100% found this document useful (1 vote)
1K views13 pagesFortiGate HA Config
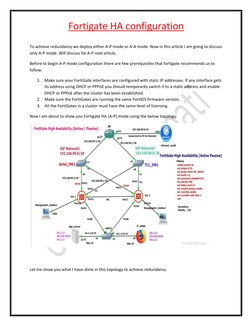
1. The document discusses configuring FortiGate high availability (HA) in active-passive mode using two FortiGate firewalls.
2. Key prerequisites for HA configuration include ensuring interfaces have static IPs, FortiGates have the same firmware version, and matching licenses.
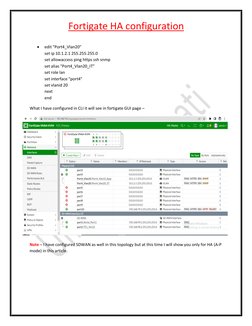
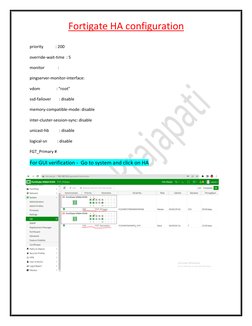
3. The topology shown has the FortiGates configured in active-passive HA mode with interfaces for management, HA heartbeat, and each VLAN. Configuration of interfaces, HA, and necessary routing protocols is explained.
Uploaded by
Be yoUrs BUCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd
100% found this document useful (1 vote)
1K views13 pagesFortiGate HA Config
1. The document discusses configuring FortiGate high availability (HA) in active-passive mode using two FortiGate firewalls.
2. Key prerequisites for HA configuration include ensuring interfaces have static IPs, FortiGates have the same firmware version, and matching licenses.
3. The topology shown has the FortiGates configured in active-passive HA mode with interfaces for management, HA heartbeat, and each VLAN. Configuration of interfaces, HA, and necessary routing protocols is explained.
Uploaded by
Be yoUrs BUCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd