Professional Documents
Culture Documents
Security in IOT
Uploaded by
Jaouadi Nourhen0 ratings0% found this document useful (0 votes)
4 views25 pagesThe document discusses security issues in internet of things (IoT). It outlines main security issues like limited resources, privacy, authentication, and availability. It describes current security attacks at different levels including jamming, spoofing, and insecure software. Proposed solutions include appropriate encryption, authentication protocols, and securely implementing software and firmware updates. In conclusion, IoT devices currently have many vulnerabilities due to limitations and lack of security standards being implemented.
Original Description:
Original Title
Security in IOT.pptx
Copyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentThe document discusses security issues in internet of things (IoT). It outlines main security issues like limited resources, privacy, authentication, and availability. It describes current security attacks at different levels including jamming, spoofing, and insecure software. Proposed solutions include appropriate encryption, authentication protocols, and securely implementing software and firmware updates. In conclusion, IoT devices currently have many vulnerabilities due to limitations and lack of security standards being implemented.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
0 ratings0% found this document useful (0 votes)
4 views25 pagesSecurity in IOT
Uploaded by
Jaouadi NourhenThe document discusses security issues in internet of things (IoT). It outlines main security issues like limited resources, privacy, authentication, and availability. It describes current security attacks at different levels including jamming, spoofing, and insecure software. Proposed solutions include appropriate encryption, authentication protocols, and securely implementing software and firmware updates. In conclusion, IoT devices currently have many vulnerabilities due to limitations and lack of security standards being implemented.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
You are on page 1of 25
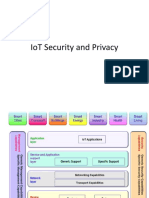
Internet Of Things
Security
Presented By : Wafa Bakir
Table of contents
● Overview
● Problematic
● Main Security issues
● Security requirements
● Current Security attacks
● Solutions
● Insights
2 Master de recherche DSIR
Overview
Nowadays, the Internet of Things (IoT) has
enormous potential and growth impact due
to the technological revolution and the
spread and appearance of events. It has
received considerable attention from
researchers and is considered the future of
the Internet.
3 Master de recherche DSIR
Problematic
most of IoT devices can be easily
compromised and are subject to various
security attacks :
● What are the main IoT security issues ?
● What are the security requirements ?
● What are current security attacks and the
proposed solutions ?
4 Master de recherche DSIR
Main Security issues
● Limited resources
● ensuring consistency and adaptation
between solutions with these limited
architectures
5 Master de recherche DSIR
Security requirements
6 Master de recherche DSIR
Privacy, confidentiality, and integrity
● An appropriate encryption technique is
needed in order to assure the privacy of the
data.
● The vast majority of the information saved
and kept on any device is exposed to
invasions of privacy.
● Assaults can allow a malicious user to gain
data integrity by changing the saved data for
illegal uses.
7 Master de recherche DSIR
Authentication and authorization
● Creating an associated standard protocol for
authentication in the IoT is extremely difficult.
● Authorization methods make sure that only
authorized people are allowed access to
systems or information.
● keeping track of how resources are used and
making sure they are used correctly through
audits and reports is a reliable and effective
way to manage network security.
8 Master de recherche DSIR
Availability of services
● Traditional denial-of-service attacks against
IoT devices could obstruct the delivery of
services.
● Different tactics, such as replay assaults,
sinkhole attacks, and jammer advertisements,
employ IoT components at various stages to
reduce the quality of service (QoS) offered to
IoT users.
9 Master de recherche DSIR
Single points of failure
● IoT-based infrastructure's continuous reliance
on heterogeneous networks has the potential
to expose numerous single points of failure.
● It's necessary to create a safe environment in
order to accommodate a greater number of
Internet of Things devices and to propose
other techniques to build a fault tolerant
system.
10 Master de recherche DSIR
Energy management
● IoT devices frequently have a small battery
life and a weak storage capacity.
● Attacks on IoT systems can lead to increased
power usage by saturating the network and
draining device resources with repetitive and
false service queries
11 Master de recherche DSIR
Current Security attacks
Low Level Attacks:
★ Hardware level
★ Physical level
★ Data link level
12 Master de recherche DSIR
Current Security attacks
● Jamming disrupts the radio signals utilized by nodes
in a network. It's characterized as the intentional use of
electromagnetic radiation to disrupt or disable a
communication system.
