0 ratings0% found this document useful (0 votes)
40 views17 pagesLocal Search
Uploaded by
Krishan Pal SinghCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF or read online on Scribd
0 ratings0% found this document useful (0 votes)
40 views17 pagesLocal Search
Uploaded by
Krishan Pal SinghCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF or read online on Scribd
You are on page 1/ 17
W.
haseol
hotad. Seach 2
> Loo ann us oO newest, trehnique fo2 Solu
Cheng tion gm ee fp Sg
7 Sr as et a pa
ag fin 4 solalion, Mann} am cbipctine fumelen 47
ola ot 4 un
> A Ypcat Search gio Se qotuld
{2 coal obit £ ee ie thon +t nl
oe a Ota Ss on a makung matt
fo tt ine Soluetten d
Y yalue ude & Low!
Local
2 gach te bens
Cries) wad LU ‘
a :
Palio St Cees vf peglucct VAL AME
aoe Cam moe Ken
Jeg ty sel.
dhe
dhe candidate © rato yc
sgyratl HANS.
cpt fo "dt
Tio
a a crise bw ie
gue wo Chet
aA cotton is a Ylobal eT on nf
ue earn hes pu Ot date oc
tor Ls % toned gplumum none & neighbor,
7h ee has 0 gpeee_& tine notion es a
oad serach te celumg —Optimi a)
4 dre Yoluteoin de la
vecten Otc joebyremial
Bey otic oF .
potter roe seeguine that
este dogicee_, dear Ot
ee — :
pve th eeded 1 que ca gre” neigh rer
gn oder a0 Bleed that Dae ee mm morrias
gue UE recrclTOm ana ce conn ea deliclee
ye need Ee Goce olptimnun a CY @/
jaunt ok sles
=> haathy 1 * an jut re a ua Umdead co gor! A ppm frrori ee
algo aa pee quroe any focal 6! (ey LS Neale
cod 48 Motel ut optimuum ( Spi /
as appeormimnertitn algo Jor
b radllie Locetub
oe 4
ate eee eae ei Giaunnog used
fe proplms ay Man- Cut farblem
PRAM: -
nent RAM moctel Yo alloco # multiple
ProtrtorS Gees puke toa posattel moc! LnecOn
2 peowUel RAM 62. PRAM.
Sequential Subsets ancl Asent!s Yheorem._
> due Kqurniial Subsets Lralviguo anol fosertls thuorvens
both wivolue Comaleuetyig am efficent BeBe pores
pom ae “P
So sequential feoh
Pe mown tdlta we +o petfgorn Qumuttel amount
Speen Fase penaetceng_Om wall Yuba ap whe prroblen
te be
»%) 2 dhon abbly @ ~pasollit algo ve enteh Solving dhe robles
‘ “phy b gp
In Some IWAlMELE , cee Toa
: 4 ato be ome Sequonvias
Poo PROCES _sthok needs Vn be dove on faoh.
geubset ope She posalle! ye Completes «
7 FEE «(oe Coutel cliide due ase oven ir
Kb Cow's cr au eee cand
ogg One “proctssoe te cach |
Fe ea EES
> Sum the Clements af each fequendally.
7 Ye apply Civiele 2 congute. prrrceatvee fo the Sem,
Vogn-
> yurs covet eeselh Un am optimal -
TM) XP(m) provotuct og ot) jee Compictrg
Awe Wu “fs 1 witagenes
ZY Brentls Wheoverny— Z
> Brent's ditorem t% Alao gq felrugue he ce Cae
numbers Joveessors. needed do aolut 0 posctieutass
@eovolum . Yan
> S$ an algonim th chessgree! Bo Wat a facoe numé
Poo eegsor idl dwung much ag te Com jr
gun aoent’s Jnrotem wary be ats
_dheotem a4 crwnous pacallel rim AOE AL
a
wn T qa “é aml const 4
npostins ee
\ , O(Ln irl T)
Pr: Lek NP be ae nuwmboer of opocatztns performer
peep Foun ane pacatel . dhe 0 goroestor Gn
ee
giimelatt step i of Me & iw in 0 (Li JP] yore
lus, die ofa sunny qin’ 8 O( LN pl +7)
ince )
= |v p]tt.
eee uatipeections we mugt make to
a Nbemm COE before we Can ope uk wh dhe
PRAM mockel. Y —
sk, we mute be able 10 Compute Ne at the ere
CF skpi vin OC fis PJ) fume. waa P porocsser
> fiat 18, eee mush Rvgre how wd operartrory ae.
actully 4o be penjoumea win step F.
