter (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:26747)
at Object.<anonymous> (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:15009)
at Generator.next (<anonymous>)
at r (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:137)
at l (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:334)
The stack trace at the sink was:
at Object.AdTdD (<anonymous>:1:618162)
at History.replaceState (<anonymous>:1:618402)
at $.changeState (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:55927)
at https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:64339
3.4. https://qa-cms.republicworld.com/login/
Previous Next
Summary
Severity: Information
Confidence: Firm
Host: https://qa-cms.republicworld.com
Path: /login/
Issue detail
The application may be vulnerable to DOM-based DOM data manipulation. Data is read from location.href and passed to history.replaceState.
Request
GET /login/ HTTP/1.1
Host: qa-cms.republicworld.com
Accept-Encoding: gzip, deflate
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.5845.111 Safari/537.36
Connection: close
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Sec-CH-UA: ".Not/A)Brand";v="99", "Google Chrome";v="116", "Chromium";v="116"
Sec-CH-UA-Platform: Windows
Sec-CH-UA-Mobile: ?0
Response
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Mon, 28 Aug 2023 11:27:11 GMT
Content-Type: text/html; charset=utf-8
Connection: close
X-Powered-By: Next.js
ETag: "152mete46jce1b"
Vary: Accept-Encoding
Content-Length: 18191
<!DOCTYPE html><html lang="en"><head><meta charSet="utf-8"/><title>Republic Digital</title><meta name="description" content="Republic Digital"/><meta
name="keywords" content=""/><meta name="viewport"
...[SNIP]...
Dynamic analysis
Data is read from location.href and passed to history.replaceState.
The following value was injected into the source:
https://qa-cms.republicworld.com/login/?ng518ehmqo=ng518ehmqo%27%22`'"/ng518ehmqo/><ng518ehmqo/\>l56fyk7olm&#ng518ehmqo=ng518ehmqo%27%22`'"/ng518ehmqo/><ng518ehmqo/\>l5
The previous value reached the sink as:
/login/?ng518ehmqo=ng518ehmqo%27%22`%27%22/ng518ehmqo/%3E%3Cng518ehmqo/\%3El56fyk7olm&#ng518ehmqo=ng518ehmqo%27%22%60'%22/ng518ehmqo/%3E%3Cng518ehmqo/\%3El56fyk7olm&
The stack trace at the source was:
at Object._0x5ed253 [as proxiedGetterCallback] (<anonymous>:1:625634)
at get href [as href] (<anonymous>:1:323401)
at t.getURL (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:80890)
at Object.<anonymous> (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:8647)
at Generator.next (<anonymous>)
at r (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:137)
at l (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:334)
at https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:393
at new Promise (<anonymous>)
at Object.<anonymous> (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:275)
at Object.V (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:9060)
at t.initialize (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:7070)
at 14642 (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:15845)
at s (https://qa-cms.republicworld.com/_next/static/chunks/webpack-cc2d95a59395ec34.js:1:167)
at https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:90459
at s.O (https://qa-cms.republicworld.com/_next/static/chunks/webpack-cc2d95a59395ec34.js:1:603)
at https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:90481
at f (https://qa-cms.republicworld.com/_next/static/chunks/webpack-cc2d95a59395ec34.js:1:4786)
at https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:51
The stack trace at the sink was:
at Object.AdTdD (<anonymous>:1:618162)
at History.replaceState (<anonymous>:1:618402)
at $.changeState (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:55927)
at https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:55382
at Generator.next (<anonymous>)
at r (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:137)
at l (https://qa-cms.republicworld.com/_next/static/chunks/main-29d5dc02355e4d97.js:1:334)
This was triggered by a message event.
4. Backup file
Previous Next
There are 2 instances of this issue:
/dashboard/writer~
/login~
Issue description
Publicly accessible backups and outdated copies of files can provide attackers with extra attack surface. Depending on the server configuration and file type, they
may also expose source code, configuration details, and other information intended to remain secret.
Issue remediation
Review the file to identify whether it's intended to be publicly accessible, and remove it from the server's web root if it isn't. It may also be worth auditing the server
contents to find other outdated files, and taking measures to prevent the problem from reoccurring.
