Professional Documents
Culture Documents
XM The ISO 27000 Family of Standards 230516
XM The ISO 27000 Family of Standards 230516
Uploaded by
kenyrOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
XM The ISO 27000 Family of Standards 230516
XM The ISO 27000 Family of Standards 230516
Uploaded by
kenyrCopyright:
Available Formats
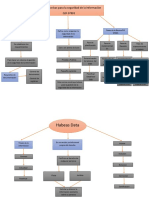
ISO 27001 Information security management systems (ISMS).
Requirements
ISO 27002 Information security controls
ISO 27005 Guidance on managing information security risks
ISO 27007 Guidelines for information security management systems auditing
se of ISO/IEC 27001 family of standards in
U
ISO 27024
Governmental / Regulatory requirements
ISO 27009 Sector-specific application of ISO/IEC 27001 — Requirements
dditional document for ISO/IEC 27002 and
a
??? ISO 27029 ISO 27011 Information security controls based on ISO/IEC 27002 for telecommunications organizations
ISO and IEC standards
Big data security and privacy — Processes ISO 27045 Other ISO 27013 Guidance on the integrated implementation of ISO/IEC 27001 and ISO/IEC 20000-1
Big data security and privacy — Implementation guidelines ISO 27046 ISO 27014 Governance of information security
Information security,
ealth informatics — Information security
H cybersecurity and ISO 27028 Guidance on ISO/IEC 27002 attributes
ISO 27799
management in health using ISO/IEC 27002 privacy protection
ISO 27551 Requirements for attribute-based unlinkable entity authentication
ISO 27554 Application of ISO 31000 for assessment of identity-related risk
Part 1: Local modes Security and Privacy requirements ISO 27555 Guidelines on personally identifiable information deletion
ISO 27553 for authentication using
Part 2: Remote modes biometrics on mobile devices ISO 27556 User-centric privacy preferences management framework
Legend ISO 27557 Application of ISO 31000:2018 for organizational privacy risk management
Under development ISO 27559 Privacy enhancing data de-identification framework
Consent record information structure ISO 27560
Important
xtension to ISO/IEC 27001 and ISO/IEC 27002 for privacy information management
E
ISO 27701
Privacy operationalisation model and method for engineering (POMME) ISO 27561 — Requirements and guidelines
Very Important
Privacy guidelines for fintech services ISO 27562 ISO 24745 Biometric information protection
Security and privacy in artificial intelligence use cases
ISO 27563
— Best practices
Guidelines on privacy preservation based on zero knowledge proofs ISO 27565 Requirements for bodies Part 1: General
Privacy providing audit and ISO 27006
Age assurance systems — Framework ISO 27566 Part 2: Privacy information management systems
technologies certification of ISMSs
Privacy guidelines for smart cities ISO 27570
Privacy framework ISO 29100
ISO 27000 Overview and vocabulary
Guidelines for privacy impact assessment ISO 29134
ISO 27003 ISMS. Guidance
Code of practice for personally identifiable information protection ISO 29151
ISO 27004 Monitoring, measurement, analysis and evaluation
Privacy capability assessment model ISO 29190
ISO 27008 Guidelines for the assessment of information security controls
Guidelines ISO 27400 ISO 27010 Information security management for inter-sector and inter-organizational communications
I oT security
Device baseline requirements ISO 27402 ISO 27015 Information security management guidelines for financial services
and privacy
Guidelines for IoT-domotics ISO 27403 he ISO 27000
T ISO 27016 Information security management — Organizational economics
Part 1: Overview and concepts
Family of Standards ode of practice for information security controls
C
ISO 27017
based on ISO/IEC 27002 for cloud services
Part 2: Requirements 16.05.2023 www.patreon.com/AndreyProzorov
Supplier ISO 27018
ode of practice for protection of personally identifiable
C
ISO 27036 information (PII) in public clouds acting as PII processors
Part 3: Guidelines for information and relationships
communication technology supply chain security
ISO 27019 Information security controls for the energy utility industry
Part 4: Guidelines for security of cloud services
