0% found this document useful (0 votes)
530 views185 pagesSecure Code Review Guide 2023
This document provides an overview of a practical secure code review course presented by Seth and Ken.
The key points covered are:
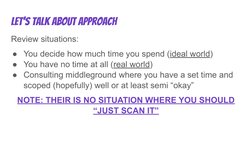
1. The course philosophy is to focus on finding what matters most from a risk-based perspective and provide comprehensive but timely reviews.
2. Attendees will learn a repeatable methodology for conducting secure code reviews through examples, exercises, and discussions of common vulnerabilities and framework nuances.
3. The course covers mapping an application's attack surface, identifying common risks, and performing risk-based reviews of authentication, authorization, injection issues and other vulnerabilities.
Uploaded by
topoyid177Copyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd
0% found this document useful (0 votes)
530 views185 pagesSecure Code Review Guide 2023
This document provides an overview of a practical secure code review course presented by Seth and Ken.
The key points covered are:
1. The course philosophy is to focus on finding what matters most from a risk-based perspective and provide comprehensive but timely reviews.
2. Attendees will learn a repeatable methodology for conducting secure code reviews through examples, exercises, and discussions of common vulnerabilities and framework nuances.
3. The course covers mapping an application's attack surface, identifying common risks, and performing risk-based reviews of authentication, authorization, injection issues and other vulnerabilities.
Uploaded by
topoyid177Copyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd