Professional Documents
Culture Documents
ss2 Mid Test Questions
ss2 Mid Test Questions
Uploaded by
okwuonujohnOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
ss2 Mid Test Questions
ss2 Mid Test Questions
Uploaded by
okwuonujohnCopyright:
Available Formats
FILE ORGANIZATION
1. Define file organization
DATA PROCESSING MIDTERM TEST
2. List four types of file organization
CREATING AND MODIFYING RELATION USING SQL
3. Outline five factors to be considered before choosing a file
QUESTIONS. organization
1. Explain SQL
INTERNET
2. What is constraints?
1. Define internet
3. List six data types
2. List 4 example of web browser
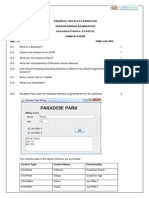
4. CREATE A DATABASE LET THE NAME BE ; ssonedatabase and
3. List some common features of web browser
create a table with the following field;
4. List 6 advantages of internet
Firstname, last name, address, phone no,dofb, gender,Id
5. List 7 abuses of internet
Create a primary key with the Id, and insert a constraint that will
6. Explain the following
check the gender to be only female. Each field must not be empty
1. Malicious software
in the table.
2. Denial of service attack
Populate your table. From the table created update a record of
3. SQL injection
your choice.
4. Phishing
1 2
FILE ORGANIZATION
1. Define file organization
DATA PROCESSING MIDTERM TEST 2. List four types of file organization
CREATING AND MODIFYING RELATION USING SQL 3. Outline five factors to be considered before choosing a file
QUESTIONS. organization
1. Explain SQL INTERNET
2. What is constraints? 1. Define internet
3. List six data types 2. List 4 example of web browser
4. CREATE A DATABASE LET THE NAME BE ; ssonedatabase and 3. List some common features of web browser
create a table with the following field; 4. List 6 advantages of internet
Firstname, last name, address, phone no,dofb, gender,Id 5. List 7 abuses of internet
Create a primary key with the Id, and insert a constraint that will 6. Explain the following
check the gender to be only female. Each field must not be empty a) Malicious software
in the table. b) Denial of service attack
Populate your table. From the table created update a record of c) SQL injection
your choice. d) Phishing
2
1
FILE ORGANIZATION
1.
Define file organization
DATA PROCESSING MIDTERM TEST 2.
List four types of file organization
CREATING AND MODIFYING RELATION USING SQL 3.
Outline five factors to be considered before choosing a file
QUESTIONS. organization
1. Explain SQL INTERNET
2. What is constraints? 1. Define internet
3. List six data types 2. List 4 example of web browser
4. CREATE A DATABASE LET THE NAME BE ; ssonedatabase and 3. List some common features of web browser
create a table with the following field; 4. List 6 advantages of internet
Firstname, last name, address, phone no,dofb, gender,Id 5. List 7 abuses of internet
Create a primary key with the Id, and insert a constraint that will 6. Explain the following
check the gender to be only female. Each field must not be empty a. Malicious software
in the table. b. Denial of service attack
Populate your table. From the table created update a record of c. SQL injection
your choice. d. Phishing 2
1
FILE ORGANIZATION
1. Define file organization
DATA PROCESSING MIDTERM TEST 2. List four types of file organization
CREATING AND MODIFYING RELATION USING SQL 3. Outline five factors to be considered before choosing a file
QUESTIONS. organization
1. Explain SQL INTERNET
