Professional Documents
Culture Documents
Cs601 Unit V
Uploaded by
Rekha RahangdaleCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Cs601 Unit V
Uploaded by
Rekha RahangdaleCopyright:
Available Formats
CS601 Wireless Communication and Networks Unit - V
UNIT – V MOBILE TRANSPORT LAYER AND
SUPPORT FOR MOBILITY
Mobile transport layer – Traditional TCP-Indirect Snooping-Mobile TCP -Support for Mobility-WWW-Wireless
Application Protocol.
TRADITIONAL TCP
Mechanisms that influence the efficiency of TCP in a mobile environment
Congestion control
Slow start
Fast retransmit/fast recovery
Implications on mobility
Congestion control
TCP has been designed for fixed networks with fixed end-systems
Hardware and software are mature enough to ensure reliability of data
The probable reason for a packet loss in a fixed network is a temporary overload some point in the
transmission path, i.e., a state of congestion at a node
The packet buffers of a router are filled and the router cannot forward the packets fast enough
The only thing a router can do in this situation is to drop packets
The sender notices the missing acknowledgement for the lost packet and assumes a packet loss due to
congestion
Retransmitting the missing packet and continuing at full sending rate would now be unwise, as this might
only increase the congestion.
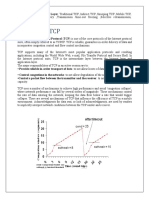
Slow start
The behavior TCP shows after the detection of congestion is called slow start
The sender always calculates a congestion window for a receiver.
The start size of the congestion window is one segment (TCP packet).
This scheme doubles the congestion window every time the acknowledgements come back, which takes
one round trip time (RTT) like 1, 2, 4, 8 etc.
This is called the exponential growth of the congestion window in the slow start mechanism.
The exponential growth stops at the congestion threshold.
As soon as the congestion window reaches the congestion threshold, further increase of the transmission
rate is only linear by adding 1 to the congestion window each time the acknowledgements come back
Linear increase continues until a time-out at the sender occurs due to a missing acknowledgement, or until
the sender detects a gap in transmitted data
o the sender sets the congestion threshold to half of the current congestion window
o The congestion window itself is set to one segment
Fast retransmit/fast recovery
Fast Retransmit
a receiver sends acknowledgements only if it receives any packets from the sender.
Receiving acknowledgements from a receiver also shows that the receiver continuously receives something
from the sender.
The gap in the packet stream is not due to severe congestion, but a simple packet loss due to a
transmission error.
The sender can now retransmit the missing packet(s) before the timer expires.
This behavior is called fast retransmit
MTech CSE (PT, 2011-14) SRM, Ramapuram 1 hcr:innovationcse@gg
CS601 Wireless Communication and Networks Unit - V
Fast Recovery
The receipt of acknowledgements shows that there is no congestion to justify a slow start.
The sender can continue with the current congestion window.
The sender performs a fast recovery from the packet loss
This mechanism can improve the efficiency of TCP dramatically
Implications on mobility
TCP concludes a congestion situation from a missing acknowledgement
o typically wrong in wireless networks, here we often have packet loss due to transmission errors
o mobility itself can cause packet loss, if e.g. a mobile node roams from one access point (e.g. foreign
agent in Mobile IP) to another while there are still packets in transit to the wrong access point and
forwarding is not possible
The performance of an unchanged TCP degrades severely
o TCP cannot be changed fundamentally due to the large base of installation in the fixed network,
TCP for mobility has to remain compatible
o the basic TCP mechanisms keep the whole Internet together
CLASSICAL TCP IMPROVEMENTS
Indirect TCP (I-TCP)
Snooping TCP
Mobile TCP
Fast retransmit/fast recovery
Transmission/time-out freezing
Selective retransmission
Transaction-oriented TCP
Indirect TCP (I-TCP)
Socket and state migration after handover of a mobile host
MTech CSE (PT, 2011-14) SRM, Ramapuram 2 hcr:innovationcse@gg
CS601 Wireless Communication and Networks Unit - V
I-TCP segments a TCP connection into a
o fixed part - Standard TCP is used
o wireless part - optimized TCP protocol
splitting of the TCP connection at, e.g., the foreign agent into 2 TCP connections, no real end-to-end
connection any longer
hosts in the fixed part of the net do not notice the characteristics of the wireless part
Advantages
no changes in the fixed network necessary, no changes for the hosts (TCP protocol) necessary, all current
optimizations to TCP still work
transmission errors on the wireless link do not propagate into the fixed network
simple to control, mobile TCP is used only for one hop between, e.g., a foreign agent and mobile host
therefore, a very fast retransmission of packets is possible, the short delay on the mobile hop is known
Disadvantages
loss of end-to-end semantics, an acknowledgement to a sender does now not any longer mean that a
receiver really got a packet, foreign agents might crash
higher latency possible due to buffering of data within the foreign agent and forwarding to a new FA
Snooping TCP
the foreign agent buffers all packets with destination mobile host and additionally ‘snoops’ the packet flow in
both directions to recognize acknowledgements
buffering enable the FA to perform a local retransmission in case of packet loss on the wireless link
Transparent extension of TCP within the foreign agent
buffering of packets sent to the mobile host
lost packets on the wireless link (both directions!) will be retransmitted immediately by the mobile host or
foreign agent, respectively (so called “local” retransmission)
the foreign agent therefore “snoops” the packet flow and recognizes acknowledgements in both directions,
it also filters ACKs
changes of TCP only within the foreign agent
Data transfer to the mobile host
o FA buffers data until it receives ACK of the MH, FA detects packet loss via duplicated ACKs or time-out
o fast retransmission possible, transparent for the fixed network
Data transfer from the mobile host
o FA detects packet loss on the wireless link via sequence numbers,
FA answers directly with a NACK to the MH
o MH can now retransmit data with only a very short delay
Integration of the MAC layer
o MAC layer often has similar mechanisms to those of TCP
o thus, the MAC layer can already detect duplicated packets due to retransmissions and discard them
Problems
o snooping TCP does not isolate the wireless link as good as I-TCP
o snooping might be useless depending on encryption schemes
Advantages
The end-to-end TCP semantic is preserved
MTech CSE (PT, 2011-14) SRM, Ramapuram 3 hcr:innovationcse@gg
CS601 Wireless Communication and Networks Unit - V
The correspondent host does not need to be changed; most of the enhancements are in the foreign agent
It does not need a handover of state as soon as the mobile host moves to another foreign agent.