● Sybil nodes utilize false identities to carry out attacks
.they may employ random, fabricated MAC values on
the physical layer to pretend to be another device.
● In Spoofing An attacker can pretend to be another
approved IoT device by claiming the real user's MAC or
IP address.
● In sleep deprivation attacks the target is
battery-operated computational hardware, like a
sensor node by keeping the sensor nodes awake.
13 Master de recherche DSIR
Current Security attacks
Medium Level Attacks:
★ Communication
★ Routing
★ Session management
14 Master de recherche DSIR
Current Security attacks
● In Buffer reservation delivering incomplete packets to
a receiving node must allocate slots for the
reassembling of received packets. Due to the
unfinished packets taking up space and causing other
fragment packets to be deleted, this attack causes
denial-of-service.
● In Sinkhole attacks The attacker uses falsified routing
information to lure nearby nodes, after which it
performs selective forwarding or modifies the data
traveling through them. The attacking node asserts
that it is providing a very alluring link. As a result, this
node is skipped by a lot of traffic
15 Master de recherche DSIR
Current Security attacks
16 Master de recherche DSIR
Current Security attacks
● Wormholes form a tunnel connecting two nodes to
ensure that the packets coming from one node
immediately reach the other node
17 Master de recherche DSIR
Current Security attacks
High Level Attacks:
★ Application layer
★ Communications
layer
18 Master de recherche DSIR
Current Security attacks
● Insecure Ecosystem interfaces : The user interfaces
for IoT services on the web, mobile, and cloud are
vulnerable to a number of risks that pose a major risk
to data privacy
● Insecure Software / Firmware is one source of
numerous IoT vulnerabilities.. Carefully testing the
code that uses languages like JSON, XML, SQLi, and XSS
is necessary. Similar to this, firmware and software
upgrades should be made properly.
19 Master de recherche DSIR
Solutions
20 Master de recherche DSIR
21 Master de recherche DSIR
Solutions
22 Master de recherche DSIR
Conclusion
Today's Internet of Things devices are
unsafe and vulnerable, and they are not
able to provide any security to protect
themselves. This is due to the resource
limitations in IoT devices as well as the
lack of developed standards and weakly
implemented security measures in
hardware and software.
23 Master de recherche DSIR
Source
International Journal of Advanced Computer Science and
Applications, Vol. 14, No. 5, 2023 :
Security in the IoT: State-of-the-Art, Issues, Solutions, and
Challenges
Ahmed SRHIR , Tomader MAZRI , Mohammed, BENBRAHIM
Department of Electrical Engineering-Networks and
Telecommunication Systems-National School of Applied Sciences, Ibn
Tofail University, Kenitra, Morocco
Master de recherche DSIR
Thank You
Master de recherche DSIR
You might also like
- Mastering Cyber Security A Comprehensive Guide: cyber security, #2From EverandMastering Cyber Security A Comprehensive Guide: cyber security, #2No ratings yet
- IoT Security - Part 1Document77 pagesIoT Security - Part 1jeanfrancoisalbertini1503No ratings yet
- IoT SecurityDocument42 pagesIoT Securityfa20-bce-046No ratings yet
- Needed PaperDocument11 pagesNeeded PaperTaimour KhanNo ratings yet
- Iot Security and PrivacyDocument23 pagesIot Security and PrivacyAanchal VermaNo ratings yet
- SECURITYDocument8 pagesSECURITYsarabjeetNo ratings yet
- Seminar PPT 1Document19 pagesSeminar PPT 1Akshara sNo ratings yet
- NetworkDocument73 pagesNetworksaadalsamed2020No ratings yet