ISO 27021 Competence requirements for information security management systems professionals
Security
Part 1: Principles and process ISO 27022 Guidance on information security management system processes
techniques
Part 2: Guidelines to plan and prepare for incident response ISO 27023 Mapping the revised editions of ISO/IEC 27001 and ISO/IEC 27002
Information security
ISO 27035
Part 3: Guidelines for ICT incident response operations
incident management ISO 27037 Guidelines for identification, collection, acquisition and preservation of digital evidence
ISO 27038 Specification for digital redaction
Part 4: Coordination
ISO 27039 Selection, deployment and operations of intrusion detection and prevention systems (IDPS)
Part 1: Overview and concepts ISO 27040 Storage security
Part 2: Organization normative framework ISO 27041 Guidance on assuring suitability and adequacy of incident investigative method
Part 3: Application security management process ISO 27042 Guidelines for the analysis and interpretation of digital evidence
Application
Part 4: Validation and verification ISO 27034 ISO 27043 Incident investigation principles and processes
security
Part 5: Protocols and application security controls data structure ISO 27070 Requirements for establishing virtualized roots of trust
Part 5-1: Protocols and application security controls data structure, XML schemas ISO 29115 Entity authentication assurance framework
ISO 29146 A framework for access management
Part 6: Case studies
Part 7: Assurance prediction framework
ISO 27031 Guidelines for information and communication technology readiness for business continuity
ISO 27032 Guidelines for cybersecurity -> Guidelines for Internet security
Part 1: Overview and concepts
ISO 27100 Overview and concepts
Part 2: Guidelines for the design and implementation of network security
Cybersecurity ISO 27102 Guidelines for cyber-insurance
Part 3: Reference networking scenarios — Threats, design techniques and control issues
ISO 27103 Cybersecurity and ISO and IEC Standards
Network
Part 4: Securing communications between networks using security gateways ISO 27033
security ISO 27109 Cybersecurity education and training
Part 5: Securing communications across networks using Virtual Private Networks (VPNs)
ISO 27110 Cybersecurity framework development guidelines
Part 6: Securing wireless IP network access
Part 7: Guidelines for network virtualization security
You might also like
- ISO IEC 27001 Lead Implementer A Complete Guide - 2020 EditionFrom EverandISO IEC 27001 Lead Implementer A Complete Guide - 2020 EditionNo ratings yet
- ISO IEC 27001 Lead Implementer A Complete Guide - 2021 EditionFrom EverandISO IEC 27001 Lead Implementer A Complete Guide - 2021 EditionNo ratings yet
- Business Continuity Planning BCP A Complete Guide - 2019 EditionFrom EverandBusiness Continuity Planning BCP A Complete Guide - 2019 EditionNo ratings yet
- ISO 27001/ISO 27002: A guide to information security management systemsFrom EverandISO 27001/ISO 27002: A guide to information security management systemsNo ratings yet
- ISO 27001 Controls – A guide to implementing and auditingFrom EverandISO 27001 Controls – A guide to implementing and auditingRating: 5 out of 5 stars5/5 (1)
- ISO27001 in a Windows Environment: The best practice implementation handbook for a Microsoft Windows environmentFrom EverandISO27001 in a Windows Environment: The best practice implementation handbook for a Microsoft Windows environmentNo ratings yet
- ISO 27001 Annex A Controls in Plain English: A Step-by-Step Handbook for Information Security Practitioners in Small BusinessesFrom EverandISO 27001 Annex A Controls in Plain English: A Step-by-Step Handbook for Information Security Practitioners in Small BusinessesRating: 5 out of 5 stars5/5 (1)
- Secure & Simple – A Small-Business Guide to Implementing ISO 27001 On Your Own: The Plain English, Step-by-Step Handbook for Information Security PractitionersFrom EverandSecure & Simple – A Small-Business Guide to Implementing ISO 27001 On Your Own: The Plain English, Step-by-Step Handbook for Information Security PractitionersNo ratings yet
- Computers, Business, and Security: The New Role for SecurityFrom EverandComputers, Business, and Security: The New Role for SecurityNo ratings yet