It does not matter if the next foreign agent uses the enhancement or not
Disadvantages
Snooping TCP does not isolate the behavior of the wireless link as well as ITCP
Using negative acknowledgements between the foreign agent and the mobile host assumes additional
mechanisms on the mobile host.
All efforts for snooping and buffering data may be useless if certain encryption schemes are applied end-to-
end between the correspondent host and mobile host
Mobile TCP
Special handling of lengthy and/or frequent disconnections
M-TCP splits as I-TCP does
o unmodified TCP fixed network to supervisory host (SH)
o optimized TCP SH to MH
Supervisory host
o no caching, no retransmission
o monitors all packets, if disconnection detected
set sender window size to 0
sender automatically goes into persistent mode
o old or new SH reopen the window
Advantages
o maintains semantics, supports disconnection, no buffer forwarding
Disadvantages
o loss on wireless link propagated into fixed network
o adapted TCP on wireless link
Fast retransmit / fast recovery
Change of foreign agent often results in packet loss
o TCP reacts with slow-start although there is no congestion
Forced fast retransmit
o as soon as the mobile host has registered with a new foreign agent, the MH sends duplicated
acknowledgements on purpose
o this forces the fast retransmit mode at the communication partners
o additionally, the TCP on the MH is forced to continue sending with the actual window size and not to go
into slow-start after registration
Advantage
o simple changes result in significant higher performance
Disadvantage
o further mix of IP and TCP, no transparent approach
Transmission / time-out freezing
Mobile hosts can be disconnected for a longer time
o no packet exchange possible, e.g., in a tunnel, disconnection due to overloaded cells or mux. with
higher priority traffic
o TCP disconnects after time-out completely
TCP freezing
o MAC layer is often able to detect interruption in advance
o MAC can inform TCP layer of upcoming loss of connection
o TCP stops sending, but does now not assume a congested link
o MAC layer signals again if reconnected
Advantage
o scheme is independent of data
Disadvantage
o TCP on mobile host has to be changed, mechanism depends on MAC layer
MTech CSE (PT, 2011-14) SRM, Ramapuram 4 hcr:innovationcse@gg
CS601 Wireless Communication and Networks Unit - V
Selective retransmission
TCP acknowledgements are often cumulative
o ACK n acknowledges correct and in-sequence receipt of packets up to n
o if single packets are missing quite often a whole packet sequence beginning at the gap has to be
retransmitted (go-back-n), thus wasting bandwidth
Selective retransmission as one solution
o RFC2018 allows for acknowledgements of single packets, not only acknowledgements of in-sequence
packet streams without gaps
o sender can now retransmit only the missing packets
Advantage
o much higher efficiency
Disadvantage
o more complex software in a receiver, more buffer needed at the receiver
Transaction-oriented TCP
TCP phases
o setup, data transmission, connection release
o using 3-way-handshake needs 3 packets for setup
and release, respectively
o thus, even short messages need a minimum of 7
packets!
Transaction oriented TCP
o RFC1644, T-TCP, describes a TCP version to
avoid this overhead
o connection setup, data transfer and connection
release can be combined
o thus, only 2 or 3 packets are needed
Advantage : efficiency
Disadvantage
o requires changed TCP
o mobility not longer transparent
Approach Mechanism Advantages Disadvantages
Loss of TCP semantics, higher
Splits TCP connection Isolation of wireless
Indirect TCP latency at handover, security
into two connections link, simple
problems
Snoops data and Transparent for end-to-
Insufficient isolation of wireless
Snooping TCP acknowledgements,local end connection, MAC
link, security problems
retransmission integration possible
Maintains end-to-end Bad isolation of wireless link,
Splits TCP connection,
semantics, andles long processing overhead due to
M-TCP chokes sender via
term and frequent bandwidth management, security
window size
disconnections problems
Fast retransmit / Avoids slow-start after
Simple and efficient Mixed layers, not transparent
fast recovery roaming
Freezes TCP state at Independent of content,
Transmission / Changes in TCP required, MAC
disconnection, resumes works for longer
time-out freezing dependent
after reconnection interruptions
Slightly more complex receiver
Selective Retransmits only lost
Very efficient software, more buffer space
retransmission data
needed
Combines connection
Transaction- Efficient for certain Changes in TCP required, not
setup/release and data
oriented TCP applications transparent, security problems
transmission
MTech CSE (PT, 2011-14) SRM, Ramapuram 5 hcr:innovationcse@gg
CS601 Wireless Communication and Networks Unit - V
WORLD WIDE WEB
Protocol (HTTP, Hypertext Transfer Protocol) and language (HTML, Hypertext Markup Language) of the
Web have not been designed for mobile applications and mobile devices, thus creating many problems!