- SDN Framework For Securing Iot Networks: AbstractDocument14 pagesSDN Framework For Securing Iot Networks: AbstractGuillo YeroviNo ratings yet
- Network Security and Cyber Security A ReviewDocument6 pagesNetwork Security and Cyber Security A ReviewIJRASETPublicationsNo ratings yet
- Extreme Surge Iot Solution White PaperDocument19 pagesExtreme Surge Iot Solution White PapermpmtechnologyNo ratings yet
- 32-Cyber SecurityDocument7 pages32-Cyber Security20 O3 004 ARUN M NNo ratings yet
- IoT Cyber AttacksDocument2 pagesIoT Cyber AttacksrayjoneskeNo ratings yet
- Network Security Attacks and Countermeasures On Layer 2 and Layer 3 Network DevicesDocument15 pagesNetwork Security Attacks and Countermeasures On Layer 2 and Layer 3 Network DevicesIJRASETPublicationsNo ratings yet
- Cipher Home A Smart Home With Network Level Security To IoT DevicesDocument5 pagesCipher Home A Smart Home With Network Level Security To IoT DevicesInternational Journal of Innovative Science and Research TechnologyNo ratings yet
- Matecconf Icmed2024 01103Document9 pagesMatecconf Icmed2024 01103Sharath M NNo ratings yet
- Iot Security Techniques Based On Machine LearningDocument20 pagesIot Security Techniques Based On Machine LearningAjj PatelNo ratings yet
- Security, Privacy & Trust: Course Code: Csio4700 Course Name: Iot For IndustriesDocument24 pagesSecurity, Privacy & Trust: Course Code: Csio4700 Course Name: Iot For IndustriesVairavel ChenniyappanNo ratings yet
- Cyber Security - Iot: 4. Unauthorized Access or ControlDocument4 pagesCyber Security - Iot: 4. Unauthorized Access or ControlKhushal SinghNo ratings yet
- Sensors 22 03744 With CoverDocument34 pagesSensors 22 03744 With CoverashwinNo ratings yet
- Cyber Security InternshipDocument10 pagesCyber Security InternshipR Bharath Kumar100% (1)
- OS Challanges and SecurityDocument5 pagesOS Challanges and SecuritymuhammadNo ratings yet
- A Review Paper of Security in Internet of Things (Iot)Document6 pagesA Review Paper of Security in Internet of Things (Iot)Sapna AgrawalNo ratings yet
- 21 Intrusion - Detection - System - For - IoT - DevicesDocument5 pages21 Intrusion - Detection - System - For - IoT - DevicesJaroos RianNo ratings yet
- Detecting Distributed Denial of Service (DDoS) in SD-IoT Environment With Enhanced Firefly Algorithm and Convolution Neural NetworkDocument15 pagesDetecting Distributed Denial of Service (DDoS) in SD-IoT Environment With Enhanced Firefly Algorithm and Convolution Neural NetworkZAKARIA JAMALNo ratings yet
- 10.1007@s11831 020 09496 0Document33 pages10.1007@s11831 020 09496 0Hatim LakhdarNo ratings yet
- Ijcna 2022 o 04Document14 pagesIjcna 2022 o 04vijaysagarb17No ratings yet
- Attack Detection in IoT Critical Infrastructures A Machine Learning and Big Data Processing ApproachDocument8 pagesAttack Detection in IoT Critical Infrastructures A Machine Learning and Big Data Processing ApproachCarlosNo ratings yet
- Chapter 6 Security and GovernanceDocument31 pagesChapter 6 Security and GovernanceKushinga E MasungaNo ratings yet
- Identifying and Analyzing Risk Mitigation Strategies in IOT Devices Using Light Weight Symmetric EncryptionDocument11 pagesIdentifying and Analyzing Risk Mitigation Strategies in IOT Devices Using Light Weight Symmetric EncryptionIJRASETPublicationsNo ratings yet
- Bolg - Anukriti - B.Tech CSE (A)Document2 pagesBolg - Anukriti - B.Tech CSE (A)anukritiverma62No ratings yet
- Lecture6 SecurityDocument20 pagesLecture6 SecurityBLa ProductionNo ratings yet
- IOT5Document20 pagesIOT5Nahom DiresNo ratings yet