- ISO/IEC 27001:2022: An introduction to information security and the ISMS standardFrom EverandISO/IEC 27001:2022: An introduction to information security and the ISMS standardRating: 5 out of 5 stars5/5 (3)
- Application security in the ISO27001:2013 EnvironmentFrom EverandApplication security in the ISO27001:2013 EnvironmentRating: 4 out of 5 stars4/5 (2)
- Information Security Risk Management for ISO27001/ISO27002From EverandInformation Security Risk Management for ISO27001/ISO27002Rating: 4.5 out of 5 stars4.5/5 (3)
- The SSCP Prep Guide: Mastering the Seven Key Areas of System SecurityFrom EverandThe SSCP Prep Guide: Mastering the Seven Key Areas of System SecurityNo ratings yet
- ISO/IEC 27701:2019: An introduction to privacy information managementFrom EverandISO/IEC 27701:2019: An introduction to privacy information managementRating: 4.5 out of 5 stars4.5/5 (3)
- Information Security Risk Management for ISO 27001/ISO 27002, third editionFrom EverandInformation Security Risk Management for ISO 27001/ISO 27002, third editionRating: 4 out of 5 stars4/5 (3)
- Information security - Edition 2022: Risk management. Management systems. The ISO/IEC 27001:2022 standard. The ISO/IEC 27002:2022 controls.From EverandInformation security - Edition 2022: Risk management. Management systems. The ISO/IEC 27001:2022 standard. The ISO/IEC 27002:2022 controls.No ratings yet
- Managing ISO Documentation – A Plain English Guide: A Step-by-Step Handbook for ISO Practitioners in Small BusinessesFrom EverandManaging ISO Documentation – A Plain English Guide: A Step-by-Step Handbook for ISO Practitioners in Small BusinessesRating: 3.5 out of 5 stars3.5/5 (3)
- Preparations for the ISO Implementation Project – A Plain English Guide: A Step-by-Step Handbook for ISO Practitioners in Small BusinessesFrom EverandPreparations for the ISO Implementation Project – A Plain English Guide: A Step-by-Step Handbook for ISO Practitioners in Small BusinessesRating: 5 out of 5 stars5/5 (1)
- Information Assurance: Managing Organizational IT Security RisksFrom EverandInformation Assurance: Managing Organizational IT Security RisksRating: 5 out of 5 stars5/5 (1)
- Securing E-Business Systems: A Guide for Managers and ExecutivesFrom EverandSecuring E-Business Systems: A Guide for Managers and ExecutivesNo ratings yet
- Nine Steps to Success: An ISO27001:2013 Implementation OverviewFrom EverandNine Steps to Success: An ISO27001:2013 Implementation OverviewRating: 3 out of 5 stars3/5 (2)
- Implementing Database Security and AuditingFrom EverandImplementing Database Security and AuditingRating: 4.5 out of 5 stars4.5/5 (3)
- ISO 27001 Risk Management in Plain English: A Step-by-Step Handbook for Information Security Practitioners in Small BusinessesFrom EverandISO 27001 Risk Management in Plain English: A Step-by-Step Handbook for Information Security Practitioners in Small BusinessesRating: 4 out of 5 stars4/5 (9)
- Implementing Service Quality based on ISO/IEC 20000: A Management GuideFrom EverandImplementing Service Quality based on ISO/IEC 20000: A Management GuideRating: 4.5 out of 5 stars4.5/5 (3)
- Cybersecurity Design Principles: Building Secure Resilient ArchitectureFrom EverandCybersecurity Design Principles: Building Secure Resilient ArchitectureNo ratings yet
- Guidelines for Chemical Transportation Safety, Security, and Risk ManagementFrom EverandGuidelines for Chemical Transportation Safety, Security, and Risk ManagementNo ratings yet
- Practical Industrial Cybersecurity: ICS, Industry 4.0, and IIoTFrom EverandPractical Industrial Cybersecurity: ICS, Industry 4.0, and IIoTNo ratings yet
- ISMS Documented Information by Andrey Prozorov v.5.1 230305Document3 pagesISMS Documented Information by Andrey Prozorov v.5.1 230305kenyrNo ratings yet
- PFD-22-48 - Visa - Security Alert - Increase in PRA FraudDocument3 pagesPFD-22-48 - Visa - Security Alert - Increase in PRA FraudkenyrNo ratings yet
- Reglamento Auditoria Interna-SbsDocument19 pagesReglamento Auditoria Interna-SbskenyrNo ratings yet
- Best Practices For WirelessDocument3 pagesBest Practices For WirelesskenyrNo ratings yet