Typical transfer sizes
o HTTP request: 100-350 byte
o responses avg. <10 kbyte, header 160 byte, GIF 4.1kByte, JPEG 12.8 kbyte, HTML 5.6 kbyte
o but also many large files that cannot be ignored
The Web is no file system
o Web pages are not simple files to download
o static and dynamic content, interaction with servers via forms, content transformation, push
technologies etc.
o many hyperlinks, automatic loading and reloading, redirecting
o a single click might have big consequences!
Hypertext transfer protocol
HTTP is a stateless, lightweight, application level protocol for data transfer between servers and clients.
The first version, HTTP/1.0 , never became a formal standard due to too many variant implementations
HTTP/1.1 is the standard currently used by most
An HTTP transaction consists of an HTTP request issued by a client and an HTTP response from a server
Stateless means that all HTTP transactions are independent of each other.
HTTP does not ‘remember’ any transaction, request, or response.
This results in a very simple implementation without the need for complex state machines.
Example
GET / HTTP/1.1
Host: www.inf.fu-berlin.de
The server might answer with something similar to the following (the response):
HTTP/1.1 200 OK
Date: Wed, 30 Oct 2002 19:44:26 GMT
Server: Apache/1.3.12 (Unix) mod_perl/1.24
Last-Modified: Wed, 30 Oct 2002 13:16:31 GMT
ETag: "2d8190-2322-3dbfdbaf"
Accept-Ranges: bytes
Content-Length: 8994
Content-Type: text/html
<html>
<head>
HTTP 1.0 and Mobility
Characteristics
stateless, client/server, request/response
needs a connection oriented protocol (TCP), one connection per request
primitive caching and security
Problems
Bandwidth and delay
designed for large bandwidth (compared to wireless access) and low delay
big and redundant protocol headers (readable for humans, stateless, therefore big headers in ASCII)
uncompressed content transfer
using TCP
o huge overhead per request (3-way-handshake) compared with the content, e.g., of a GET request
o slow-start problematic
DNS lookup by client causes additional traffic
MTech CSE (PT, 2011-14) SRM, Ramapuram 6 hcr:innovationcse@gg
CS601 Wireless Communication and Networks Unit - V
Caching
quite often disabled by information providers to be able to create user profiles, usage statistics etc.
dynamic objects cannot be cached
o numerous counters, time, date, personalization, ...
mobility quite often inhibits caches
Security problems
o how to use SSL/TLS together with proxies?
today: many user customized pages, dynamically generated on request via CGI, ASP, ...
POSTing (i.e., sending to a server)
can typically not be buffered, very problematic if currently disconnected
Hyper Text Markup Language (HTML) and Mobile Devices
HTML
o designed for computers with “high” performance, color high-resolution display, mouse, hard disk
o typically, web pages optimized for design, not for communication
Mobile devices
o often only small, low-resolution displays, very limited input interfaces (small touch-pads, soft-keyboards)
Additional “features”
o animated GIF, Java AWT, Frames, ActiveX Controls, Shockwave, movie clips, audio, ...
o many web pages assume true color, multimedia support, high-resolution and many plug-ins
Web pages ignore the heterogeneity of end-systems!
o e.g., without additional mechanisms, large high-resolution pictures would be transferred to a mobile
phone with a low-resolution display causing high costs
Approaches toward WWW for mobile devices
Image scaling
o picture can be scaled down to fewer colors, lower resolution, or to just the title of the picture.
o The user can then decide to download the picture separately.
o Clipping, zooming, or detail studies can be offered to users if they are interested in a part of the picture.
Content transformation
o Postscript or portable document format (PDF) into plain text before transmitting
Content extraction / semantic compression
o headline extraction, automatic abstract generation
Special languages and protocols
o HDML (handheld device markup language):
simple language similar to HTML requiring a special browser
HDTP (handheld device transport protocol): transport protocol for HDML
Push technologies
o Instead of pulling content from a server, the server could also push content to a client
o This avoids the overhead of setting up connections for each item, but is only useful for some content
e.g. news, weather information, road conditions, where users do not have to interact much
Application gateways, enhanced servers
o simple clients, pre-calculations in the fixed network
o compression, filtering, content extraction
o automatic adaptation to network characteristics
Problems
o proprietary approaches, require special enhancements for browsers
o heterogeneous devices make approaches more complicated
HTTP Ver 1.1 Improvements
Connection re-use
o use the same TCP connection for several requests and responses
o Persistent connections are default in 1.1 (keep-alive option in 1.0)
o pipelining : multiple requests
Caching enhancements
MTech CSE (PT, 2011-14) SRM, Ramapuram 7 hcr:innovationcse@gg
CS601 Wireless Communication and Networks Unit - V
o A cache may now also store cacheable responses to reduce response time and bandwidth for future,
equivalent responses
o semantic transparency
o A special tag allows for the identification of content and helps to determine if two different URIs map to
the same content
o defines a large set of cache-control directives
public/private, max-age, no-cache
Bandwidth optimization
o supports compression, negotiation of compression parameters and different compression styles (hop-
by-hop or end-to-end).