References
Web Security Academy: Information disclosure via backup files
Vulnerability classifications
CWE-530: Exposure of Backup File to an Unauthorized Control Sphere
CAPEC-37: Retrieve Embedded Sensitive Data
CAPEC-204: Lifting Sensitive Data Embedded in Cache
4.1. https://qa-cms.republicworld.com/dashboard/writer~
Previous Next
Summary
Severity: Information
Confidence: Certain
Host: https://qa-cms.republicworld.com
Path: /dashboard/writer/
Request 1
GET /dashboard/writer~ HTTP/1.1
Host: qa-cms.republicworld.com
Accept-Encoding: gzip, deflate
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.5845.111 Safari/537.36
Connection: close
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Sec-CH-UA: ".Not/A)Brand";v="99", "Google Chrome";v="116", "Chromium";v="116"
Sec-CH-UA-Platform: Windows
Sec-CH-UA-Mobile: ?0
Response 1
HTTP/1.1 308 Permanent Redirect
Server: nginx/1.18.0 (Ubuntu)
Date: Mon, 28 Aug 2023 10:10:07 GMT
Connection: close
Location: /dashboard/writer~/
Refresh: 0;url=/dashboard/writer~/
Content-Length: 19
/dashboard/writer~/
Request 2
GET /dashboard/g~ HTTP/1.1
Host: qa-cms.republicworld.com
Accept-Encoding: gzip, deflate
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.5845.111 Safari/537.36
Connection: close
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Sec-CH-UA: ".Not/A)Brand";v="99", "Google Chrome";v="116", "Chromium";v="116"
Sec-CH-UA-Platform: Windows
Sec-CH-UA-Mobile: ?0
Response 2
HTTP/1.1 308 Permanent Redirect
Server: nginx/1.18.0 (Ubuntu)
Date: Mon, 28 Aug 2023 10:10:07 GMT
Connection: close
Location: /dashboard/g~/
Refresh: 0;url=/dashboard/g~/
Content-Length: 14
/dashboard/g~/
4.2. https://qa-cms.republicworld.com/login~
Previous Next
Summary
Severity: Information
Confidence: Certain
Host: https://qa-cms.republicworld.com
Path: /login/
Request 1
GET /login~ HTTP/1.1
Host: qa-cms.republicworld.com
Accept-Encoding: gzip, deflate
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.5845.111 Safari/537.36
Connection: close
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Sec-CH-UA: ".Not/A)Brand";v="99", "Google Chrome";v="116", "Chromium";v="116"
Sec-CH-UA-Platform: Windows
Sec-CH-UA-Mobile: ?0
Response 1
HTTP/1.1 308 Permanent Redirect
Server: nginx/1.18.0 (Ubuntu)
Date: Mon, 28 Aug 2023 11:30:31 GMT
Connection: close
Location: /login~/
Refresh: 0;url=/login~/
Content-Length: 8
/login~/
Request 2
GET /k~ HTTP/1.1
Host: qa-cms.republicworld.com
Accept-Encoding: gzip, deflate
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.5845.111 Safari/537.36
Connection: close
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Sec-CH-UA: ".Not/A)Brand";v="99", "Google Chrome";v="116", "Chromium";v="116"
Sec-CH-UA-Platform: Windows
Sec-CH-UA-Mobile: ?0
Response 2
HTTP/1.1 308 Permanent Redirect
Server: nginx/1.18.0 (Ubuntu)
Date: Mon, 28 Aug 2023 11:30:31 GMT
Connection: close
Location: /k~/
Refresh: 0;url=/k~/
Content-Length: 4
/k~/
5. Cacheable HTTPS response
Previous Next
There are 2 instances of this issue:
/dashboard/writer/
/login/
Issue description
Unless directed otherwise, browsers may store a local cached copy of content received from web servers. Some browsers, including Internet Explorer, cache
content accessed via HTTPS. If sensitive information in application responses is stored in the local cache, then this may be retrieved by other users who have
access to the same computer at a future time.