- Importance of Cyber Security IJERTCONV8IS05036Document3 pagesImportance of Cyber Security IJERTCONV8IS05036draken729123No ratings yet
- Wafaa IOTSecurityDocument30 pagesWafaa IOTSecurityWafaa BasilNo ratings yet
- Liu 2021Document37 pagesLiu 2021JudybenavidesNo ratings yet
- Novel Three-Tier Intrusion Detection and Prevention System in Software Defined NetworkDocument15 pagesNovel Three-Tier Intrusion Detection and Prevention System in Software Defined NetworkUsman AhmedNo ratings yet
- Challenges Facing On IoT and Gaps That Exist in The IoT Cybersecurity of Data Transferred by MQTT & CoAP ProtocolsDocument8 pagesChallenges Facing On IoT and Gaps That Exist in The IoT Cybersecurity of Data Transferred by MQTT & CoAP ProtocolsInternational Journal of Innovative Science and Research Technology100% (1)
- Securing Smart Homes Via Software-Defined Networking and Low-Cost Traffic ClassificationDocument9 pagesSecuring Smart Homes Via Software-Defined Networking and Low-Cost Traffic ClassificationHiba AyoubNo ratings yet
- A Deep Learning Based Framework For Cyberattack Detection in IoT NetworksDocument21 pagesA Deep Learning Based Framework For Cyberattack Detection in IoT NetworksAI tailieuNo ratings yet
- Security in IOTDocument104 pagesSecurity in IOTLogapriya RNo ratings yet
- Ijsrp - Network Security DJ SANGHVIDocument5 pagesIjsrp - Network Security DJ SANGHVISagar chaudhariNo ratings yet
- 2 Sensors-21-04884Document18 pages2 Sensors-21-04884Taimour KhanNo ratings yet
- Exploring The Security of IoT DevicesDocument8 pagesExploring The Security of IoT Devicesderangula joshithasreeNo ratings yet
- SDN Iot2Document6 pagesSDN Iot2Somasekhar VuyyuruNo ratings yet
- Kamaldeep, 2021Document12 pagesKamaldeep, 2021Faisal AliNo ratings yet
- A Security Framework For IOT Devices Against Wireless ThreatsDocument6 pagesA Security Framework For IOT Devices Against Wireless ThreatsFritz FatigaNo ratings yet
- IoT BLOGGDocument15 pagesIoT BLOGGPratikshaNo ratings yet
- An Energy-Aware Highly Available and Fault-Tolerant Method For Reliable IoT SystemsDocument19 pagesAn Energy-Aware Highly Available and Fault-Tolerant Method For Reliable IoT SystemsTeba SamiNo ratings yet
- 19cse304-Cybersecurity Answer KeyDocument19 pages19cse304-Cybersecurity Answer KeyabhiNo ratings yet
- C B Patel Computer Collage: "Sel F Defendin G Network"Document21 pagesC B Patel Computer Collage: "Sel F Defendin G Network"299 Shingala MiraliNo ratings yet
- A Trusted Feature Aggregator Federated Learning For Distributed Malicious Attak Detection-14Document15 pagesA Trusted Feature Aggregator Federated Learning For Distributed Malicious Attak Detection-14Canada OlympiadNo ratings yet
- Danish Javeed, Muhammad Shahid Saeed, Ijaz Ahmad, Muhammad Adil, Prabhat Kumar, and A K M Najmul Islam Affiliation Not Available December 14, 2023Document27 pagesDanish Javeed, Muhammad Shahid Saeed, Ijaz Ahmad, Muhammad Adil, Prabhat Kumar, and A K M Najmul Islam Affiliation Not Available December 14, 2023Dr. V. Padmavathi Associate ProfessorNo ratings yet
- Security Challenges and Issues in Cloud Computing - The Way AheadDocument4 pagesSecurity Challenges and Issues in Cloud Computing - The Way Aheadetylr mailNo ratings yet
- OS Challanges and SecurityDocument3 pagesOS Challanges and SecuritymuhammadNo ratings yet
- Security in Wireless Sensor Networks: Comparative StudyDocument11 pagesSecurity in Wireless Sensor Networks: Comparative StudyAnonymous Gl4IRRjzNNo ratings yet
- Io TSecurity 2021Document12 pagesIo TSecurity 2021Ronald SmithNo ratings yet
