Professional Documents
Culture Documents
Basic PDF Word Document Analysis
Uploaded by
The Hungry QuokkaOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
Basic PDF Word Document Analysis
Uploaded by
The Hungry QuokkaCopyright:
Available Formats
Lab: Investigating Malicious PDF: Analysis
Goals
- Learn how to profile and examine a PDF file and be able to tell
whether it’s malicious or not.
- Use various tools to statically analyze a PDF file and determine
the PDF’s file content
- Extract and analyze suspicious objects
Scenario
- You are a forensic examiner in a large firm. John Kim, A
colleague of yours from HR department received two resumes for an
open position within the firm.
- John Kim viewed the resumes and listed the senders as possible
candidates. Linda.pdf & Lucy.pdf
- Few days later, the firewall administrator noticed a strange
connection going from John Kim’s machine to outside the network.
- Check the 2 resumes and identify the maliciousness of the files.
Requirements
- Windows VM – CDTH Analyst
- Pyid
- PDF_Parser
- exiftool
- Linda.pdf | Lucy2.pdf
GUIDEM I.T. TRAINING CENTER INVESTIGATING MALICIOUS PDF: ANALYSIS 1 | PAGE
Walkthrough
1. Setting up the Lab Environment
- Check if the files are all in the same folder:
- C:\Users\IEUser\Desktop\Lab Files\Day3\PDF
- Make sure you have the following tools to investigate PDF. Check
the Flare folders and you should have the following tools:
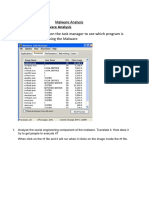
2. Obtain General Overview of the Suspicious PDF Files
- We start off by running the PDFID.py script on each file of the
suspected PDFs, as follows.
- Make sure your PDF files and tools are all residing into one
folder.
- The results will be similar to the following:
GUIDEM I.T. TRAINING CENTER INVESTIGATING MALICIOUS PDF: ANALYSIS 2 | PAGE
Linda.pdf
Lucy2.pdf
GUIDEM I.T. TRAINING CENTER INVESTIGATING MALICIOUS PDF: ANALYSIS 3 | PAGE
- Notice how running the tool on different files returns different
results. The big difference between the number of objects is the
first thing we notice.
- The second file (Lucy2.pdf) contains a Javascript object!
- This is interesting and suspicious at the same time since resume
file has very little use of JavaScript. Something we can tell is
that even though the two files are similar in structure and
format, the other one doesn’t contain Javascript objects.
3. Extract the Files Metadata
- It is worth trying to extract both files’ metadata and see if we
can find anything useful within. We can use exiftool once again
as follows.
- Linda.pdf
GUIDEM I.T. TRAINING CENTER INVESTIGATING MALICIOUS PDF: ANALYSIS 4 | PAGE
Lucy2.pdf
- One thing we noticed here is that Lucy2’s file contains less
metadata
- On the other hand, Linda’s file seems like a template that has
been downloaded from a website.
- This adds another question mark on Lucy’s file, in addition to
the existence of JavaScript object.
4. List the Objects in the Malicious File
- We can use the pdf_parser.py script to perform a more in-depth
analysis of the pdf file.
- By now we have a good reason to suspect Lucy2’s file. So, we’ll
continue our in-depth analysis against it.
- We’ll first start by a general examination using the --stats
option.
GUIDEM I.T. TRAINING CENTER INVESTIGATING MALICIOUS PDF: ANALYSIS 5 | PAGE
pdf-parser.py Lucy2.pdf
- The output may seem too large for the console terminal to show,
so it may be better to redirect the output to another text file
using the “>” symbol.
- The most distinguishable difference between the two files is that
Lucy’s contains a Javascript object which is typically used by
attackers to deliver malicious payloads
- It would be a good idea to search for that specific object and
extract it for further analysis.
- We can search for the Javascript reference within the file using
the –search Javascript option.
- pdf-parser.py --search Javascript Lucy2.pdf
- It will produce the same result but more specific to that object
and search filter that you put.
GUIDEM I.T. TRAINING CENTER INVESTIGATING MALICIOUS PDF: ANALYSIS 6 | PAGE
5. Preparing the Extracted Object for Analysis
- Sometimes an attacker tries to make your life harder by
compressing or obfuscating the hidden payload
- In order to be able to read it and fully analyze the malicious
code, we may need to decompress the Javascript content.
- We can do that using the --filter and --raw options.
- We will use the object 148 since we just noticed on the previous
task that a PDF calls cmd.exe for some reason and that’s what we
need to find out.
pdf-parser.py --object=148 --filter --raw Lucy2.pdf
- Even without an in-depth knowledge of Javascript and before
starting the malicious code analysis, we can see that something
is not right.
- Why would a Javascript code, within a PDF file, want to call
cmd.exe for?