2. What is constraints? 1. Define internet
3. List six data types 2. List 4 example of web browser
4. CREATE A DATABASE LET THE NAME BE ; ssonedatabase and 3. List some common features of web browser
create a table with the following field; 4. List 6 advantages of internet
Firstname, last name, address, phone no,dofb, gender,Id 5. List 7 abuses of internet
Create a primary key with the Id, and insert a constraint that will 6 Explain the following
check the gender to be only female. Each field must not be empty a. Malicious software
in the table. b. Denial of service attack
Populate your table. From the table created update a record of c. SQL injection
your choice. d. Phishing
2
1
You might also like
- Data Engineering Road MapDocument1 pageData Engineering Road MapVanraj MakwanaNo ratings yet
- BCA 428 OracleDocument142 pagesBCA 428 OraclekskchariNo ratings yet
- IPT HSC Notes 2011 - MrBrightsideDocument94 pagesIPT HSC Notes 2011 - MrBrightsideZohairAhmad100% (1)
- Quiz 2Document13 pagesQuiz 2prudhvi ch100% (1)
- ORACLE PL/SQLDocument61 pagesORACLE PL/SQLPraneeth NeelisettyNo ratings yet
- Slowly Changing DimensionDocument14 pagesSlowly Changing Dimensiondprakash70100% (1)
- Unit I - Relational Database Part - A (2 Marks) : 1. Define Database Management SystemDocument27 pagesUnit I - Relational Database Part - A (2 Marks) : 1. Define Database Management SystemMohammad Bilal - Asst. Prof, Dept. of CSENo ratings yet
- Classic Star Schema As Data Model of Data WarehouseDocument7 pagesClassic Star Schema As Data Model of Data WarehouseAnanya BiswasNo ratings yet
- Hotel Room Booking & AvailabilityDocument84 pagesHotel Room Booking & AvailabilitySathas Krishnan87% (15)
- Managing Information Systems SyllabusDocument12 pagesManaging Information Systems SyllabuspusakalyeNo ratings yet
- Online Footwear SynopsisDocument44 pagesOnline Footwear SynopsisAnkit Jain56% (9)
- Assignment 5Document1 pageAssignment 5nspecial241No ratings yet
- Emelc - Computer 4Document4 pagesEmelc - Computer 4Shierey Ann CalcenaNo ratings yet
- University of Cagayan ValleyDocument5 pagesUniversity of Cagayan ValleyPlacid ItyNo ratings yet
- Is HDB Content ListDocument2 pagesIs HDB Content ListcosideskNo ratings yet
- SPE 2106 FUNDAMENTALS OF DATABASE SYSTEM Course OutlineDocument3 pagesSPE 2106 FUNDAMENTALS OF DATABASE SYSTEM Course OutlinekcalvinmwendaNo ratings yet
- Balingit Ranalyn R. Cruz, Maureen Anne A. Jimenez, Michael Nuñez, Neslie Danes M. Sampiano, Arlene Ann L. BSA 5-2Document4 pagesBalingit Ranalyn R. Cruz, Maureen Anne A. Jimenez, Michael Nuñez, Neslie Danes M. Sampiano, Arlene Ann L. BSA 5-2lilienne ylenaNo ratings yet
- Bba 1st Front PageDocument1 pageBba 1st Front PageMayank RajputNo ratings yet
- Dbms Manual by Gouresh (1) Kanishq (1) 645 (1) 12Document53 pagesDbms Manual by Gouresh (1) Kanishq (1) 645 (1) 12kanishq MukatiNo ratings yet
- DBM 612 Business Information SystemsDocument4 pagesDBM 612 Business Information SystemsobaladermottNo ratings yet
- BCA-IVSem Info. System 6676 - 23-07-2021Document1 pageBCA-IVSem Info. System 6676 - 23-07-2021Anuj VermaNo ratings yet
- Chapter 14Document3 pagesChapter 14Shin MelodyNo ratings yet
- Question Bank Computer Science (2 Year)Document20 pagesQuestion Bank Computer Science (2 Year)Muhammad Attiq Ur RehmanNo ratings yet
- Assignment 1 QuestionsDocument1 pageAssignment 1 QuestionsBikram ThapaNo ratings yet
- Practice Exercises: AnswerDocument4 pagesPractice Exercises: AnswerNUBG Gamer100% (1)