o allows for partial transmission of objects (like images)
Security
o comprises further mechanisms to check message
o integrity and to authenticate clients, proxies, and servers
Cookies
o can set up a long-term “session” by storing state upon request
Mobile WWW System Architecture
client/server system
Caching is a major topic in the web client/server scenario
Integrated browser enhancement Additional application supporting
Pre-fetching, caching, off-line use browsing
o e.g. Internet Explorer Pre-fetching, caching, off-line use
o e.g. original WebWhacker
Client proxy as browser support Network proxy as browser support
Pre-fetching, caching, off-line use adaptive content transformation
o e.g., Caubweb, TeleWeb, Weblicator, for bad connections, pre-fetching,
WebWhacker, WebEx, WebMirror, caching
o e.g., TranSend, Digestor
MTech CSE (PT, 2011-14) SRM, Ramapuram 8 hcr:innovationcse@gg
CS601 Wireless Communication and Networks Unit - V
Client and network proxy as browser Client and network proxy with special
support transmission protocol
combination of benefits plus adaptive content transformation
simplified protocols for bad connections, pre-fetching,
o e.g., MobiScape, WebExpress caching
o e.g., Mowgli
WIRELESS APPLICATION PROTOCOL
Goals
o deliver Internet content and enhanced services to mobile devices and users (mobile phones, PDAs)
o independence from wireless network standards
o open for everyone to participate, protocol specifications will be proposed to standardization bodies
o applications should scale well beyond current transport media and device types and should also be
applicable to future developments
Platforms
o e.g., GSM (900, 1800, 1900), CDMA IS-95, TDMA IS-136, 3rd generation systems (IMT-2000, UMTS,
W-CDMA)
Forum
o WAP Forum, co-founded by Ericsson, Motorola, Nokia, Unwired Planet
o further information http://www.wapforum.org
WAP - scope of standardization
Browser
o “micro browser”, similar to existing, well-known browsers in the Internet
Script language
o similar to Java script, adapted to the mobile environment
WTA / WTAI
o Wireless Telephony Application (Interface): access to all telephone functions
Content formats
o e.g., business cards (vCard), calendar events (vCalender)
Protocol layers
o transport layer, security layer, session layer etc.
Working Groups
o WAP Architecture Working Group, WAP Wireless Protocol Working Group, WAP Wireless Security
Working Group, WAP Wireless Application Working Group
WAP Forum / Open Mobile Alliance Specifications must be (ISERS)
Interoperable
o allowing terminals and software from different vendors to communicate with networks from different
providers;
Scaleable
o protocols and services should scale with customer needs and number of customers;
Efficient
MTech CSE (PT, 2011-14) SRM, Ramapuram 9 hcr:innovationcse@gg
CS601 Wireless Communication and Networks Unit - V
o provision of QoS suited to the characteristics of the wireless and mobile networks;
Reliable
o provision of a consistent and predictable platform for deploying services
Secure
o preservation of the integrity of user data, protection of devices and services from security problems.
WAP Architecture
Components and interface of the WAP 1.x architecture
GSM: Global System for Mobile communication
HSCSD : High-Speed Circuit Switched Data
GPRS: General Packet Radio Service
WDP: Wireless Datagram Protocol
WCMP : Wireless Control Message Protocol
T-SAP : Transport Layer Service Access Point
WTLS : Wireless Transport Layer Security
SEC-SAP: SECurity SAP
WTP: Wireless Transaction Protocol
TR-SAP: Transaction SAP
WSP: Wireless Session Protocol
S-SAP: Session-SAP
WAE: Wireless Application Environment
WML: Wireless Markup Language
Bearer services
The basis for transmission of data is formed by different bearer services
Examples:
SMS, HSCSD, GPRS, CDPD, IS-136, PHS
No special interface has been specified between the bearer service and the next higher layer
Transport layer
Has wireless datagram protocol (WDP) and the additional wireless control message protocol (WCMP)
offers a bearer independent, consistent datagram-oriented service
Communication is done transparently over one of the available bearer services
Transport Layer Service Access Point (T-SAP) is the common interface to be used by higher layers
independent of the underlying network
Security layer
wireless transport layer security protocol WTLS offers its service at the security SAP (SEC-SAP).
WTLS is based on the transport layer security
MTech CSE (PT, 2011-14) SRM, Ramapuram 10 hcr:innovationcse@gg
CS601 Wireless Communication and Networks Unit - V
optimized for use in wireless networks with narrow-band channels
offer data integrity, privacy, authentication, and (some) denial-of-service protection
Transaction Layer
uses wireless transaction protocol (WTP)
offers a lightweight transaction service at the transaction SAP (TR-SAP).
This service efficiently provides reliable or unreliable requests and asynchronous transactions
Session layer
uses wireless session protocol (WSP)
offers two services at the session-SAP (S-SAP),
o one connection-oriented
o one connectionless if used directly on top of WDP.
A special service for browsing the web (WSP/B) has been defined that offers
o HTTP/1.1 functionality,
o long-lived session state,
o session suspend and resume,
o session migration
o other features needed for wireless mobile access to the web.
Application layer
wireless application environment (WAE)
offers a framework for the integration of different www and mobile telephony applications
offers many protocols and services with special service access points
Integration of WAP components
To be able to browse these pages or additional pages with handheld devices, a wireless markup language
(WML) has been defined in WAP.
Special filters within the fixed network can now translate HTML into WML, web servers can already provide
pages in WML, or the gateways between the fixed and wireless network can translate HTML into WML.
These gateways also act as proxies for web access
WML is additionally converted into binary WML for more efficient transmission
a special gateway can be implemented to access traditional telephony services via binary WML.
This wireless telephony application (WTA) server translates, e.g., signaling of the telephone network
(incoming call etc.) into WML events displayed at the handheld device.