GUIDEM I.T. TRAINING CENTER INVESTIGATING MALICIOUS PDF: ANALYSIS 7 | PAGE
6. Extracting the evil code from the object
- Now that we have displayed the code in plain text, it is better
to extract it to separate file to make the analysis easier. We
can do that as before using the “>” symbol after the previous
command.
pdf-parser.py --object=148 --filter --raw Lucy2.pdf > object148.js
pdf-parser.py --object=147 --filter --raw Lucy2.pdf > object147.js
GUIDEM I.T. TRAINING CENTER INVESTIGATING MALICIOUS PDF: ANALYSIS 8 | PAGE
7. Analyzing the Evil Code from the Object
Object147.js
- The first code seems to be saving a file called Lucy on the
victim’s HDD. The nlaunch:0 suggests that there are no programs
being launched for now.
- The second script is even more interesting; The PDF seems to be
launching the CMD.exe from the victim’s machine.
GUIDEM I.T. TRAINING CENTER INVESTIGATING MALICIOUS PDF: ANALYSIS 9 | PAGE
Object 148.js
- This is definitely not something a normal resume would do.
- This behavior indicates a normal phishing campaign that tries to
call cmd.exe to perform certain shell commands. It could be to
download the whole payload from C2 server. It could be to delete
certain files to destroy the system.
GUIDEM I.T. TRAINING CENTER INVESTIGATING MALICIOUS PDF: ANALYSIS 10 | P A G E
You might also like
- Hacking of Computer Networks: Full Course on Hacking of Computer NetworksFrom EverandHacking of Computer Networks: Full Course on Hacking of Computer NetworksNo ratings yet
- PDF Analysis CheatsheetDocument4 pagesPDF Analysis Cheatsheetroot.localhost00No ratings yet
- Analyzing Microsoft Office DocumentsDocument10 pagesAnalyzing Microsoft Office DocumentsThe Hungry QuokkaNo ratings yet
- Extract Hidden Data From PDFDocument2 pagesExtract Hidden Data From PDFNicoleNo ratings yet
- Practical 1Document10 pagesPractical 1tafadzwavictor.chipereNo ratings yet
- Failed To Find PDF File SDFDocument2 pagesFailed To Find PDF File SDFStephenNo ratings yet
- A Pattern Recognition System For Malicious PDF Files DetectionDocument15 pagesA Pattern Recognition System For Malicious PDF Files DetectionReckon IndepthNo ratings yet
- File Analysis Forensics Tools and TechniqueDocument2 pagesFile Analysis Forensics Tools and TechniqueSiddhesh KarekarNo ratings yet
- Malware AnalysisDocument21 pagesMalware AnalysisAyush rawal100% (1)
- PDF MalwareDocument7 pagesPDF MalwareSunil RangaswamyNo ratings yet
- Computer Forensics Based On What I Have Read: Definition of Computer ForensicsDocument4 pagesComputer Forensics Based On What I Have Read: Definition of Computer ForensicsLama Baajour MokdadNo ratings yet
- Welcome To MSIT: Check ListDocument4 pagesWelcome To MSIT: Check ListSuraj NarangNo ratings yet
- Analysing Malicious Microsoft Office and Adobe PDF DocumentsDocument6 pagesAnalysing Malicious Microsoft Office and Adobe PDF DocumentsSanjana chowdaryNo ratings yet
- Fundamentals of Programming AssignmentDocument13 pagesFundamentals of Programming AssignmentMashood AhmadNo ratings yet
- Exploit Js Pdfka IpDocument2 pagesExploit Js Pdfka IpMichaelNo ratings yet
- Lab 3 COMP1475 2018 19Document2 pagesLab 3 COMP1475 2018 19id.xrp.alphaNo ratings yet
- Malware AnalysisDocument15 pagesMalware AnalysisJosue OuattaraNo ratings yet
- Audit PDF / Read PDF With Peepdf - Analyze & Modify PDF FilesDocument2 pagesAudit PDF / Read PDF With Peepdf - Analyze & Modify PDF FilesDongDuongICTNo ratings yet
- Linux System Programming Part 1 - Linux Basics: IBA Bulgaria 2018Document18 pagesLinux System Programming Part 1 - Linux Basics: IBA Bulgaria 2018Калоян ТотевNo ratings yet
- BackdoorDocument15 pagesBackdoortechNo ratings yet
- File HandlingDocument15 pagesFile HandlingMANJUBASHINI.B MIT-AP/CSENo ratings yet
- File PdfboxDocument2 pagesFile PdfboxMatthewNo ratings yet