- Log On To AcessDocument2 pagesLog On To AcessElon MuskNo ratings yet
- Lab 01Document1 pageLab 011211103281No ratings yet
- Practical Questions PODDocument1 pagePractical Questions PODaayush waghereNo ratings yet
- Introduction To SQLDocument56 pagesIntroduction To SQLRalfh Pescadero De GuzmanNo ratings yet
- ADBMS Mid Term Contents: Introduction To Database - File-Based SystemDocument14 pagesADBMS Mid Term Contents: Introduction To Database - File-Based SystemMizanur ShohelNo ratings yet
- DBMS Concepts & Programming in FoxProDocument3 pagesDBMS Concepts & Programming in FoxProPiyush Raj SinhaNo ratings yet
- DBMSDocument16 pagesDBMSchinnu chinnuNo ratings yet
- Ss2 Data Processing 2nd TermDocument33 pagesSs2 Data Processing 2nd TermEro ChuksNo ratings yet
- DBMS - Prelim - AnswerDocument2 pagesDBMS - Prelim - AnswerHack FinNo ratings yet
- Database OperationsDocument13 pagesDatabase OperationsOpa KopNo ratings yet
- Welcome To MSIT: Check ListDocument4 pagesWelcome To MSIT: Check ListSuraj NarangNo ratings yet
- ICT Ed.446 - DBMS UpdatedDocument5 pagesICT Ed.446 - DBMS UpdatedHOPE11 00No ratings yet
- Lab Task1 DatabaseDocument6 pagesLab Task1 DatabaseNurul ImanNo ratings yet
- Tutorial 1: TIS1101/TDB2111 Database Fundamentals/Database SystemsDocument1 pageTutorial 1: TIS1101/TDB2111 Database Fundamentals/Database SystemsYuvaraj ElsusNo ratings yet
- Kings: Department of Computer Science & Engineering Question BankDocument5 pagesKings: Department of Computer Science & Engineering Question BankDhiravidanNo ratings yet
- Oracle Database 11g: SQL Fundamentals I: Exam Number: 1Z0-051 Exam Price: US$ 125Document4 pagesOracle Database 11g: SQL Fundamentals I: Exam Number: 1Z0-051 Exam Price: US$ 125Pius Opio Okello ErupaasiNo ratings yet
- DBMS Assignment 1Document3 pagesDBMS Assignment 1Abdiasis HamudNo ratings yet
- 5 BtechDocument22 pages5 BtechSandeep Kumar ShuklaNo ratings yet
- Namma Kalvi 12th Computer Applications Chapter 3 Surya GuideDocument11 pagesNamma Kalvi 12th Computer Applications Chapter 3 Surya GuideManisha SNo ratings yet
- Unit I Introduction and Conceptual Modelling PART-A (2 Marks)Document6 pagesUnit I Introduction and Conceptual Modelling PART-A (2 Marks)prabha_dhandayudamNo ratings yet
- Bài Tập Chương 1 - Database Concepts: Họ Và Tên - Mã Sinh Viên - o0o - I. Review QuestionsDocument4 pagesBài Tập Chương 1 - Database Concepts: Họ Và Tên - Mã Sinh Viên - o0o - I. Review QuestionsThành NguyễnNo ratings yet
- Need For DBMSDocument11 pagesNeed For DBMSudhaya suriyaNo ratings yet
- Dmmgym-Ie: HourslDocument2 pagesDmmgym-Ie: Hourslsagar batraNo ratings yet
- Ss 2 Data Processing Second Term E-NoteDocument40 pagesSs 2 Data Processing Second Term E-NoteJesseNo ratings yet
- Business AnalyticsDocument2 pagesBusiness AnalyticsElyse Ann ReyesNo ratings yet
- 202 Database Management Systems-Min PDFDocument3 pages202 Database Management Systems-Min PDFSuraj WaniNo ratings yet
- Course Outline Template Intro To DBDocument5 pagesCourse Outline Template Intro To DBmuhammad atiqNo ratings yet
- DNP s3 22-23 Even SemDocument14 pagesDNP s3 22-23 Even SemGodugulaRevathiNo ratings yet
- Final DbmsDocument10 pagesFinal DbmsAnupam GyawaliNo ratings yet
- The Data ControlDocument9 pagesThe Data Controlmidhungbabu88No ratings yet
- 9 - The Database Design Part-3Document18 pages9 - The Database Design Part-3ay9993805No ratings yet