> gd coe nual now ernactly Now to ssyn Cael Processor
one RET 1D attome ib a de perder Win Simulalera ste 4
GL a9 ‘
a Ome Lttm ' &
Paine a Mak fre (oa, a2 -- ~ an), Yaitegee
as ompue QU dnt parefn Bum. s, 7
sini 7 a a
Mg Leeeuscei ue or ne Te we 4, ap
. Castl
RHR OCIS 9
dine ‘
q Le o(n) prroeesors,
os] MS e118] 8 Ne i
| [2/4 a z, 4 2 z 4 B ‘4 e eH lea
pu jo HL poral t |
Recursive coubly 0
Pree govt
c Ae numbces of
£ an ol 2oqn) sown
sima.t tn) 2K Pin) pout
garocessons fo C (or}isyo)
use Con suede
due
amd shi) Aches
qinve us an ©
oN \
dedi or arcae Clammendy
Logn Sabana,
J seems
yteluig she gpsefert Compe
u packaack’ irs eee ane
myer Corn
peo Compute UU “tat parcted
use why
Que roo ee 540% Pp Sub coving
“ae ai
BEBE Se
ihr ale RSID ae .
chk Ise job
a
Pol alan “pce ‘ol do que, pos caltet
aac problem
6.
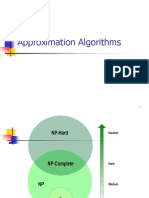
In computer science and operations research, approximation algorithms are algorithms
used to find approximate solutions to optimization problems. Approximation algorithms
are often associated with NP-hard problems; since it is unlikely that there can ever be
efficient polynomial time exact algorithms solving NP-hard problems, one settles for
polynomial time sub-optimal solutions. Unlike heuristics, which usually only find
reasonably good solutions reasonably fast, one wants provable solution quality and
provable run time bounds. Ideally, the approximation is optimal up to a small constant
factor (for instance within 5% of the optimal solution). Approximation algorithms are
increasingly being used for problems where exact polynomial-time algorithms are known
but are too expensive due to the input size.
A typical example for an approximation algorithm is the one for vertex cover in graphs:
find an uncovered edge and add both endpoints to the vertex cover, until none remain. It
is clear that the resulting cover is at most twice as large as the optimal one. This is a
constant factor approximation algorithm with a factor of 2.
NP-hard problems vary greatly in their approximability; some, such as the bin packing
problem, can be approximated within any factor greater than 1 (such a family of
approximation algorithms is often called a polynomial time approximation scheme or
PTAS). Others are impossible to approximate within any constant, or even polynomial
factor unless P = NP, such as the maximum clique problem.
NP-hard problems can often be expressed as integer programs (IP) and solved exactly in
exponential time. Many approximation algorithms emerge from the linear programming
relaxation of the integer program,
Not all approximation algorithms are suitable for all practical applications. They often
use IP/LP/Semidefinite solvers, complex data structures or sophisticated algorithmic
techniques which lead to difficult implementation problems. Also, some approximation
algorithms have impractical running times even though they are polynomial time, for
example O(n"), Yet the study of even very expensive algorithms is not a completely
theoretical pursuit as they can yield valuable insights. A classic example is the initial
PTAS for Euclidean TSP due to Sanjeev Arora which had prohibitive running time, yet
within a year, Arora refined the ideas into a linear time algorithm. Such algorithms are
also worthwhile in some applications where the running times and cost can be justified
eg. computational biology, financial engineering, transportation planning, and inventory
management. In such scenarios, they must compete with the corresponding direct IP
formulations,
Another limitation of the approach is that it applies only to optimization problems and not
to "pure" decision problems like satisfiability, although it is often possible to conceive
optimization versions of such problems, such as the maximum satisfiability problem.