- Intrusion Detection System Through Advance Machine Learning For The Internet of Things NetworksDocument7 pagesIntrusion Detection System Through Advance Machine Learning For The Internet of Things NetworksMuhammad Junaid KhalidNo ratings yet
- 10 0000@ieeexplore Ieee Org@8717819 PDFDocument5 pages10 0000@ieeexplore Ieee Org@8717819 PDFGuillo YeroviNo ratings yet
- Dazine 2018Document5 pagesDazine 2018Teddy IswahyudiNo ratings yet
- FACA 261 Operation Manual 12-20-11 PDFDocument56 pagesFACA 261 Operation Manual 12-20-11 PDFwilmerNo ratings yet
- Statement of Work For Biosafe Labs India PVT - LTD.: S.No. Milestones Tasks RemindersDocument24 pagesStatement of Work For Biosafe Labs India PVT - LTD.: S.No. Milestones Tasks Remindersaakash kumarNo ratings yet
- Instructions Cyborg Beast Updated 6-26-14Document18 pagesInstructions Cyborg Beast Updated 6-26-14fredyugaNo ratings yet
- Microprogram ControlDocument30 pagesMicroprogram ControlMit BhaiyaNo ratings yet
- Qasim Comlete MonographDocument81 pagesQasim Comlete Monographshams ur rehman100% (1)
- Lec08 PDFDocument26 pagesLec08 PDFalb3rtnetNo ratings yet
- ARM ArchitectureDocument547 pagesARM ArchitectureAmrita BhattNo ratings yet
- 9258 ManualDocument35 pages9258 ManualcabisurNo ratings yet
- PaX I3dDocument162 pagesPaX I3dKalvin100% (1)
- Implementation of FPGA Based 3-Phase Inverter FED BLDC MotorDocument5 pagesImplementation of FPGA Based 3-Phase Inverter FED BLDC Motortakaca40No ratings yet
- 3WL1 Upgrade EN 201901221016555255 PDFDocument98 pages3WL1 Upgrade EN 201901221016555255 PDFDasNo ratings yet
- 287045611447707Document16 pages287045611447707N b vedi100% (1)
- Bapi Idoc PresentationDocument13 pagesBapi Idoc Presentationapi-26420083100% (4)
- Virtualization: Virtualization and Basics of VirtualizationDocument16 pagesVirtualization: Virtualization and Basics of VirtualizationGirum TesfayeNo ratings yet
- 4 TuberiasDocument8 pages4 TuberiasVladimir VeraNo ratings yet
- Multiple Comparisons (Only Computing All Treatments With A Control)Document16 pagesMultiple Comparisons (Only Computing All Treatments With A Control)Rohaila RohaniNo ratings yet
- Benihana Teaching NoteDocument24 pagesBenihana Teaching Noteaeonassoc100% (6)
- Downey05semaphores PDFDocument291 pagesDowney05semaphores PDFJivanSharmaNo ratings yet
- AU09 Lab PD222-1LDocument46 pagesAU09 Lab PD222-1Lahbipn1No ratings yet
- Oracle ADF SecurityDocument30 pagesOracle ADF SecurityiamsonalNo ratings yet
- Lenovo YOGA3 AIZY0 LA-B921P PDFDocument36 pagesLenovo YOGA3 AIZY0 LA-B921P PDFFernando Amaro HernandezNo ratings yet
- Federal-Postal-Court-Command-Claim - 2022-1.Document2 pagesFederal-Postal-Court-Command-Claim - 2022-1.Ramon Martinez100% (2)
- Quake SeriesDocument264 pagesQuake SeriesSean Cotter0% (1)
- RDBMS Full ProgramsDocument2 pagesRDBMS Full ProgramsSulbha GathNo ratings yet
- Digital Technologies in Education TimelineDocument3 pagesDigital Technologies in Education Timelineapi-316829653No ratings yet
- Activeserver: Frictionless Fraud Prevention With 3D Secure 2Document9 pagesActiveserver: Frictionless Fraud Prevention With 3D Secure 2karlosm84No ratings yet
- OOAD All Chapter NOTES - 20211218132503Document79 pagesOOAD All Chapter NOTES - 20211218132503Sushan KawanNo ratings yet
- 73 Rasterization HwImplOfMicropolygonRasterizationDocument9 pages73 Rasterization HwImplOfMicropolygonRasterizationabijoshNo ratings yet
- 1.PDA Cilamaya CipeundeuyDocument14 pages1.PDA Cilamaya CipeundeuyigitNo ratings yet
- Login With WhatsApp ProposalDocument10 pagesLogin With WhatsApp ProposalBhavik KoladiyaNo ratings yet