Wireless Datagram Protocol (WDP)
Protocol of the transport layer within the WAP architecture
o uses directly transports mechanisms of different network technologies
o offers a common interface for higher layer protocols
o allows for transparent communication using different transport technologies
Goals of WDP
o create a worldwide
interoperable transport
system with the help of WDP
adapted to the different
underlying technologies
o transmission services such
as SMS in GSM might
change, new services can
replace the old ones
WDP service primitives
WDP offers source and
destination port numbers used for
multiplexing and demultiplexing of
data respectively
MTech CSE (PT, 2011-14) SRM, Ramapuram 11 hcr:innovationcse@gg
CS601 Wireless Communication and Networks Unit - V
The service primitive to send a datagram is TDUnitdata.req with
o the destination address (DA), destination port (DP), Source address (SA), source port (SP), and user
data (UD) as mandatory parameters
The T-DUnitdata.ind service primitive indicates the reception of data
error is indicated with the T-DError.ind service primitive
o error code (EC) is returned indicating the reason for the error to the higher layer
Wireless Control Message Protocol (WCMP)
provides error handling mechanisms for WDP
Typical WCMP messages are
o destination unreachable (route, port, address unreachable),
o parameter problem (errors in the packet header),
o message too big,
o reassembly failure
o echo request/reply
Wireless Transport Layer Security (WTLS)
Goals
o data integrity
prevention of changes in data
o privacy
prevention of tapping
o authentication
creation of authenticated relations between a mobile device and a server
o protection against denial-of-service attacks
protection against repetition of data and unverified data
WTLS
o is based on the TLS (Transport Layer Security) protocol (former SSL, Secure Sockets Layer)
o optimized for low-bandwidth communication channels
WTLS Establishing A Secure Session
The first step is to initiate the session with the SEC-Create primitive.
MTech CSE (PT, 2011-14) SRM, Ramapuram 12 hcr:innovationcse@gg
CS601 Wireless Communication and Networks Unit - V
Parameters are source address (SA), source port (SP) of the originator, destination address (DA),
destination port (DP) of the peer.
The originator proposes
o a key exchange suite (KES) (e.g., RSA , DH ,ECC ),
o a cipher suite (CS) (e.g., DES, IDEA)
o a compression method (CM)
The peer answers with parameters for the sequence number mode (SNM),
o the key refresh cycle (KR),
o the session identifier (SID) (which is unique with each peer),
o the selected key exchange suite (KES’), cipher suite (CS’), compression method (CM’).
The peer also issues a SEC-Exchange primitive.
o This indicates that the peer wishes to perform public-key authentication with the client, i.e., the peer
requests a client certificate (CC) from the originator
The originator answers with its certificate and issues a SEC-Commit.req primitive.
This primitive indicates that the handshake is completed
WTLS Datagram Transfer
After setting up a secure connection between two peers, user data can be exchanged.
This is done using the simple SEC-Unitdata primitive
Wireless Transaction Protocol
Goals
o different transaction services, offloads applications
application can select reliability, efficiency
o support of different communication scenarios
class 0: unreliable message transfer
class 1: reliable message transfer without result message
class 2: reliable message transfer with exactly one reliable result message
o supports peer-to-peer, client/server and multicast applications
o low memory requirements, suited to simple devices (< 10kbyte )
o efficient for wireless transmission
segmentation/reassembly
selective retransmission
header compression
optimized connection setup (setup with data transfer)
The three service primitives offered by WTP are
o TR-Invoke to initiate a new transaction,
o TR-Result to send back the result of a previously initiated transaction
o TR-Abort to abort an existing transaction
The PDUs exchanged between two WTP entities for normal transactions are the
o invoke PDU,
o ack PDU
o result PDU.
A special feature of WTP is its ability to provide a user acknowledgement or, alternatively, an automatic
acknowledgement by the WTP entity
MTech CSE (PT, 2011-14) SRM, Ramapuram 13 hcr:innovationcse@gg
CS601 Wireless Communication and Networks Unit - V
WTP Class 0
Class 0 offers an unreliable transaction service without a result message.
The transaction is stateless and cannot be aborted.
The service is requested with the TR-Invoke.req primitive
Parameters are the source address (SA), source port (SP), destination address (DA), destination port (DP
the A flag the user of this service can determine, if the responder WTP entity should generate an
acknowledgement or if a user acknowledgement should be used.
The WTP layer will transmit the user data (UD) transparently to its destination.
The class type C indicates here class 0.
the transaction handle H provides a simple index to uniquely identify the transaction
o an alias for the tuple (SA, SP, DA, DP)
The WTP entity at the responder then generates a TR-Invoke.ind primitive
H’ is the local handle for the transaction on the responder’s side
WTP Class 1
WTP class 2: Basic transaction, no user acknowledgement
MTech CSE (PT, 2011-14) SRM, Ramapuram 14 hcr:innovationcse@gg
CS601 Wireless Communication and Networks Unit - V
WTP class 2: Basic transaction, with user Acknowledgement
WTP class 2 transaction with “hold on”, no user acknowledgement
Wireless Session Protocol (WSP)
Goals
o HTTP 1.1 functionality
o Request/reply, content type negotiation, ...
o support of client/server, transactions, push technology
o key management, authentication, Internet security services
o session management (interruption, resume,...)