- METRICA V3 Planificacion de Sistemas de InformacionDocument22 pagesMETRICA V3 Planificacion de Sistemas de InformacionGonzalo Mejía VásquezNo ratings yet
- Installing Groundwork Monitor 6.6 - Support - GWConnectDocument5 pagesInstalling Groundwork Monitor 6.6 - Support - GWConnectkenyrNo ratings yet
- Manual Control RiesgosDocument61 pagesManual Control RiesgoskenyrNo ratings yet
- Understanding Security Layers: Lesson 1Document32 pagesUnderstanding Security Layers: Lesson 1Kristopher CharlesNo ratings yet
- 2021 IMS Management Review ReportDocument50 pages2021 IMS Management Review ReportDebby JosephNo ratings yet
- Panagiotis C. Kalantzis, CISSP, CISM, ISO2700LA: Strategic Cybersecurity Leader & Executive ConsultantDocument4 pagesPanagiotis C. Kalantzis, CISSP, CISM, ISO2700LA: Strategic Cybersecurity Leader & Executive ConsultantPanos KalantzisNo ratings yet
- SI-PT-10.02.01.04-Protocolo de Soporte Storbox - Entel v1Document10 pagesSI-PT-10.02.01.04-Protocolo de Soporte Storbox - Entel v1Eduardo Espinoza ValeriaNo ratings yet
- CMP - by MSDocument80 pagesCMP - by MSMahendra SutharNo ratings yet
- Itil V3 - at A Glance: Service DesignDocument1 pageItil V3 - at A Glance: Service DesignAleksandr TsirkunovNo ratings yet
- Implementación de Una Infraestructura Tecnológica Con Vlan para La Seguridad de La Información en La Municipalidad Distrital de Pampas - 2016Document58 pagesImplementación de Una Infraestructura Tecnológica Con Vlan para La Seguridad de La Información en La Municipalidad Distrital de Pampas - 2016Joel Quichca SotacuroNo ratings yet
- Aula 6 - Windows 10 - VIDocument15 pagesAula 6 - Windows 10 - VICândido LelisNo ratings yet
- 8 CSA Guidance in 60minutesDocument25 pages8 CSA Guidance in 60minutesalexmorenoasuarNo ratings yet
- What Is Information SecurityDocument36 pagesWhat Is Information SecurityEyan AlamanNo ratings yet
- Dirección MacDocument32 pagesDirección MacOdette Bahena NuñezNo ratings yet
- Apostila - Módulo 3 - Bootcamp Analista de Ataque CibernéticoDocument133 pagesApostila - Módulo 3 - Bootcamp Analista de Ataque CibernéticoTainá MorenoNo ratings yet
- Context OrganisationDocument5 pagesContext OrganisationRizky SyaputraNo ratings yet
- Information Security Auditors Module (Part-1) & Information Security Auditors Module (Part-2)Document2 pagesInformation Security Auditors Module (Part-1) & Information Security Auditors Module (Part-2)Sadik ShaikhNo ratings yet
- EX FINAL 4 - IBM Cybersecurity Analyst Professional Certificate Assessment Exam - CourseraDocument28 pagesEX FINAL 4 - IBM Cybersecurity Analyst Professional Certificate Assessment Exam - CourseraPaul Bances SeverinoNo ratings yet
- Evidencia Mapas Mentales y Ejemplo de Empresa PDFDocument3 pagesEvidencia Mapas Mentales y Ejemplo de Empresa PDFcaas random100% (1)
- Cloud Security Architecture Assessment Service Brief Azure v2 0Document2 pagesCloud Security Architecture Assessment Service Brief Azure v2 0LmoreiraNo ratings yet
- Tarea 4Document11 pagesTarea 4edgar ascencioNo ratings yet
- Anexo Condiciones Del ContratoDocument11 pagesAnexo Condiciones Del ContratoasuarezsmNo ratings yet
- Information Security - Review Question - CIADocument1 pageInformation Security - Review Question - CIAElise ShingNo ratings yet
- NSSF - Vacant Job Positions - November 2023Document53 pagesNSSF - Vacant Job Positions - November 2023johnfranc999No ratings yet
- Iso 27001Document24 pagesIso 27001Suki GNo ratings yet
- Política Nacional CiberseguridadDocument36 pagesPolítica Nacional CiberseguridadManuel MuñozNo ratings yet
- Securing and Managing Storage InfrastructureDocument51 pagesSecuring and Managing Storage InfrastructureTulipNo ratings yet
- Data Protection, Overnance & ComplianceDocument27 pagesData Protection, Overnance & ComplianceDaniel OnyangoNo ratings yet
- Rbi Circular EbankingDocument174 pagesRbi Circular EbankingKoka Laxman RaoNo ratings yet
- Iso+iec 27001-2013 PDFDocument24 pagesIso+iec 27001-2013 PDFJacqueline SalazarNo ratings yet
- Sesión 01Document26 pagesSesión 01Arae AraeNo ratings yet
- Security Awareness NotesDocument23 pagesSecurity Awareness NotesParvaiz Lodhi100% (13)
- Conteúdo Psi CompletoDocument76 pagesConteúdo Psi CompletoTarcisio AngeloNo ratings yet