Issue remediation
Applications should return caching directives instructing browsers not to store local copies of any sensitive data. Often, this can be achieved by configuring the web
server to prevent caching for relevant paths within the web root. Alternatively, most web development platforms allow you to control the server's caching directives
from within individual scripts. Ideally, the web server should return the following HTTP headers in all responses containing sensitive content:
Cache-control: no-store
Pragma: no-cache
References
Web Security Academy: Information disclosure
Vulnerability classifications
CWE-524: Information Exposure Through Caching
CWE-525: Information Exposure Through Browser Caching
CAPEC-37: Retrieve Embedded Sensitive Data
5.1. https://qa-cms.republicworld.com/dashboard/writer/
Previous Next
Summary
Severity: Information
Confidence: Certain
Host: https://qa-cms.republicworld.com
Path: /dashboard/writer/
Request 1
GET /dashboard/writer/ HTTP/1.1
Host: qa-cms.republicworld.com
Accept-Encoding: gzip, deflate
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.5845.111 Safari/537.36
Connection: close
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Sec-CH-UA: ".Not/A)Brand";v="99", "Google Chrome";v="116", "Chromium";v="116"
Sec-CH-UA-Platform: Windows
Sec-CH-UA-Mobile: ?0
Response 1
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Mon, 28 Aug 2023 10:07:10 GMT
Content-Type: text/html; charset=utf-8
Connection: close
X-Powered-By: Next.js
ETag: "luov05329geli"
Vary: Accept-Encoding
Content-Length: 18918
<!DOCTYPE html><html lang="en"><head><meta charSet="utf-8"/><title>Republic Digital</title><meta name="description" content="Republic Digital"/><meta
name="keywords" content=""/><meta name="viewport"
...[SNIP]...
5.2. https://qa-cms.republicworld.com/login/
Previous
Summary
Severity: Information
Confidence: Certain
Host: https://qa-cms.republicworld.com
Path: /login/
Request 1
GET /login/ HTTP/1.1
Host: qa-cms.republicworld.com
Accept-Encoding: gzip, deflate
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.5845.111 Safari/537.36
Connection: close
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Sec-CH-UA: ".Not/A)Brand";v="99", "Google Chrome";v="116", "Chromium";v="116"
Sec-CH-UA-Platform: Windows
Sec-CH-UA-Mobile: ?0
Response 1
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Mon, 28 Aug 2023 11:27:11 GMT
Content-Type: text/html; charset=utf-8
Connection: close
X-Powered-By: Next.js
ETag: "152mete46jce1b"
Vary: Accept-Encoding
Content-Length: 18191
<!DOCTYPE html><html lang="en"><head><meta charSet="utf-8"/><title>Republic Digital</title><meta name="description" content="Republic Digital"/><meta
name="keywords" content=""/><meta name="viewport"
...[SNIP]...
6. TLS certificate
Previous
Summary
Severity: Information
Confidence: Certain
Host: https://qa-cms.republicworld.com
Path: /
Issue detail
The server presented a valid, trusted TLS certificate. This issue is purely informational.
The server presented the following certificates:
Server certificate
Issued to: *.republicworld.com, republicworld.com
Issued by: Sectigo RSA Domain Validation Secure Server CA
Valid from: Mon May 08 05:30:00 IST 2023
Valid to: Thu May 09 05:29:59 IST 2024
Certificate chain #1
Issued to: Sectigo RSA Domain Validation Secure Server CA
Issued by: USERTrust RSA Certification Authority
Valid from: Fri Nov 02 05:30:00 IST 2018
Valid to: Wed Jan 01 05:29:59 IST 2031
Certificate chain #2
Issued to: USERTrust RSA Certification Authority
Issued by: USERTrust RSA Certification Authority
Valid from: Mon Feb 01 05:30:00 IST 2010
Valid to: Tue Jan 19 05:29:59 IST 2038
Issue background
TLS (or SSL) helps to protect the confidentiality and integrity of information in transit between the browser and server, and to provide authentication of the server's
identity. To serve this purpose, the server must present an TLS certificate that is valid for the server's hostname, is issued by a trusted authority and is valid for the
current date. If any one of these requirements is not met, TLS connections to the server will not provide the full protection for which TLS is designed.
It should be noted that various attacks exist against TLS in general, and in the context of HTTPS web connections in particular. It may be possible for a determined
and suitably-positioned attacker to compromise TLS connections without user detection even when a valid TLS certificate is used.
References
SSL/TLS Configuration Guide
Vulnerability classifications
CWE-295: Improper Certificate Validation
CWE-326: Inadequate Encryption Strength
CWE-327: Use of a Broken or Risky Cryptographic Algorithm
Report generated by Burp Suite web vulnerability scanner v2023.9.3, at Mon Aug 28 17:09:34 IST 2023.