- Data Engineering RoadmapDocument1 pageData Engineering Roadmapkashif.kudalkar7067No ratings yet
- Assignment 1 Database LatestDocument5 pagesAssignment 1 Database LatestWan Nur Ardini AmiraNo ratings yet
- 2 It302g Linux OsDocument8 pages2 It302g Linux OsAmit DeshaiNo ratings yet
- Database Management SystemsDocument1 pageDatabase Management SystemsAmrit MulepatyNo ratings yet
- Research Paper 5 2004Document15 pagesResearch Paper 5 2004Shubham PitaleNo ratings yet
- Basic of SQL: DBMS: (Database Management System) : Data Base Management System Is The (Or)Document1 pageBasic of SQL: DBMS: (Database Management System) : Data Base Management System Is The (Or)Manohar Reddy PullagurlaNo ratings yet
- ICT Ed.487 System Administration Using LinuxDocument6 pagesICT Ed.487 System Administration Using LinuxExtra MailNo ratings yet
- Scheme of Work Review Template - 2022 - 2023Document3 pagesScheme of Work Review Template - 2022 - 2023Muhammed MuhammedNo ratings yet
- Documents - 6603-Abinitio Course Contents-BasicDocument4 pagesDocuments - 6603-Abinitio Course Contents-BasicAjay MetriNo ratings yet
- Rdbms III SemDocument80 pagesRdbms III Semsms948072No ratings yet
- BCT2103 Course OutlineDocument1 pageBCT2103 Course OutlinenewtonNo ratings yet
- VVP Engineering College: Assignment 2 DDLDocument12 pagesVVP Engineering College: Assignment 2 DDLUugttt7No ratings yet
- Lab2 Physical DesignDocument25 pagesLab2 Physical DesignBíNo ratings yet
- ExamenDocument3 pagesExamenEder Legua0% (1)
- Programming Assignment Unit 7 Solution v1Document12 pagesProgramming Assignment Unit 7 Solution v1SouAi AzIzNo ratings yet
- LabAssignment1 19Document4 pagesLabAssignment1 19Rithik SachdevNo ratings yet
- Cassandra Installation ReviewDocument6 pagesCassandra Installation ReviewjoiedevieNo ratings yet
- Scope, and The Inter-Relationships Among These EntitiesDocument12 pagesScope, and The Inter-Relationships Among These EntitiesSyafiq AhmadNo ratings yet
- Dbms PPT For Chapter 7Document45 pagesDbms PPT For Chapter 7Sreekavya AchantiNo ratings yet
- Sanjana Dbms WorkDocument38 pagesSanjana Dbms WorkMajety S LskshmiNo ratings yet
- SQL Queries Student Catalog QueriesDocument20 pagesSQL Queries Student Catalog Queriesshyam15287No ratings yet
- Get The Best Out of Oracle Partitioning: A Practical Guide and ReferenceDocument353 pagesGet The Best Out of Oracle Partitioning: A Practical Guide and ReferenceSanju VermaNo ratings yet
- TCS 111Document3 pagesTCS 111bobu16No ratings yet
- Movie DatabaseDocument3 pagesMovie DatabaseChandrakanth D Kulkarni100% (1)
- In 901HF1 MessageReferenceDocument455 pagesIn 901HF1 MessageReferencejalabas11No ratings yet
- Dbms MANUALDocument98 pagesDbms MANUALYogita GhumareNo ratings yet
- CSC3064 Database Engineering: Entity-Relationship (E-R) ModelingDocument7 pagesCSC3064 Database Engineering: Entity-Relationship (E-R) ModelingHolly InSanestNo ratings yet
- CBSE Class 11 Informatics Practices Sample Paper-01 (Solved)Document10 pagesCBSE Class 11 Informatics Practices Sample Paper-01 (Solved)cbsesamplepaper83% (24)
- Mysql FinalDocument14 pagesMysql FinalNITANT KALRANo ratings yet
- Cs403 Midterm Solved Mcqs by MoaazDocument29 pagesCs403 Midterm Solved Mcqs by Moaazsalman_scribd100% (1)
- Change LogDocument22 pagesChange LogRavinderRaviNo ratings yet
- Automated Network Administration ToolDocument67 pagesAutomated Network Administration ToolGouse BaigNo ratings yet
- SQL CheatsheeDocument3 pagesSQL CheatsheeSeshu SeshuNo ratings yet