Services
o session management (establish, release, suspend, resume)
o capability negotiation
o content encoding
WSP/B (Browsing)
o HTTP/1.1 functionality - but binary encoded
o exchange of session headers
o push and pull data transfer
o asynchronous requests
MTech CSE (PT, 2011-14) SRM, Ramapuram 15 hcr:innovationcse@gg
CS601 Wireless Communication and Networks Unit - V
WSP/B session establishment
server address (SA), client address (CA), client header (CH), requested capabilities (RC), server header (SH),
negotiated capabilities (NC), reason R
WSP/B session suspension and resume
WSP/B session termination
MTech CSE (PT, 2011-14) SRM, Ramapuram 16 hcr:innovationcse@gg
CS601 Wireless Communication and Networks Unit - V
WSP/B completed transaction
client transaction identifier CTID, method M, request URI RU, server transaction identifier STID, status (S),
response header (RH), response body (RB)
WSP utilization of WTP as lower layer
WSP/B asynchronous, unordered requests
Push primitives
a server can push data towards a client if allowed
push header (PH), push body (PB), server push identifier (SPID), client push identifier (CPID)
WSP/B non-confirmed push
WSP/B confirmed push
MTech CSE (PT, 2011-14) SRM, Ramapuram 17 hcr:innovationcse@gg
CS601 Wireless Communication and Networks Unit - V
Wireless Application Environment (WAE)
Goals
o network independent application environment for low-bandwidth, wireless devices
o integrated Internet/WWW programming model with high interoperability
Requirements
o device and network independent, international support
o manufacturers can determine look-and-feel, user interface
o considerations of slow links, limited memory, low computing power, small display, simple user interface
(compared to desktop computers)
Components
o architecture: application model, browser, gateway, server
o WML: XML-Syntax, based on card stacks, variables, ...
o WMLScript: procedural, loops, conditions, ... (similar to JavaScript)
o WTA: telephone services, such as call control, text messages, phone book, ... (accessible from
WML/WMLScript)
o content formats: vCard, vCalendar, Wireless Bitmap, WML, ...
WAE logical model
Wireless Markup Language (WML)
WML follows deck and card metaphor
o WML document consists of many cards, cards are grouped to decks
o a deck is similar to an HTML page, unit of content transmission
o WML describes only intent of interaction in an abstract manner
o presentation depends on device capabilities
Features
o text and images
o user interaction
o navigation
o context management
WML Example
<WML>
<CARD>
<DO TYPE="ACCEPT">
<GO URL="#card_two"/>
</DO>
This is a simple first card!
On the next you can choose ...
</CARD>
<CARD NAME="card_two">
... your favorite pizza:
MTech CSE (PT, 2011-14) SRM, Ramapuram 18 hcr:innovationcse@gg
CS601 Wireless Communication and Networks Unit - V
<SELECT KEY="PIZZA">
<OPTION VALUE=”M”>Margherita</OPTION>
<OPTION VALUE=”F”>Funghi</OPTION>
<OPTION VALUE=”V”>Vulcano</OPTION>
</SELECT>
</CARD>
</WML>
WMLScript
Complement to WML
Provides general scripting capabilities
Features
o validity check of user input
check input before sent to server
o access to device facilities
hardware and software (phone call, address book etc.)
o local user interaction
interaction without round-trip delay
o extensions to the device software
configure device, download new functionality after deployment
Example:
function pizza_test(pizza_type) {
var taste = "unknown";
if (pizza_type = "Margherita") {
taste = "well... ";
}
else {
if (pizza_type = "Vulcano") {
taste = "quite hot";
};
};
return taste;
};
Wireless Telephony Application (WTA)
Collection of telephony specific extensions
Extension of basic WAE application model
o content push
server can push content to the client
client may now be able to handle unknown events
o handling of network events
table indicating how to react on certain events from the network
o access to telephony functions
any application on the client may access telephony functions
Example
o calling a number (WML)
wtai://wp/mc;07216086415
o calling a number (WMLScript)
WTAPublic.makeCall("07216086415");
MTech CSE (PT, 2011-14) SRM, Ramapuram 19 hcr:innovationcse@gg
CS601 Wireless Communication and Networks Unit - V
WTA logical architecture
WTA example: voice message
WAP push architecture with proxy gateway
Comments & Feedback
Thanks to my family members who supported me while I spent hours and hours to prepare this.
Your feedback is welcome at GHCRajan@gmail.com
MTech CSE (PT, 2011-14) SRM, Ramapuram 20 hcr:innovationcse@gg
You might also like
- Mobile TCPDocument7 pagesMobile TCPTUSHARNo ratings yet
- Directorate of Technical Education, Tamilnadu: Thanthai Periyar Government Institute of Technology, Vellore-632002Document22 pagesDirectorate of Technical Education, Tamilnadu: Thanthai Periyar Government Institute of Technology, Vellore-632002Karthick RaajNo ratings yet
- MC Unit 4Document28 pagesMC Unit 4Naveenkumar TariNo ratings yet