You might also like
- WebApp ReportDocument9 pagesWebApp ReportRavi GiriNo ratings yet
- 5255 - 44 - 20112023 12 - 00 - 00 A. M.Document129 pages5255 - 44 - 20112023 12 - 00 - 00 A. M.fredyNo ratings yet
- Burp Scanner ReportDocument3 pagesBurp Scanner ReportPr RabariNo ratings yet
- Vlab Demo - Using ASM For Web Vulnerabilities - v12.0.C PDFDocument22 pagesVlab Demo - Using ASM For Web Vulnerabilities - v12.0.C PDFVaishak PdNo ratings yet
- Detailed Scan Report: Identified Confirmed CriticalDocument103 pagesDetailed Scan Report: Identified Confirmed CriticalViktor CherenapovNo ratings yet
- WebStrike PDF ReportDocument4 pagesWebStrike PDF ReportBiswajitNo ratings yet
- VLab Demo - Using ASM For Web Vulnerabilities - V12.0.0.01Document21 pagesVLab Demo - Using ASM For Web Vulnerabilities - V12.0.0.01Marcos ValleNo ratings yet
- IntruderReport - 06 Oct 2021Document15 pagesIntruderReport - 06 Oct 2021DigitalboxNo ratings yet
- ETHICAL HACKING GUIDE-Part 3: Comprehensive Guide to Ethical Hacking worldFrom EverandETHICAL HACKING GUIDE-Part 3: Comprehensive Guide to Ethical Hacking worldNo ratings yet
- Cargill Web Application Scanning ReportDocument27 pagesCargill Web Application Scanning ReportHari KingNo ratings yet
- Cloud Agent TroubleshootingDocument15 pagesCloud Agent Troubleshootingtom.karl.schranzNo ratings yet
- Owasp Zap Hostedscan Report 2024-02-12Document17 pagesOwasp Zap Hostedscan Report 2024-02-12faizan.rezaNo ratings yet
- Penetration Testing Report: DateDocument9 pagesPenetration Testing Report: DatetraeNo ratings yet
- IntruderReport2 - 04 Oct 2021Document9 pagesIntruderReport2 - 04 Oct 2021DigitalboxNo ratings yet
- Vulnerability Scan: Prepared byDocument13 pagesVulnerability Scan: Prepared byzitexitNo ratings yet
- Assessment Report: (076271c3)Document87 pagesAssessment Report: (076271c3)Marco SciortinoNo ratings yet
- Comprehensive New Https Tech Jobs Credit Agricole ComDocument27 pagesComprehensive New Https Tech Jobs Credit Agricole ComBrain codeNo ratings yet
- IntruderReport - 04 Oct 2021Document13 pagesIntruderReport - 04 Oct 2021DigitalboxNo ratings yet
- Analisis VIRTUALIZACIONDocument74 pagesAnalisis VIRTUALIZACIONNelson TorresNo ratings yet
- 1 - Threat Modeling ReportDocument4 pages1 - Threat Modeling ReportSagar SaklaniNo ratings yet
- Vulnerability Scan: Prepared byDocument14 pagesVulnerability Scan: Prepared byzitexitNo ratings yet
- Analisis WEBDocument88 pagesAnalisis WEBNelson TorresNo ratings yet
- Vulnerability Test Report: IP ScanDocument32 pagesVulnerability Test Report: IP ScanJorge FalconiNo ratings yet
- Cisco Firesight System 5.3 V1 - Always On: About This Cisco SolutionDocument22 pagesCisco Firesight System 5.3 V1 - Always On: About This Cisco SolutionIoana PetcuNo ratings yet
- XSS - Part 1Document5 pagesXSS - Part 1Silviu PricopeNo ratings yet
- Azure - Windows Server - Host Scan - 2024 Jan q5trvkDocument410 pagesAzure - Windows Server - Host Scan - 2024 Jan q5trvkeshensanjula2002No ratings yet
- Lightspeed Cache Vulnerability PaperDocument14 pagesLightspeed Cache Vulnerability PaperMajedNo ratings yet
- Report Generated by Nessus™ Mon, 09 Sep 2019 12:21:40 - 03Document79 pagesReport Generated by Nessus™ Mon, 09 Sep 2019 12:21:40 - 03Nelson TorresNo ratings yet
- Technical White Paper On Web Application FirewallDocument14 pagesTechnical White Paper On Web Application FirewallAla EddineNo ratings yet
- Report Web AuditDocument17 pagesReport Web Auditanupprakash36No ratings yet