Inapproximability has been a fruitful area of research in computational complexity theory
since the 1990 result of Feige, Goldwasser, Lovasz, Safa and Szegedy on the
inapproximability of Independent Set, After Arora et af. proved the PCP theorem a year
4
later, it has now been shown that Johnson's 1974 approximation algorithms for Max SAT,
Set Cover, Independent Set and Coloring all achieve the optimal approximation ratio,
assuming P != NP.
Optimization problem
In mathematics and computer science, an optimization problem is the problem of
finding the best solution from all feasible solutions. More formally, an optimization
problem A is a quadruple (J,f,m,g), where
+ Tis set of instances;
+ given an instance x is element of I, f(x) is the set of feasible solutions;
‘+ given an instance x and a feasible solution y of x, 7(x,)) denotes the measure of
Y, which is usually a positive real
+ gis the goal function, and is either min or max,
Heuristic algorithm
In computer science, a heuristic algorithm, or simply a heuristic, is an algorithm that is
able to produce an acceptable solution to a problem in many practical scenarios, in the
fashion of a general heuristic, but for which there is no formal proof of its correctness.
Alternatively, it may be correct, but may not be proven to produce an optimal solution, or
to use reasonable resources. Heuristics are typically used when there is no known method
to find an optimal solution, under the given constraints (of time, space efc.) or at all.
Two fundamental goals in computer science are finding algorithms with provably good
run times and with provably good or optimal solution quality. A heuristic is an algorithm
that abandons one or both of these goals; for example, it usually finds pretty good
solutions, but there is no proof the solutions could not get arbitrarily bad; or it usually
runs reasonably quickly, but there is no argument that this will always be the case.
For instance, say you are packing odd-shaped items into a box. Finding a perfect solution
is a hard problem: there is no known way to do it that is significantly faster than trying
every possible way of packing them. What most people do, then, is "put the largest items
in first, then fit the smaller items into the spaces left around them." This will not
necessarily be perfect packing, but it will usually give a packing that is pretty good. It is
an example of a heuristic solution.
Several heuristic methods are used by antivirus software to detect viruses and other
malware.
Judea Pearl
computer problem solving, using several altemative approaches
| states that heuristic methods are based upon intelligent search strategies for
Often, one can find specially crafted problem instances where the heuristic will in fact
produce very bad results or run very slowly; however, such pathological instances might
never occur in practice because of their special structure. Therefore, the use of heuristics
is very common in real world implementations. For many practical problems, a heuristic
algorithm may be the only way to get good solutions in a reasonable amount of time.
There is a class of general heuristic strategies called metaheuristics, which often use
randomized search for example. They can be applied to a wide range of problems, but
‘good performance is never guaranteed.
D tat Pte wut n aiobnel pois (sites) um sae Home.
7 Yue vorenoi cb Kou P us two dubslivisedn cy tae plane
Re ee f
A paint 4 Lies um We cell Corveesbondlurig fo 4 Reb,
REP AL
Zuatidean Orstamte (1?) < Euclidlean.. clistines OF)
(er each Pi ep, ji :
> we denote jue vores clea” Of P_by- Vor (P),
> de cebls unt Coxwcesponds to o gure puis clenoted
by lez) Cablel ‘he yporndU Coll og a
VY) Ywo yckes jour a preipereeckelart broctoy
corenti leagean Js a Lune
eo) thar entonds Maifineke iv
ben cluctetion amd, 4 Fuo
balf planes on citten wide.
©
wi é i
Cotkintor Xctes, Heard heed og parole Limes
cheque 23
A vewndi veutin cs the
Coafice op a Ompty Crete
thes ag fourhinty % 2
morte Sut
—>
rote cell
unpow!
aN emcN Oe nv pont ste f a4. oe
we plone. fer pot P- (P,P) and we (mt) %)
al
d (Pp, %) 2 (eae) ae (3 -%)*
dleoted quae @uchiduan dustomoe
> bs Fe duncte Ha lint Supra ta
arse Ces p will bo demoted by &
Fou, ES tas
Bed) 2 § e]dlan) = d (493.
be We kuaithoy pand 4.