- Indirect TCP, Snooping TCP, Mobile TCP - Mobile Transport LayerDocument12 pagesIndirect TCP, Snooping TCP, Mobile TCP - Mobile Transport LayerMukesh91% (220)
- Mobile Transport Layer MechanismsDocument15 pagesMobile Transport Layer MechanismsAditya SinghNo ratings yet
- TCPFor WirelessDocument16 pagesTCPFor WirelessZack StormNo ratings yet
- TCP For Wireless NetworksDocument16 pagesTCP For Wireless NetworksAnbarasan TRNo ratings yet
- Mobile TCP protocols optimize performance for wireless networksDocument22 pagesMobile TCP protocols optimize performance for wireless networksSri Tulasi100% (1)
- Unit Iii MC Mobile Transport Layer Part 4Document7 pagesUnit Iii MC Mobile Transport Layer Part 4SLDFLAGNo ratings yet
- Mobile Communications Chapter 10: Mobile Transport LayerDocument15 pagesMobile Communications Chapter 10: Mobile Transport LayerImranNo ratings yet
- Unit 5Document26 pagesUnit 5ashwani tyagiNo ratings yet
- Unit 5 Final NotesDocument20 pagesUnit 5 Final Notesappsectesting3No ratings yet
- Transport Layer ProtocolDocument28 pagesTransport Layer ProtocolShivanisAccountNo ratings yet
- Unit IV Mobile Transport LayerDocument10 pagesUnit IV Mobile Transport LayerShradha PandeyNo ratings yet
- Mobile TCP Optimization for Reliable Transport Layer CommunicationsDocument18 pagesMobile TCP Optimization for Reliable Transport Layer Communicationschandra100% (1)
- Mobile TCP Transport Layer OptimizationDocument18 pagesMobile TCP Transport Layer OptimizationArulNo ratings yet
- Mod. 3.3 Indirect TCP, Snooping TCP, Mobile TCPDocument18 pagesMod. 3.3 Indirect TCP, Snooping TCP, Mobile TCPkhanvilkarshruti6No ratings yet
- Mobile TCP improvements for efficient data transportDocument28 pagesMobile TCP improvements for efficient data transportGanesh KumarNo ratings yet
- Unit IiDocument9 pagesUnit Iimoneeranaaz11No ratings yet
- 4444.... Mobile Transport Layer Mobile Transport Layer Mobile Transport Layer Mobile Transport LayerDocument16 pages4444.... Mobile Transport Layer Mobile Transport Layer Mobile Transport Layer Mobile Transport LayerDr. Sashi Kanth Reddy ANo ratings yet
- Transport Layer Challenges By: Talha Mudassar 015 Fahad Nabi 63 Rashid Mehmood 96Document6 pagesTransport Layer Challenges By: Talha Mudassar 015 Fahad Nabi 63 Rashid Mehmood 96Noman AliNo ratings yet
- 2010 MC1633 (1) MTLDocument32 pages2010 MC1633 (1) MTLjavednjavedNo ratings yet
- Rejinpaul MC UNIT4Document27 pagesRejinpaul MC UNIT4SENTHIL VNo ratings yet
- Mobile TCP: Optimizing TCP for Wireless NetworksDocument27 pagesMobile TCP: Optimizing TCP for Wireless NetworksMfleh MflehNo ratings yet
- Implications On Mobility PDFDocument4 pagesImplications On Mobility PDFNabilaNo ratings yet
- Mobile Transport LayerDocument15 pagesMobile Transport LayerAshish SharmaNo ratings yet
- Unit Iii: Transport LayerDocument47 pagesUnit Iii: Transport Layerg ezhilNo ratings yet
- MC CH-3Document25 pagesMC CH-3faayaoromoo14No ratings yet
- C09 Transport ProtocolsDocument19 pagesC09 Transport ProtocolsAndes HarahapNo ratings yet
- Traditional TCP: Unit-4: Mobile Transport LayerDocument30 pagesTraditional TCP: Unit-4: Mobile Transport LayerAaj JjaNo ratings yet
- TCP Over Wireless: Dr. RitikaDocument53 pagesTCP Over Wireless: Dr. RitikamonumunduriNo ratings yet
- A Comparison of Techniques For Improving TCP Performance Over Wireless LinksDocument4 pagesA Comparison of Techniques For Improving TCP Performance Over Wireless LinksMuthu Vijay DeepakNo ratings yet
- Mobile Transport LayerDocument18 pagesMobile Transport LayervalansterNo ratings yet
- Mobile IP performance and optimizationsDocument8 pagesMobile IP performance and optimizationsBintang Mandala PutraNo ratings yet
- C09 Transport ProtocolsDocument18 pagesC09 Transport ProtocolsSenthil RNo ratings yet
- Opnetwork03 WanDocument7 pagesOpnetwork03 WanHán LaNo ratings yet
- Mobile Transport LayerDocument43 pagesMobile Transport LayerPoli Markova0% (1)
- Mobile Transport Layer & Ad Hoc NetworkingDocument38 pagesMobile Transport Layer & Ad Hoc NetworkingaishwaryaNo ratings yet
- Mobile Communications Chapter 9: Mobile Transport Layer: Additional OptimizationsDocument23 pagesMobile Communications Chapter 9: Mobile Transport Layer: Additional OptimizationsVidya ANo ratings yet
- Snooping TCP As A Transparent TCP ExtensionDocument2 pagesSnooping TCP As A Transparent TCP ExtensionKrishanu ModakNo ratings yet
- Transport Layer: Example: HTTP (Used by Web Services)Document5 pagesTransport Layer: Example: HTTP (Used by Web Services)satmeher5279No ratings yet
- Unit 4Document14 pagesUnit 4126 Kavya sriNo ratings yet
- C08 Transport ProtocolsDocument19 pagesC08 Transport ProtocolsraghuippiliNo ratings yet
- Mobile TCP and WAP protocolsDocument70 pagesMobile TCP and WAP protocolsIliyas AhamedNo ratings yet
- A Throughput Analysis of TCP in ADHOC NetworksDocument8 pagesA Throughput Analysis of TCP in ADHOC NetworksCS & ITNo ratings yet
- مصطفى نتوورك PDFDocument9 pagesمصطفى نتوورك PDFBassam AlmunagemNo ratings yet