- Security Sample VAPT ReportDocument28 pagesSecurity Sample VAPT ReportRavi GiriNo ratings yet
- PentestTools WebsiteScanner ReportDocument7 pagesPentestTools WebsiteScanner ReportMario Sernaque RumicheNo ratings yet
- Hacker 101Document2 pagesHacker 101Emiliano LarreaNo ratings yet
- PAN ACE7.0 100% PassDocument112 pagesPAN ACE7.0 100% PassRobert Martin87% (31)
- Web Application Audit Report: Demo AccountDocument12 pagesWeb Application Audit Report: Demo AccountSamuel KonanNo ratings yet
- Vuln ScanDocument12 pagesVuln ScanBrijendra Pratap SinghNo ratings yet
- (Divi Report) Daptatech RepDocument5 pages(Divi Report) Daptatech RepcarlosNo ratings yet
- CiscoDocument92 pagesCiscoari sirwanNo ratings yet
- ZAP Scanning: Project 2Document24 pagesZAP Scanning: Project 2Sabyasachi duttaNo ratings yet
- BadStore Net v2 1 Manual PDFDocument23 pagesBadStore Net v2 1 Manual PDFGuillermo AndradeNo ratings yet
- Developer Report: Acunetix Website Audit 23 December, 2021Document7 pagesDeveloper Report: Acunetix Website Audit 23 December, 2021BAGAS TRI RAMADANA -No ratings yet
- Website Vulnerability Scanner Report (Light)Document4 pagesWebsite Vulnerability Scanner Report (Light)MasBaNo ratings yet
- Web Vulnerability ReportDocument7 pagesWeb Vulnerability ReporthitcaNo ratings yet
- Website Vulnerability Scanner Report (Light)Document6 pagesWebsite Vulnerability Scanner Report (Light)alex681219No ratings yet
- Delhi Ford 1Document18 pagesDelhi Ford 1Vivek GautamNo ratings yet
- Sample Web Application Security AssessmentDocument15 pagesSample Web Application Security AssessmentEsteban Francisco Sánchez MillaNo ratings yet
- Research Blogs FeedDocument22 pagesResearch Blogs FeedHéctor Javier HerreraNo ratings yet
- A.185 53 151 170 185 53 151 171 185 53 151 172 185 53 151 174 185 53 151 189 F3ek7rDocument171 pagesA.185 53 151 170 185 53 151 171 185 53 151 172 185 53 151 174 185 53 151 189 F3ek7rNirdesh RayaNo ratings yet
- Sample Report WebDocument19 pagesSample Report WebMuhammad AwaisNo ratings yet
- Summer Internship ProjectDocument15 pagesSummer Internship ProjectadityaNo ratings yet
- Test - Accredited Configuration Engineer (ACE) Exam - PAN-OS 7.0 VersionDocument13 pagesTest - Accredited Configuration Engineer (ACE) Exam - PAN-OS 7.0 VersiongustavoNo ratings yet
- Palo Alto Networks - Testking.pcnse7.v2016!09!07.by - Pierre.51qDocument37 pagesPalo Alto Networks - Testking.pcnse7.v2016!09!07.by - Pierre.51qSaurabh Gupta100% (1)
- Best Practices - DDoS ProtectorDocument4 pagesBest Practices - DDoS ProtectorWiKiToNNo ratings yet
- BM Scan ReportDocument61 pagesBM Scan ReportprabufameNo ratings yet
- Web Application Vapt Cybersapiens United LLP: Report OnDocument19 pagesWeb Application Vapt Cybersapiens United LLP: Report OnPavan Kumar Chinta100% (1)
- 33小铺扫描附件Document9 pages33小铺扫描附件ni koNo ratings yet
- Robert Arias 20163930 Ubuntu Test 2 - ZnhxabDocument38 pagesRobert Arias 20163930 Ubuntu Test 2 - ZnhxabNico RosarioNo ratings yet
- Vdocument - in - Iot Penetration Test Report Iot Penetration Test Report Momentum Axel 720pDocument15 pagesVdocument - in - Iot Penetration Test Report Iot Penetration Test Report Momentum Axel 720pWagner P RodriguesNo ratings yet
- Lab Fat: CSE3501 Information Security Analysis and AuditDocument21 pagesLab Fat: CSE3501 Information Security Analysis and AuditSona SharmaNo ratings yet
- Comandos MetroDocument19 pagesComandos MetroComunicação Lagoinha Campo GrandeNo ratings yet
- What Is That?Document15 pagesWhat Is That?ajipurnomoNo ratings yet