- eCXD Labs PDFDocument285 pageseCXD Labs PDFRachid Moyse PolaniaNo ratings yet
- Analyzing Malicious Document FilesDocument1 pageAnalyzing Malicious Document Filesmaria jesus gonzalez torresNo ratings yet
- Practical LinuxDocument62 pagesPractical LinuxIsha TripathiNo ratings yet
- 21.2.11 Lab - Encrypting and Decrypting Data Using A Hacker ToolDocument5 pages21.2.11 Lab - Encrypting and Decrypting Data Using A Hacker ToolGee CloudNo ratings yet
- Data Files and Storage (Internal/External Storage) Smart Application DevelopmentDocument21 pagesData Files and Storage (Internal/External Storage) Smart Application DevelopmentDr-Adeel AsgharNo ratings yet
- Exploit PDF 51Document2 pagesExploit PDF 51JessicaNo ratings yet
- Lab 2Document5 pagesLab 2Vadim CiubotaruNo ratings yet
- Ilovepdf MergedDocument12 pagesIlovepdf MergedjercemesquivelNo ratings yet
- Malicious Activity Detection 1697702706Document13 pagesMalicious Activity Detection 1697702706Rishabh JoshiNo ratings yet
- Readme ZyboDocument2 pagesReadme Zyboyassinema1992No ratings yet
- A4 Resume ParserDocument1 pageA4 Resume ParserMunthitra ThadthapongNo ratings yet
- Expose Redacted PDF InformationDocument2 pagesExpose Redacted PDF InformationMoisesNo ratings yet
- 01 Enisa Network Forensics ToolsetDocument32 pages01 Enisa Network Forensics ToolsetMorion BortaNo ratings yet
- Internet Security CheatsheetsDocument8 pagesInternet Security CheatsheetsdinoNo ratings yet
- Corrupt Files - Prof CDocument10 pagesCorrupt Files - Prof CHarley QuinnNo ratings yet
- MOBISEC 2020 - 05 - Real-World Android AppsDocument22 pagesMOBISEC 2020 - 05 - Real-World Android AppsaaaaaaNo ratings yet
- "Hacking With Metasploit" TutorialDocument18 pages"Hacking With Metasploit" TutorialDaniel E. RamosNo ratings yet
- Filetype PDF Intex Google HackingDocument1 pageFiletype PDF Intex Google HackingVictoria100% (1)
- Medium-Com-@peacefDocument8 pagesMedium-Com-@peacefkurashNo ratings yet
- FAQ PreWorkDocument6 pagesFAQ PreWorkShehroz KhanNo ratings yet
- SANS Analysing Malicious Docs Cheat SheetDocument1 pageSANS Analysing Malicious Docs Cheat SheetagnaldooliNo ratings yet
- Cyber Defense Forensic Analyst - Real World Hands-On ExamplesDocument17 pagesCyber Defense Forensic Analyst - Real World Hands-On ExamplesSandeep Kumar SeeramNo ratings yet
- Hack Like A Pro - How To Embed A Backdoor Connection in An Innocent-Looking PDF Null ByteDocument27 pagesHack Like A Pro - How To Embed A Backdoor Connection in An Innocent-Looking PDF Null ByteDarthFerenczyNo ratings yet
- Analyzing Data Using Python - Importing, Exporting, Analyzing Data With PandasDocument50 pagesAnalyzing Data Using Python - Importing, Exporting, Analyzing Data With Pandasmartin napangaNo ratings yet
- Penetration Testing of Password Protected DocumentsDocument22 pagesPenetration Testing of Password Protected DocumentsulrichkomnNo ratings yet
- Cortex Hands On Investigation and Threat Hunting WorkshopDocument57 pagesCortex Hands On Investigation and Threat Hunting Workshopdbf75No ratings yet
- Python PDF 2: Writing and Manipulating A PDF With Pypdf2 and ReportlabDocument22 pagesPython PDF 2: Writing and Manipulating A PDF With Pypdf2 and ReportlabDuh HuhNo ratings yet
- Filetype PDF ActionscriptDocument2 pagesFiletype PDF ActionscriptTrudellNo ratings yet
- Remote and Local File Inclusion ExplainedDocument6 pagesRemote and Local File Inclusion Explainedanon-4476100% (2)
- Digital Forensics With Kali Lin - Shiva v. N. ParasramDocument536 pagesDigital Forensics With Kali Lin - Shiva v. N. ParasramstroganovborisNo ratings yet
- EHDF Ut2Document12 pagesEHDF Ut2Faizal KhanNo ratings yet
- Linux Basic CommandsDocument34 pagesLinux Basic CommandsBrasil TerraplanistaNo ratings yet
- MR YARN - Lab 2 - Cloud - Updated-V2.0Document22 pagesMR YARN - Lab 2 - Cloud - Updated-V2.0bender1686No ratings yet