- Transport Layer Protocols For Ad-Hoc NetworksDocument29 pagesTransport Layer Protocols For Ad-Hoc NetworksShachi P GowdaNo ratings yet
- A Solution For Improving TCP Performance Over Wireless LinksDocument12 pagesA Solution For Improving TCP Performance Over Wireless LinksBirsh EndawkieNo ratings yet
- Mobile Transport Layer Implications On MobilityDocument4 pagesMobile Transport Layer Implications On MobilityrosmyNo ratings yet
- TCP Modifications for Wireless NetworksDocument30 pagesTCP Modifications for Wireless NetworksMurugan Antham RNo ratings yet
- Mobile Communications Chapter 9: Mobile Transport LayerDocument13 pagesMobile Communications Chapter 9: Mobile Transport Layernero neroNo ratings yet
- C09-Transport ProtocolsDocument18 pagesC09-Transport ProtocolsArul JothiNo ratings yet
- Mobile Communications Mobile Transport LayerDocument18 pagesMobile Communications Mobile Transport LayerChaudhary AdnanNo ratings yet
- Mobile TCP: Made by Sarika Aher, Anagha Bagul & Faihzan ShaikhDocument15 pagesMobile TCP: Made by Sarika Aher, Anagha Bagul & Faihzan ShaikhFaihzan F Ahmad ShaikhNo ratings yet
- Priority TX in 802 - 11Document19 pagesPriority TX in 802 - 11Manuel ChawNo ratings yet
- Mobile Transport Layer OptimizationDocument18 pagesMobile Transport Layer OptimizationMunivel EllappanNo ratings yet
- CN Ass 3 SolnDocument10 pagesCN Ass 3 SolnNoobs RageNo ratings yet
- Introduction to Internet & Web Technology: Internet & Web TechnologyFrom EverandIntroduction to Internet & Web Technology: Internet & Web TechnologyNo ratings yet
- 2024-03-16Document6 pages2024-03-16robertyroberty354No ratings yet
- SG 8Document2 pagesSG 8sindhu67% (6)
- Bits Pilani, Dubai CampusDocument11 pagesBits Pilani, Dubai CampussatyaNo ratings yet
- Digital Marketing: Submitted By: Rakesh Kumar Raushan REG. NO. - 1233300006/12Document100 pagesDigital Marketing: Submitted By: Rakesh Kumar Raushan REG. NO. - 1233300006/12Vipul DesaiNo ratings yet
- Java Magazine JUnit 5 ArrivesDocument75 pagesJava Magazine JUnit 5 ArrivesWesley RamosNo ratings yet
- IPPBX-Upgrade Manual R V3.0-D20140319-EN PDFDocument11 pagesIPPBX-Upgrade Manual R V3.0-D20140319-EN PDFDavid OparindeNo ratings yet
- 08-DOM Manipulation and JqueryDocument52 pages08-DOM Manipulation and JqueryIgor KalganovNo ratings yet
- Cambridge IGCSE™: Information and Communication Technology 0417/13 May/June 2022Document15 pagesCambridge IGCSE™: Information and Communication Technology 0417/13 May/June 2022ilovefettuccineNo ratings yet
- FTK-ProjectDocument15 pagesFTK-ProjectSelina KyleNo ratings yet
- Azpen A727 Tablet User GuideDocument20 pagesAzpen A727 Tablet User GuideMetalBreathNo ratings yet
- SIP Server Configuration GuideDocument33 pagesSIP Server Configuration GuideHassamNo ratings yet
- Resume 79ea342f148df4d9452dDocument1 pageResume 79ea342f148df4d9452dMD ASIF ALAMNo ratings yet
- Excel For MAC Quick Start GuideDocument4 pagesExcel For MAC Quick Start GuideMalaquías HuamánNo ratings yet
- Dns BigDocument2,194 pagesDns BigZoro ShresthaNo ratings yet
- Changelog OpenXava 5.8.1Document54 pagesChangelog OpenXava 5.8.1jamesdeavoloNo ratings yet
- Online Student Bus Pass SystemDocument38 pagesOnline Student Bus Pass SystemMouni Doll1067% (3)
- 400.05.PM.03 - Predictive Maintenance - V - 0.1Document39 pages400.05.PM.03 - Predictive Maintenance - V - 0.1Neeraj TiwariNo ratings yet
- Transport Phenomena Fundamentals PDFDocument2 pagesTransport Phenomena Fundamentals PDFAnonymous RDOwEc0% (2)
- Lập Kế Hoạch Và Theo Dõi Chiến Dịch Marketing EmailDocument10 pagesLập Kế Hoạch Và Theo Dõi Chiến Dịch Marketing EmailLoc HoangNo ratings yet
- Bluetooth Programming With Python 3: The Two OptionsDocument5 pagesBluetooth Programming With Python 3: The Two OptionsHemant HomkarNo ratings yet
- How To Cancel Your Premium Membership: Scribd Help CenterDocument4 pagesHow To Cancel Your Premium Membership: Scribd Help CenterTulika BoseNo ratings yet
- SD APracticalGuide WhitePaper-1Document25 pagesSD APracticalGuide WhitePaper-1Antonio AguilarNo ratings yet
- Test Guide TapnationDocument12 pagesTest Guide TapnationZied SioudNo ratings yet
- Artifi Cial Intelligence: G. KonidarisDocument76 pagesArtifi Cial Intelligence: G. KonidarisjannNo ratings yet
- Summer Project SEO GuideDocument16 pagesSummer Project SEO GuideFarhan Rahman rBUzaKPhwpNo ratings yet
- RRL DocumentsDocument6 pagesRRL DocumentsMary Joy VillacrusisNo ratings yet
- Social media addiction causes and effectsDocument36 pagesSocial media addiction causes and effectsMa. Cheska Kaye BendalNo ratings yet
- Online Complaint Management System For Ambo UniversityDocument63 pagesOnline Complaint Management System For Ambo UniversityMubarek HusenNo ratings yet
- Lyric User Guide v5pt0 2A02203PDF RevADocument1,174 pagesLyric User Guide v5pt0 2A02203PDF RevAMundo IPTV50% (2)
- CE4525 4.0v1 Getting Started With Sophos Central XDR Live DiscoverDocument22 pagesCE4525 4.0v1 Getting Started With Sophos Central XDR Live DiscoverAlcibiades MachadoNo ratings yet