- Network Security OverviewDocument54 pagesNetwork Security OverviewRINTORISDIANRNo ratings yet
- Path Loss: Sevan Siyyah AbdullahDocument20 pagesPath Loss: Sevan Siyyah Abdullahnina mimaNo ratings yet
- KS0142 Keyestudio SIM900 GSM - GPRS Module Shield PDFDocument6 pagesKS0142 Keyestudio SIM900 GSM - GPRS Module Shield PDFJ.G N.HNo ratings yet
- UBNT New PresentationDocument20 pagesUBNT New PresentationJohn Seth Toribio SalazarNo ratings yet
- EMCview - Files - CISPR 11 - EN 55011 - V1 - 3Document25 pagesEMCview - Files - CISPR 11 - EN 55011 - V1 - 3Michael MayerhoferNo ratings yet
- Flexpod Datacenter For Ai/Ml With Cisco Ucs 480 ML For Deep LearningDocument105 pagesFlexpod Datacenter For Ai/Ml With Cisco Ucs 480 ML For Deep LearningSampath Kumar PolisettyNo ratings yet
- 38.LFDC Relay Testing With F6150-1Document89 pages38.LFDC Relay Testing With F6150-1Sristhi GanguliNo ratings yet
- Computer Networks Lab Manual R18Document63 pagesComputer Networks Lab Manual R18Naga Kalyan0% (1)
- AN296094 Method For Converting A PWM Output To An Analog Output When Using Hall Effect Sensor ICsDocument8 pagesAN296094 Method For Converting A PWM Output To An Analog Output When Using Hall Effect Sensor ICsaless2056No ratings yet
- What Is 2G?Document19 pagesWhat Is 2G?Haya MalikNo ratings yet
- Amazon Web Services - Two-NIC BIG-IP VEDocument3 pagesAmazon Web Services - Two-NIC BIG-IP VEsaidov19No ratings yet
- Scsi:: Internet Small Computer System Interface, An Internet Protocol (IP) - BasedDocument10 pagesScsi:: Internet Small Computer System Interface, An Internet Protocol (IP) - BasedpavanguptaNo ratings yet
- Ericsson New BTSDocument7 pagesEricsson New BTSemailad_ayo100% (1)
- UNI-T Oscilloscopes User Manual V1.0Document27 pagesUNI-T Oscilloscopes User Manual V1.0Paco PillNo ratings yet
- Redundancy Load Balancing PDFDocument15 pagesRedundancy Load Balancing PDFTabarez AhmedNo ratings yet
- Logicore Ip Reed-Solomon Encoder v8.0: Product GuideDocument30 pagesLogicore Ip Reed-Solomon Encoder v8.0: Product GuideamanNo ratings yet
- Lockdown DDocument19 pagesLockdown DGeorge MihailaNo ratings yet
- EC-Council: Exam Questions 312-50v11Document16 pagesEC-Council: Exam Questions 312-50v11Lê Huyền MyNo ratings yet
- HowTo Configure NVMe Over Fabrics (NVMe-oF) Target Offload 2022-0528Document11 pagesHowTo Configure NVMe Over Fabrics (NVMe-oF) Target Offload 2022-0528James ZhangNo ratings yet
- Comparison of Iot Application Layer ProtocolsDocument63 pagesComparison of Iot Application Layer ProtocolsAditriNo ratings yet
- Umwd 09016 XDHDocument3 pagesUmwd 09016 XDHИван ФиличевNo ratings yet
- Lab 5: 802.1X: Wired Networks: PEAPDocument13 pagesLab 5: 802.1X: Wired Networks: PEAPJosel ArevaloNo ratings yet
- SM Smg935uDocument119 pagesSM Smg935uHAITHM MURSHEDNo ratings yet
- Roaming 2Document19 pagesRoaming 2reddifmail100% (1)
- A New Approach For Multilevel Steganography Using Visual Cryptography For Multimedia Application"Document18 pagesA New Approach For Multilevel Steganography Using Visual Cryptography For Multimedia Application"Marisna N. FadhilaNo ratings yet
- Cyber Course 1 Capstone - Part III - Student Template - Rev Aug 22Document4 pagesCyber Course 1 Capstone - Part III - Student Template - Rev Aug 22Fraz Sarwar0070% (1)
- MG - Networking L4 - Wireess Network IndoorDocument25 pagesMG - Networking L4 - Wireess Network IndoorgarysamjonesNo ratings yet
- Cpeo 450 Ds FinalDocument4 pagesCpeo 450 Ds Finalmy_scribd_docsNo ratings yet