- Investigating Windows 10Document6 pagesInvestigating Windows 10api-545804212No ratings yet
- SIN UD1 Activities ENGDocument3 pagesSIN UD1 Activities ENGJOSELUISNo ratings yet
- Explorer PDF Generation Information Disclosure VulnerabilityDocument2 pagesExplorer PDF Generation Information Disclosure VulnerabilityDeniceNo ratings yet
- ITSC203 Lab3bDocument10 pagesITSC203 Lab3bktftj5ydfvNo ratings yet
- Binary FilesDocument10 pagesBinary FilesYashpal MishraNo ratings yet
- Vicomp Blue ReaderDocument14 pagesVicomp Blue ReaderIgi SiviNo ratings yet
- CS441-Lab-04 Node Js BasicsDocument4 pagesCS441-Lab-04 Node Js BasicsMuhammad QubaisNo ratings yet
- Android App DevelopmentDocument26 pagesAndroid App DevelopmentDivyajeet SinghNo ratings yet
- PDF HCP OData Provisioning en USDocument30 pagesPDF HCP OData Provisioning en USsreekanth_seelamNo ratings yet
- Linux 9-16 ExamsDocument14 pagesLinux 9-16 ExamsScribdTranslationsNo ratings yet
- CSS Cheat SheetDocument5 pagesCSS Cheat SheetPeterlogeNo ratings yet
- Dmitri Tsumak BSC ThesisDocument48 pagesDmitri Tsumak BSC Thesismohamed bilhageNo ratings yet
- Jdegtdelete - Allimage/ Jdegtdelete - Allimagekeystr: SyntaxDocument4 pagesJdegtdelete - Allimage/ Jdegtdelete - Allimagekeystr: SyntaxRaveRaveNo ratings yet
- About HTML: Prof. David RossiterDocument8 pagesAbout HTML: Prof. David Rossiterlieth-4No ratings yet
- Breakdown AssistantDocument23 pagesBreakdown AssistantRajat kumarNo ratings yet
- Grade 7 Information TechnologyDocument94 pagesGrade 7 Information Technologysintayhu simeNo ratings yet
- BRKCRS 1452Document90 pagesBRKCRS 1452saqer_11No ratings yet
- Data Sheet 6AV2123-2MB03-0AX0: General InformationDocument9 pagesData Sheet 6AV2123-2MB03-0AX0: General InformationEkanit ChuaykoedNo ratings yet
- Summer Training Report Sample PDFDocument38 pagesSummer Training Report Sample PDFAnita PrasadNo ratings yet
- Building Python Microservices FastapiDocument420 pagesBuilding Python Microservices FastapiJean CarlosNo ratings yet
- TAFJ DistributionDocument11 pagesTAFJ DistributionShaqif Hasan SajibNo ratings yet
- Cheat Sheet - DOM: What Is The DOM?Document3 pagesCheat Sheet - DOM: What Is The DOM?scribd accountNo ratings yet
- Week2 2Document8 pagesWeek2 2Thanh Huyền CaoNo ratings yet
- Updated Manual MWT 2020 5Document87 pagesUpdated Manual MWT 2020 5simNo ratings yet
- Spring Boot Hospital ListDocument25 pagesSpring Boot Hospital ListHemant Kushwaha100% (1)
- ICF 9 1st SummativeDocument2 pagesICF 9 1st Summativeallan tomasNo ratings yet
- Getting Started Documentation: Set Up EnvironmentDocument9 pagesGetting Started Documentation: Set Up EnvironmentAleksNo ratings yet
- R ProgrammingDocument5 pagesR ProgrammingSourav NayakNo ratings yet
- CVE-2020-14882 - Oracle WebLogic Remote Code Execution Vulnerability Exploited in The Wild - Blog - 2020-11-30 - 15-29 - A6151ff9Document933 pagesCVE-2020-14882 - Oracle WebLogic Remote Code Execution Vulnerability Exploited in The Wild - Blog - 2020-11-30 - 15-29 - A6151ff9Alessandro BocchinoNo ratings yet
- Symantec Data Loss Prevention Installation Guide For Linux: Last Updated: September 24, 2020Document105 pagesSymantec Data Loss Prevention Installation Guide For Linux: Last Updated: September 24, 2020artreisNo ratings yet
- Company Overview: IB5k Job Description Full Stack / Ruby DeveloperDocument2 pagesCompany Overview: IB5k Job Description Full Stack / Ruby DeveloperDeneme Deneme AsNo ratings yet
- Subham Chakraborty ResumeDocument1 pageSubham Chakraborty ResumetankuliNo ratings yet
- Lightning and LWC Interview QuestionsDocument9 pagesLightning and LWC Interview QuestionslakshmiumaNo ratings yet
- Akamai Splunk SIEM Splunk ConnectorDocument12 pagesAkamai Splunk SIEM Splunk ConnectorZoumana DiomandeNo ratings yet
- Really Friendly Git IntroDocument26 pagesReally Friendly Git Introscribd1comNo ratings yet