(Pd) as the pespemelsettas Jone too Sei
oy que June dg reet Pe t i‘ a
Ye pepanatin yur lanl plane . ~ a
Dinr)e saan Zag
Conteurneny # jeep ae had} plane D GP) onlay g
iL
7 a s) 2 Dp (ht)
, i aes 177 et
“hs YOVPNEL Pra Oi Rest Oa
Finally, yuo aerial cliogseam of icaran clufemee oa
vis)2_U TeES) Nn VRGS)
pres PEL
to S:
@®
Applicnktens af Serene Tal Penile
be of tn Sciemte!
wr ‘Ruth's Post office. Pooblom :- Given O i
focatrins ee pe offie Jno Oo leLemuins
Qa ae
die cloarak Dsl ope $0 fee Lo
2 Erosest Paiit- Given 0 wt ofp points , itil
tu0 pe CLbotat togtdenr.
3y AU Newark _N. Gubows 2
viel toh - ae Q a a ports
Wy éucli chan Hunwm un Spanning “tie. q
sy hougett Eripty Cutele , aloo Jenowen as wee.
‘ump, Problem.
£) fyned Roclus Kean Netghbows : und all pois
eat cloowst eee (ee distance (ipa
7) au k Neweeak Neighbours ~ bind each pert '
K Cloorst rg bors:
8) enumescoten auitance wn peta sen Grolee, .— Bird
the cleatal tty, , deny te on clagtad pas dle
de nunt fee pos
seu Umale
>A vorenst deizam of n ctishinet ce
n colle -
> one cell tan hour vical ‘
ut au the colle Com , aa
wok . (0) 6
> the number veers Vane - 6 yl
> he numbers é €<3an-6. ware
en, Pe
> te nmloey of mace Fen enn
Conoluseting Voronoi puso uning divfale amol
ei f
VD (se)
2) ened Fuso Vorener ctengean ay)
a Menai Ue to pict uals Iwreary 1 ti
e) oh pel vewnit CEPOP
2 Ntoy Menge
Pwicke — Cunel on 82 Verona: cuagram ao
"> Spl: A wet aC aD plomas pei
> gudpuk t- Yho voronol Aung af s:
Skpli- SB S Contains oa one poont , lt.
Sepus Fund a mecuilan fone L penpendlictelan ee
yeants adh olivicles s jute Sv ard Sa. duel dat
Sr (Sa) Les +0 que hpt outlet) ye oma Sue
Ser Cie S, and SR Cue equal.
3- Conobruet vt Vernal lea @ df SL and&r
deequesivaly , Wdendte trae er. by
Vp (2) land Vo (sa): 4 :
sitpii= Comal O diviclng Preae _ rave Lines;
ay pharm HP wou us dud Locus 0 points
rude ancously toot doa pont sm SL Uno 4
Vp (Se) caleal
port wn Sk Odtaud alt yu
fie wo due
You might also like
- Advanced Algorithms Approximation AlgorithmsNo ratings yetAdvanced Algorithms Approximation Algorithms50 pages
- CS510 Notes 17 Approximation - AlgorithmsNo ratings yetCS510 Notes 17 Approximation - Algorithms40 pages
- Chapter - 2: Fundamentals of Algorithmic Problem SolvingNo ratings yetChapter - 2: Fundamentals of Algorithmic Problem Solving23 pages
- Department of Computer Science and EngineeringNo ratings yetDepartment of Computer Science and Engineering10 pages
- Brief Historical Context of NP CompleteNo ratings yetBrief Historical Context of NP Complete10 pages
- Introduction to Approximation AlgorithmsNo ratings yetIntroduction to Approximation Algorithms46 pages
- 2 - Data Structures and Algorithms in Problem SolvingNo ratings yet2 - Data Structures and Algorithms in Problem Solving8 pages
- Computational Complexity Theory: P (Polynomial Time)No ratings yetComputational Complexity Theory: P (Polynomial Time)11 pages
- Near-Optimal Solutions with Approximation AlgorithmsNo ratings yetNear-Optimal Solutions with Approximation Algorithms23 pages
- Computational Complexity: Definition of Mixed-Integer ProgrammingNo ratings yetComputational Complexity: Definition of Mixed-Integer Programming8 pages